Mikrotik VLAN Clients können nicht kommunizieren "?"
Hallo Mikrotik-Profis,
von Euch habe ich schon viele Hilfen; Tipps und Tricks bekommen, dafür schon mal vielen Dank!
Jetzt möchte ich mich noch einmal an Euch wenden.
Das Problem:
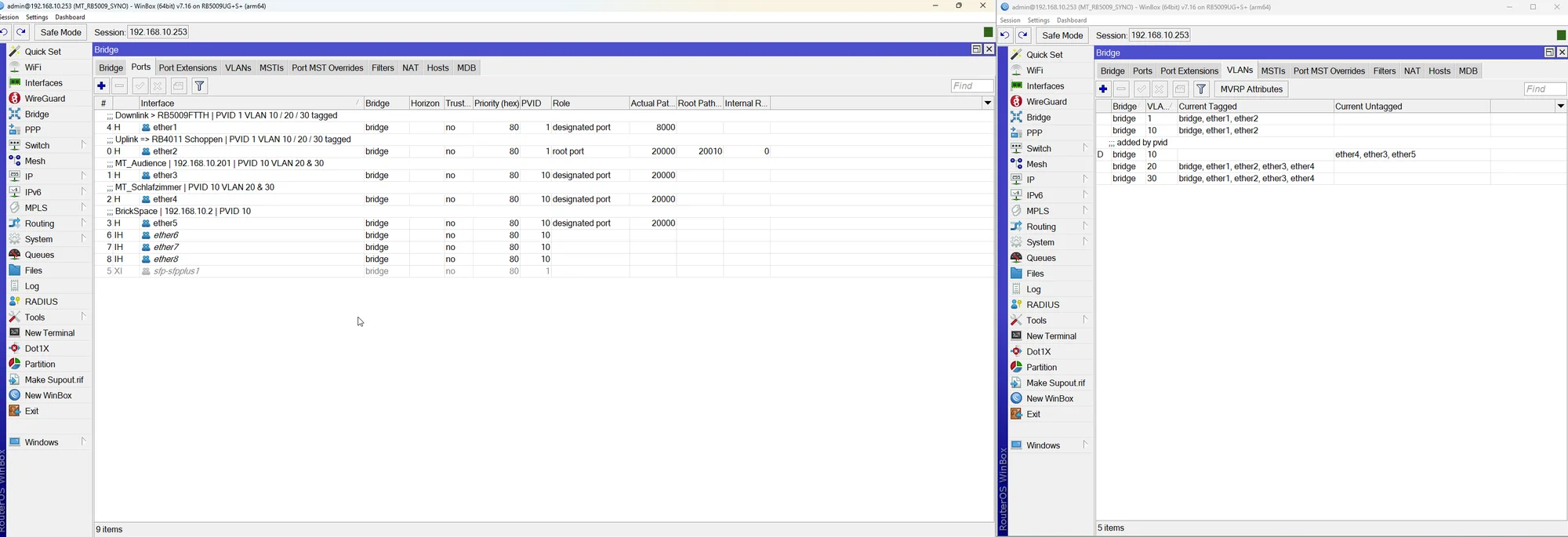
Nach dem ich drei VLANs eingerichtet habe, Privat10/Gast20/IoT30, bekomme ich meine Kameras, sowie das Backup-Target nicht mehr mit der Synology (DS718+) verbunden.
Die Kameras sowie das BackUp-Target (DS112+) werden gefunden und angezeigt, sobald es um die Authentifizierung geht, komme ich nicht weiter.
Die Geräte sind im Privaten VLAN 10, können angepingt werden und sind über die IP per Browser erreichbar und funktionieren fehlerfrei.
Das VLAN-Setup wurde nach Anleitung/Anweisung von aqui und commodity erstellt.
Die Sache mit den dynamischen Zuweisungen für die Wifi-APs bekomme ich nicht hin, daher bitte nicht wundern, sieht etwas wild aus.
Soweit ich es gelesen und verstanden habe, darf bei Verwendung von VLANs die Bridge keine IP haben.
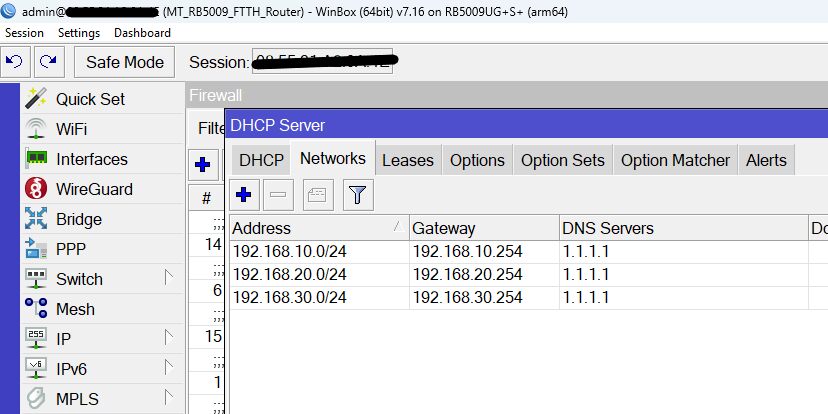
Jedes VLAN hat eine separate IP und DCHP-Server.
Klappt auch alles super, vom Gast und IoT-Netzt kann man nicht auf die Synos, etc. zugreifen.
Das Setup:
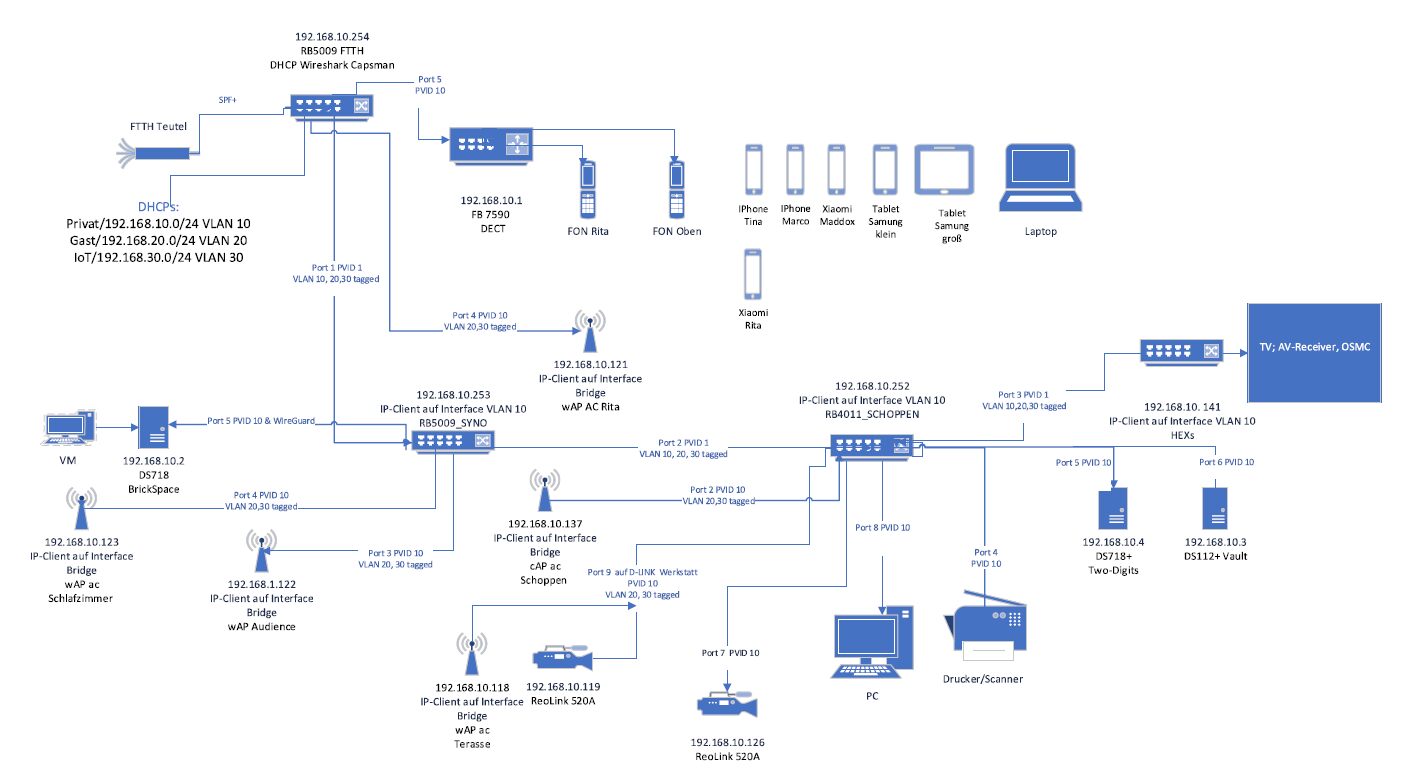
RB5009 (FTTH), ROS 7.16:
=>Router, FTTH, DHCP; CAPsMAN; WireGuard; VLAN 10/20/30; Wifi-AP, FritzBox(DECT), Uplink zu RB5009 Syno)
RB5009 (Syno), ROS 7.16:
=> Switch, DS718+, 2x Wifi-AP und Uplink zu RB4011(Schoppen)
RB4011 (Schoppen)ROS 7.16:
=> Switch für DS718+ (Stby-Gerät), DS112+ (BackUpTarget), Drucker, IP-Telefon, Reo-Link Cam, Uplink zum HEXs (dieser wird nicht weiter betrachtet)
etwas viel....ok....
Könnt Ihr erkennen, was ich das falsch eingestellt habe?
Grüße
Marco
von Euch habe ich schon viele Hilfen; Tipps und Tricks bekommen, dafür schon mal vielen Dank!
Jetzt möchte ich mich noch einmal an Euch wenden.
Das Problem:
Nach dem ich drei VLANs eingerichtet habe, Privat10/Gast20/IoT30, bekomme ich meine Kameras, sowie das Backup-Target nicht mehr mit der Synology (DS718+) verbunden.
Die Kameras sowie das BackUp-Target (DS112+) werden gefunden und angezeigt, sobald es um die Authentifizierung geht, komme ich nicht weiter.
Die Geräte sind im Privaten VLAN 10, können angepingt werden und sind über die IP per Browser erreichbar und funktionieren fehlerfrei.
Das VLAN-Setup wurde nach Anleitung/Anweisung von aqui und commodity erstellt.
Die Sache mit den dynamischen Zuweisungen für die Wifi-APs bekomme ich nicht hin, daher bitte nicht wundern, sieht etwas wild aus.
Soweit ich es gelesen und verstanden habe, darf bei Verwendung von VLANs die Bridge keine IP haben.
Jedes VLAN hat eine separate IP und DCHP-Server.
Klappt auch alles super, vom Gast und IoT-Netzt kann man nicht auf die Synos, etc. zugreifen.
Das Setup:
RB5009 (FTTH), ROS 7.16:
=>Router, FTTH, DHCP; CAPsMAN; WireGuard; VLAN 10/20/30; Wifi-AP, FritzBox(DECT), Uplink zu RB5009 Syno)
/interface bridge
add admin-mac=08:xxxxxxxxE auto-mac=no comment=defconf name=bridge \
vlan-filtering=yes
/interface ethernet
set [ find default-name=ether1 ] comment=\
"Uplink => RB5009 SYNO (akt. HEXs) | VLAN 10 / 20 / 30 "
set [ find default-name=ether4 ] comment=\
"Uplink MT_RITA | 192.168.178.4 | VLAN 10 / 20 / 30 "
set [ find default-name=ether5 ] comment="Uplink => FritzBox => DECT only"
set [ find default-name=ether8 ] comment=\
"Direkt-LAN zum Schoppen Netztwerkdose 1.1"
set [ find default-name=sfp-sfpplus1 ] auto-negotiation=no speed=\
1G-baseT-full
/interface wireguard
add comment="F\FCr BrickSpace DS718+|192.168.10.2" listen-port=13231 mtu=1420 \
name=wg0
/interface vlan
add interface=bridge name="vlan10 Privat" vlan-id=10
add interface=bridge name="vlan20 Gast" vlan-id=20
add interface=bridge name="vlan30 IoT" vlan-id=30
add interface=sfp-sfpplus1 name=vlan800 vlan-id=800
/interface pppoe-client
add add-default-route=yes allow=pap,mschap2 disabled=no interface=vlan800 \
name=Teutel-FTTH use-peer-dns=yes user=V000782
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface lte apn
set [ find default=yes ] ip-type=ipv4 use-network-apn=no
/interface wifi channel
add band=2ghz-n disabled=no frequency=2300-7300 name=channel1 width=20mhz
add band=5ghz-ac disabled=no frequency=2300-7300 name=channel2 \
skip-dfs-channels=disabled width=20/40/80mhz
/interface wifi datapath
add bridge=bridge disabled=yes name=WiFi
add bridge=bridge disabled=no name=Privat
add bridge=bridge disabled=no name=Gast
add bridge=bridge disabled=no name=IoT
/interface wifi security
add authentication-types=wpa-psk disabled=no group-encryption=ccmp name=\
Privat
add authentication-types=wpa-psk,wpa2-psk disabled=no group-encryption=ccmp \
name=Gast
add authentication-types=wpa-psk,wpa2-psk disabled=no group-encryption=ccmp \
name=IoT
/interface wifi configuration
add channel=channel1 channel.band=2ghz-n .skip-dfs-channels=disabled .width=\
20mhz country="United States" datapath=WiFi datapath.bridge=bridge \
.interface-list=all disabled=no mode=ap name=2,4 security=Privat \
security.authentication-types=wpa-psk .encryption="" ssid="Noxon Access"
add channel=channel2 channel.band=5ghz-ac .skip-dfs-channels=disabled .width=\
20/40/80mhz country="United States" datapath=WiFi disabled=no mode=ap \
name=5.0 security=Privat security.authentication-types=wpa2-psk ssid=\
W-Lan
add channel=channel2 channel.band=5ghz-ac .skip-dfs-channels=disabled .width=\
20/40/80mhz country="United States" datapath=WiFi disabled=no mode=ap \
name=5.1 security=Privat security.authentication-types=wpa2-psk ssid=\
W-Lan
add channel=channel1 channel.band=2ghz-n .skip-dfs-channels=disabled .width=\
20mhz country="United States" datapath=Gast datapath.bridge=bridge \
disabled=no mode=ap name="WiFi 2.4 Gast" security=Gast \
security.authentication-types=wpa-psk .encryption="" ssid="WiFi 2.4 Gast"
add channel=channel2 channel.band=5ghz-n .skip-dfs-channels=disabled .width=\
20/40/80mhz country="United States" datapath=Gast disabled=no mode=ap \
name="WiFi 5.0 Gast" security=Gast security.authentication-types=wpa-psk \
.encryption="" ssid="WiFi 5.0 Gast"
add channel=channel1 channel.band=2ghz-n .skip-dfs-channels=disabled .width=\
20mhz country="United States" datapath=IoT datapath.bridge=bridge \
.client-isolation=yes disabled=no mode=ap name=IoT security=IoT \
security.authentication-types=wpa-psk .encryption="" ssid=IoT
/interface wifi
add channel=channel1 channel.band=2ghz-n .frequency=2300-7300 .width=20mhz \
configuration=2,4 configuration.mode=ap datapath=WiFi disabled=no name=\
"cap-Audience 2,4" radio-mac=2C:C8:1B:77:D2:D5 security=Privat \
security.authentication-types=wpa-psk
add channel.frequency=2300-7300 configuration="WiFi 2.4 Gast" \
configuration.mode=ap disabled=no mac-address=2E:C8:1B:77:D2:D5 \
master-interface="cap-Audience 2,4" name="cap-Audience 2,4 Gast"
add channel=channel2 channel.frequency=2300-7300 configuration=5.0 \
configuration.mode=ap datapath=WiFi disabled=no name="cap-Audience 5.0" \
radio-mac=2C:C8:1B:77:D2:D7 security=Privat \
security.authentication-types=wpa-psk,wpa2-psk
add channel=channel2 channel.frequency=2300-7300 configuration=5.1 \
configuration.mode=ap datapath=WiFi disabled=no name="cap-Audience 5.1" \
radio-mac=2C:C8:1B:77:D2:D6 security=Privat \
security.authentication-types=wpa-psk,wpa2-psk
add channel.frequency=2300-7300 configuration=IoT configuration.mode=ap \
datapath=IoT disabled=no mac-address=2E:C8:1B:77:D2:D6 master-interface=\
"cap-Audience 2,4" name="cap-Audience IoT"
add channel.frequency=2300-7300 configuration="WiFi 5.0 Gast" \
configuration.mode=ap datapath=Gast disabled=no mac-address=\
2E:C8:1B:77:D2:D7 master-interface="cap-Audience 5.0" name=\
"cap-Audience Wifi 5.0 Gast"
add channel=channel1 channel.band=2ghz-n .frequency=2300-7300 .width=20mhz \
configuration=2,4 configuration.mode=ap datapath=WiFi disabled=no mtu=\
1500 name="cap-Rita 2,4" radio-mac=78:9A:18:9E:63:AE security=Privat \
security.authentication-types=wpa-psk
add channel.frequency=2300-7300 configuration="WiFi 2.4 Gast" \
configuration.mode=ap disabled=no mac-address=7A:9A:18:9E:63:AE \
master-interface="cap-Rita 2,4" name="cap-Rita 2,4 Gast"
add channel=channel2 channel.frequency=2300-7300 configuration=5.0 \
configuration.mode=ap datapath=WiFi disabled=no name="cap-Rita 5.0" \
radio-mac=78:9A:18:9E:63:AF security=Privat \
security.authentication-types=wpa-psk,wpa2-psk
add channel.frequency=2300-7300 configuration=IoT configuration.mode=ap \
disabled=no mac-address=7A:9A:18:9E:63:B0 master-interface="cap-Rita 2,4" \
name="cap-Rita IoT"
add channel.frequency=2300-7300 configuration="WiFi 5.0 Gast" \
configuration.mode=ap disabled=no mac-address=7A:9A:18:9E:63:AF \
master-interface="cap-Rita 5.0" name="cap-Rita Wifi 5.0 Gast"
add channel.frequency=2300-7300 configuration=2,4 configuration.mode=ap \
disabled=no name="cap-Schalfzimmer 2,4" radio-mac=78:9A:18:9E:5F:82
add channel.frequency=2300-7300 configuration="WiFi 2.4 Gast" \
configuration.mode=ap datapath=Gast disabled=no mac-address=\
7A:9A:18:9E:5F:82 master-interface="cap-Schalfzimmer 2,4" name=\
"cap-Schalfzimmer 2,4 Gast"
add channel.frequency=2300-7300 configuration=5.0 configuration.mode=ap \
disabled=no name="cap-Schlafzimmer 5.0" radio-mac=78:9A:18:9E:5F:83
add channel.frequency=2300-7300 configuration=IoT configuration.mode=ap \
disabled=no mac-address=7A:9A:18:9E:5F:84 master-interface=\
"cap-Schalfzimmer 2,4" name="cap-Schlafzimmer IoT"
add channel.frequency=2300-7300 configuration="WiFi 5.0 Gast" \
configuration.mode=ap disabled=no mac-address=7A:9A:18:9E:5F:83 \
master-interface="cap-Schlafzimmer 5.0" name=\
"cap-Schlafzimmer Wifi 5.0 Gast"
add channel.frequency=2300-7300 configuration=2,4 configuration.mode=ap \
disabled=no name="cap-Schoppen 2,4" radio-mac=DC:2C:6E:1B:87:04
add channel.frequency=2300-7300 configuration="WiFi 2.4 Gast" \
configuration.mode=ap disabled=no mac-address=DE:2C:6E:1B:87:04 \
master-interface="cap-Schoppen 2,4" name="cap-Schoppen 2,4 Gast"
add channel.frequency=2300-7300 configuration=5.0 configuration.mode=ap \
disabled=no name="cap-Schoppen 5.0" radio-mac=DC:2C:6E:1B:87:05
add channel.frequency=2300-7300 configuration="WiFi 5.0 Gast" \
configuration.mode=ap disabled=no mac-address=DE:2C:6E:1B:87:05 \
master-interface="cap-Schoppen 5.0" name="cap-Schoppen 5.0 Gast"
add channel.frequency=2300-7300 configuration=IoT configuration.mode=ap \
disabled=no mac-address=DE:2C:6E:1B:87:06 master-interface=\
"cap-Schoppen 2,4" name="cap-Schoppen IoT"
add channel.frequency=2300-7300 configuration=2,4 configuration.mode=ap \
disabled=no name="cap-Terrasse 2,4" radio-mac=08:55:31:3D:6E:F8
add channel.frequency=2300-7300 configuration="WiFi 2.4 Gast" \
