Mikrotik Firmware 7.9+ und nichts geht mehr
Hallo, hat alles super geklappt hab so Dinge wie Nextcloud und Passbolt von "außen" erreichbar gemacht bekommen. Hätte nie gedacht das ich mal sowas aufbauen könnte.
Lief auch alles super, bin super zufrieden allerdings bin ich bei Mikrotik Firmware Version 7.8 stecken geblieben. Bis zu dieser Firmware lief alles super. Hatte dann mal auf 7.9 und 7.10 hochgezogen und auf einmal funktionierte gar nichts mehr. Mit nichts meine ich, ich komme nicht mehr in die anderen VLAN's und nicht mehr ins Internet. Ich vermute irgendwas mit dem DNS und/oder der Firewall (dst-nat)? DNS (unbound) läuft bei mir auf einem RPi extern (10.1.1.2 zusammen mit AdGuard) und dort ist auch der DHCP-Server tätig.
Downgrade ich zurück auf 7.8 funktioniert alles wieder wunderbar.
Die derzeitige Konfigdatei:
Lief auch alles super, bin super zufrieden allerdings bin ich bei Mikrotik Firmware Version 7.8 stecken geblieben. Bis zu dieser Firmware lief alles super. Hatte dann mal auf 7.9 und 7.10 hochgezogen und auf einmal funktionierte gar nichts mehr. Mit nichts meine ich, ich komme nicht mehr in die anderen VLAN's und nicht mehr ins Internet. Ich vermute irgendwas mit dem DNS und/oder der Firewall (dst-nat)? DNS (unbound) läuft bei mir auf einem RPi extern (10.1.1.2 zusammen mit AdGuard) und dort ist auch der DHCP-Server tätig.
Downgrade ich zurück auf 7.8 funktioniert alles wieder wunderbar.
Die derzeitige Konfigdatei:
# jul/19/2023 14:33:29 by RouterOS 7.8
# software id = VMNZ-R2JY
#
# model = CRS326-24G-2S+
# serial number = XXXXXXXXXX
/caps-man channel
add band=2ghz-g/n control-channel-width=20mhz frequency=2452 name=2GHz
add band=5ghz-a/n/ac control-channel-width=20mhz extension-channel=Ceee \
frequency=5180 name=5GHz
/interface bridge
add igmp-snooping=yes igmp-version=3 ingress-filtering=no multicast-querier=\
yes name="bridge - VLAN" vlan-filtering=yes
/interface ethernet
set [ find default-name=ether1 ] name="ether1 - ISP"
set [ find default-name=ether2 ] name="ether2 - RPi-Services"
set [ find default-name=ether3 ] name="ether3 - AP1"
set [ find default-name=ether4 ] name="ether4 - Server"
set [ find default-name=ether5 ] name="ether5 - Homematic"
set [ find default-name=ether6 ] disabled=yes name="ether6 - AP1"
set [ find default-name=ether7 ] disabled=yes name="ether7 - Server"
set [ find default-name=ether8 ] disabled=yes
set [ find default-name=ether9 ] disabled=yes
set [ find default-name=ether10 ] disabled=yes
set [ find default-name=ether11 ] disabled=yes
set [ find default-name=ether12 ] disabled=yes
set [ find default-name=ether13 ] disabled=yes
set [ find default-name=ether14 ] disabled=yes
set [ find default-name=ether15 ] disabled=yes
set [ find default-name=ether16 ] disabled=yes
set [ find default-name=ether17 ] disabled=yes
set [ find default-name=ether18 ] disabled=yes
set [ find default-name=ether19 ] disabled=yes
set [ find default-name=ether20 ] disabled=yes
set [ find default-name=ether21 ] disabled=yes
set [ find default-name=ether22 ] disabled=yes
set [ find default-name=ether23 ] disabled=yes
set [ find default-name=sfp-sfpplus1 ] disabled=yes
set [ find default-name=sfp-sfpplus2 ] disabled=yes
/interface vlan
add interface="bridge - VLAN" name="VLAN1(Mgmt)" vlan-id=1
add interface="bridge - VLAN" name=VLAN10 vlan-id=10
add interface="bridge - VLAN" name=VLAN20 vlan-id=20
add interface="bridge - VLAN" name=VLAN30 vlan-id=30
add interface="bridge - VLAN" name=VLAN40 vlan-id=40
add interface="bridge - VLAN" name=VLAN50 vlan-id=50
add interface="bridge - VLAN" name=VLAN100 vlan-id=100
/caps-man datapath
