Mikrotik hinter Fritz, Wireguard Site to Site, keine Verbindung
Hallo,
mit hilfe von Aqui habe ich bereits eine funktionierende IPSec Verbindung konfiguriert. Nun kommt die Neugier und der Upgradetrieb dazu und hat das Setup wie folgt erweitert:
Ziel Site to Site Verbindung:
Büro
Fest IP 37.xx.xx.xx
192.168.0.1 Fritz
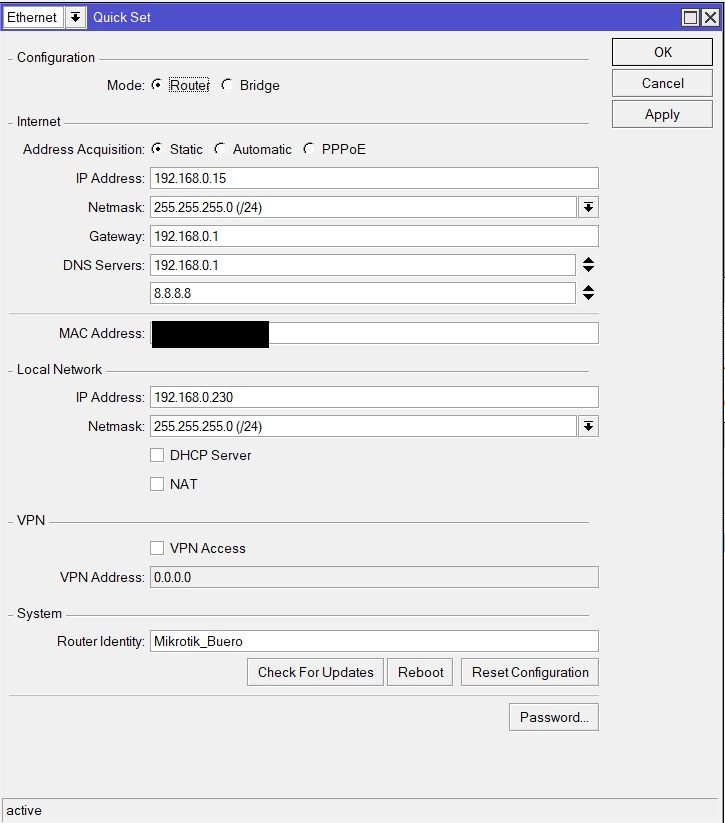
192.168.0.15 Mikrotik Hex
192.168.0.230 Mikrotik Hex
nach
Zuhause
DSL Light
192.168.178.1 Fritz
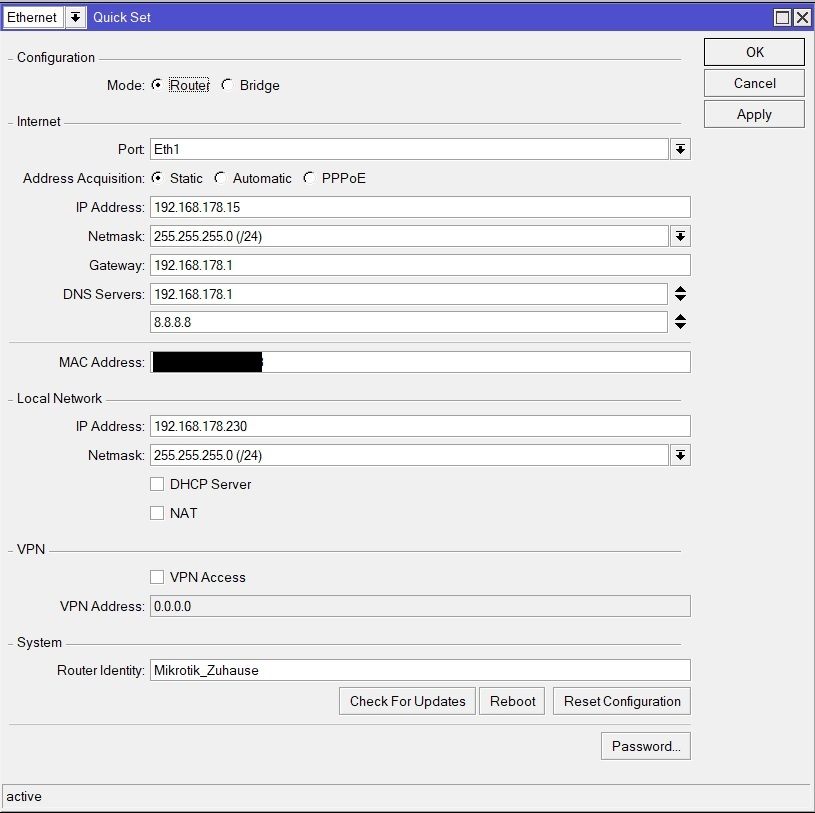
192.168.178.15 Mikrotik RB2011
192.168.178.230 Mikrotik RB2011
als Tunnel habe ich die IP aus dem Forum gewählt: 100.64.64.0
Die Mikrotiks sind mit dem Port 1 direkt an der Fritz und mit einem anderen Port am Switch.