configuration.mode=ap disabled=no mac-address=0A:55:31:3D:6E:F8 \
master-interface="cap-Terrasse 2,4" name="cap-Terrasse 2,4 Gast"
add channel.frequency=2300-7300 configuration=5.0 configuration.mode=ap \
disabled=no name="cap-Terrasse 5.0" radio-mac=08:55:31:3D:6E:F9
add channel.frequency=2300-7300 configuration="WiFi 5.0 Gast" \
configuration.mode=ap disabled=no mac-address=0A:55:31:3D:6E:F9 \
master-interface="cap-Terrasse 5.0" name="cap-Terrasse 5.0 Gast"
add channel.frequency=2300-7300 configuration=IoT configuration.mode=ap \
disabled=no mac-address=0A:55:31:3D:6E:FB master-interface=\
"cap-Terrasse 2,4" name="cap-Terrasse IoT"
/ip pool
add name=Pool_LAN ranges=192.168.178.100-192.168.178.199
add name=Privat ranges=192.168.10.100-192.168.10.199
add name=Gast ranges=192.168.20.99-192.168.20.199
add name=IoT ranges=192.168.30.99-192.168.30.199
/ip dhcp-server
add address-pool=Privat interface="vlan10 Privat" name=dhcp_Privat
add address-pool=Gast interface="vlan20 Gast" name=dhcp_Gast
add address-pool=IoT interface="vlan30 IoT" name=dhcp_IoT
/ip smb users
set [ find default=yes ] disabled=yes
/queue type
add kind=pcq name=pcq-download-gastnetz pcq-classifier=dst-address pcq-rate=\
5M
/routing bgp template
set default disabled=no output.network=bgp-networks
/routing table
add disabled=no fib name=Wireguard
/disk settings
set auto-media-interface=bridge auto-media-sharing=yes auto-smb-sharing=yes
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4 pvid=10
add bridge=bridge comment=defconf interface=ether5 pvid=10
add bridge=bridge comment=defconf interface=ether6
add bridge=bridge comment=defconf interface=ether7
add bridge=bridge comment=defconf interface=ether8 pvid=10
add bridge=bridge comment=defconf interface=ether1
add bridge=bridge interface="vlan10 Privat" pvid=10
add bridge=bridge interface="vlan20 Gast" pvid=20
add bridge=bridge interface="vlan30 IoT" pvid=30
/ip firewall connection tracking
set udp-timeout=10s
/ip neighbor discovery-settings
set discover-interface-list=all
/ip settings
set max-neighbor-entries=8192
/interface bridge vlan
add bridge=bridge tagged=bridge,ether1 untagged=ether8,ether4 vlan-ids=10
add bridge=bridge tagged=bridge,ether1,ether8,ether4 vlan-ids=20
add bridge=bridge tagged=bridge,ether1,ether8,ether4 vlan-ids=30
add bridge=bridge untagged=ether5 vlan-ids=10
add bridge=bridge vlan-ids=20
add bridge=bridge vlan-ids=30
/interface list member
add interface=Teutel-FTTH list=WAN
add interface="vlan10 Privat" list=LAN
add interface="vlan20 Gast" list=LAN
add interface="vlan30 IoT" list=LAN
add interface=ether1 list=LAN
add interface=ether2 list=LAN
add interface=ether3 list=LAN
add interface=ether4 list=LAN
add interface=ether5 list=LAN
add interface=ether6 list=LAN
add interface=ether7 list=LAN
add interface=ether8 list=LAN
add interface=bridge list=LAN
/interface ovpn-server server
set auth=sha1,md5
/interface wifi access-list
add action=accept disabled=yes interface=any signal-range=-80..120
add action=reject disabled=yes interface=any signal-range=-120..-81
/interface wifi cap
set caps-man-addresses="" discovery-interfaces=""
/interface wifi capsman
set ca-certificate=auto certificate=auto enabled=yes interfaces=\
"vlan10 Privat" package-path="" require-peer-certificate=no \
upgrade-policy=none
/interface wireguard peers
add allowed-address=0.0.0.0/0 comment=PRIMARY endpoint-address=\
wg1.connect2any.net endpoint-port=xxxxx interface=wg0 name=peer1 \
persistent-keepalive=1m public-key=\
"xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"
/ip address
add address=192.168.178.254/24 comment=defconf disabled=yes interface=bridge \
network=192.168.178.0
add address=10.0.0.56 interface=wg0 network=10.0.0.0
add address=192.168.10.254/24 interface="vlan10 Privat" network=192.168.10.0
add address=192.168.20.254/24 interface="vlan20 Gast" network=192.168.20.0
add address=192.168.30.254/24 interface="vlan30 IoT" network=192.168.30.0
/ip arp
add address=192.168.10.201 interface="vlan10 Privat" mac-address=\
xxxxx
add address=192.168.10.202 interface="vlan10 Privat" mac-address=\
xxxxx
add address=192.168.10.203 interface="vlan10 Privat" mac-address=\
xxxxxx
add address=192.168.10.204 interface="vlan10 Privat" mac-address=\
xxxxx
add address=192.168.10.205 interface="vlan10 Privat" mac-address=\
xxxxx
add address=192.168.10.100 interface="vlan10 Privat" mac-address=\
9xxxxx
add address=192.168.10.1 interface="vlan10 Privat" published=yes
add address=192.168.10.2 interface="vlan10 Privat" published=yes
/ip dhcp-server network
add address=192.168.10.0/24 dns-server=1.1.1.1 gateway=192.168.10.254 \
netmask=24
add address=192.168.20.0/24 dns-server=1.1.1.1 gateway=192.168.20.254 \
netmask=24
add address=192.168.30.0/24 dns-server=1.1.1.1 gateway=192.168.30.254 \
netmask=24
/ip dns
set allow-remote-requests=yes servers=1.1.1.1
/ip dns static
add address=192.168.88.1 comment=defconf name=router.lan type=A
/ip firewall filter
add action=fasttrack-connection chain=forward comment="Fasttrack DNS UPD" \
dst-port=53 hw-offload=yes protocol=udp
add action=fasttrack-connection chain=forward comment="Fasttrack DNS UPD" \
dst-address-list=192.168.10.254 dst-port=53 hw-offload=yes protocol=udp
add action=fasttrack-connection chain=forward comment="Fasttrack DNS TCP" \
dst-port=53 hw-offload=yes protocol=tcp
add action=fasttrack-connection chain=input comment="Fasttrack DNS TCP" \
dst-address-list=192.168.10.254 dst-port=53 hw-offload=yes protocol=tcp
add action=drop chain=input comment="WAN => Firewall => Ping blockieren" \
in-interface=Teutel-FTTH protocol=icmp
add action=accept chain=input comment="Aufgebaute Verbindungen erlauben" \
connection-state=established,related
add action=accept chain=input comment="LAN => Firewall => Zugriff erlaubt" \
in-interface=bridge
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment=\
"Allg. Verbindungen ohne Grund werden gedroppt"
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=accept chain=input in-interface=sfp-sfpplus1 protocol=icmp
add action=accept chain=input comment="VLAN 10 zur Firewall Ping erlauben" \
in-interface="vlan10 Privat" protocol=icmp
add action=accept chain=forward comment="Ping von Privat zu Gast" \
in-interface="vlan10 Privat" out-interface="vlan20 Gast" protocol=icmp
add action=accept chain=forward comment="Ping von Gast zu IoT" in-interface=\
"vlan10 Privat" out-interface="vlan30 IoT" protocol=icmp
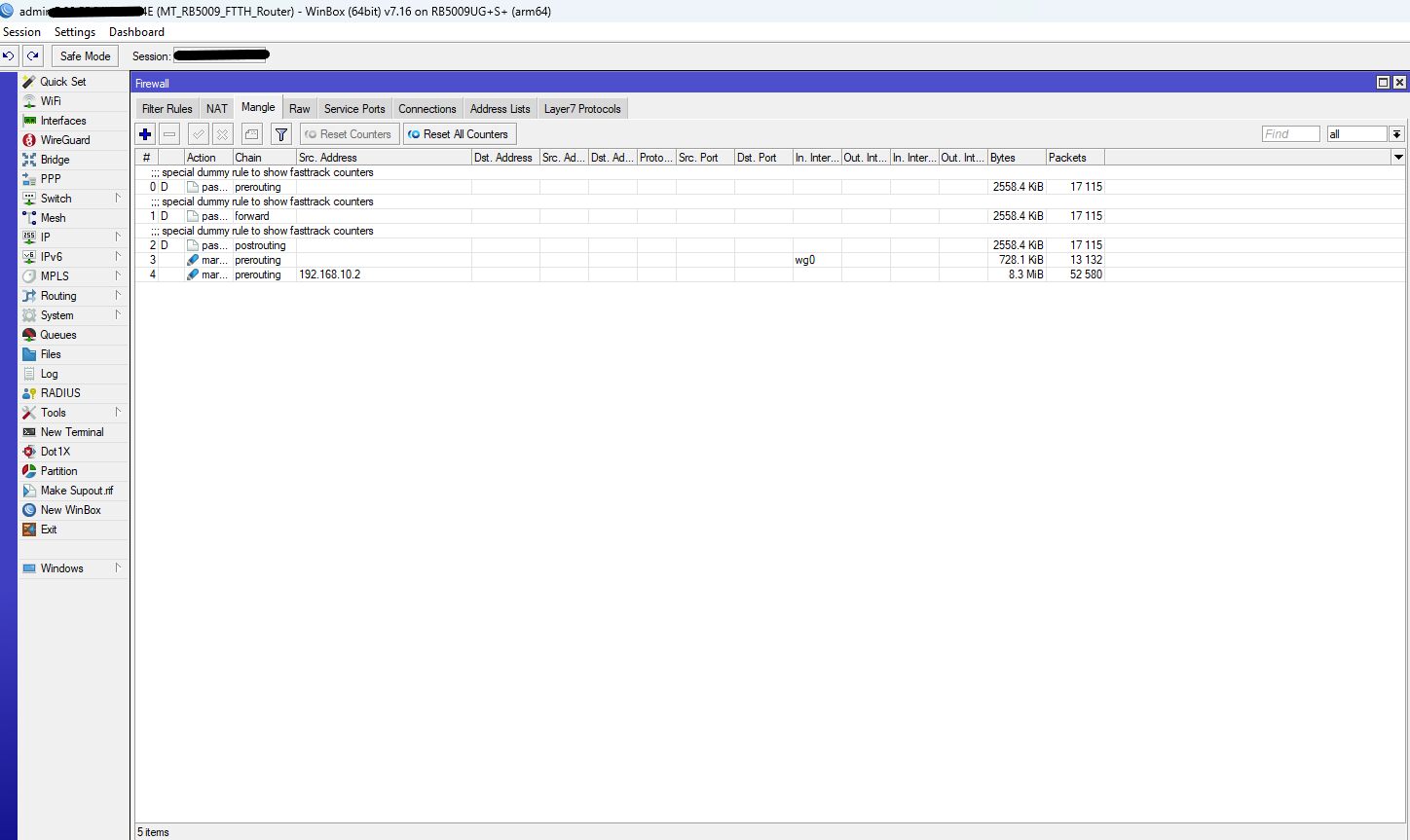
/ip firewall mangle
add action=mark-connection chain=prerouting connection-mark=no-mark \
in-interface=wg0 new-connection-mark=wireguard passthrough=yes
add action=mark-connection chain=prerouting connection-mark=no-mark \
new-connection-mark=wireguard passthrough=yes src-address=192.168.10.2
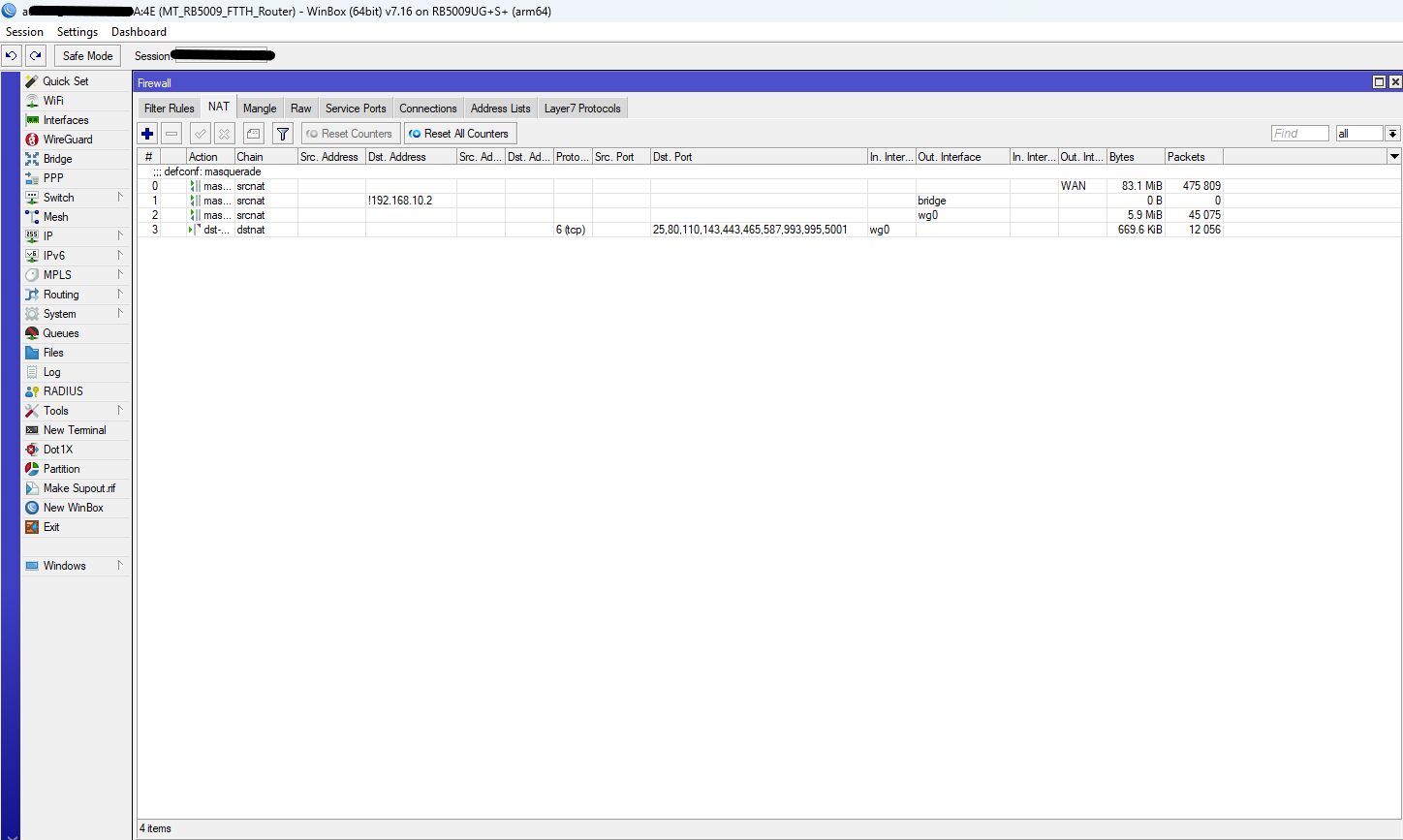
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=masquerade chain=srcnat dst-address=!192.168.10.2 out-interface=\
bridge
add action=masquerade chain=srcnat out-interface=wg0
add action=dst-nat chain=dstnat dst-port=\
25,80,110,143,443,465,587,993,995,5001 in-interface=wg0 protocol=tcp \
to-addresses=192.168.10.2
/ip ipsec profile
set [ find default=yes ] dpd-interval=2m dpd-maximum-failures=5
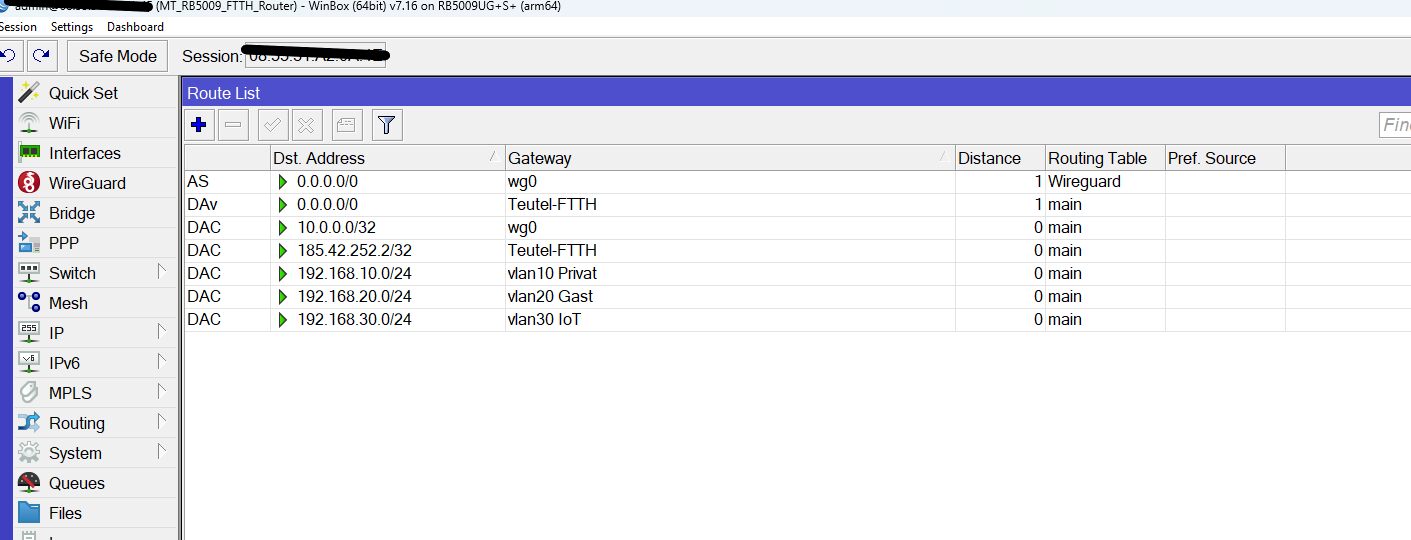
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=wg0 pref-src="" \
routing-table=Wireguard scope=30 suppress-hw-offload=no target-scope=10
/ipv6 dhcp-client
add disabled=yes interface=Teutel-FTTH pool-name=IPv6 request=prefix
/ipv6 dhcp-server
add address-pool="" disabled=yes interface=bridge name=IPv6
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" \
dst-port=33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
/routing rule
add action=lookup disabled=no src-address=192.168.10.2/32 table=Wireguard
add action=lookup disabled=yes src-address=192.168.178.2/32 table=Wireguard
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name=MT_RB5009_FTTH_Router
/system note
set show-at-login=no
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LANRB5009 (Syno), ROS 7.16:
=> Switch, DS718+, 2x Wifi-AP und Uplink zu RB4011(Schoppen)
/interface bridge
add admin-mac=Cxxxxxxxxxxx9 auto-mac=no comment=defconf name=bridge \
vlan-filtering=yes
/interface ethernet
set [ find default-name=ether1 ] comment=\
"Uplink > RB4011 Schoppen | VLAN 10 / 20 / 30 "
set [ find default-name=ether2 ] comment=\
"Downlink => RB5009_Schoppen | 192.168.10.252 | VLAN 10 / 20 / 30 "
set [ find default-name=ether3 ] comment=\
"MT_Audience | VLAN 10 / 20 / 30 "
set [ find default-name=ether4 ] comment=\
"MT_Schlafzimmer | VLAN 10 / 20 / 30 "
set [ find default-name=ether5 ] comment=\
"BrickSpace | 192.168.10.2 | VLAN 10 "
set [ find default-name=ether6 ] disabled=yes
set [ find default-name=ether7 ] disabled=yes
set [ find default-name=ether8 ] disabled=yes
/interface vlan
add interface=bridge name="vlan 10 Privat" vlan-id=10
add interface=bridge name="vlan 20 Gast" vlan-id=20
add interface=bridge name="vlan 30 IoT" vlan-id=30
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/disk settings
set auto-media-interface=bridge auto-media-sharing=yes auto-smb-sharing=yes
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3 pvid=10
add bridge=bridge comment=defconf interface=ether4 pvid=10
add bridge=bridge comment=defconf interface=ether5 pvid=10
add bridge=bridge comment=defconf interface=ether1
add bridge=bridge interface=sfp-sfpplus1
add bridge=bridge interface=ether6 pvid=10
add bridge=bridge interface=ether7 pvid=10
add bridge=bridge interface=ether8 pvid=10
add bridge=bridge interface="vlan 10 Privat" pvid=10
add bridge=bridge interface="vlan 20 Gast" pvid=20
add bridge=bridge interface="vlan 30 IoT" pvid=30
/ip neighbor discovery-settings
set discover-interface-list=all
/interface bridge vlan
add bridge=bridge tagged=bridge,ether1,ether2 untagged=ether3,ether4,ether5 \
vlan-ids=10
add bridge=bridge tagged=bridge,ether1,ether2,ether3,ether4 vlan-ids=20
add bridge=bridge tagged=bridge,ether1,ether2,ether3,ether4 vlan-ids=30
/interface list member
add interface=ether1 list=LAN
add interface=ether2 list=LAN
add interface=ether3 list=LAN
add interface=ether4 list=LAN
add interface=ether5 list=LAN
add interface=ether6 list=LAN
add interface=ether7 list=LAN
add interface=ether8 list=LAN
add interface=sfp-sfpplus1 list=LAN
add interface="vlan 10 Privat" list=LAN
add interface="vlan 20 Gast" list=LAN
add interface="vlan 30 IoT" list=LAN
add interface=bridge list=LAN
/ip address
add address=192.168.178.253/24 disabled=yes interface=bridge network=\
192.168.178.0
add address=192.168.10.253/24 interface="vlan 10 Privat" network=192.168.10.0
add address=192.168.20.253/24 interface="vlan 20 Gast" network=192.168.20.0