add bridge="bridge - VLAN" client-to-client-forwarding=yes mtu=1500 name=\
datapath1 vlan-id=30 vlan-mode=use-tag
add bridge="bridge - VLAN" client-to-client-forwarding=yes local-forwarding=\
no name="datapath2 - Guest" vlan-id=20 vlan-mode=use-tag
/caps-man security
add authentication-types=wpa2-psk encryption=aes-ccm name=wpa2
add authentication-types=wpa2-psk encryption=aes-ccm name=security_guest
/caps-man configuration
add channel=2GHz country=germany datapath=datapath1 mode=ap multicast-helper=\
full name="Dynamic VLANs" security=wpa2 ssid=TUXNET_AP
add channel=5GHz country=germany datapath=datapath1 datapath.mtu=1500 mode=ap \
multicast-helper=full name="WLAN 5GHz" security=wpa2 ssid=TUXNET_AP_5G
add channel=5GHz country=germany datapath=datapath1 mode=ap multicast-helper=\
full name="WLAN 5GHz Guest" security=wpa2 ssid=TUXNET_GUEST_AP_5G
add channel=2GHz country=germany datapath=datapath1 mode=ap multicast-helper=\
full name="WLAN GUEST" security=wpa2 ssid=TUXNETAPGUEST
/caps-man interface
add channel=2GHz configuration="Dynamic VLANs" datapath=datapath1 \
datapath.local-forwarding=no .vlan-mode=use-tag disabled=no l2mtu=1600 \
mac-address=18:FD:74:5D:49:EE master-interface=none name=cap1 radio-mac=\
18:FD:74:5D:49:EE radio-name=18FD745D49EE security=wpa2
add channel=5GHz configuration="WLAN 5GHz" datapath=datapath1 \
datapath.vlan-mode=use-tag disabled=no l2mtu=1600 mac-address=\
18:FD:74:5D:49:EF master-interface=none mtu=1500 name=cap2 radio-mac=\
18:FD:74:5D:49:EF radio-name=18FD745D49EF security=wpa2
add channel=2GHz channel.frequency=2452 configuration="WLAN GUEST" datapath=\
"datapath2 - Guest" datapath.vlan-id=20 .vlan-mode=use-tag disabled=yes \
l2mtu=1600 mac-address=1A:FD:74:5D:49:EE master-interface=cap1 name=cap3 \
radio-mac=00:00:00:00:00:00 radio-name="" security=security_guest
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip ipsec peer
add exchange-mode=ike2 name=DynamicIP passive=yes send-initial-contact=no
/ip ipsec profile
set [ find default=yes ] enc-algorithm=aes-256,aes-128,3des
/ip ipsec proposal
set [ find default=yes ] enc-algorithms=\
aes-256-cbc,aes-192-cbc,aes-192-gcm,aes-128-cbc,3des pfs-group=none
/port
set 0 name=serial0
/ppp profile
set *0 dns-server=10.1.1.2 local-address=10.1.1.254 remote-address=10.1.1.2 \
use-encryption=required use-ipv6=no use-mpls=yes
add dns-server=10.1.1.2 name=l2tp_vpn use-encryption=required use-ipv6=no \
use-upnp=yes
set *FFFFFFFE dns-server=10.1.1.2 local-address=10.1.100.1 remote-address=\
192.168.8.1
/caps-man aaa
set called-format=mac mac-format=18:FD:74:5D:49:EF mac-mode=\
as-username-and-password
/caps-man manager
set ca-certificate=auto certificate=auto enabled=yes
/interface bridge port
add bridge="bridge - VLAN" comment="Raspberry DNS, DHCP, AdGuard" \
frame-types=admit-only-untagged-and-priority-tagged interface=\
"ether2 - RPi-Services"
add bridge="bridge - VLAN" comment="Mikrotik Access Point 1" frame-types=\
admit-only-untagged-and-priority-tagged interface="ether3 - AP1" \
multicast-router=disabled pvid=30
add bridge="bridge - VLAN" comment="Big Server" frame-types=\
admit-only-untagged-and-priority-tagged interface="ether4 - Server" \
multicast-router=disabled pvid=40
add bridge="bridge - VLAN" comment="Homematic Sender" frame-types=\
admit-only-untagged-and-priority-tagged interface="ether5 - Homematic" \
multicast-router=disabled pvid=50
add bridge="bridge - VLAN" disabled=yes frame-types=\
admit-only-untagged-and-priority-tagged interface="ether1 - ISP"
/interface bridge settings
set use-ip-firewall-for-vlan=yes
/ip neighbor discovery-settings
set discover-interface-list=all
/ip settings