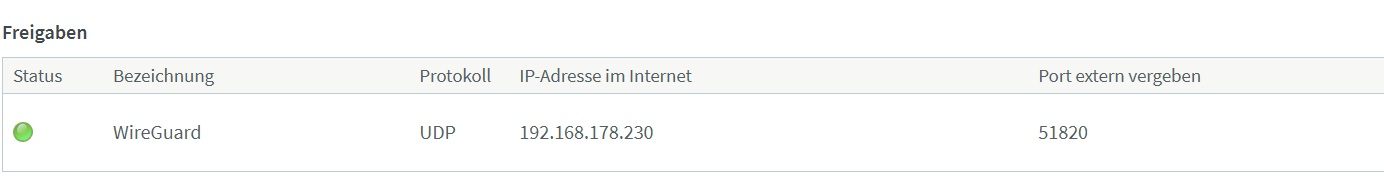
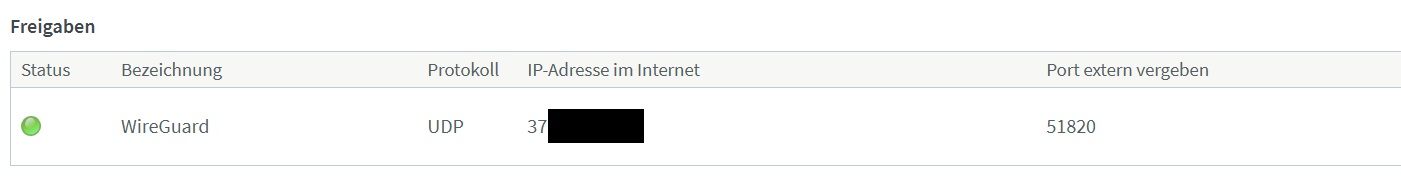
In beiden Fritzboxen habe ich den Port 51820 freigeschaltet:
und die Mikrotiks lt. Anleitung konfiguriert:
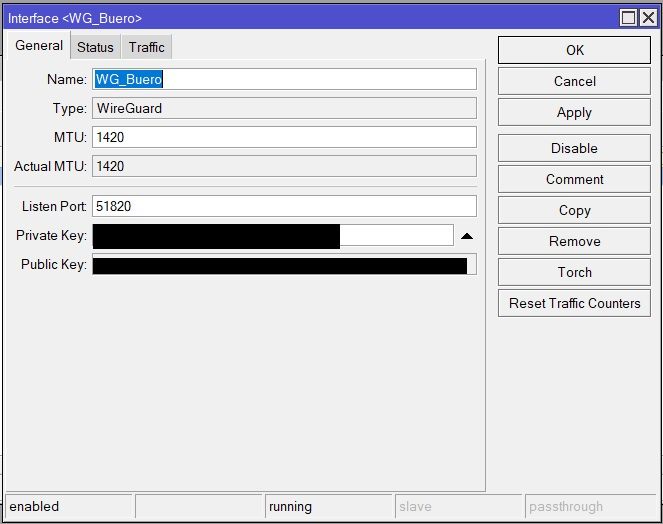
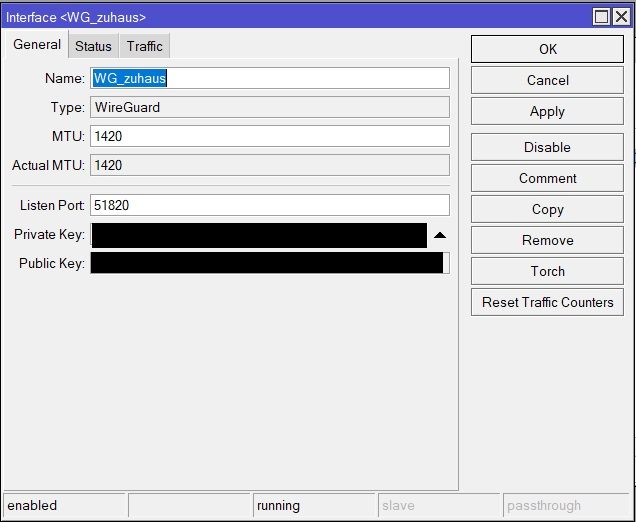
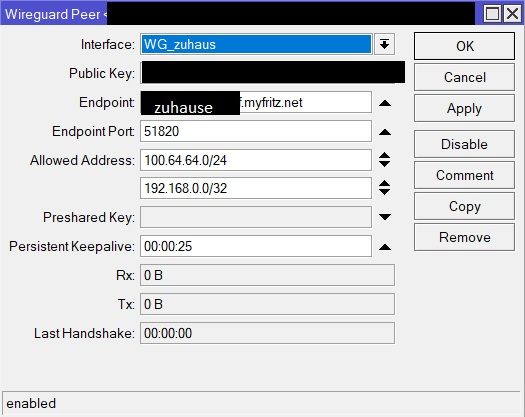
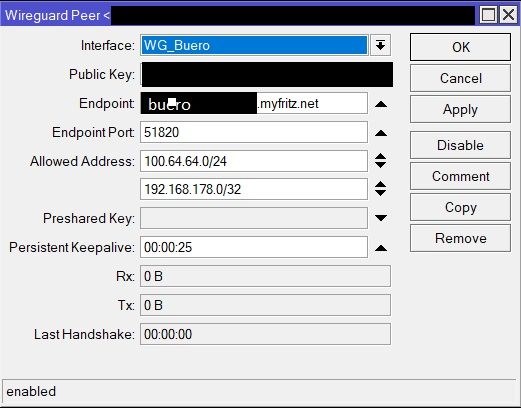
Die Adressen auf beiden Mikrotiks hinterlegt:
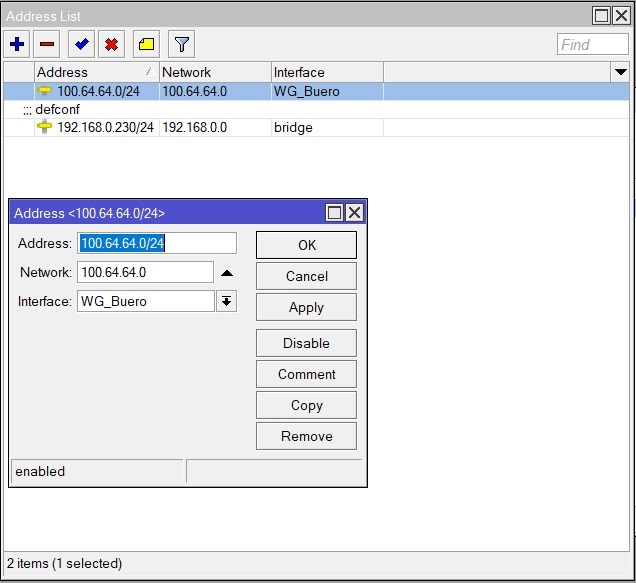
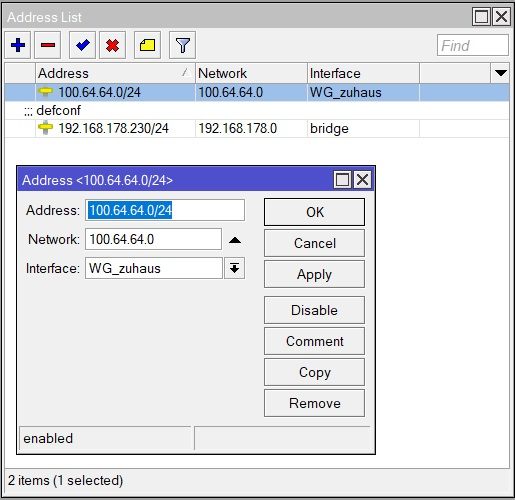
Die Routen angelegt:
