Mikrotik L2TP IPSEC kein Zugriff aufs Lan aber auf Router und per VPN angebundene Standorte
Hallo,
ich habe zwei Standorte per IPSec angebunden, nun wollte ich per L2TP IPSec eine RoadWarrior Verbindung herstellen, dies funktioniert aus soweit. Ich habe aber leider kein Zugriff auf das Lan. Ping zum Router und vom Router gehen. Auch der Zugriff auf die per IPSec eingebundenen Netze.
Wie in der Konfig zu sehen ist, werden IP-Adressen aus dem Lan-Netz an die Clients verteilt. Für den DHCP Server habe ich dementsprechend fürs Lan den Bereich begrenzt und einen extra Pool für L2TP angelegt. Auch wenn ich in der L2TP Konfig den normalen Lan Pool angebe bekomme ich keine Verbindung ins Lan.
Proxy-ARP ist in der Bridge aktiviert. So steht es in dem Beispiel von Mikrotik und auf diversen anderen Seiten.
Ich habe auch zum testen alle Drop-Regeln deaktiviert, auch so war leider kein Ping auf die Geräte im Lan möglich.
Die Geräte im Lan haben keine Firewall aktiv und sind auch aus den anderen Standortverbindungen zu erreichen.
Hier die Konfig.:
Recht vielen Dank schon mal für die Hilfe
Gruß
quax08
ich habe zwei Standorte per IPSec angebunden, nun wollte ich per L2TP IPSec eine RoadWarrior Verbindung herstellen, dies funktioniert aus soweit. Ich habe aber leider kein Zugriff auf das Lan. Ping zum Router und vom Router gehen. Auch der Zugriff auf die per IPSec eingebundenen Netze.
Wie in der Konfig zu sehen ist, werden IP-Adressen aus dem Lan-Netz an die Clients verteilt. Für den DHCP Server habe ich dementsprechend fürs Lan den Bereich begrenzt und einen extra Pool für L2TP angelegt. Auch wenn ich in der L2TP Konfig den normalen Lan Pool angebe bekomme ich keine Verbindung ins Lan.
Proxy-ARP ist in der Bridge aktiviert. So steht es in dem Beispiel von Mikrotik und auf diversen anderen Seiten.
Ich habe auch zum testen alle Drop-Regeln deaktiviert, auch so war leider kein Ping auf die Geräte im Lan möglich.
Die Geräte im Lan haben keine Firewall aktiv und sind auch aus den anderen Standortverbindungen zu erreichen.
Hier die Konfig.:
[admin@MainRouter] > ppp profile export hide-sensitive
# sep/08/2020 11:19:29 by RouterOS 6.47.2
# software id = 78NP-AYW9
#
# model = RouterBOARD 3011UiAS
# serial number = 5D6B0560E360
/ppp profile
add change-tcp-mss=yes local-address=172.16.51.1 name=l2tp-server-profile \
remote-address=l2tp-pool use-encryption=yes use-ipv6=no use-upnp=no
[admin@MainRouter] > ip ipsec export hide-sensitive
# sep/08/2020 11:21:38 by RouterOS 6.47.2
# software id = 78NP-AYW9
#
# model = RouterBOARD 3011UiAS
# serial number = 5D6B0560E360
/ip ipsec profile
set [ find default=yes ] dh-group=modp4096,modp2048,modp1024 enc-algorithm=\
aes-256,aes-192 hash-algorithm=sha256 lifetime=45m
add dh-group=modp2048 enc-algorithm=aes-256,aes-128,3des hash-algorithm=\
sha256 lifetime=8h name=profile-yyyy
add enc-algorithm=aes-256,aes-128 hash-algorithm=sha256 lifetime=8h name=\
profile-xxxx
/ip ipsec peer
add address=xyxyxy.de exchange-mode=ike2 name=yyyy profile=\
profile-yyyy
add exchange-mode=ike2 name=xxxx passive=yes profile=profile-xxxx \
send-initial-contact=no
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha512,sha256 enc-algorithms=\
aes-256-cbc,aes-256-ctr,aes-256-gcm
add auth-algorithms=sha256 enc-algorithms=aes-256-cbc,aes-128-cbc lifetime=1h \
name=yyyy pfs-group=modp2048
add auth-algorithms=sha256 enc-algorithms=aes-256-cbc,aes-128-cbc lifetime=1h \
name=xxxx pfs-group=modp2048
/ip ipsec identity
add my-id=user-fqdn:mikrotik@vpn.intern peer=yyyy remote-id=\