set rp-filter=loose
/interface bridge vlan
add bridge="bridge - VLAN" tagged="bridge - VLAN" vlan-ids=10
add bridge="bridge - VLAN" tagged="bridge - VLAN" vlan-ids=20
add bridge="bridge - VLAN" tagged="bridge - VLAN" vlan-ids=30
add bridge="bridge - VLAN" vlan-ids=1
add bridge="bridge - VLAN" tagged="bridge - VLAN" vlan-ids=40
add bridge="bridge - VLAN" tagged="bridge - VLAN" vlan-ids=50
add bridge="bridge - VLAN" comment="VLAN100 | VPN" tagged="bridge - VLAN" \
vlan-ids=100
/interface detect-internet
set detect-interface-list=WAN internet-interface-list=WAN lan-interface-list=\
LAN wan-interface-list=WAN
/interface l2tp-server server
set allow-fast-path=yes default-profile=l2tp_vpn enabled=yes use-ipsec=\
required
/interface list member
add comment=defconf interface="bridge - VLAN" list=LAN
add interface="ether1 - ISP" list=WAN
/ip address
add address=192.168.8.97/24 interface="ether1 - ISP" network=192.168.8.0
add address=10.1.10.1/24 comment="Admin, Management" interface=VLAN10 \
network=10.1.10.0
add address=10.1.20.1/24 comment="Gaeste, nur Internet" interface=VLAN20 \
network=10.1.20.0
add address=10.1.30.1/24 comment="PCs, Notebooks, Handys, TV intern" \
interface=VLAN30 network=10.1.30.0
add address=10.1.40.1/24 comment=Server interface=VLAN40 network=10.1.40.0
add address=10.1.50.1/24 comment="IOT, Smarthome, unsichere" interface=VLAN50 \
network=10.1.50.0
add address=10.1.1.254/24 interface="bridge - VLAN" network=10.1.1.0
add address=10.1.100.1/24 comment="VPN over L2TP" interface=VLAN100 network=\
10.1.100.0
/ip cloud
set update-time=no
/ip dhcp-relay
add dhcp-server=10.1.1.2 disabled=no interface=VLAN10 local-address=10.1.10.1 \
name=VLAN10-Relay
add dhcp-server=10.1.1.2 disabled=no interface=VLAN20 local-address=10.1.20.1 \
name=VLAN20-Relay
add dhcp-server=10.1.1.2 disabled=no interface=VLAN30 local-address=10.1.30.1 \
name=VLAN30-Relay
add dhcp-server=10.1.1.2 disabled=no interface=VLAN40 local-address=10.1.40.1 \
name=VLAN40-Relay
add dhcp-server=10.1.1.2 disabled=no interface=VLAN50 local-address=10.1.50.1 \
name=VLAN50-Relay
add dhcp-server=10.1.1.2 disabled=no interface=VLAN100 local-address=\
10.1.100.1 name=VLAN100-Relay
/ip dns
set servers=10.1.1.2
/ip firewall address-list
add address=10.1.10.0/24 list=LANs
add address=10.1.20.0/24 list=LANs
add address=10.1.30.0/24 list=LANs
add address=10.1.40.0/24 list=LANs
add address=10.1.50.0/24 list=LANs
add address=10.1.100.0/24 list=LANs
add address=192.168.8.97 list=WANs
add address=10.1.1.2 list="MT Router"
add address=10.1.40.3 comment=RPi-Server1 list=RPi-Server1
add address=0.0.0.0/8 comment="defconf: RFC6890" list=no_forward_ipv4
add address=169.254.0.0/16 comment="defconf: RFC6890" list=no_forward_ipv4
add address=224.0.0.0/4 comment="defconf: multicast" disabled=yes list=\
no_forward_ipv4
add address=255.255.255.255 comment="defconf: RFC6890" list=no_forward_ipv4
add list=ddos-attackers
add list=ddos-targets
add address=127.0.0.0/8 comment="defconf: RFC6890" list=bad_ipv4
add address=192.0.0.0/24 comment="defconf: RFC6890" list=bad_ipv4
add address=192.0.2.0/24 comment="defconf: RFC6890 documentation" list=\
bad_ipv4
add address=198.51.100.0/24 comment="defconf: RFC6890 documentation" list=\
bad_ipv4
add address=203.0.113.0/24 comment="defconf: RFC6890 documentation" list=\
bad_ipv4
add address=240.0.0.0/4 comment="defconf: RFC6890 reserved" list=bad_ipv4
add address=0.0.0.0/8 comment="defconf: RFC6890" list=not_global_ipv4
add address=10.0.0.0/8 comment="defconf: RFC6890" list=not_global_ipv4
add address=100.64.0.0/10 comment="defconf: RFC6890" list=not_global_ipv4