add address=192.168.30.253/24 interface="vlan 30 IoT" network=192.168.30.0
/ip dns
set servers=1.1.1.1
/ip ipsec profile
set [ find default=yes ] dpd-interval=2m dpd-maximum-failures=5
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=192.168.10.254 \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name=MT_RB5009_SYNO
/system note
set show-at-login=no
/system scheduler
add interval=1d name=reboot-6am on-event="/system reboot" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=2017-01-17 start-time=04:30:00
add interval=1w name=Update on-event="/system package update install" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=1970-01-05 start-time=04:10:00RB4011 (Schoppen)ROS 7.16:
=> Switch für DS718+ (Stby-Gerät), DS112+ (BackUpTarget), Drucker, IP-Telefon, Reo-Link Cam, Uplink zum HEXs (dieser wird nicht weiter betrachtet)
/interface bridge
add admin-mac=CxxxxxxxxxB auto-mac=no comment=defconf name=bridge \
port-cost-mode=short vlan-filtering=yes
/interface ethernet
set [ find default-name=ether1 ] comment="Downlink => RB5009 SYNO"
set [ find default-name=ether2 ] comment="MT_Schoppen | VLAN10/20/30"
set [ find default-name=ether3 ] comment="HEXs| VLAN 10"
set [ find default-name=ether4 ] comment="Drucker VLAN 10"
set [ find default-name=ether5 ] comment="DS718+ Two-Digits | VLAN 10"
set [ find default-name=ether6 ] comment="DS118+ Vault | VLAN 10"
set [ find default-name=ether7 ] comment="ReoLink 520 Einfahrt | VLAN 10"
set [ find default-name=ether8 ] comment="PC-B\FCro | VLAN 10"
set [ find default-name=ether9 ] comment=\
"D-Link Werkstatt => MT_Terrasse | VLAN 10/20/30"
set [ find default-name=ether10 ] comment=--ohne---
/interface vlan
add interface=bridge name="vlan 10 Privat" vlan-id=10
add interface=bridge name="vlan 20 Gast" vlan-id=20
add interface=bridge name="vlan 30 IoT" vlan-id=30
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface lte apn
set [ find default=yes ] ip-type=ipv4 use-network-apn=no
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/port
set 0 name=serial0
set 1 name=serial1
/interface bridge port
add bridge=bridge comment=defconf interface=ether2 internal-path-cost=10 \
path-cost=10 pvid=10
add bridge=bridge comment=defconf ingress-filtering=no interface=ether3 \
internal-path-cost=10 path-cost=10
add bridge=bridge comment=defconf ingress-filtering=no interface=ether4 \
internal-path-cost=10 path-cost=10 pvid=10
add bridge=bridge comment=defconf ingress-filtering=no interface=ether5 \
internal-path-cost=10 path-cost=10 pvid=10
add bridge=bridge comment=defconf ingress-filtering=no interface=ether6 \
internal-path-cost=10 path-cost=10 pvid=10
add bridge=bridge comment=defconf interface=ether7 internal-path-cost=10 \
path-cost=10 pvid=10
add bridge=bridge comment=defconf interface=ether8 internal-path-cost=10 \
path-cost=10 pvid=10
add bridge=bridge comment=defconf ingress-filtering=no interface=ether9 \
internal-path-cost=10 path-cost=10 pvid=10
add bridge=bridge comment=defconf ingress-filtering=no interface=ether10 \
internal-path-cost=10 path-cost=10 pvid=10
add bridge=bridge comment=defconf ingress-filtering=no interface=sfp-sfpplus1 \
internal-path-cost=10 path-cost=10
add bridge=bridge comment=defconf ingress-filtering=no interface=ether1 \
internal-path-cost=10 path-cost=10
add bridge=bridge interface="vlan 10 Privat" pvid=10
add bridge=bridge interface="vlan 20 Gast" pvid=20
add bridge=bridge interface="vlan 30 IoT" pvid=30
/ip firewall connection tracking
set udp-timeout=10s
/ip neighbor discovery-settings
set discover-interface-list=all
/ip settings
set max-neighbor-entries=8192
/ipv6 settings
set max-neighbor-entries=8192
/interface bridge vlan
add bridge=bridge tagged=bridge,ether1,ether3 untagged=\
ether2,ether4,ether5,ether6,ether8,ether9,ether7 vlan-ids=10
add bridge=bridge tagged=bridge,ether1,ether2,ether9,ether3 vlan-ids=20
add bridge=bridge tagged=bridge,ether1,ether2,ether9,ether3 vlan-ids=30
/interface list member
add interface=ether2 list=LAN
add interface=ether3 list=LAN
add interface=ether4 list=LAN
add interface=ether5 list=LAN
add interface=ether6 list=LAN
add interface=ether7 list=LAN
add interface=ether8 list=LAN
add interface=ether9 list=LAN
add interface=ether10 list=LAN
add interface=sfp-sfpplus1 list=LAN
add interface="vlan 10 Privat" list=LAN
add interface="vlan 20 Gast" list=LAN
add interface="vlan 30 IoT" list=LAN
add interface=ether1 list=WAN
/interface ovpn-server server
set auth=sha1,md5
/ip address
add address=192.168.10.252/24 disabled=yes interface=bridge network=\
192.168.10.0
add address=192.168.20.252/24 interface="vlan 20 Gast" network=192.168.20.0
add address=192.168.30.252/24 interface="vlan 30 IoT" network=192.168.30.0
add address=192.168.10.252/24 interface="vlan 10 Privat" network=192.168.10.0
/ip cloud
set update-time=no
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf gateway=192.168.88.1
/ip dns
set allow-remote-requests=yes servers=1.1.1.1
/ip dns static
add address=192.168.10.252 comment=defconf name=router.lan type=A
/routing bfd configuration
add disabled=no interfaces=all min-rx=200ms min-tx=200ms multiplier=5
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name=MT_RB4011_Schoppen
/system note
set show-at-login=no
/system ntp client
set enabled=yes
/system ntp client servers
add address="server 0.de.pool.ntp.org"
add address=192.53.103.104
/system resource irq rps
set sfp-sfpplus1 disabled=no
/system routerboard settings
set auto-upgrade=yes
/system scheduler
add interval=1d name=reboot-6am on-event="/system reboot" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=2017-01-17 start-time=04:30:00
add interval=1w name=Update on-event="/system package update install" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=2024-08-20 start-time=04:00:00
/system script
add dont-require-permissions=yes name="System Package" owner=admin policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source=":\
if ([/system package update get status] = \"New version is available\") do\
={\r\
\n:log warning \"System package update is available\";\r\
\n/system package update install;\r\
\n:delay 10:\r\
\n:log warning \"reboot\";\r\
\n/system reboot} else={:log warning \"No System package update is availab\
le\"}\r\
\n:log warning \"END\"\r\
\n"
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LANetwas viel....ok....
Könnt Ihr erkennen, was ich das falsch eingestellt habe?
Grüße
Marco


Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 668541
Url: https://administrator.de/forum/mikrotik-vlan-clients-koennen-nicht-kommunizieren-668541.html
Ausgedruckt am: 05.08.2025 um 07:08 Uhr
33 Kommentare
Neuester Kommentar
darf bei Verwendung von VLANs die Bridge keine IP haben.
Das ist richtig!Was unklar an deinem "Setup" ist, ist WIE die 2 Router 5009 und 4011 verbunden sind. Oder sind es sogar 3 Router weil keiner weiss was 5009 Schoppen, Syno oder was auch immer ist!
Dabei generell die Frage welchen tieferen Sinn es hat 2 oder mehr Router in einem Netzwerk zu betreiben?? Normal ist ein Router und x Switches.
Hier wäre eine kurze Skizze des Netzdesigns sicher für alle hilfreich. Das gilt besonders für die Uplinks die die 2 (oder 3) Router verbinden und die der APs. Also alle Links die die VLANs tagged übertragen müssen.
Ebenso was "SYNO" bedeutet und was das mit "HEXs" zu tun hat?? 🤔
Fehler die man auf die Schnelle schon sieht:
- Was völlig falsch ist, ist das du ALLEN 3 Routern IP Adressen in den VLANs verpasst hast. Das ist der größte Fehler, denn so hast du 3 mögliche Router die zwischen den VLANs routen können was natürlich Unsinn ist und auch gefährlich für die Netzwerk Sicherheit sofern du ein Firewall Regelwerk zw. den VLANs nutzt. Ist das nur an einem Router aktiv konfiguriert man als Angreifer schlicht ein anderes Gateway um das einfach zu überwinden. 2 VLAN IP Adresssen machen nur Sinn wenn man VRRP als L3 Redundanz konfiguriert (siehe Tutorial!) Das ist bei dir aber NICHT der Fall. Hier ist also dein L3 Design völliger Murks!!
- Bestimme also welches VLAN Device hier "L3 Core" Switch sein soll und nur DER hält die IP Adressen und DHCP Server und macht das Routing! ALLE anderen Beteiligten arbeiten einzig und allen NUR im Layer 2 Mode. Sprich sie haben lediglich nur eine einzige IP im Management VLAN was vermutlich (geraten) dein Privatnetz (10) ist. In der Regel ist das das Gerät an dem sternförmig alle anderen angeschlossen sind.
- Die VLAN IP Interfaces müssen NICHT in der VLAN Bridge als Interfaces definiert werden. Das VLAN Tutorial weist extra in rot mit Warndreieck darauf hin!
- Gleiches gilt für UNtagged Ports. Diese müssen NICHT als Bridge Port Member eingetragen sein sondern es reicht vollkommen das über die PVID festzulegen. Auch darauf weist das Tutorial hin.
- Interface können nicht gleichzeitig tagged und untagged sein. Zu mindestens nicht über die VLAN Bridge so konfiguriert!
- Das gilt für die Uplink Ports ether4 und ether8 die falsch untagged für VLAN 10 gesetzt sind aber tagged für 20 und 30 was so in der Bridge nicht geht. Wenn du das Native VLAN dieser Uplinks auf ein anderes als 1 setzen willst machst du das einzig und allein NUR über die PVID aber NICHT indem du bei den VLAN Memberports diese auf UNtagged setzt. Zumal UNtagged Ports generell NICHT als Memberports eingetragen werden. Es reicht einzig nur die PVID. Siehe oben!
- Sollen also für die Ports 4 und 8 das Native bzw. PVID VLAN 10 sein und 20 und 30 jeweils tagged muss nur die Port PVID auf 10 gesetzt sein und NUR 20 und 30 tagged. Ein Winbox Screenshot würde hier helfen weil der deutlich übersichtlicher ist!
Fazit:
Das Tutorial wirklich einmal in aller Ruhe lesen und auch richtig umsetzen!! 🧐
2 grobe Kardinalsfehler die Ursache deiner Fehlfunktion sind musst du bereinigen:
- Punkt 1: Einmal das völlig falsche Layer 3 Design. VLAN Routing einzig nur auf einem Gerät. Alles andere nur L2 / Switching.
- Punkt 4: Das falsche Tagging der VLANs auf den Uplinks 1, 4 und 8
Wie gesagt: Eine Designskizze welches Gerät WAS machen soll und WIE und WO angeschlossen ist (Uplinks) würde allen hier helfen. Besonders was diese 3 Router sollen, ob du die als einfache VLAN Switches "missbrauchen" willst oder welchen Sinn die haben. Besonders was "SYNO", "Schoppen" und all die anderen kryptischen Begriffe bedeuten.
Wenn du den Konfig Export postest wäre es zudem hilfreich alles was nicht Threadfragen bezogen ist der Übersichtlichkeit halber rauszunehmen.
Kannst Du dir nun ein Bild machen?
Jau...Die Kardinalsfehler sind nun weg. Hab das Tagging/Untagging bereinigt.
Perfekt! 👍Bleibt dann nur die Frage: Rennt denn nun alles wie es soll oder müssen wir mit ein paar Schoppen Wein nochmal an deine Fehler ran???