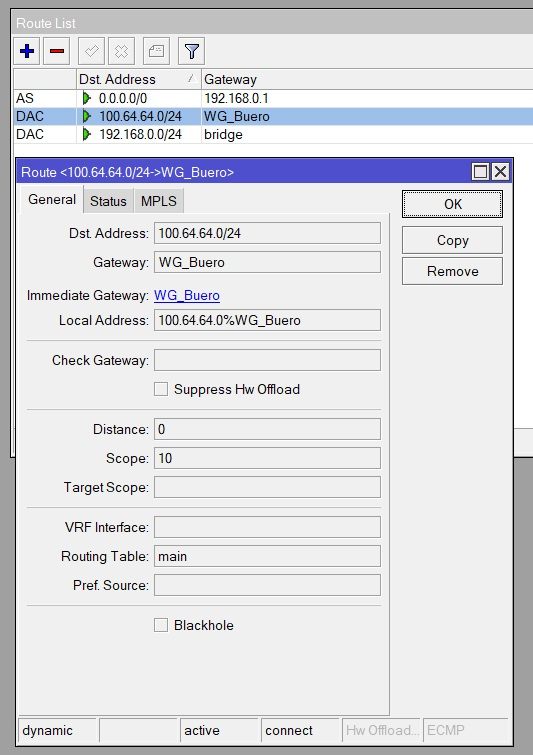
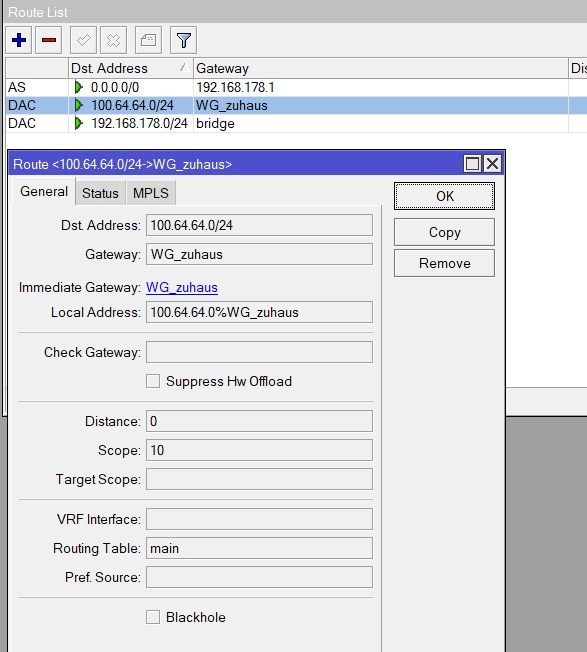
und die Firewall freigeschaltet:
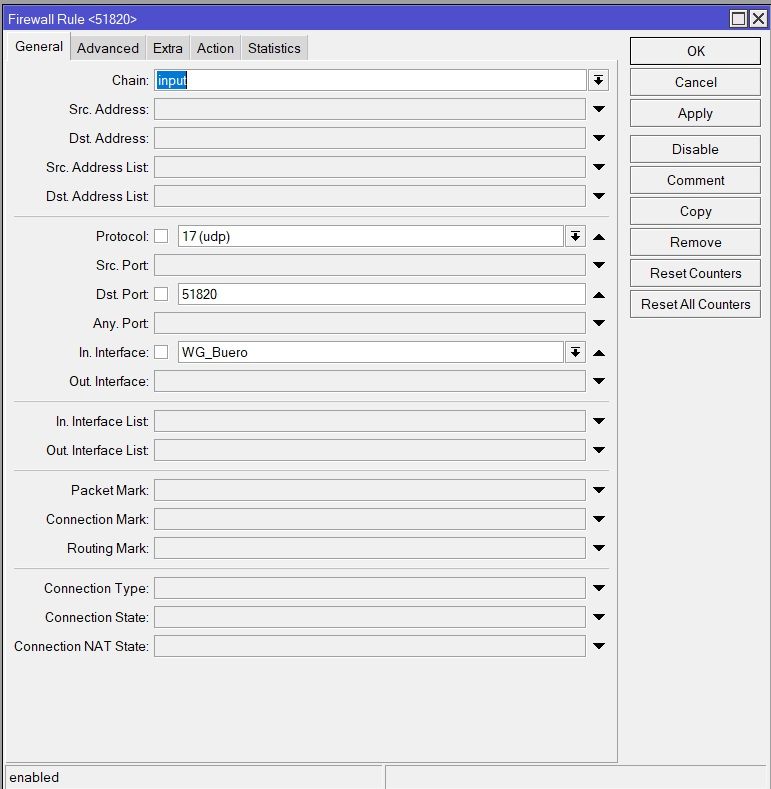
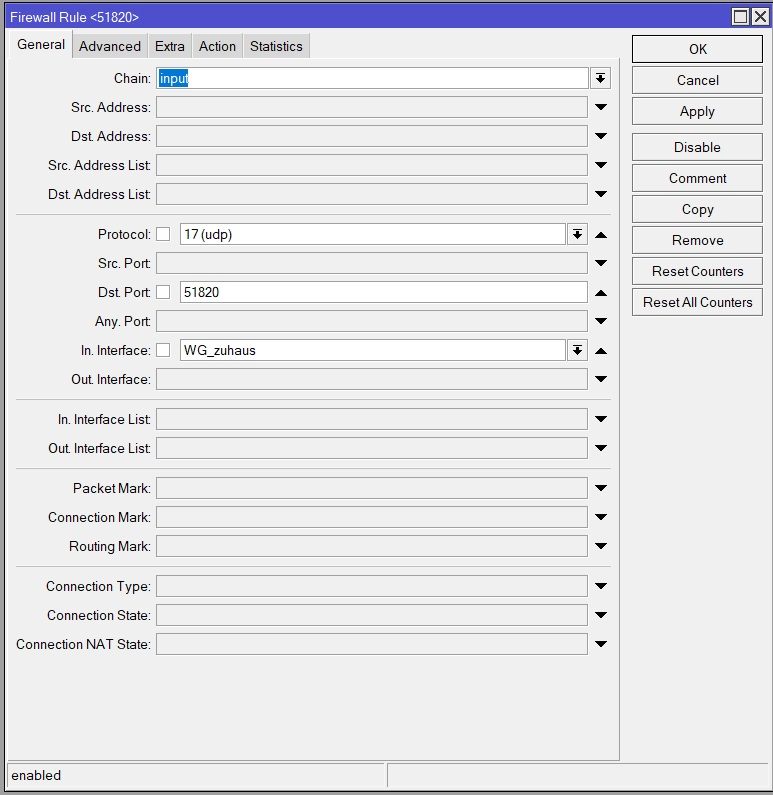
Und war nun der Meinung mich an den diversen Anleitungen im Forum ans Ziel gearbeitet zu haben... Aber leider tut sich nichts, keine Verbindung und im Log wird nichts angezeigt. Also kein Fehler, an welcher Stelle es klemmt.
Nun steh ich wieder auf dem Schlauch und weiss nicht, an welcher Stelle anpacken zu müssen.