add address=169.254.0.0/16 comment="defconf: RFC6890" list=not_global_ipv4
add address=172.16.0.0/12 comment="defconf: RFC6890" list=not_global_ipv4
add address=192.0.0.0/29 comment="defconf: RFC6890" list=not_global_ipv4
add address=192.168.0.0/16 comment="defconf: RFC6890" disabled=yes list=\
not_global_ipv4
add address=198.18.0.0/15 comment="defconf: RFC6890 benchmark" list=\
not_global_ipv4
add address=255.255.255.255 comment="defconf: RFC6890" list=not_global_ipv4
add address=224.0.0.0/4 comment="defconf: multicast" disabled=yes list=\
bad_src_ipv4
add address=255.255.255.255 comment="defconf: RFC6890" list=bad_src_ipv4
add address=0.0.0.0/8 comment="defconf: RFC6890" list=bad_dst_ipv4
add address=224.0.0.0/4 comment="defconf: RFC6890" disabled=yes list=\
bad_dst_ipv4
add address=10.1.30.3 list=allowed_to_router
add address=10.1.100.3 list=allowed_to_router
add address=10.1.100.3 list=L2TP_allowed
add address=10.1.100.4 list=L2TP_allowed
add address=10.1.40.10 list=UPnPdevices
add address=10.1.30.174 list=UPnPdevices
add address=10.1.1.2 list=UPnPdevices
/ip firewall filter
add action=return chain=detect-ddos dst-limit=32,32,src-and-dst-addresses/10s
add action=add-dst-to-address-list address-list=ddos-targets \
address-list-timeout=10m chain=detect-ddos
add action=add-src-to-address-list address-list=ddos-attackers \
address-list-timeout=10m chain=detect-ddos
add action=return chain=detect-ddos dst-limit=32,32,src-and-dst-addresses/10s \
protocol=tcp tcp-flags=syn,ack
add action=drop chain=input log-prefix=ICMP protocol=icmp
add action=drop chain=input comment=";;; Drop invalid packets" \
connection-state=invalid log-prefix=DropInvalid
add action=drop chain=input comment=";;; Drop new packets not SYN" \
connection-state=new log-prefix=DropNotSyn protocol=tcp tcp-flags=!syn
add action=drop chain=input comment=";;; Drop MSS packets" connection-state=\
new protocol=tcp tcp-mss=!536-65535
add action=drop chain=input comment=";;; Port scan minimized" protocol=tcp \
psd=20,3s,10,2
add action=drop chain=input comment=";;; Anti Smurf attacks" limit=2,2:packet \
protocol=tcp tcp-flags=rst
add action=fasttrack-connection chain=input comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=input comment="defconf: accept established,related" \
connection-state=established,related log-prefix=inputlog
add action=accept chain=input log-prefix=igmplog protocol=igmp
add action=accept chain=input dst-port=500,1701,4500 in-interface=\
"ether1 - ISP" protocol=udp
add action=accept chain=input in-interface="ether1 - ISP" protocol=ipsec-esp
add action=accept chain=input in-interface="ether1 - ISP" protocol=ipsec-ah
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN log-prefix=NOTLAN
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=drop chain=forward comment="defconf: drop bad forward IPs" \
src-address-list=no_forward_ipv4
add action=drop chain=forward comment="defconf: drop bad forward IPs" \
dst-address-list=no_forward_ipv4 log-prefix=DROPIP
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment="defconf: accept established,related" \
connection-state=established,related log-prefix=Logger
add action=accept chain=forward protocol=igmp
add action=accept chain=forward comment=\
"LAN -> WAN | RPi-Services Zugriff auf WAN" out-interface="ether1 - ISP" \
src-address=10.1.1.2
add action=accept chain=forward dst-address=10.1.1.2 in-interface=\
"ether1 - ISP"
add action=accept chain=forward comment=\
"VPN -> WAN | Akzeptiere VPN ins Internet -> PPP myvpn" out-interface=\
"ether1 - ISP" src-address-list=L2TP_allowed
add action=accept chain=forward out-interface="bridge - VLAN" \