user-fqdn:pfsense@vpn.intern
add my-id=user-fqdn:3011@vpn.intern peer=xxxx remote-id=\
user-fqdn:hap@vpn.intern
/ip ipsec policy
add dst-address=172.16.1.0/24 peer=yyyy proposal=yyyy \
sa-dst-address=ersterStandort sa-src-address=eigeneWANIP src-address=\
172.16.51.0/24 tunnel=yes
add dst-address=192.168.18.0/24 peer=xxxx proposal=xxxx sa-dst-address=\
zweiterStandort sa-src-address=eigeneWANIP src-address=172.16.51.0/24 \
tunnel=yes
[admin@MainRouter] > ip pool export hide-sensitive
# sep/08/2020 11:26:26 by RouterOS 6.47.2
# software id = 78NP-AYW9
#
# model = RouterBOARD 3011UiAS
# serial number = 5D6B0560E360
/ip pool
add name=dhcp ranges=172.16.51.200-172.16.51.250
add name=l2tp-pool ranges=172.16.51.190-172.16.51.199
[admin@MainRouter] > ip firewall export hide-sensitive
# sep/08/2020 11:45:37 by RouterOS 6.47.2
# software id = 78NP-AYW9
#
# model = RouterBOARD 3011UiAS
# serial number = 5D6B0560E360
/ip firewall filter
add action=accept chain=input dst-port=500,1701,4500 in-interface=pppoe-out1 \
protocol=udp
add action=accept chain=input in-interface=pppoe-out1 protocol=ipsec-esp
add action=drop chain=input comment="Drop Invalid connections" \
connection-state=invalid
add action=accept chain=input comment="Allow ICMP" protocol=icmp
add action=accept chain=input in-interface=!pppoe-out1 src-address=\
172.16.51.0/24
add action=drop chain=forward comment="drop invalid connections" \
connection-state=invalid protocol=tcp
add action=accept chain=forward comment=\
"allow already established connections" connection-state=established
add action=accept chain=forward comment="allow related connections" \
connection-state=related
add action=accept chain=forward dst-address=172.16.1.0/24
add action=jump chain=forward jump-target=tcp protocol=tcp
add action=jump chain=forward jump-target=udp protocol=udp
add action=jump chain=forward jump-target=icmp protocol=icmp
add action=drop chain=tcp comment="deny RPC portmapper" dst-port=111 \
protocol=tcp
add action=drop chain=tcp comment="deny RPC portmapper" dst-port=135 \
protocol=tcp
add action=drop chain=tcp comment="deny NBT" dst-port=137-139 protocol=tcp
add action=drop chain=tcp comment="deny cifs" dst-port=445 protocol=tcp
add action=drop chain=tcp comment="deny NFS" dst-port=2049 protocol=tcp
add action=drop chain=tcp comment="deny NetBus" dst-port=12345-12346 \
protocol=tcp
add action=drop chain=tcp comment="deny NetBus" dst-port=20034 protocol=tcp
add action=drop chain=tcp comment="deny BackOriffice" dst-port=3133 protocol=\
tcp
add action=drop chain=tcp comment="deny DHCP" dst-port=67-68 protocol=tcp
add action=drop chain=udp comment="deny TFTP" dst-port=69 protocol=udp
add action=drop chain=udp comment="deny PRC portmapper" dst-port=111 \
protocol=udp
add action=drop chain=udp comment="deny PRC portmapper" dst-port=135 \
protocol=udp
add action=drop chain=udp comment="deny NBT" dst-port=137-139 protocol=udp
add action=drop chain=udp comment="deny NFS" dst-port=2049 protocol=udp
add action=drop chain=udp comment="deny BackOriffice" dst-port=3133 protocol=\
udp
add action=accept chain=icmp comment="echo reply" icmp-options=0:0 protocol=\
icmp
add action=accept chain=icmp comment="net unreachable" icmp-options=3:0 \
protocol=icmp
add action=accept chain=icmp comment="host unreachable" icmp-options=3:1 \
protocol=icmp
add action=accept chain=icmp comment=\
"host unreachable fragmentation required" icmp-options=3:4 protocol=icmp
add action=accept chain=icmp comment="allow source quench" icmp-options=4:0 \