mit hilfe von Aqui habe ich bereits eine funktionierende IPSec Verbindung konfiguriert. Nun kommt die Neugier und der Upgradetrieb dazu und hat das Setup wie folgt erweitert:
Ziel Site to Site Verbindung:
Büro
Fest IP 37.xx.xx.xx
192.168.0.1 Fritz
192.168.0.15 Mikrotik Hex
192.168.0.230 Mikrotik Hex
nach
Zuhause
DSL Light
192.168.178.1 Fritz
192.168.178.15 Mikrotik RB2011
192.168.178.230 Mikrotik RB2011
als Tunnel habe ich die IP aus dem Forum gewählt: 100.64.64.0
Die Mikrotiks sind mit dem Port 1 direkt an der Fritz und mit einem anderen Port am Switch.


In beiden Fritzboxen habe ich den Port 51820 freigeschaltet:


und die Mikrotiks lt. Anleitung konfiguriert:




Die Adressen auf beiden Mikrotiks hinterlegt:


Die Routen angelegt:


und die Firewall freigeschaltet:


Und war nun der Meinung mich an den diversen Anleitungen im Forum ans Ziel gearbeitet zu haben... Aber leider tut sich nichts, keine Verbindung und im Log wird nichts angezeigt. Also kein Fehler, an welcher Stelle es klemmt.