src-address-list=L2TP_allowed
add action=accept chain=forward comment="VLAN 30 ----- LAN -> BRIDGE | Akzepti\
ere Traffic von VLAN30 zur Bridge, zum ISP, von der Bridge und in VLAN40" \
in-interface=VLAN30 log-prefix=Bridgelog30 out-interface="bridge - VLAN"
add action=accept chain=forward in-interface=VLAN30 out-interface=\
"ether1 - ISP"
add action=accept chain=forward in-interface="bridge - VLAN" out-interface=\
VLAN30
add action=accept chain=forward in-interface=VLAN30 out-interface=VLAN40
add action=accept chain=forward comment="VLAN 40 ----- BRIDGE -> VLAN40 | Akze\
ptiere Zugriff auf die RPi-Server aus dem LAN + WAN" in-interface=\
"bridge - VLAN" out-interface=VLAN40
add action=accept chain=forward in-interface=VLAN40 out-interface=\
"bridge - VLAN"
add action=accept chain=forward in-interface=VLAN40 out-interface=\
"ether1 - ISP"
add action=accept chain=forward in-interface=VLAN40 out-interface=VLAN30
add action=accept chain=forward comment=\
"VLAN 50 ----- BRIDGE -> VLAN50 | Akzeptiere Zugriff auf Homematic" \
in-interface="bridge - VLAN" out-interface=VLAN50
add action=accept chain=forward in-interface=VLAN50 out-interface=\
"bridge - VLAN"
add action=accept chain=forward in-interface=VLAN40 out-interface=VLAN50
add action=accept chain=forward comment=\
"L2TP ----- LAN -> VLAN40 | Akzeptiere Zugriff auf Server" log-prefix=\
l2tplog out-interface=VLAN40 src-address-list=L2TP_allowed
add action=drop chain=forward comment="defconf: drop all the rest" log=yes \
log-prefix=droprest
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
out-interface="ether1 - ISP"
add action=masquerade chain=srcnat comment="defconf: masquerade" dst-address=\
10.1.1.2
add action=dst-nat chain=dstnat in-interface="ether1 - ISP" protocol=tcp \
to-addresses=10.1.1.2
/ip firewall raw
add action=drop chain=prerouting dst-address-list=ddos-targets \
src-address-list=ddos-attackers
add action=accept chain=prerouting comment=\
"defconf: enable for transparent firewall" disabled=yes log-prefix=Logger
add action=accept chain=prerouting comment="defconf: accept DHCP discover" \
dst-address=255.255.255.255 dst-port=67 in-interface-list=LAN protocol=\
udp src-address=0.0.0.0 src-port=68
add action=drop chain=prerouting comment="defconf: drop bogon IP's" \
src-address-list=bad_ipv4
add action=drop chain=prerouting comment="defconf: drop bogon IP's" \
dst-address-list=bad_ipv4
add action=drop chain=prerouting comment="defconf: drop bogon IP's" \
src-address-list=bad_src_ipv4
add action=drop chain=prerouting comment="defconf: drop bogon IP's" \
dst-address-list=bad_dst_ipv4
add action=drop chain=prerouting comment="defconf: drop non global from WAN" \
in-interface-list=WAN src-address-list=not_global_ipv4
add action=drop chain=prerouting comment=\
"defconf: drop forward to local lan from WAN" dst-address=10.1.1.0/24 \
in-interface-list=WAN
add action=drop chain=prerouting comment=\
"defconf: drop local if not from default IP range" in-interface-list=LAN \
src-address=!10.1.1.0/24
add action=drop chain=prerouting comment="defconf: drop bad UDP" port=0 \
protocol=udp
add action=jump chain=prerouting comment="defconf: jump to ICMP chain" \
jump-target=icmp4 protocol=icmp
add action=jump chain=prerouting comment="defconf: jump to TCP chain" \
jump-target=bad_tcp protocol=tcp
add action=accept chain=prerouting comment=\
"defconf: accept everything else from LAN" in-interface-list=LAN
add action=accept chain=prerouting comment=\
"defconf: accept everything else from WAN" in-interface-list=WAN
add action=accept chain=prerouting comment=\
"defconf: accept everything else from LAN" src-address-list=LANs