protocol=icmp
add action=accept chain=icmp comment="allow echo request" icmp-options=8:0 \
protocol=icmp
add action=accept chain=icmp comment="allow time exceed" icmp-options=11:0 \
protocol=icmp
add action=accept chain=icmp comment="allow parameter bad" icmp-options=12:0 \
protocol=icmp
add action=drop chain=icmp comment="deny all other types"
add action=accept chain=input in-interface=!pppoe-out2 src-address=\
172.16.110.0/24
add action=accept chain=input comment="Allow Established connections" \
connection-state=established
add action=drop chain=input comment="Drop everything eslse"
/ip firewall mangle
add action=mark-connection chain=prerouting in-interface=Konsolen-vlan106 \
new-connection-mark=Konsolen-Conn passthrough=yes
add action=mark-connection chain=prerouting in-interface=Kamera-vlan100 \
new-connection-mark=Kamera-Conn passthrough=yes
add action=mark-packet chain=prerouting connection-mark=Konsolen-Conn \
new-packet-mark=Konsolen-Pack passthrough=yes
add action=mark-packet chain=prerouting connection-mark=Kamera-Conn \
new-packet-mark=Kamera-Pack passthrough=yes
add action=accept chain=prerouting dst-address=192.168.2.0/24 in-interface=\
bridge1
add action=mark-connection chain=prerouting connection-mark=no-mark \
in-interface=pppoe-out1 new-connection-mark=WAN-Telekom-Conn passthrough=\
yes
add action=mark-connection chain=prerouting connection-mark=no-mark \
in-interface=pppoe-out2 new-connection-mark=WAN-gggg-Conn passthrough=\
yes
add action=mark-connection chain=prerouting connection-mark=no-mark \
dst-address-type=!local in-interface=bridge1 new-connection-mark=\
WAN-Telekom-Conn passthrough=yes per-connection-classifier=\
both-addresses-and-ports:2/0
add action=mark-connection chain=prerouting connection-mark=no-mark \
dst-address-type=!local in-interface=bridge1 new-connection-mark=\
WAN-gggg-Conn passthrough=yes per-connection-classifier=\
both-addresses-and-ports:2/1
add action=mark-routing chain=prerouting connection-mark=WAN-Telekom-Conn \
in-interface=bridge1 new-routing-mark=Telekom-Routing passthrough=yes
add action=mark-routing chain=prerouting connection-mark=WAN-gggg-Conn \
in-interface=bridge1 new-routing-mark=gggg-Routing passthrough=yes
add action=mark-routing chain=output connection-mark=WAN-Telekom-Conn \
new-routing-mark=Telekom-Routing passthrough=yes
add action=mark-routing chain=output connection-mark=WAN-gggg-Conn \
new-routing-mark=gggg-Routing passthrough=yes
/ip firewall nat
add action=accept chain=srcnat comment="VPN yyyy" dst-address=\
172.16.1.0/24 src-address=172.16.51.0/24
add action=accept chain=srcnat comment=xxxx dst-address=192.168.18.0/24 \
src-address=172.16.51.0/24
add action=masquerade chain=srcnat dst-address=192.168.2.0/24 out-interface=\
ether1 src-address=172.16.51.0/24
add action=masquerade chain=srcnat comment="Telekom PPPoE" out-interface=\
pppoe-out1
add action=masquerade chain=srcnat comment="gggg PPPoE" out-interface=\
pppoe-out2
/ip firewall service-port
set ftp disabled=yes
set tftp disabled=yes
set irc disabled=yes
set h323 disabled=yes
set pptp disabled=yes
set udplite disabled=yes
set dccp disabled=yes
set sctp disabled=yes
[admin@MainRouter] >Recht vielen Dank schon mal für die Hilfe
Gruß
quax08
Please also mark the comments that contributed to the solution of the article
Content-Key: 602701
Url: https://administrator.de/contentid/602701
Printed on: April 19, 2024 at 19:04 o'clock
9 Comments
Latest comment
Bist du hiernach vorgegangen ??