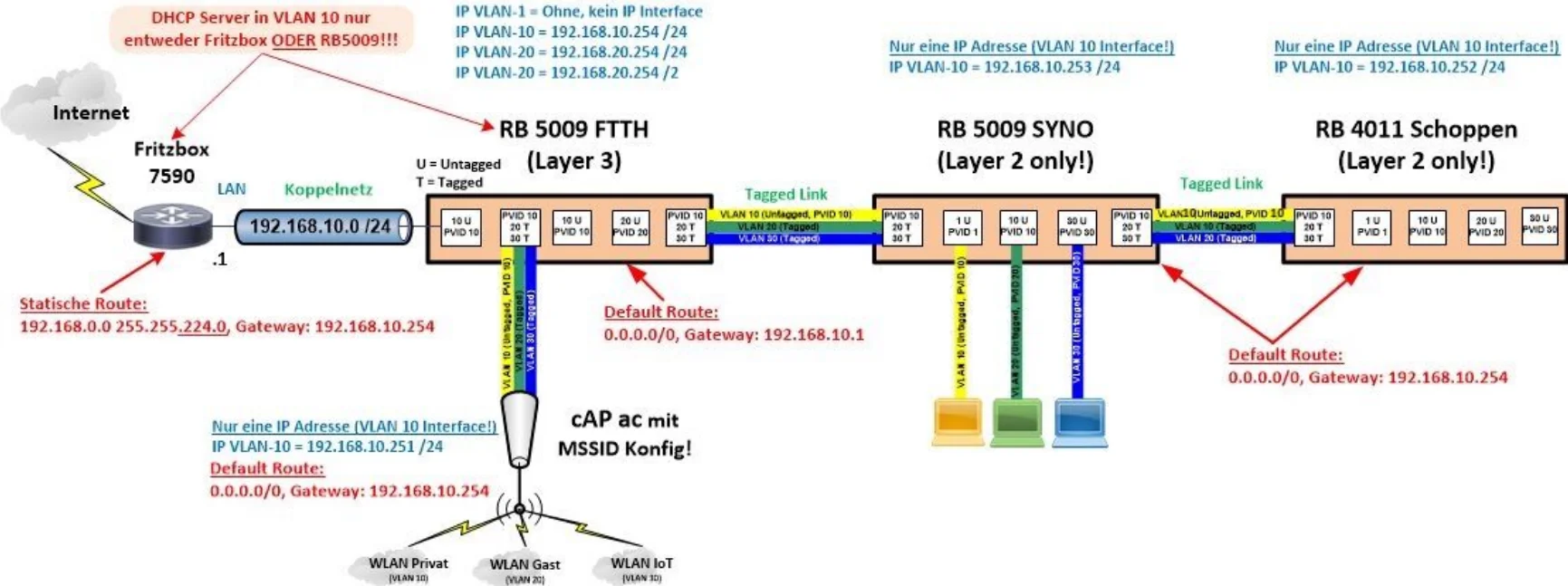
Hier nochmals wie dein Netz ohne Endgeräte Wimmelei im Backbone auszusehen hat.
Designtechnisch wäre es deutlich besser wenn der SYNO statt FTTH das zentrale L3 Geschäft machen würde, da der "zentral" liegt und so die L3 Wege von den anderen Komponenten am kürzesten sind. Solltest du ggf. umstellen.
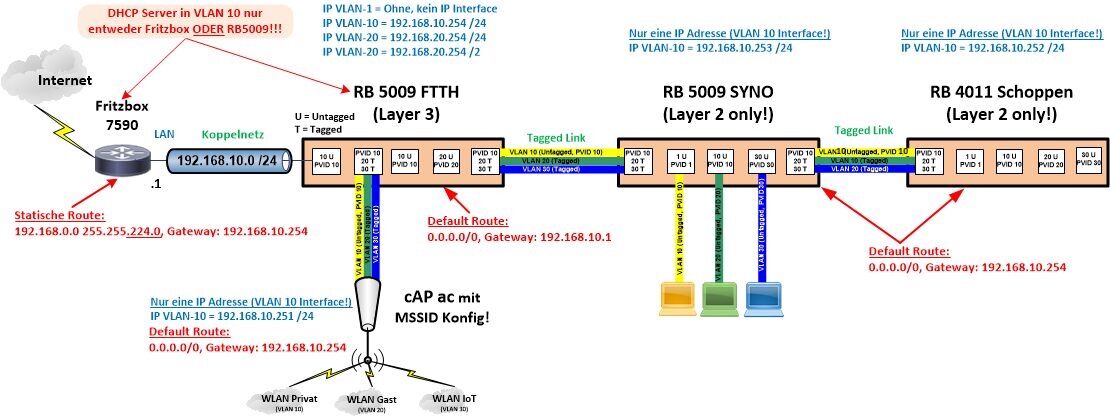
- VLAN 10 = PVID
- VLAN 20 = Tagged
- VLAN 30 = Tagged
- Achte auf den DHCP Server im VLAN 10! Da gilt: Es kann nur einen geben!!
- Statische Management IPs auf den Geräten immer außerhalb der DHCP Range oder wenn mit DHCP dann immer nur mit fester Reservierung über die Mac Adresse.
- Die reinen Layer 2 konfigurierten "Switches" SYNO und Schoppen haben nur eine einzige IP im VLAN 10 Interface ansonsten KEINE weiteren VLAN Interfaces! Die VLANs 10, 20 und 30 werden dort einzig nur in der Bridge konfiguriert.
- Bridge Interfaces dürfen in einem VLAN Setup KEINE IP Adresse haben!!! Auf keinem MT Gerät! (Siehe Tutorial)
- Gleiches gilt für die cAP ac Accesspoints im MSSID Setup!! Nur eine VLAN 10 IP, KEINE IP auf dem Bridge Interface, VLANs nur auf der Bridge!
- Winbox Screenshots helfen beim Troubleshooting.
"Riesling-Schorle"
Du meinst dann sicher einen Schuppen?!duden.de/rechtschreibung/Schoppen
Egal...
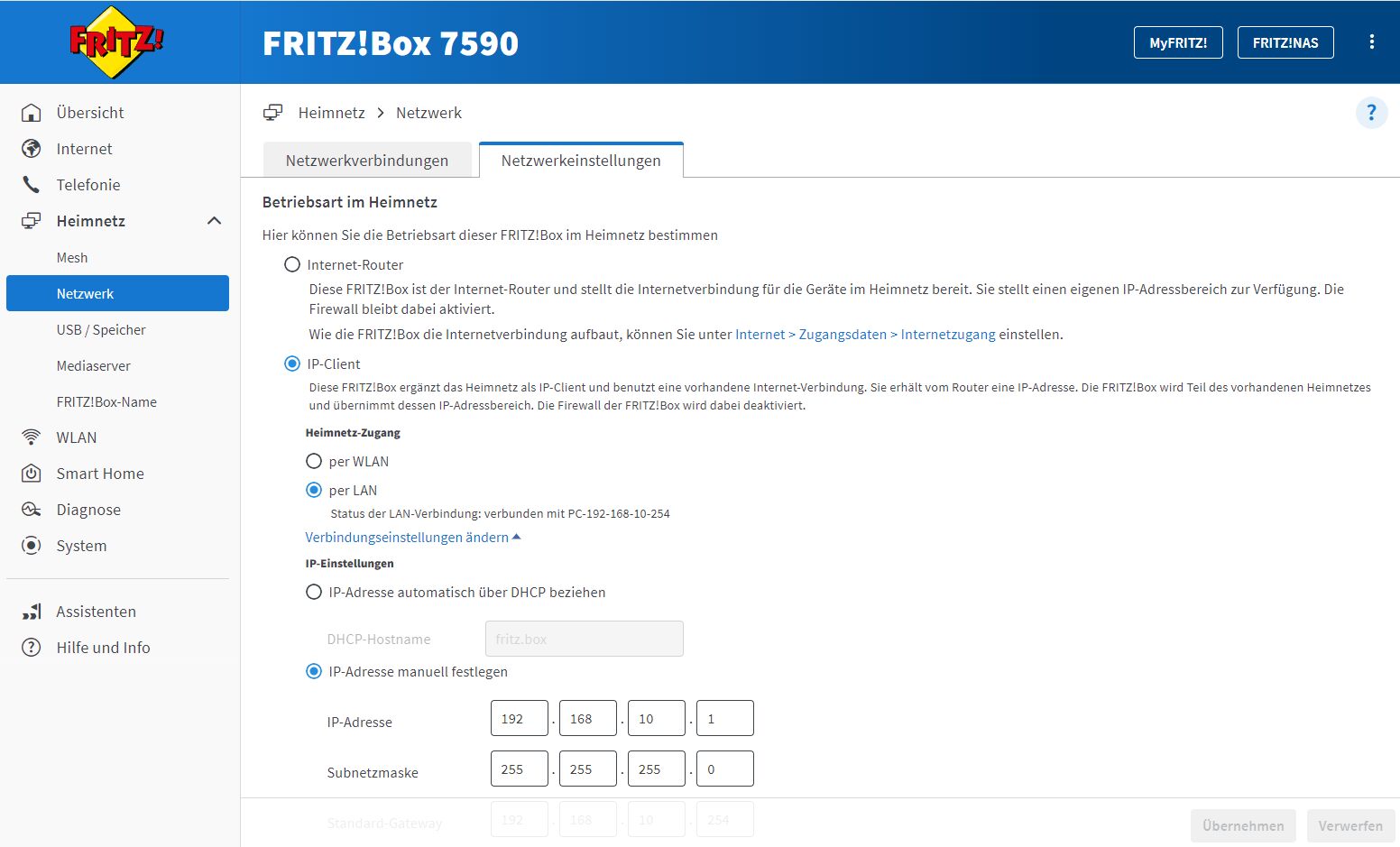
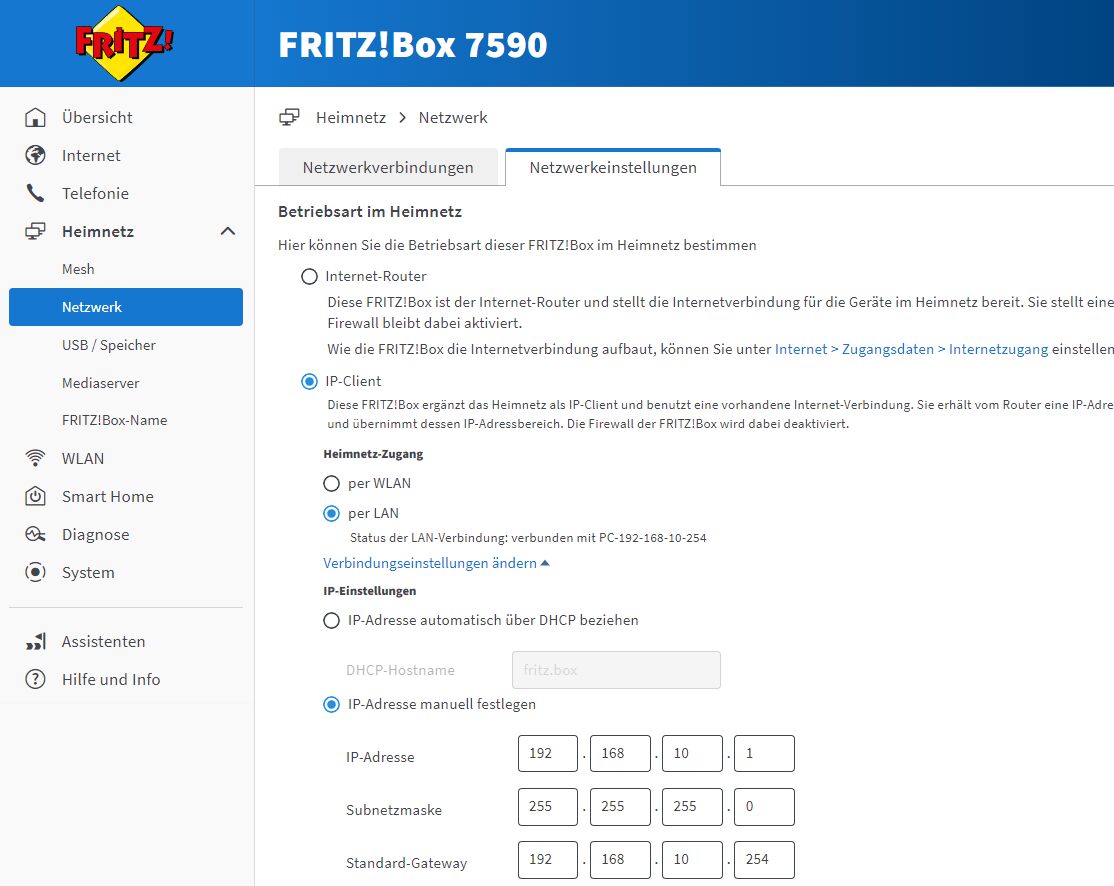
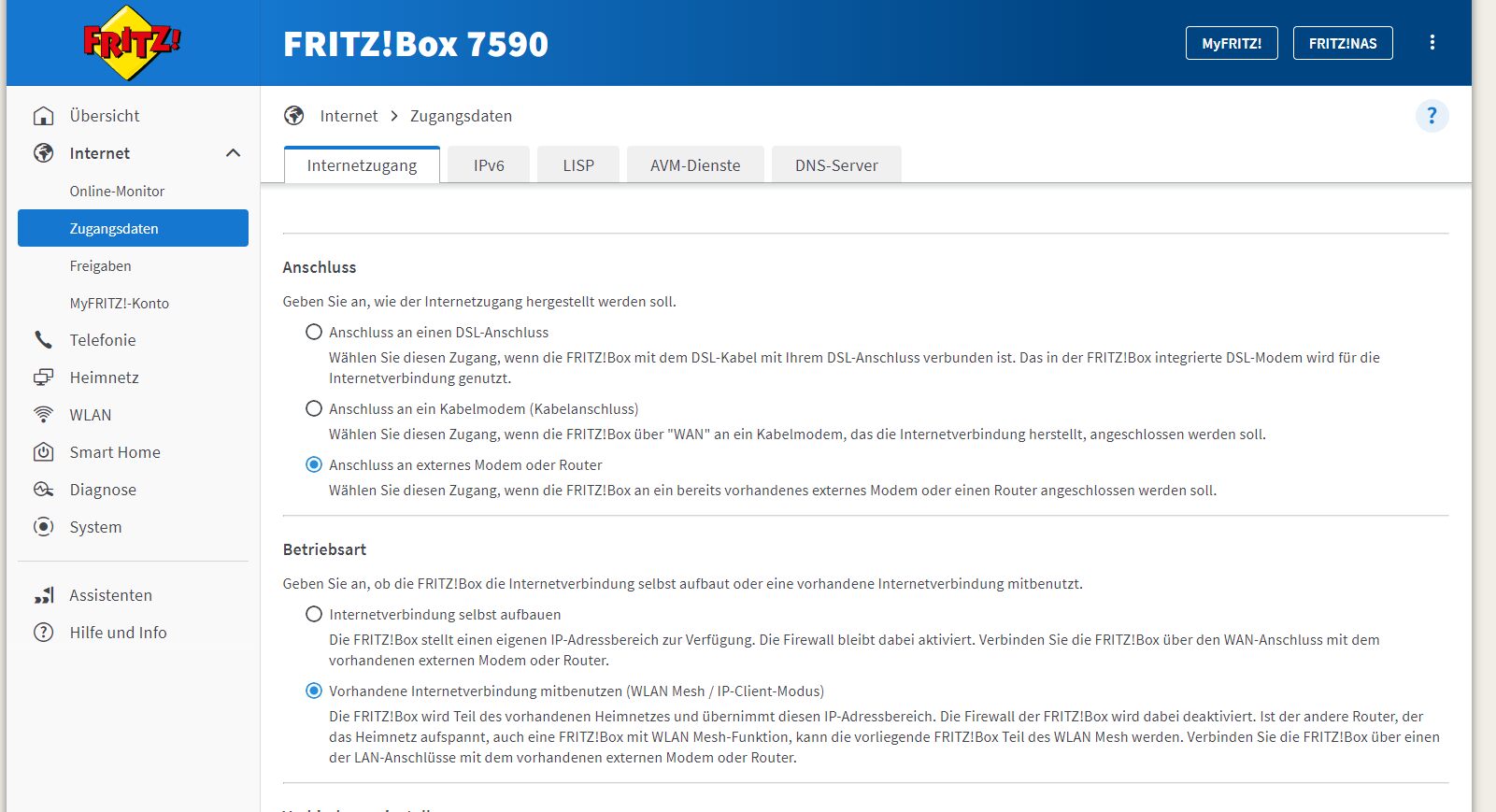
Die Fritte (Bridge-Mode) ist nicht als Modem aktiv, das macht der RB5009FTTH.
Das kann niemals sein, denn wäre dem so würde die Fritte, wie der Name ja schon sagt, bridgen am LAN Port. Sprich dort 1:1 das ungeschützte Internet übertragen.Es wäre dann fatal wenn dieser Koppelport am Mikrotik irgendwie Member der VLAN-Bridge wäre und als PVID 10 gesetzt hätte!
In dem Fall dürfte dieser Port logischerweise niemals irgendein VLAN Memberport sein. Er MUSS dann zwangsweise ein dedizierter IP Routingport sein OHNE irgendeine VLAN Funktion. So wie im Tutorial beschrieben.
Dein Setup rennt ausschliesslich nur so in einer Router Kaskade wenn der davor kaskadierte Router als stinknormaler NAT Router arbeitet?! Da du auch noch VoIP routest, was die Fritzbox auch nur im NAT Routing Mode überhaupt supportet, kann deine Angabe also niemals stimmen.
Hier erzählst du also Murks und solltest das nochmal genau prüfen!!!
Letztlich ist das zwar ein gravierendes Problem aber nicht das eigentliche Problem deines Threads. Das basiert einzig auf dem Setup der Trunk/Uplinks der die 3 Router/Switch Geräte und die APs bedient.
Hier machst du irgendwo einen gravierenden Fehler. Leider fehlt wieder ein Winbox Screenshot um das letztlich beurteilen zu können.
In Deiner Skizze hast Du die Tagged Links vom L3 zum L2 und zum L2 unterschiedlich getagged:
Sorry, das war, wiue du dir sicher schon selber gedacht hast, ein Dreckfuhler auf dem gelben Link der aber jetzt korrigiert ist.Generell ist dein Setup mit der Nichtnutzung des VLAN 1 nicht falsch. Es hat aber den Nachteil das du ALLE Komponenten vorher anfassen musst um diese Uplinks immer vorab entsprechend zu setzen um so eine VLAN 10 IP zu bekommen.
Für Anfänger ist es deutlich einfacher das VLAN 1 aktiv zu nutzen, denn das Interface ist immer vorhanden, man bekommt eine IP OHNE vorher das Setup anpassen zu müssen. Es macht das Management also etwas einfacher.
Wie gesagt letztlich ist dein Setup nicht falsch aber erfordert immer etwas Vorarbeit.