add action=accept chain=prerouting comment=\
"defconf: accept everything else from LAN" dst-address-list=LANs
add action=drop chain=prerouting comment="defconf: drop the rest" log-prefix=\
droprest
add action=drop chain=bad_tcp comment="defconf: TCP flag filter" protocol=tcp \
tcp-flags=!fin,!syn,!rst,!ack
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=fin,syn
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=fin,rst
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=fin,!ack
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=fin,urg
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=syn,rst
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=rst,urg
add action=drop chain=bad_tcp comment="defconf: TCP port 0 drop" port=0 \
protocol=tcp
add action=accept chain=icmp4 comment="defconf: echo reply" icmp-options=0:0 \
limit=5,10:packet protocol=icmp
add action=accept chain=icmp4 comment="defconf: net unreachable" \
icmp-options=3:0 protocol=icmp
add action=accept chain=icmp4 comment="defconf: host unreachable" \
icmp-options=3:1 protocol=icmp
add action=accept chain=icmp4 comment="defconf: protocol unreachable" \
icmp-options=3:2 protocol=icmp
add action=accept chain=icmp4 comment="defconf: port unreachable" \
icmp-options=3:3 protocol=icmp
add action=accept chain=icmp4 comment="defconf: fragmentation needed" \
icmp-options=3:4 protocol=icmp
add action=accept chain=icmp4 comment="defconf: echo" icmp-options=8:0 limit=\
5,10:packet protocol=icmp
add action=accept chain=icmp4 comment="defconf: time exceeded " icmp-options=\
11:0-255 protocol=icmp
add action=drop chain=icmp4 comment="defconf: drop other icmp" protocol=icmp
/ip ipsec identity
add generate-policy=port-override my-id=fqdn:vpn.meinedomain.de peer=DynamicIP \
remote-id=fqdn:vpn.meinedomain.de
/ip ipsec policy
set 0 dst-address=0.0.0.0/0 src-address=0.0.0.0/0
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.8.1 \
pref-src="" routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh port=2200
set api disabled=yes
set api-ssl disabled=yes
/ip upnp
set enabled=yes show-dummy-rule=no
/ip upnp interfaces
add interface="ether1 - ISP" type=external
add interface="bridge - VLAN" type=internal
/ipv6 firewall filter
add action=drop chain=forward
/ppp secret
add comment="VPN | Tommy" local-address=10.1.100.1 name=vpnuser1 profile=\
l2tp_vpn remote-address=10.1.100.3 service=l2tp
add comment="VPN | Tommy" local-address=10.1.100.1 name=vpnuser2 profile=\
l2tp_vpn remote-address=10.1.100.4 service=l2tp
/radius
add address=10.1.1.2 disabled=yes service=wireless src-address=10.1.1.1
/routing igmp-proxy
set quick-leave=yes
/routing igmp-proxy interface
add alternative-subnets=10.1.30.0/24,10.1.100.0/24 interface=VLAN40 upstream=\
yes
add interface=VLAN30
add interface=VLAN100
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name="MikroTik Switch"
/system logging
add disabled=yes topics=igmp-proxy
/system ntp client
set enabled=yes
/system ntp server
set enabled=yes
/system ntp client servers
add address=0.pool.ntp.org
add address=1.pool.ntp.org
add address=2.pool.ntp.org
add address=3.pool.ntp.org
/system routerboard settings
set boot-os=router-os
/tool bandwidth-server
set enabled=no
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=none
/tool mac-server ping
set enabled=noBitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 7898115862
Url: https://administrator.de/forum/mikrotik-firmware-7-9-und-nichts-geht-mehr-7898115862.html
Ausgedruckt am: 15.07.2025 um 12:07 Uhr
13 Kommentare
Neuester Kommentar
Dein Konfig Posting hattest du ja leider vorab aus dem original Thread gelöscht. 