Scheitern am IPsec VPN mit MikroTik
Mögliche Fehler:
Scheitern am IPsec VPN mit MikroTik
Mögliche Fehler:
- Proxy ARP aktiviert ?
- L2TP VPN Client IP Adressen vergessen in der MT Firewall einzutragen das sie vom NAT (Adress Translation) ausgenommen sind ?
- Wenn du Windows Endgeräte anpingst ggf. ICMP (Ping) in der Firewall freigeben was dort generell gesperrt ist.
- Stimmen die Rückrouten ? Sprich haben die angepingten Endgeräte einen Gateway Eintrag ?
Das hattest du auch beachtet ?
Mikrotik kein Zugriff über VPN direkt auf Router
Mikrotik kein Zugriff über VPN direkt auf Router
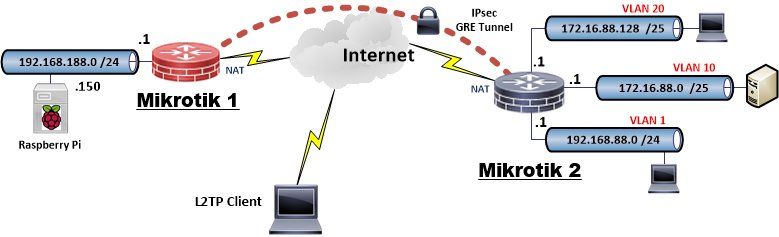
Zum Verifizieren mal einen kleinen Testaufbau geamacht:
2 Mikrotiks mit einem Standort IPsec VPN sowie GRE Tunnel und dynamischen Routing liefen schon. Standard Firewall aus der Default Konfig. Auf dem Roten dann einfach nur einen L2TP Server hinzugefügt.
Konfig der beiden Geräte:
Fazit:
Funktioniert fehlerlos und ohne Probleme. Alle Endgeräte in den jeweiligen lokalen LANs sind vom L2TP Client völlig problemlos ping- und erreichbar !
Dein Verhalten lässt sich absolut nicht nachvollziehen !!
2 Mikrotiks mit einem Standort IPsec VPN sowie GRE Tunnel und dynamischen Routing liefen schon. Standard Firewall aus der Default Konfig. Auf dem Roten dann einfach nur einen L2TP Server hinzugefügt.
Konfig der beiden Geräte:
 Mikrotik 1:
Mikrotik 1:
[admin@RB750GL] > export
# sep/09/2020 08:38:25 by RouterOS 6.47.3
#
# model = 750GL
/interface bridge
add admin-mac=D4:CA:6D:12:76:34 arp=proxy-arp auto-mac=no comment=Bridge name=bridge
/interface ethernet
set [ find default-name=ether1 ] comment="WAN Interface"
/interface gre
add allow-fast-path=no ipsec-secret=geheim123 local-address=10.99.1.149 mtu=1400 name=\
gre-tunnel-RB750 remote-address=10.1.1.150
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048 enc-algorithm=aes-256,aes-128 nat-traversal=no
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha256,sha1 enc-algorithms=aes-256-cbc,aes-128-cbc \
pfs-group=modp2048
/ip pool
add name=dhcp_pool1 ranges=192.168.188.100-192.168.188.150
/ip dhcp-server
add address-pool=dhcp_pool1 disabled=no interface=bridge
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
/interface l2tp-server server
set authentication=mschap2 enabled=yes ipsec-secret=test1234 use-ipsec=yes
/ip address
add address=192.168.188.1/24 comment="Lokales LAN" interface=bridge network=192.168.188.0
add address=172.31.31.13/30 interface=gre-tunnel-RB750 network=172.31.31.12
/ip dhcp-client
add comment="Internet Port" disabled=no interface=ether1
/ip dhcp-server network
add address=192.168.188.0/24 dhcp-option="NTP Server" domain=home.arpa gateway=\
192.168.188.1 netmask=24
/ip dns
set allow-remote-requests=yes
/ip firewall filter
add action=accept chain=input dst-port=500 protocol=udp
add action=accept chain=input dst-port=1701 protocol=udp
add action=accept chain=input dst-port=4500 protocol=udp
add action=accept chain=input protocol=ipsec-esp
add action=accept chain=input comment="defconf: accept established,related,untracked" \
connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" ipsec-policy=\
in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" ipsec-policy=\
out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment="defconf: accept established,related, untracked" \
connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop all from WAN not DSTNATed" \
connection-nat-state=!dstnat connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" ipsec-policy=out,none \
out-interface-list=WAN
/ip ipsec settings
set accounting=no
/ppp secret
add local-address=192.168.188.1 name=testuser password=test123 remote-address=\
192.168.188.222 service=l2tp
/routing rip
set redistribute-static=yes
/routing rip interface
add interface=bridge passive=yes receive=v2
add interface=gre-tunnel-RB750 receive=v2
/routing rip network
add network=192.168.188.0/24
add network=172.31.31.12/30
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name=RB750GL
/system ntp client
set enabled=yes
[admin@RB750GL] >  Mikrotik 2:
Mikrotik 2:
[admin@RB750] > export
# sep/09/2020 08:12:58 by RouterOS 6.47.3
#
# model = 750
/interface bridge
add admin-mac=00:0C:42:12:90:34 auto-mac=no comment="VLAN Bridge" igmp-snooping=yes name=\
bridge vlan-filtering=yes
/interface ethernet
set [ find default-name=ether1 ] comment="WAN Port (NAT)"
set [ find default-name=ether3 ] comment="Management (VLAN1)"
set [ find default-name=ether5 ] comment="Tagged Uplink"
/interface gre
add allow-fast-path=no comment="GRE Tunnel RB750" ipsec-secret=geheim123 local-address=\
10.1.1.150 mtu=1400 name=gre-tunnel-RB750G remote-address=10.99.1.149
add allow-fast-path=no comment="GRE Tunnel hAP" ipsec-secret=test123 local-address=\
10.1.1.150 name=gre-tunnel-hap remote-address=10.99.1.199
/interface vlan
add interface=bridge name=vlan1 vlan-id=1
add interface=bridge name=vlan10 vlan-id=10
add interface=bridge name=vlan20 vlan-id=20
add interface=bridge name=vlan30 vlan-id=30
/ip ipsec profile
set [ find default=yes ] dh-group=modp2048 enc-algorithm=aes-256,aes-128 nat-traversal=no
add dh-group=modp2048 enc-algorithm=aes-256,aes-128 hash-algorithm=sha256 name=Cisco \
nat-traversal=no
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha256,sha1 enc-algorithms=aes-256-cbc,aes-128-cbc \
pfs-group=modp2048
add auth-algorithms=sha256 enc-algorithms=aes-256-cbc,aes-128-cbc lifetime=1h name=Cisco \
pfs-group=modp2048
/ip pool
add name=Pool1 ranges=192.168.88.100-192.168.88.150
add name=Pool10 ranges=172.16.88.15-172.16.88.20
add name=Pool20 ranges=172.16.88.150-172.16.88.200
add name=Pool30 ranges=192.168.178.100-192.168.178.120
/ip dhcp-server
add address-pool=Pool10 disabled=no interface=vlan10 name="DHCP VLAN-10"
add address-pool=Pool1 disabled=no interface=vlan1 name="DHCP VLAN-1"
add address-pool=Pool20 disabled=no interface=vlan20 name="DHCP VLAN-20"
add address-pool=Pool30 disabled=no interface=vlan30 name="DHCP VLAN-30"
/interface bridge port
add bridge=bridge frame-types=admit-only-untagged-and-priority-tagged interface=ether4 \
pvid=30
add bridge=bridge frame-types=admit-only-vlan-tagged interface=vlan1
add bridge=bridge frame-types=admit-only-vlan-tagged interface=vlan10 pvid=10
add bridge=bridge frame-types=admit-only-vlan-tagged interface=vlan20 pvid=20
add bridge=bridge comment="Uplink Switch" interface=ether5
add bridge=bridge frame-types=admit-only-vlan-tagged interface=vlan30 pvid=30
/interface bridge vlan
add bridge=bridge tagged=vlan1,bridge untagged=ether5 vlan-ids=1