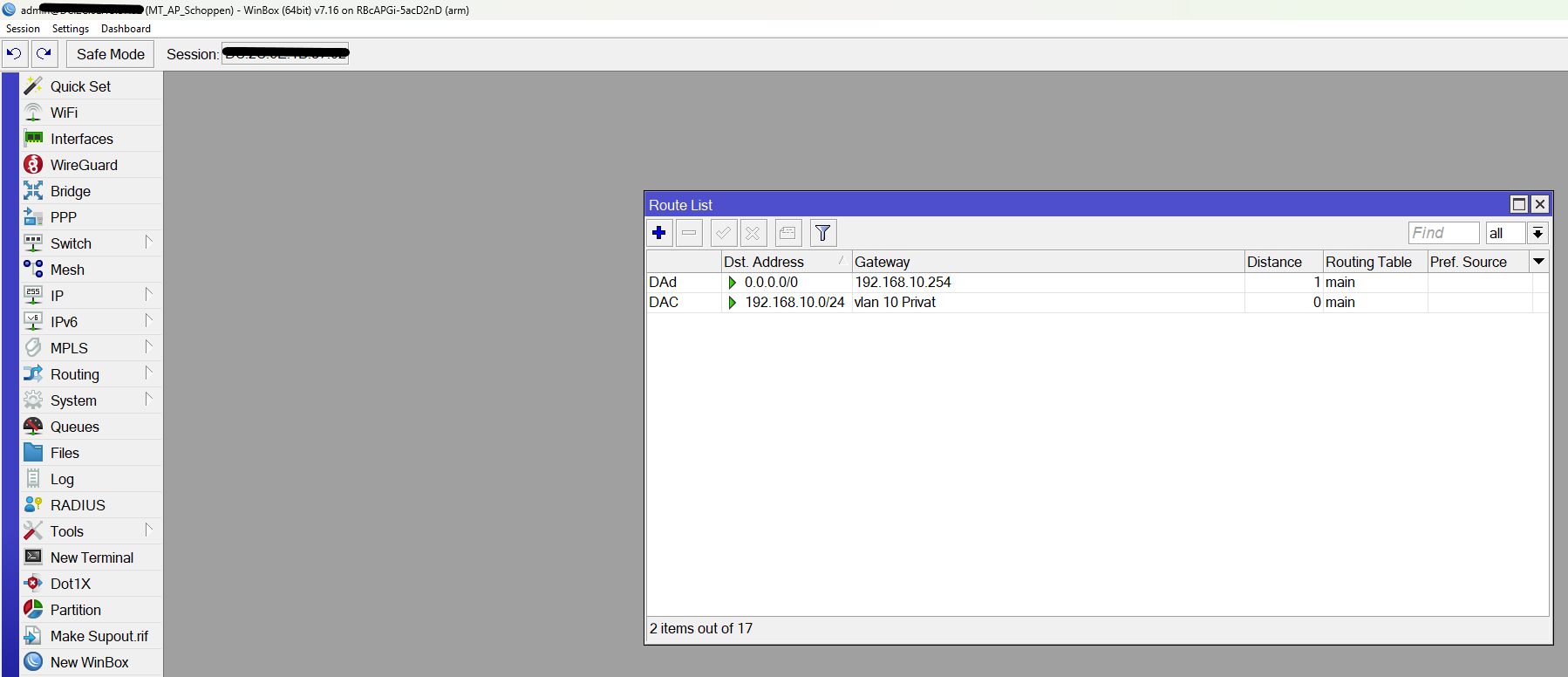
Der L3 hat auf VLAN-Interface 10/20/30 eine IP => OK?
Das ist OK! 👍Auf dem L3 laufen die drei DHCP Server, NUR auf dem L3.
Das ist nur fast OK, denn WAS ist mit dem parallel laufenden DHCP Server auf der FritzBox?!Da dein Fritzbox Setup unklar und vermutlich "Bridging" Murks ist, ist davon auszugehen das die Fritzbox auch im 10er VLAN aktiv ist und damit auch ihr DHCP Server sofern du den dort NICHT deaktiviert hast?. Es kann nur einen geben...!
Im VLAN 10 "sehe" ich alles, kann alles anpingen aber nicht "connecten"....
Das kann mehrere Ursachen haben...- Die unklare Fritzbox Konfig und ggf. der parallel laufende Bridging betrib mit dem ungeschützten Internet
- Amok laufende, parallel agierende DHCP Server im VLAN 10
- Falsch oder fehlerhaft konfigurierte Gateways und DNS Server im VLAN 10. Hier hättest du immer auch die FritzBox aber die solltest du NICHT verwenden! In allen VLANs sollte immer der RB5009 FTTH in allen VLANs Gateway und DNS Server sein. Check das in den Endgeräten!
hat das was mit der Firewall zu tun?
Nein, denn wie du ja selber sagst ist auf keinem der Mikrotik Geräte die Firewall aktiv. Was übrigens auch fatal wäre wenn dein Fritzbox Bridging Argument oben wahr wäre. Dann müsste der 5009 FTTH logischerweise zwingend NAT und auch Firewalling machen!Werde nachher den Absender in der Advanced-Karte testen…
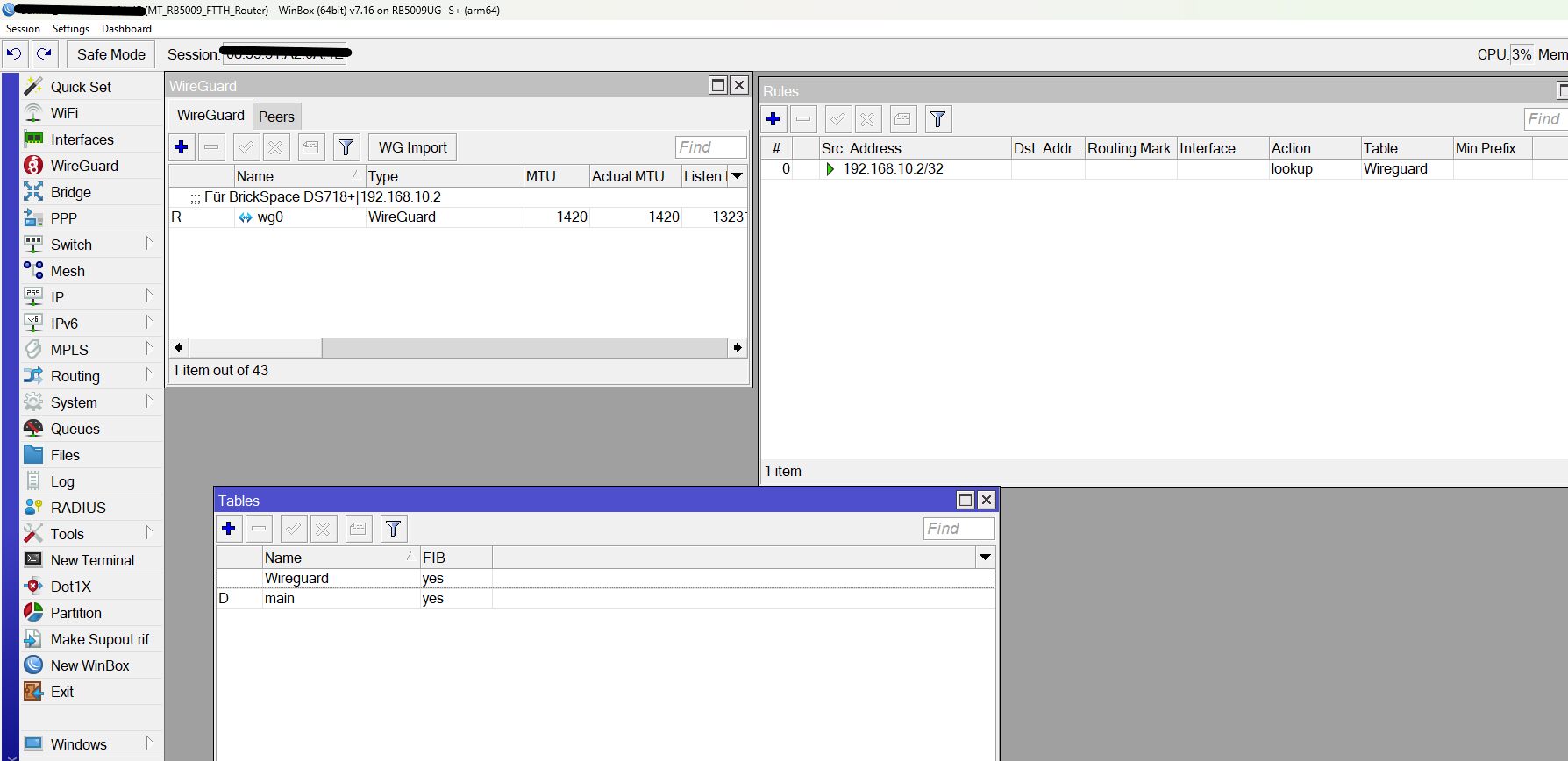
Das wäre wichtig!Die DS718+(.10.2) ist über WireGuard von außen zu erreichen
Ist für dein eigentliches Problem erstmal irrelevant.Nebenbei aber auch ziemlicher Blödsinn und auch völlig unsinnig, denn dein RB5009 kann auch Wireguard was dann in der Peripherie bleibt. So mit einem Server im internen Netz musst du zwangsweise ungeschützten Internet Traffic ins lokale LAN lassen. Sicherheitstechnischer und auch performancetechnischer Unsinn wenn man einen VPN Router betreibt der so gut wie alle VPN Protokolle supportet. Aber egal...andere Baustelle!
Dieses MSSID krieg ich leider nicht auf die Kette
Hier hast du sicher etwas verwechselt. Es geht NICHT um das MSSID mit dem CapsMan sondern immer um eine standalone MSSID Konfig die du auf den APs vornimmst. Alles OHNE Capsman.Es wäre ja völliger Blödsinn einzelne APs einzelne SSIDs auszustrahlen zu lassen wenn jeder AP den du hast alle 3 SSIDs bedienen kann?!
Mit den virtuellen APs ist das doch ein simpler M ausklick und im Handumdrehen aufzusetzen. WAS genau bekommst du denn da nicht "auf die Kette"?? Nimm dir mal einen deiner APs und setze das dort auf um das mal auf einem AP erstmal testweise zum Fliegen zu bekommen.
Wir können dir hier auch nochmal genaue Screenshots vom Setup posten. Das schafft auch ein Laie auf Anhieb.
Wie gesagt, 3 wichtige Baustellen hast du zu prüfen:
- Das falsche FritzBox Setup ob mt oder ohne Bridging und das VLAN 10 Setup mit DHCP usw. Hier fehlt ein DHCP Adresscheck auf den Endgeräten (ipconfig etc.)
- Setup der Trunk Uplinks zwischen den 3 Komponenten und APs. Entweder dein Konzept ohne VLAN 1 dann mit entsporechedem Setup vorweg. Oder...mit aktiv genutztem VLAN 1
- Sinnvolles MSSID Setup der APs. Das macht aber nur dann Sinn wenn dein gesamtes VLAN Backbone sauber und korrekt rennt.
Muss das VLAN 1mit an Board sein?
Es ist ja immer von sich aus an Bord, da ja Default. Weg bekommst du es also nicht. Du kannst es nur inaktiv lassen, wie bei dir.Also keine PVID Ports dort reinlegen und auch keine VLAN IP Adressen.
Das ist absolut OK, bedeutet aber, wie auch schon gesagt, das du IMMER dann alle Komponenten vorab einzeln anfassen musst um zu mindestens an den Uplinks diese so einzurichten das sie entsprechende Management IPs bekommt und sie zugänglich sind zur Konfiguration.
Per se also nicht falsch nur etwas größerer Konfig Aufwand.
Da es ja aber so oder so immer vorhanden ist und nicht entfernbar ist kann man sich auch fragen ob man es nicht doch sinnvoll aktiv verwenden will?!
Fürs Management wäre das bei Anfängern oder Laien im Segmentierungs Umfeld sicher keine falsche Entscheidung, denn alle Ports liegen da im Default drin ohne sie vorab einzeln konfigtechnisch anfassen zu müssen. Das macht das Admin Leben etwas leichter.
Letztlich aber natürlich immer eine persönliche Entscheidung...
Tip zum Routing oben:
Sieh dir deine ggf. falsche Wireguard Konfig dort nochmal an mit dem Gateway Redirect (0.0.0.0/0) und lies dir die Pros und Cons dazu HIER nochmal genau durch?! Split Tunneling ist in der Regel die intelligentere Entscheidung es sei denn man will unbedingt einen Redirect?!
MSSID Screenshots folgen...
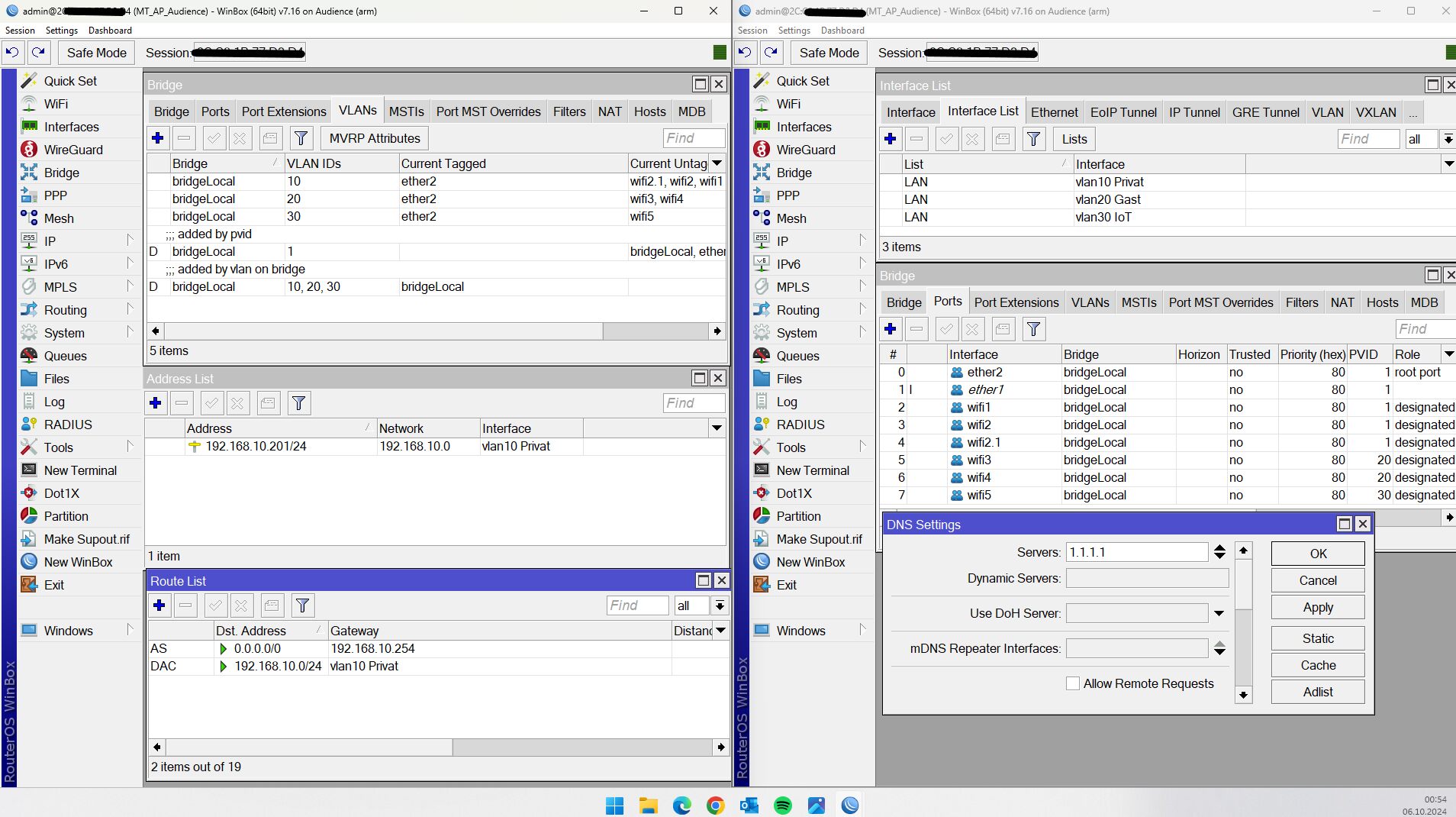
Auf Wunsch eines besonderen Herren hier das einfache MSSID Setup für einen Standalone AP ohne CapsMan. 😉
Bei 4 oder mehr APs wird das Management, da zentral, aber mit dem CapsMan ggf. etwas einfacher. Das kommt aber immer drauf an ob man häufig Änderungen macht. Ist das nicht der Fall kann man so ein Setup natürlich auch auf n Standalone APs klonen. Wie immer Geschmackssache...