Da steht auch der Grund des Warum bzw. Setup Fehler in deiner Konfig.
Fehler in deiner MT Konfig
Da steht auch der Grund des Warum bzw. Setup Fehler in deiner Konfig.
Fehler in deiner MT Konfig
dass ich keine Verbindung mehr mit L2TP/IPsec aufbauen kann vom Smartphone aus
Halte dich an das Mikrotik L2TP VPN Tutorial dann sollte auch das schnell wieder klappen! und nicht auf die Bridge, steht ja auch ganz ausführlich in rot da.
Richtig denn WAS gilt immer im Mikrotik VLAN Umfeld??? Richtig: Keine IP Adresse oder IP Konfigs auf dem Bridge Interface!! 😉wäre eine dauerhafte Anbindung des MT an einen VPN-Anbieter.
Davon kann man dir nur dringenst abraten. Die sind durch die Bank alle unseriös und haben die Unternehmenssitze in totalitären oder diktatorischen Staaten. Damit erweist man sich einen datenschutztechnischen Bärendienst. Ein warnendes Beispiel findest du u.a. hier.
TOR Browser ist ggf. dann der richtige Weg?!
heise.de/ratgeber/Darknet-Tor-Browser-auf-PC-und-Smartphone-einr ...
heise.de/ratgeber/Tor-Browser-als-sicherer-Zweitbrowser-6540983. ...

Infos zu IKEv2 Alternativen findest du, wie immer, hier:
IKEv2 VPN Server für Windows und Apple Clients mit Raspberry Pi
IPsec IKEv2 VPN für mobile Benutzer auf der pfSense oder OPNsense Firewall einrichten
heise.de/ratgeber/Darknet-Tor-Browser-auf-PC-und-Smartphone-einr ...
heise.de/ratgeber/Tor-Browser-als-sicherer-Zweitbrowser-6540983. ...
Mein Smartphone zeigt mir in roter Schrift bei L2TP/IPSec
Das kannst du ignorieren, denn im Hintergrund werkelt da ja IPsec mit AES256 was derzeit als hinreichend sicher gilt! Es geht bei der meldung wohl primär um das fehlende Zertifikat was im Heimbereich aber tolerabel ist je nachdem wieviel Sicherheit man für sich selbst haben möchte und als Maßstab bestimmt. Infos zu IKEv2 Alternativen findest du, wie immer, hier:
IKEv2 VPN Server für Windows und Apple Clients mit Raspberry Pi
IPsec IKEv2 VPN für mobile Benutzer auf der pfSense oder OPNsense Firewall einrichten
Smartphone VPN Clients machen oftmals von sich aus ein Gateway Redirect, sprich leiten alles in den Tunnel. Das ist aber immer Smartphone bzw. Client spezifisch!