add bridge=bridge tagged=bridge,vlan10,ether5 vlan-ids=10
add bridge=bridge tagged=bridge,vlan20,ether5 vlan-ids=20
add bridge=bridge tagged=bridge,vlan30,ether5 untagged=ether4 vlan-ids=30
/ip address
add address=192.168.88.1/24 comment="L3 VLAN 1" interface=vlan1 network=192.168.88.0
add address=172.16.88.1/25 comment="L3 VLAN-10" interface=vlan10 network=172.16.88.0
add address=172.16.88.129/25 comment="L3 VLAN-20" interface=vlan20 network=172.16.88.128
add address=172.31.31.2/30 comment="GRE Tunnel IP hAP" interface=gre-tunnel-hap network=\
172.31.31.0
add address=172.31.31.14/30 interface=gre-tunnel-RB750G network=172.31.31.12
add address=192.168.178.1/24 interface=vlan30 network=192.168.178.0
/ip dhcp-client
add comment=WAN-Port disabled=no interface=ether1
/ip dhcp-server network
add address=172.16.88.0/25 comment=VLAN-10 dns-server=192.168.7.254 gateway=172.16.88.1 \
netmask=25
add address=172.16.88.128/25 comment=VLAN-20 dns-server=192.168.7.254 gateway=172.16.88.129 \
netmask=25
add address=192.168.88.0/24 comment=VLAN-1 gateway=192.168.88.1 netmask=24
add address=192.168.178.0/24 dns-server=192.168.7.254 gateway=192.168.178.1 netmask=24
/ip dns
set allow-remote-requests=yes
/ip firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" \
connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" ipsec-policy=\
in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" ipsec-policy=\
out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment="defconf: accept established,related, untracked" \
connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop all from WAN not DSTNATed" \
connection-nat-state=!dstnat connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" ipsec-policy=out,none \
out-interface-list=WAN
/ip service
set telnet address=192.168.88.0/24
set ftp disabled=yes
set www disabled=yes
set ssh address=192.168.88.0/24
set api disabled=yes
set winbox address=192.168.88.0/24
set api-ssl disabled=yes
/ip ssh
set allow-none-crypto=yes forwarding-enabled=remote
/routing rip interface
add receive=v2
add interface=vlan1 passive=yes receive=v2
add interface=vlan10 passive=yes receive=v2
add interface=vlan20 passive=yes receive=v2
add interface=gre-tunnel-hap receive=v2
add interface=gre-tunnel-RB750G receive=v2
/routing rip network
add network=172.31.31.8/30
add network=192.168.88.0/24
add network=172.16.88.0/25
add network=172.16.88.128/25
add network=172.31.31.0/30
add network=172.31.31.12/30
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name=RB750
/system ntp client
set enabled=yes
[admin@RB750] > Fazit:
Funktioniert fehlerlos und ohne Probleme. Alle Endgeräte in den jeweiligen lokalen LANs sind vom L2TP Client völlig problemlos ping- und erreichbar !
Dein Verhalten lässt sich absolut nicht nachvollziehen !!
Muss aber de facto an deiner Konfig oder einer falschen FW Regel liegen. Wie gesagt...in einer Standard Konfig mit typischer Internet Firewall lässt sich der Fehler nicht nachvollziehen.
Das o.a. Setup rennt fehlerlos !
Ggf. deaktivierst du temporär mal schrittweise deine Regeln mit Ausnahme der wichtigsten und checkst welche da den VPN Traffic blockt ?!
Das o.a. Setup rennt fehlerlos !
Ggf. deaktivierst du temporär mal schrittweise deine Regeln mit Ausnahme der wichtigsten und checkst welche da den VPN Traffic blockt ?!