Nun steh ich wieder auf dem Schlauch und weiss nicht, an welcher Stelle anpacken zu müssen.
Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 5756708730
Url: https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html
Ausgedruckt am: 05.08.2025 um 07:08 Uhr
16 Kommentare
Neuester Kommentar
Hi,
wenn du bei deinen MikroTiks auf der WAN und LAN Seite den selben IP Adressbereich hast, kannst du die beiden Geräte gleich als Bridge konfigurieren und nicht als Router, dann brauchst du auch keine Firewallregeln.
SG
Edit: auf der Büroseite brauchst du keinen Endpoint konfigurieren. Mir haben die YouTube Videos von „The Network Berg“ geholfen, kann ich dir nur empfehlen 😉
wenn du bei deinen MikroTiks auf der WAN und LAN Seite den selben IP Adressbereich hast, kannst du die beiden Geräte gleich als Bridge konfigurieren und nicht als Router, dann brauchst du auch keine Firewallregeln.
SG
Edit: auf der Büroseite brauchst du keinen Endpoint konfigurieren. Mir haben die YouTube Videos von „The Network Berg“ geholfen, kann ich dir nur empfehlen 😉
Naja, warum nicht Fritz!box zu Fritz!box?
Die IP Adressierung der Wireguard Interfaces ist vollkommen falsch ebenso die AllowedIPs un deren Subnetzmasken stimmen beidseitig ebenfalls nicht.
Des weiteren verwendest du einen für CGNat reservierten Adressbereich 100.64.0.0/10.
Ich würde dir erst mal die Grundlagen zur IP-Adressierung empfehlen bevor du mit Wireguard losrennst.
Und dann in der Firewall natürlich die Forward-Chain für Wireguard freischalten
Des weiteren brauchst du natürlich auch zwei Routen
Auf dem Heimrouter eine Route ins Büro Netz
Auf dem Buero Router eine Route ins Heimnetz
Gruß Wurstel
Des weiteren verwendest du einen für CGNat reservierten Adressbereich 100.64.0.0/10.
Ich würde dir erst mal die Grundlagen zur IP-Adressierung empfehlen bevor du mit Wireguard losrennst.
/interface wireguard peers
add allowed-address=10.20.0.1/32,192.168.0.0/24 endpoint-address=\
xxbueroxx.myfritz.net endpoint-port=51820 interface=WG_zuhaus \
persistent-keepalive=25s public-key=\
"xxxx"
/ip address
add address=10.20.0.2/24 interface=WG_zuhaus network=10.20.0.0/interface wireguard peers
add allowed-address=10.20.0.2/32,192.168.178.0/24 endpoint-address=\
xxzuhausexx.myfritz.net endpoint-port=51820 interface=WG_Buero \
persistent-keepalive=25s public-key=\
"xxxx"
/ip address
add address=10.20.0.1/24 interface=WG_Buero network=10.20.0.0Und dann in der Firewall natürlich die Forward-Chain für Wireguard freischalten
/ip firewall filter add chain=forward place-before=0 dst-address=192.168.0.0/24 action=accept
/ip firewall filter add chain=forward place-before=0 src-address=192.168.0.0/24 action=accept/ip firewall filter add chain=forward place-before=0 dst-address=192.168.178.0/24 action=accept
/ip firewall filter add chain=forward place-before=0 src-address=192.168.178.0/24 action=acceptDes weiteren brauchst du natürlich auch zwei Routen
Auf dem Heimrouter eine Route ins Büro Netz
/ip route add dst-address=192.168.0.0/24 gateway=10.20.0.1Auf dem Buero Router eine Route ins Heimnetz
/ip route add dst-address=192.168.178.0/24 gateway=10.20.0.2Gruß Wurstel
Hast du dir dieses Video angeschaut?
youtu.be/P6f8Qc4EItc
Mit diesem solltest du alle Einstellungen haben 😉
youtu.be/P6f8Qc4EItc
Mit diesem solltest du alle Einstellungen haben 😉
Ach ja die statischen Routen hatte ich noch vergessen, habe ich oben ergänzt, sorry.