Bei Apple ist es Standard aber bei anderen Clients muss das ggf. explizit aktiviert sein wie z.B. auch am Windows Client:
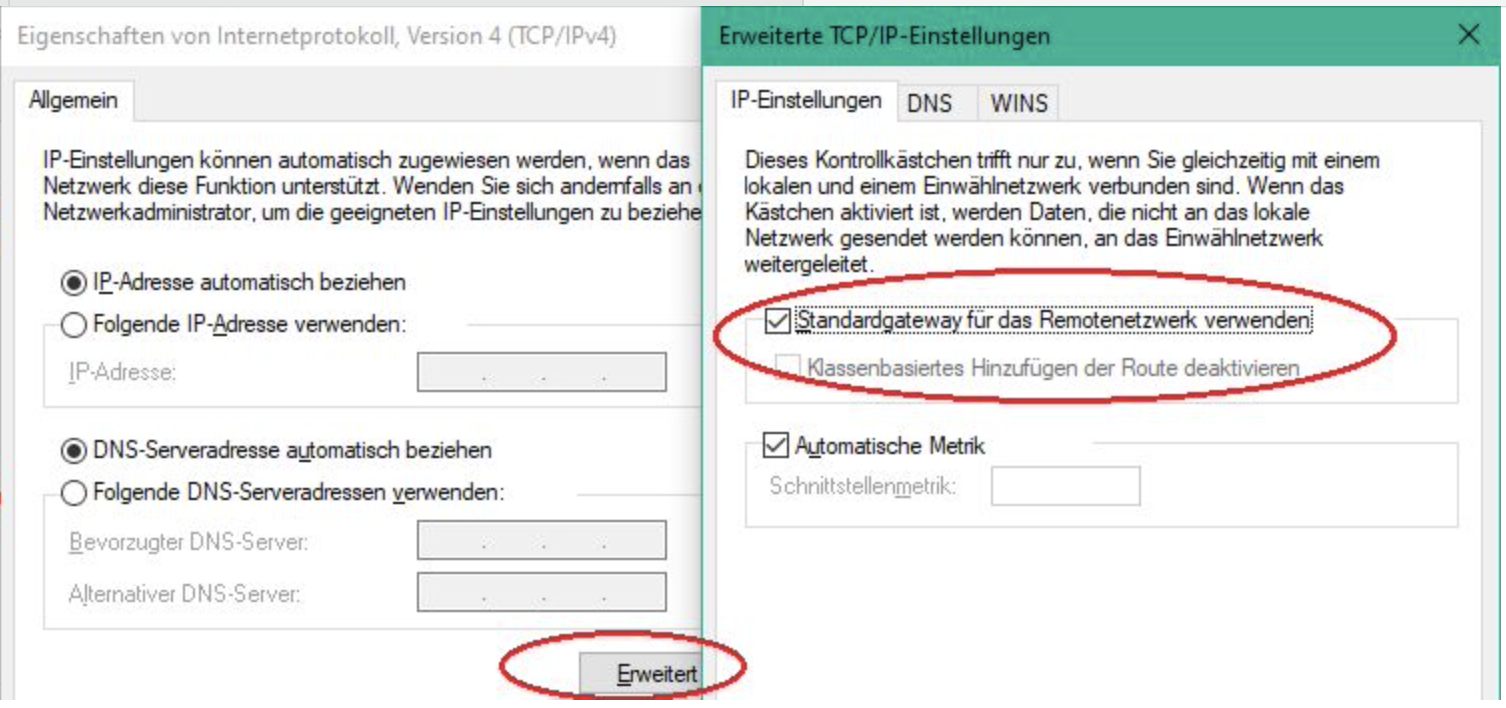 Es ist also keineswegs immer nur dein Router allein!
Es ist also keineswegs immer nur dein Router allein! 
Hilfreich zum Troubleshooting ist eine Tool App für beide Plattformen wie die bekannten HE.NET Tools die dir die Routing Table bei aktivem VPN Client anzeigen.
Bei Apple ist es Standard aber bei anderen Clients muss das ggf. explizit aktiviert sein wie z.B. auch am Windows Client:

Hilfreich zum Troubleshooting ist eine Tool App für beide Plattformen wie die bekannten HE.NET Tools die dir die Routing Table bei aktivem VPN Client anzeigen.
Wenn es das denn nun war bitte deinen Thread hier dann auch als erledigt schliessen!