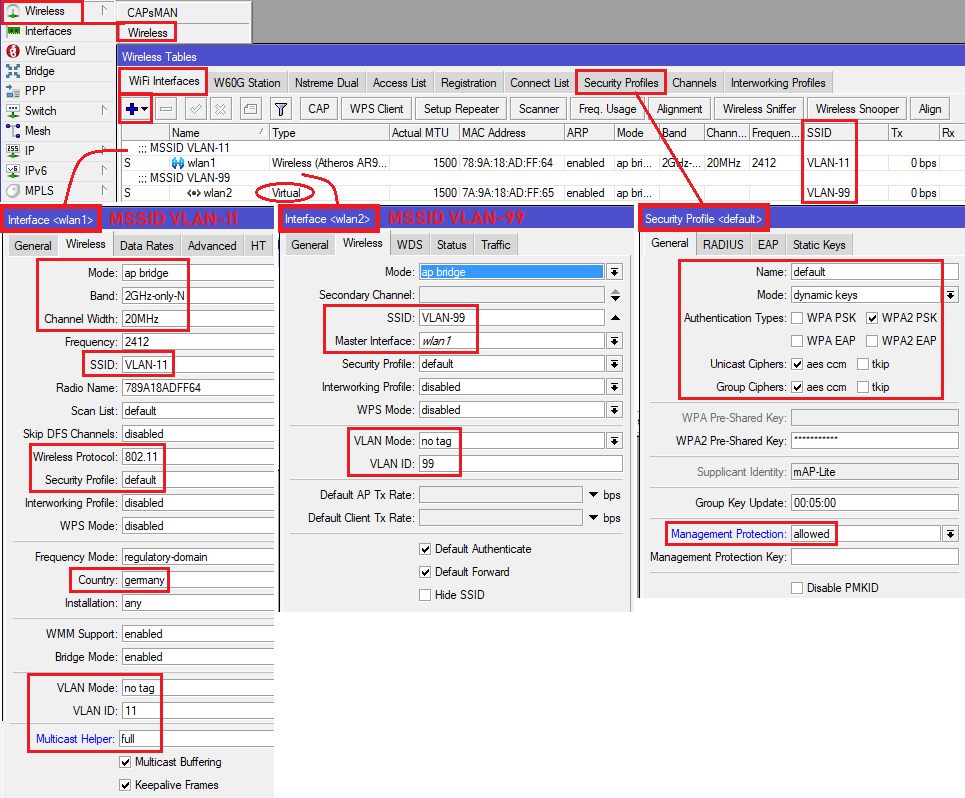
Beispiel der Übersicht halber nur auf dem 2,4 GHz Radio eines mAPs. Bei einem Dual Radio AP muss man zusätzlich auch die 5GHz Radios identisch an die VLAN-Bridge hängen
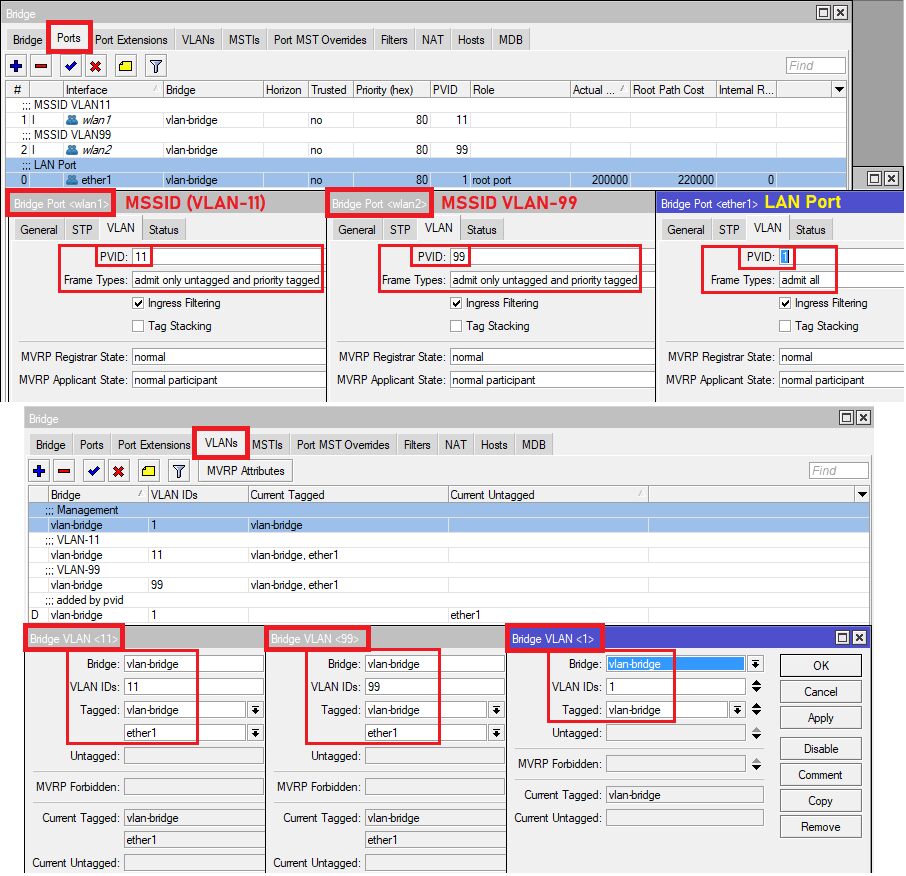
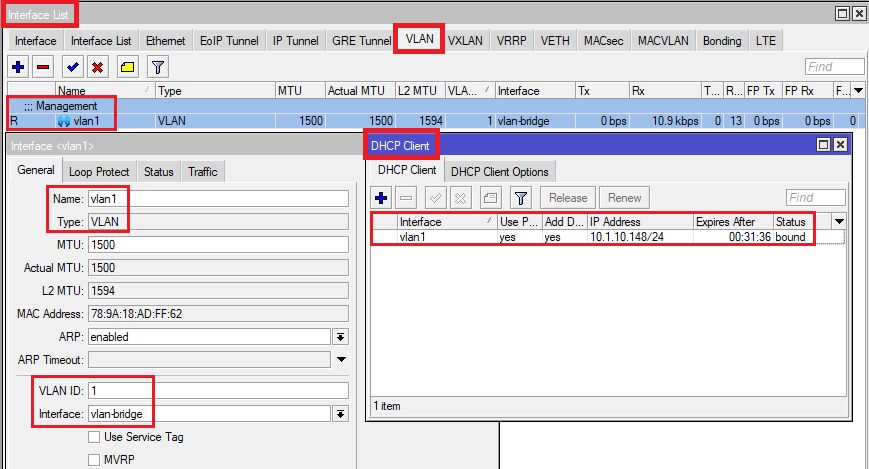
Ermöglicht eine flexible IP Adress Zuteilung und später über die Mac Adress Reservierung auch die Zuteilung einer festen Management IP.
Switch:
Der Mikrotik hängt an einem Cisco Catalyst Switch mit folgender Konfig
(PVID ist 1 und tagged für 11 und 99)
Klappt natürlich mit jedem x-beliebigen Baumarkt VLAN Switch und gleichem Port Setup auch.
Works as designed!! 👍
Was ist an so einem simplen, selbsterklärenden Setup denn nun so schwer das man es nicht auf die Kette heben kann? Ist doch alles kein Hexenwerk!! 😉
Bei 4 oder mehr APs wird das Management, da zentral, aber mit dem CapsMan ggf. etwas einfacher. Das kommt aber immer drauf an ob man häufig Änderungen macht. Ist das nicht der Fall kann man so ein Setup natürlich auch auf n Standalone APs klonen. Wie immer Geschmackssache...
Beispiel der Übersicht halber nur auf dem 2,4 GHz Radio eines mAPs. Bei einem Dual Radio AP muss man zusätzlich auch die 5GHz Radios identisch an die VLAN-Bridge hängen
- Management per DHCP Client im VLAN 1
- MSSID VLANs 11 und 99
- RouterOS Ver. 7.16 (Stable)
Inhaltsverzeichnis

Ermöglicht eine flexible IP Adress Zuteilung und später über die Mac Adress Reservierung auch die Zuteilung einer festen Management IP.

- Das WLAN Primärinterface wlan1 bedient das VLAN 11
- Das virtuelle Interface wlan2 bedient das VLAN 99
- Auf dem Management Interface (hier vlan1 ist aus gutem Grund kein WLAN Netz gemappt!


Switch:
Der Mikrotik hängt an einem Cisco Catalyst Switch mit folgender Konfig
interface GigabitEthernet0/12
description MSSID AP Testport
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 1,11,99
switchport mode trunk
switchport nonegotiate
spanning-tree portfast Klappt natürlich mit jedem x-beliebigen Baumarkt VLAN Switch und gleichem Port Setup auch.
Works as designed!! 👍
Was ist an so einem simplen, selbsterklärenden Setup denn nun so schwer das man es nicht auf die Kette heben kann? Ist doch alles kein Hexenwerk!! 😉
Das WireGuard-Setup wurde bei mir von jemanden externes eingerichtet
Wie gruselig!! Der und alle seine Bekannten und deren Kumpels haben jetzt Zugriff auf dein Netz. Datensicherheit sieht bekanntlich anders aus! [ Mit L2TP] hättest du bordeigene Clients nutzen können.Vielleicht darf ich noch mal auf mein LAN-Problem zurück kommen:
Ja besser ist das. Das sind alles andere Baustellen!Soweit ich mein Setup überblicke, habe ich das Tutorial und Deine Tipps bzw. "Must-Haves" umgesetzt.
Das ist gut, dann sollte es keine Fehler mehr geben!VLAN 20,30 & Bridge =>TimeOut.
Wieso schon wieder "Bridge"??? 😡- In einem VLAN Umfeld gibt es KEINE Bridge IP!!!
- Man kann deshalb keine Bridge pingen!!!
habe ich das Tutorial und Deine Tipps bzw. "Must-Haves" umgesetzt.
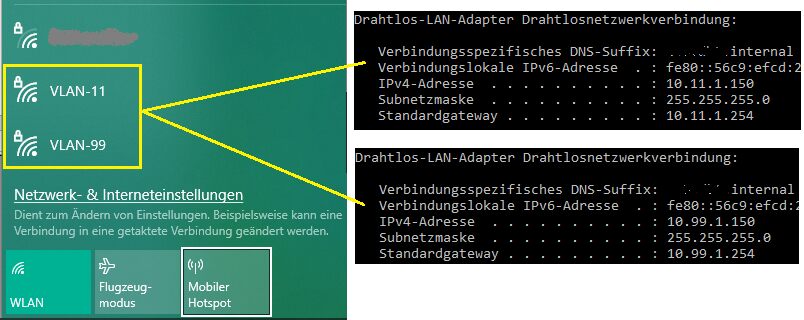
Wohl eher nicht wenn man das wieder lesen muss!!! 🙄Kannst du denn testweise von den nur L2 VLAN 10 Management Geräten "SYNO" und "Schoppen" mit deren Ping Funktion im Winbox Menü die VLAN 20 und VLAN 30 IPs des "FTTH" pingen?
Und... vice versa vom "FTTH" über dessen Ping mit jeweils vorherigem Setting der Absender IP auf 20 und 30 (unter "Advanced" Reiter im Ping) die jeweils beiden VLAN 10 IPs von "SYNO" und "Schoppen"??
Also hat die F*g-Bridge auch keine IP. Logisch
Warum schreibst du das dann?! und beim testen habe ich auch den Reiter Bridge ausgewählt um zu gucken was da als Ergebnis steht...
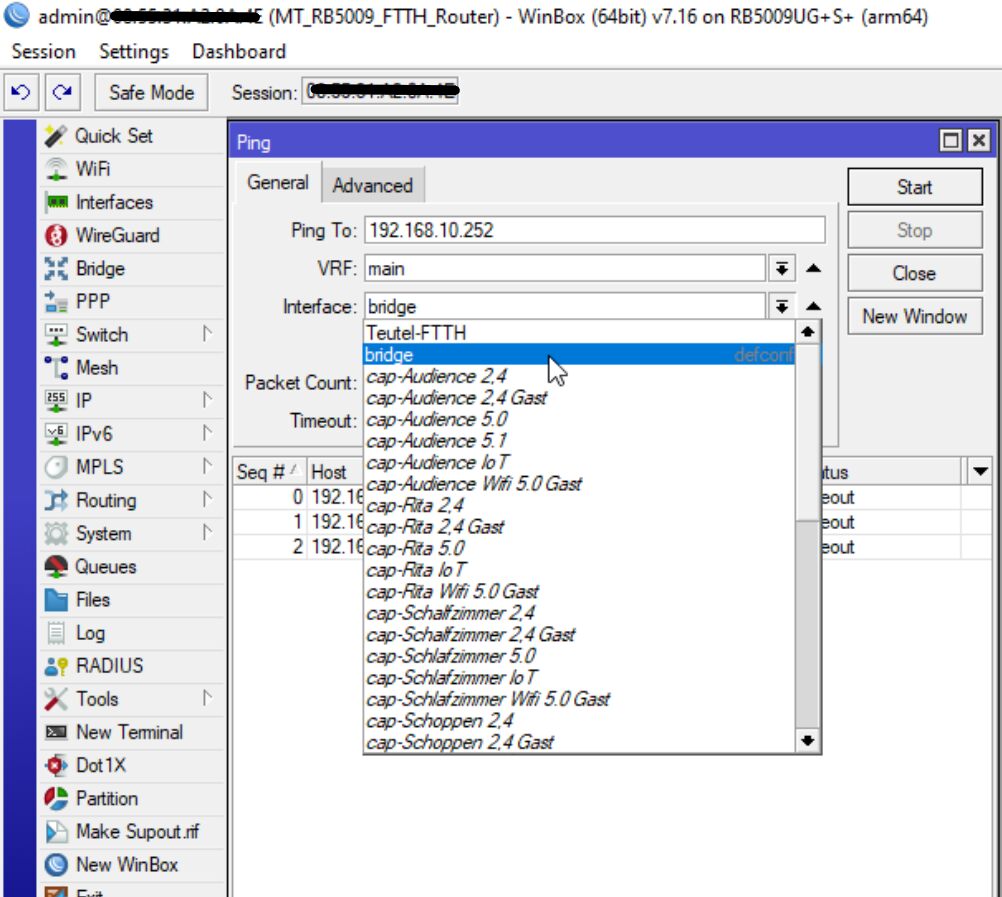
Rembrandt? Ägypten? Die Winbox Ping Funktion hat nirgendwo einen Reiter wo man was von der Bridge setzen kann!Es ist doch ganz einfach:
- Per Winbox auf den 5009er FTTH gehen und die Ping Funktion unter Tools aufrufen
- Absender IP auf die FTTH, VLAN10 IP setzen (Reiter "Advanced")
- SYNO VLAN 10 IP pingen
- Schoppen VLAN 10 IP pingen
- Absender IP auf die FTTH, VLAN20 IP setzen (Reiter "Advanced")
- Wieder SYNO VLAN 10 IP pingen (andere gibts da ja nicht!)
- Wieder Schoppen VLAN 10 IP pingen (andere gibts da ja nicht!)
- Absender IP auf die FTTH, VLAN30 IP setzen
- Wieder SYNO VLAN 10 IP pingen
- Wieder Schoppen VLAN 10 IP pingen
- Dann Ping wie oben von SYNO und Schoppen VLAN 10 auf den FTTH VLAN 10, 20 und 30.
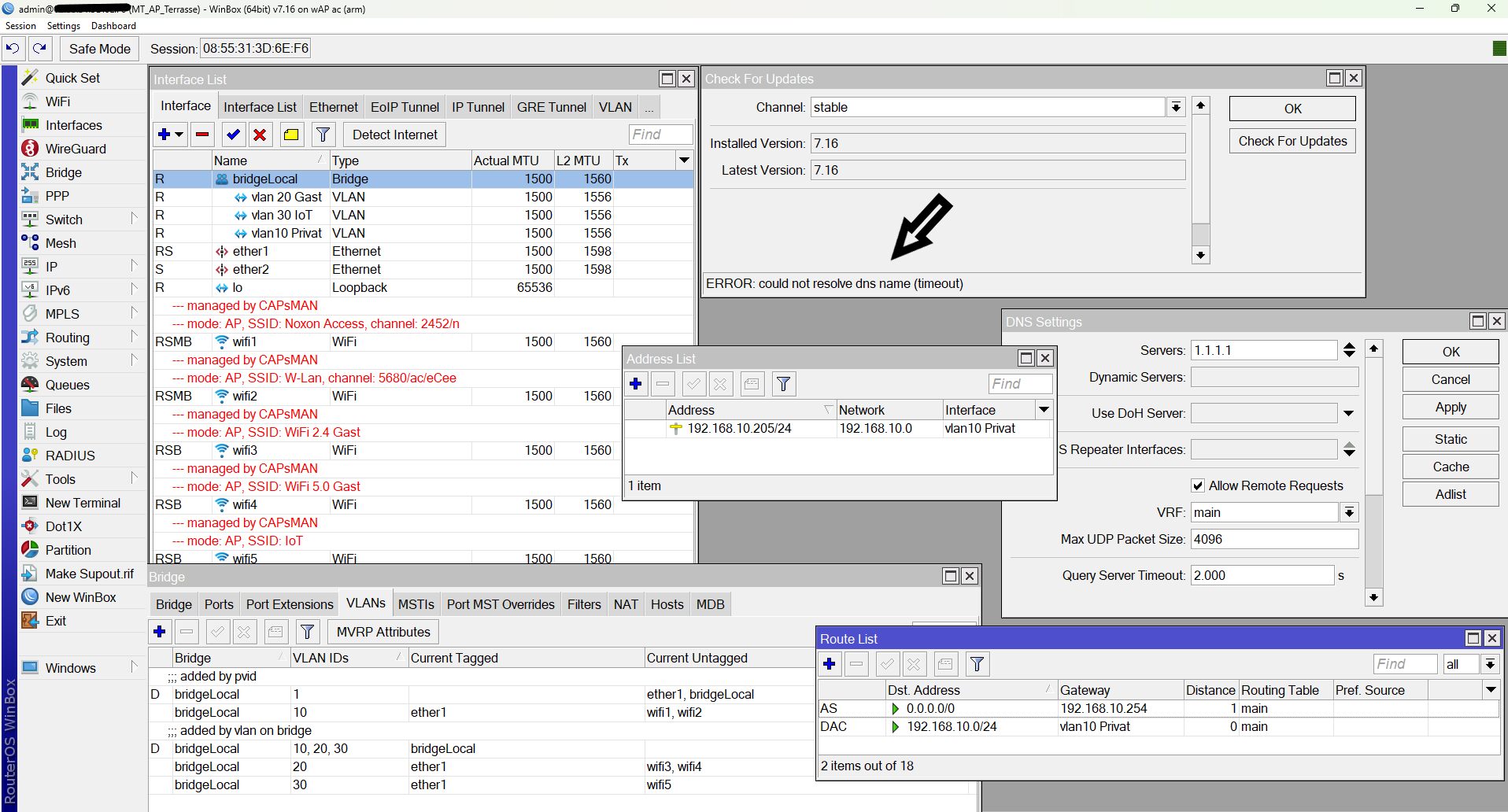
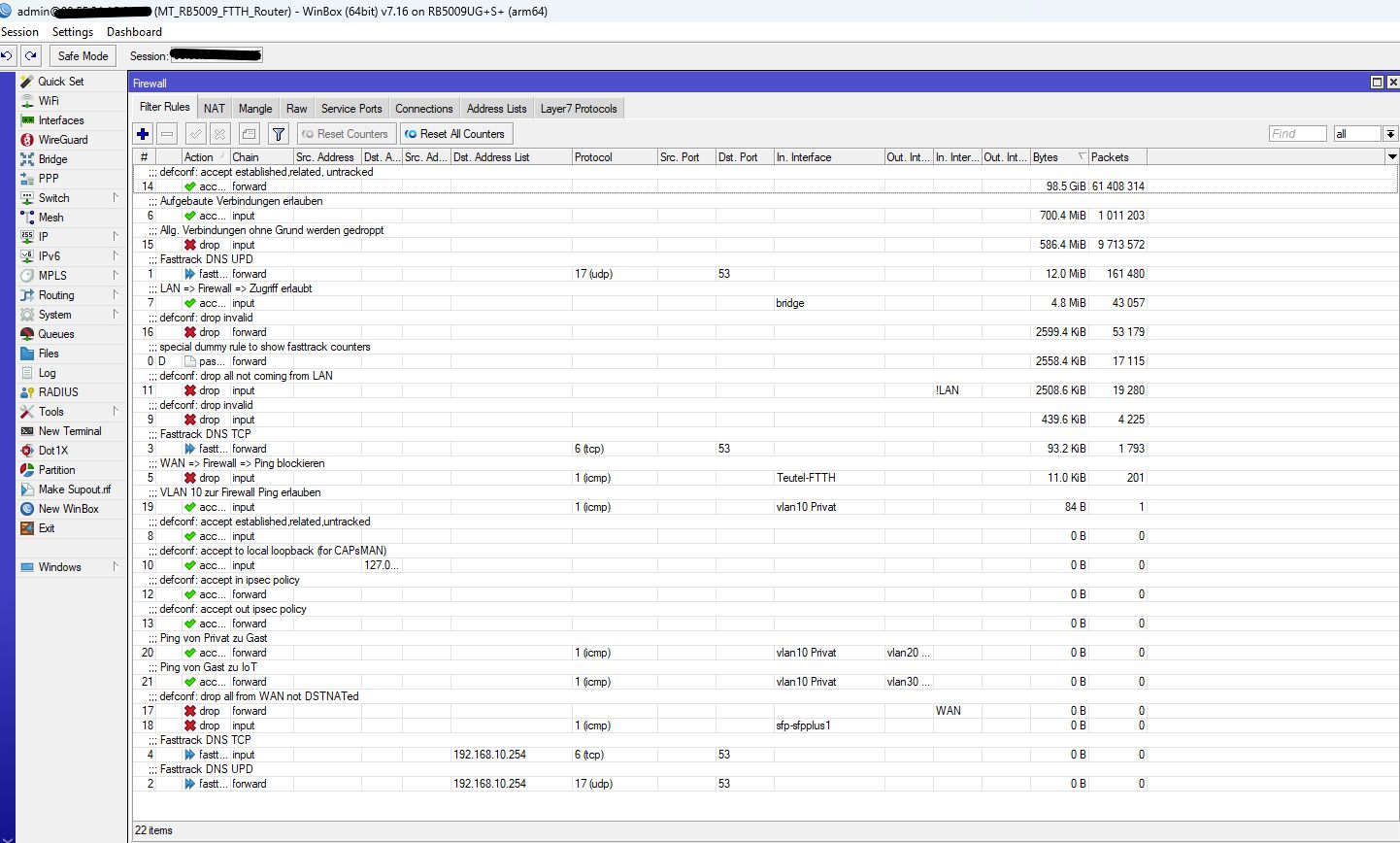
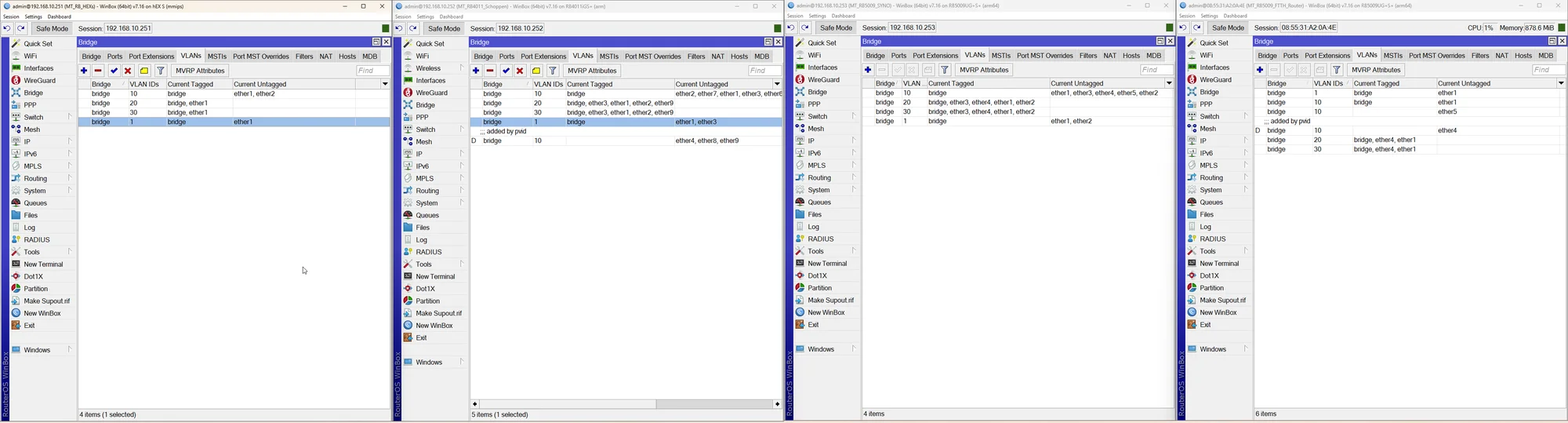
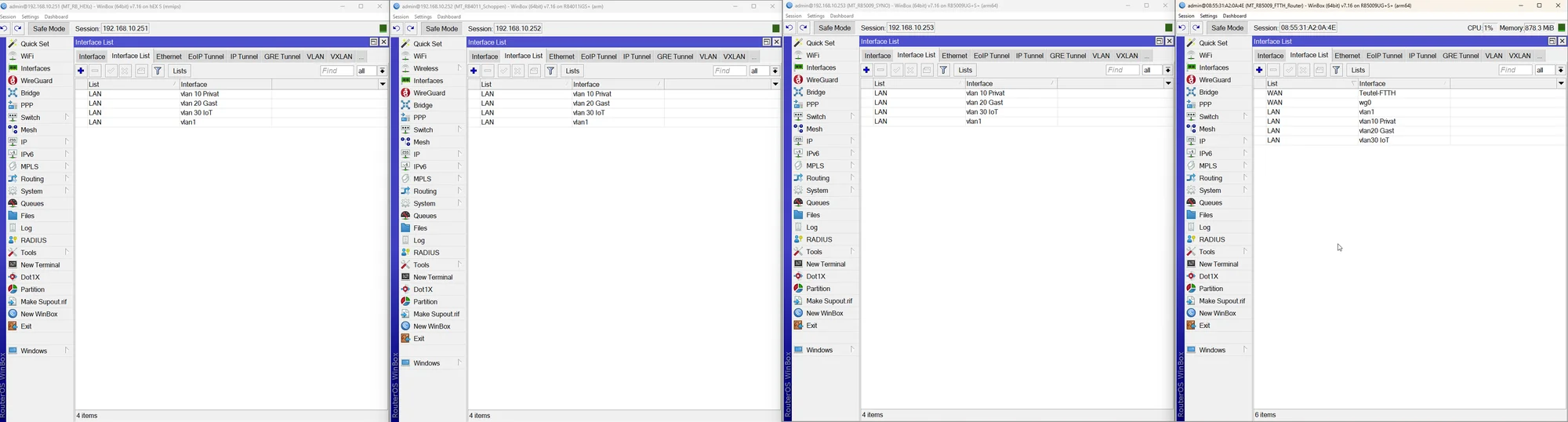
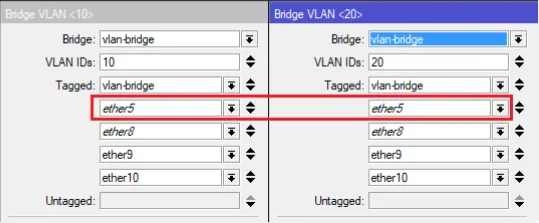
Checke nochmals alle deine Uplink Ports die FTTH, SYNO und Schoppen verbinden und deren PVID und VLAN Setting dort in der VLAN Bridge. Das ist dein "Backbone" an dem alles hängt.
Firewall Settings die ggf. IP Traffic zw. 10, 20 und 30 blocken hast du ja (noch) nicht aktiv, richtig?!
nirgendwo einen Reiter
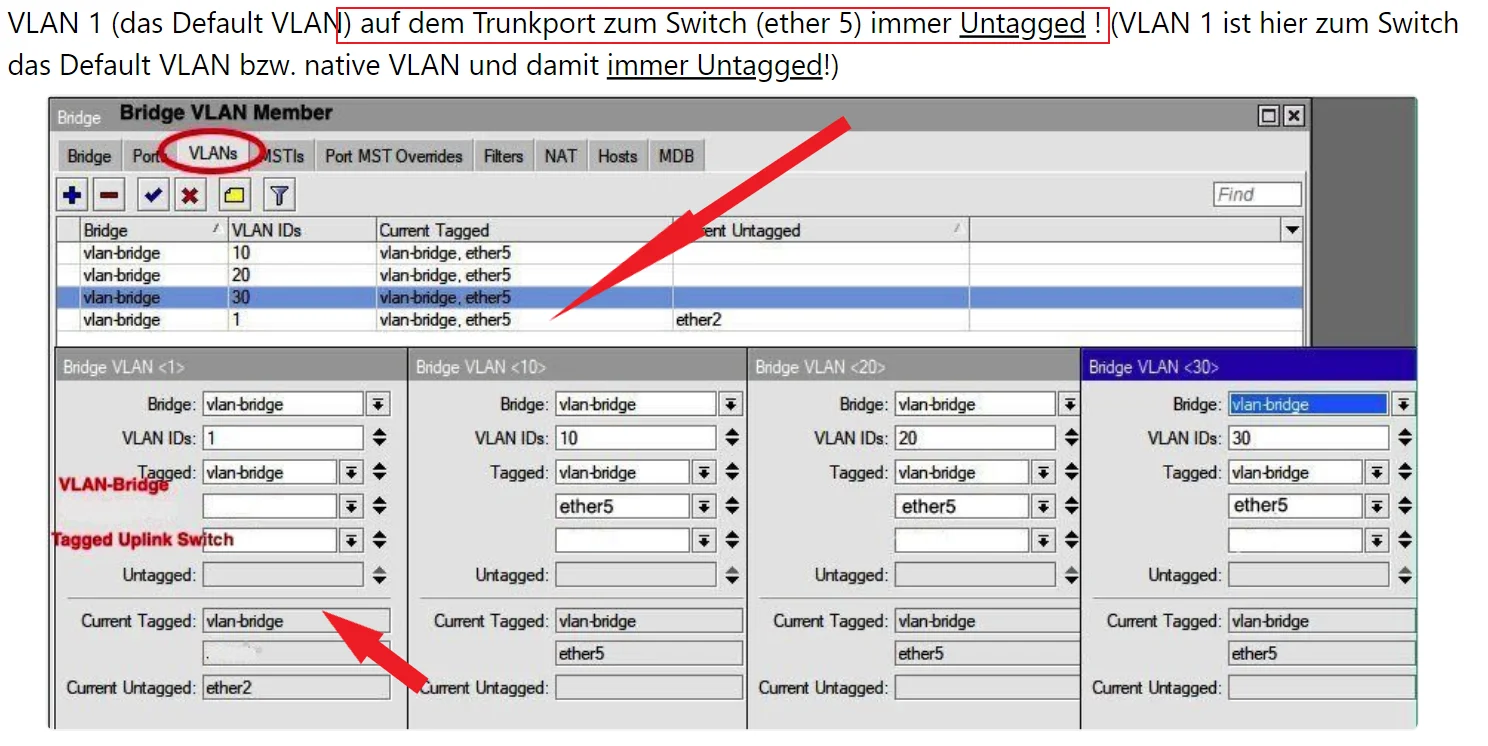
Ping ist (fast) immer Layer 3 also IP (ICMP Protokoll mit Echo Request/Reply). Da gibt man logischerweise niemals Layer 2 Interfaces an! 😉Trunkport zum Switch (ether 5) immer untagged...
Das hast du missverstanden weil du die wichtigste Information zurückgehalten hast. Die Aussage gilt NUR für das PVID VLAN auf diesen Trunks!!! Das steht doch alles auch haarklein im Tutorial.Ein Trunkport ist ja immer hybrid. Das PVID VLAN wird dort immer UNtagged übertragen alle anderen VLANs immer tagged! Ein Trunk transportiert also so immer beide Arten von Traffic egal ob man das PVID VLAN aktiv nutzt oder nicht.
Wenn, dann also bitte richtig zitieren!
Problem steht!
Unverständlich.Habe genau dein Setup hier mit einem RB2011 (der hat den UM) und 2mal RB750 nachgestellt und das funktioniert wie erwartet völlig einwandfrei! Hier allerdings mit VLAN 1 als PVID VLAN auf den 2 Trunklinks die die 3 Komponenten verbinden.
Da wieder die aktuellen Screenshots fehlen kann man hier also nur kristallkugeln das das Tagging bei dir falsch ist oder du vergessen hast die Bridge auf VLAN Filtering zu setzen usw.
Irgendeinen Kincken hast du da noch drin in den beiden Trunks.
Vielleicht macht es wirklich Sinn mal ganz neu anzufangen. Dann zuallererst mit dem Trunks.
sobald es über einen anderen Switch geht => flötepiepen!
Und wieder ein Indiz das bei deiner Trunk Konfiguration ein grober Fehler sein muss!! Ist ja eindeutig wenn dieser Traffic nicht von einem zum anderen Gerät über den Trunk transportiert wird. Hilfreich wäre gewesen wenn du die Trunkports in allen Geräten unter "Comment" mal korrekt benannt hättest anstatt ein nichtssagendes "defconf" dort zu belassen. Hilfe für Externe beim Troubleshooting sieht anders aus.
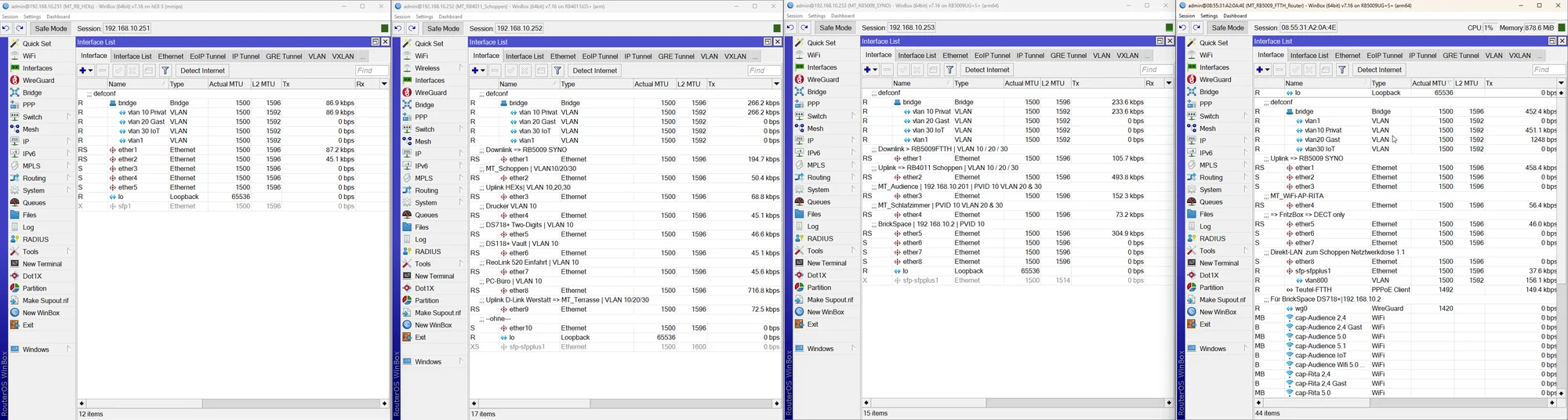
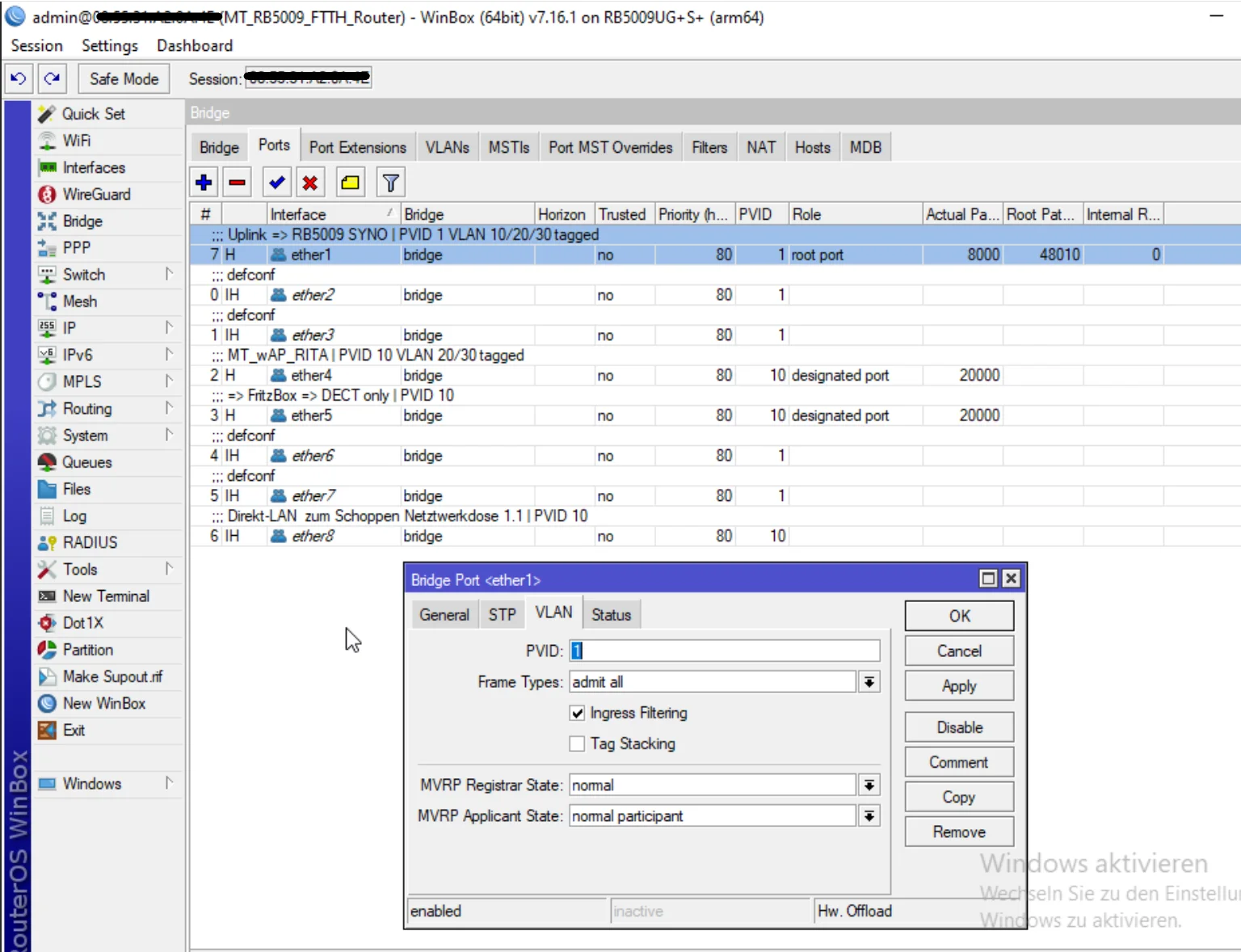
Habe ich vergessen, etwas zu knipsen?
Ja!!Das Wichtigste zur Überprüfung der Trunk Ports fehlt natürlich mal wieder. 😡
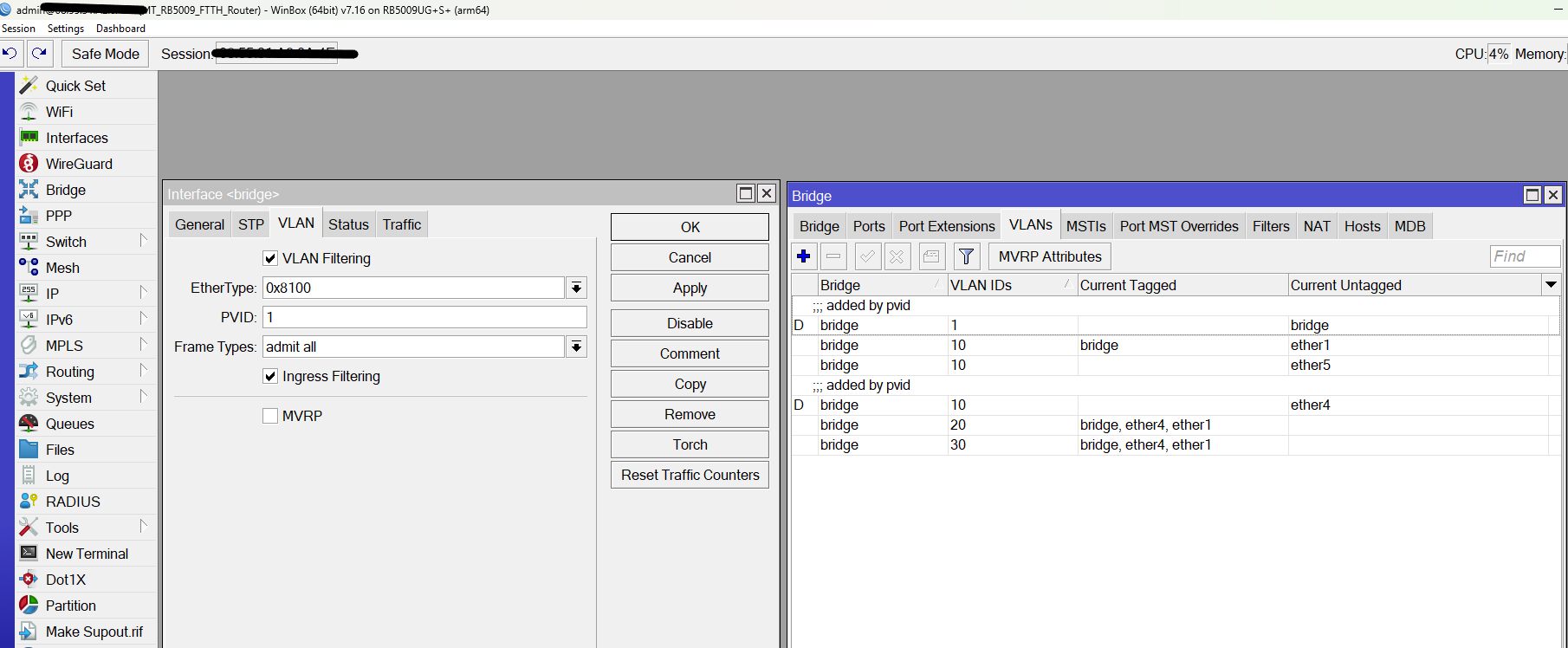
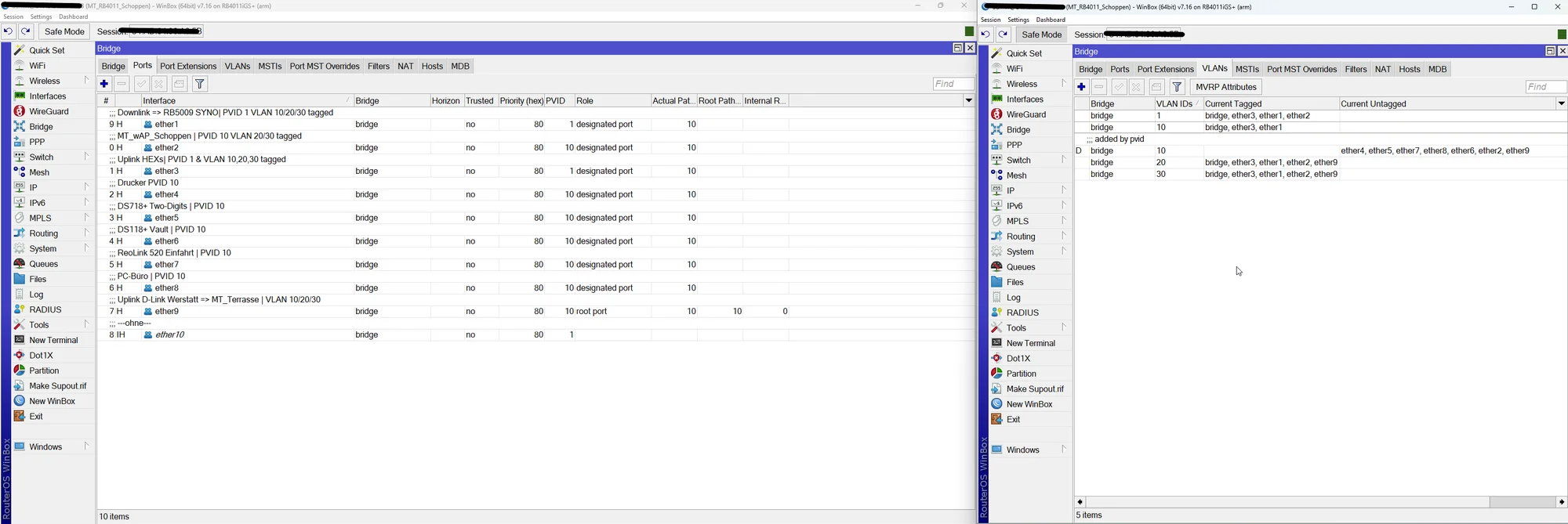
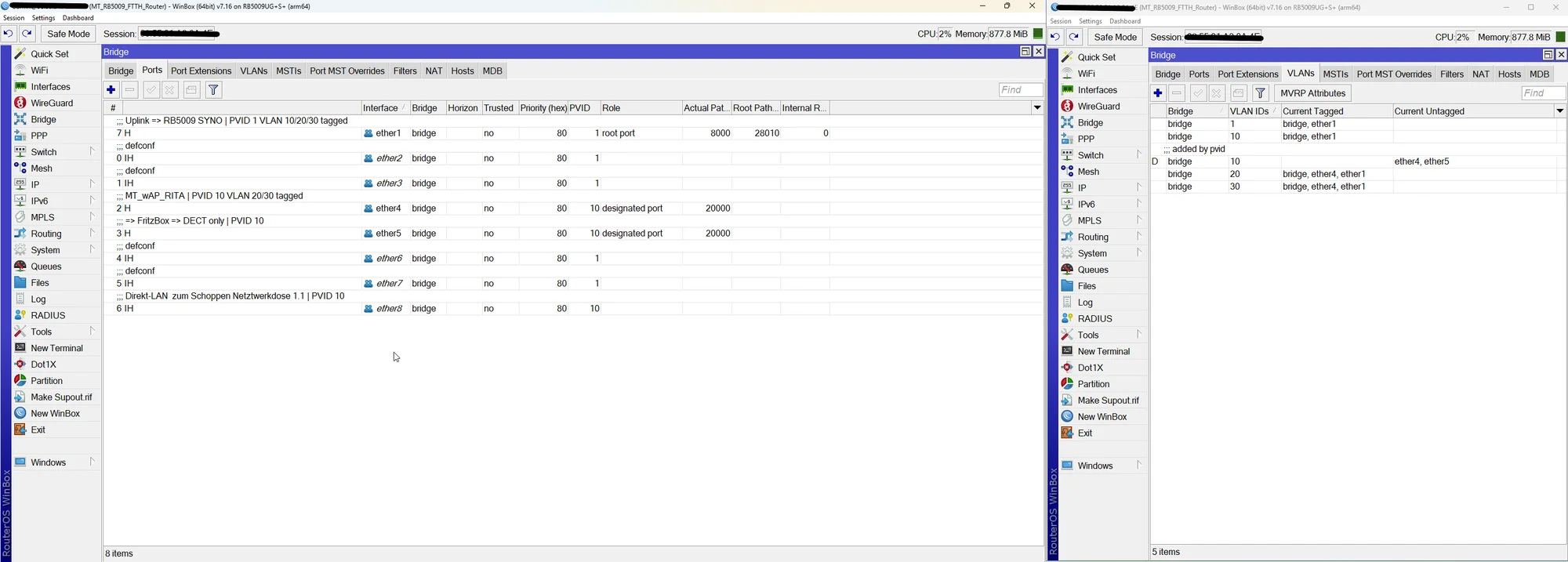
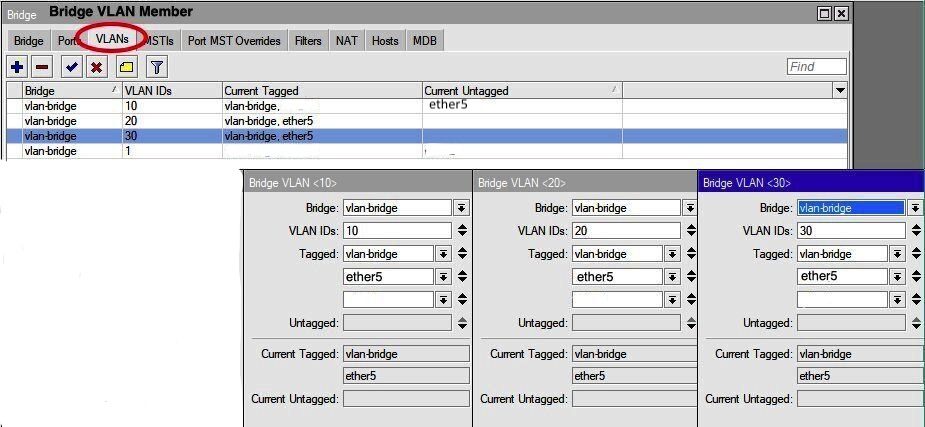
Das ist das VLAN Setting und Tagging der Trunk Ports in der Bridge plus deren PVID Einstellung.
Auf den ersten Blick kann man das Elend bei VLAN 10 schon sehen dessen Tagging FEHLT auf dem Trunk Ports.
Ob das jetzt richtig oder falsch ist hängt davon mit welchem PVID VLAN du nun arbeitest auf den Trunks! Hast du jetzt auf 1 umgestellt oder verwendest du weiterhin 10??
Nur noch einmal zur Erinnerung wie ALLE deine 4 Trunk Port Interfaces zw. den 3 Switches/Router auszusehen haben.
Das Beispiel geht davon aus das das PVID Interface 1 ist an den Trunkports. Hier beispielhaft mit 2 getagged übertragenen VLANs 10 und 20 also in Summer 3 aktiven VLANs auf dem Trunk:
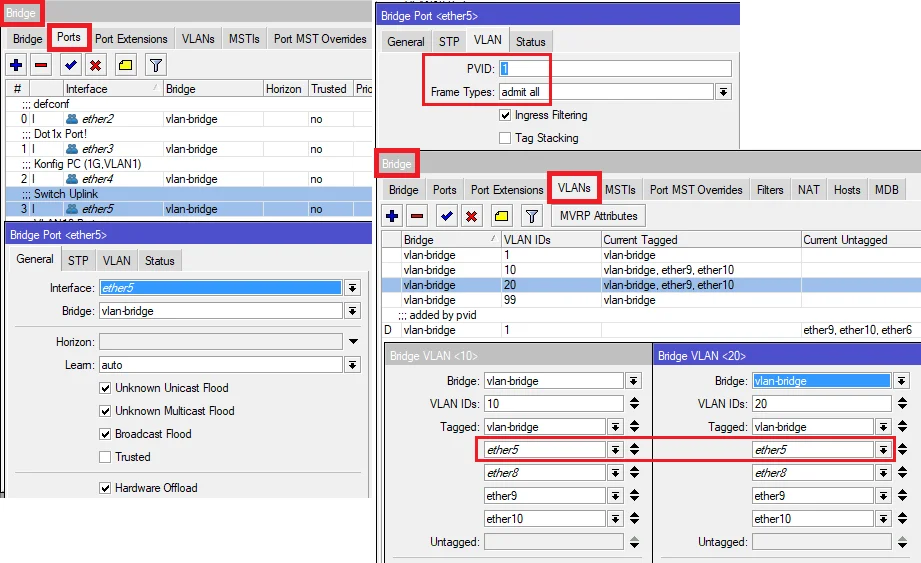 Für den Fall das du mit PVID 1 arbeitest achte darauf das du nicht in diese Falle bzgl. VLAN 1 tappst!
Für den Fall das du mit PVID 1 arbeitest achte darauf das du nicht in diese Falle bzgl. VLAN 1 tappst!
Das ist irrelevant wenn du mit PVID 10 arbeitest, deshalb ist es immer wichtig zu wissen welches PVID VLAN du durchgängig verwendest.
Das Beispiel geht davon aus das das PVID Interface 1 ist an den Trunkports. Hier beispielhaft mit 2 getagged übertragenen VLANs 10 und 20 also in Summer 3 aktiven VLANs auf dem Trunk:

Das ist irrelevant wenn du mit PVID 10 arbeitest, deshalb ist es immer wichtig zu wissen welches PVID VLAN du durchgängig verwendest.
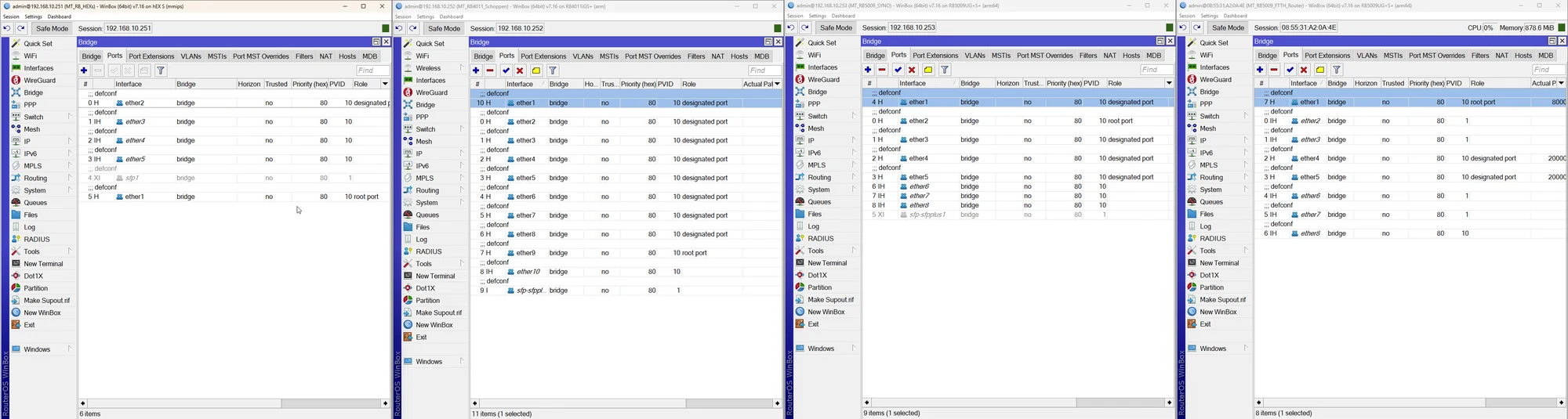
Die Trunkports sind alle auf PVID 1 mit VLAN 10/20/30 tagged, siehe Bilder.
Warum taucht dann z.B. beim "Schoppen" VLAN 1 tagged auch fälschlicherweise die Ports ether 1, 2 und auch 3 auf obwohl es PVID VLAN ist und diese Ports für VLAN 1 dann logischerweise NIE getagged sein dürfen?! Tagged und UNtagged zugleich geht ja nun mal nicht! Beim Syno ist es auch falsch ebenso beim FTTH was das Bridge VLAN1 betrifft.
Leider fehlt hier wieder einmal der ensprechende Screenshot zum Bridge VLAN 1 Setting der Tagged Ports! 😡
Wie oben dir schon mehrfach gepostet darf dort in den Tagged Portzuweisungen des VLAN 1 einzig und allein NUR die Bridge zugewiesen sein und keine weiteren Tagged Interfaces wie bei dir!! Ansonsten kollidiert das doch mit dem PVID Setting!
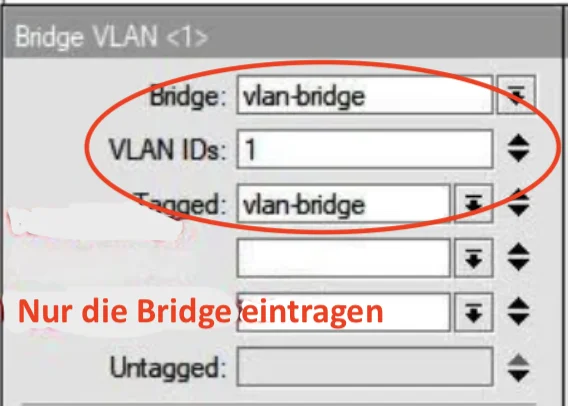
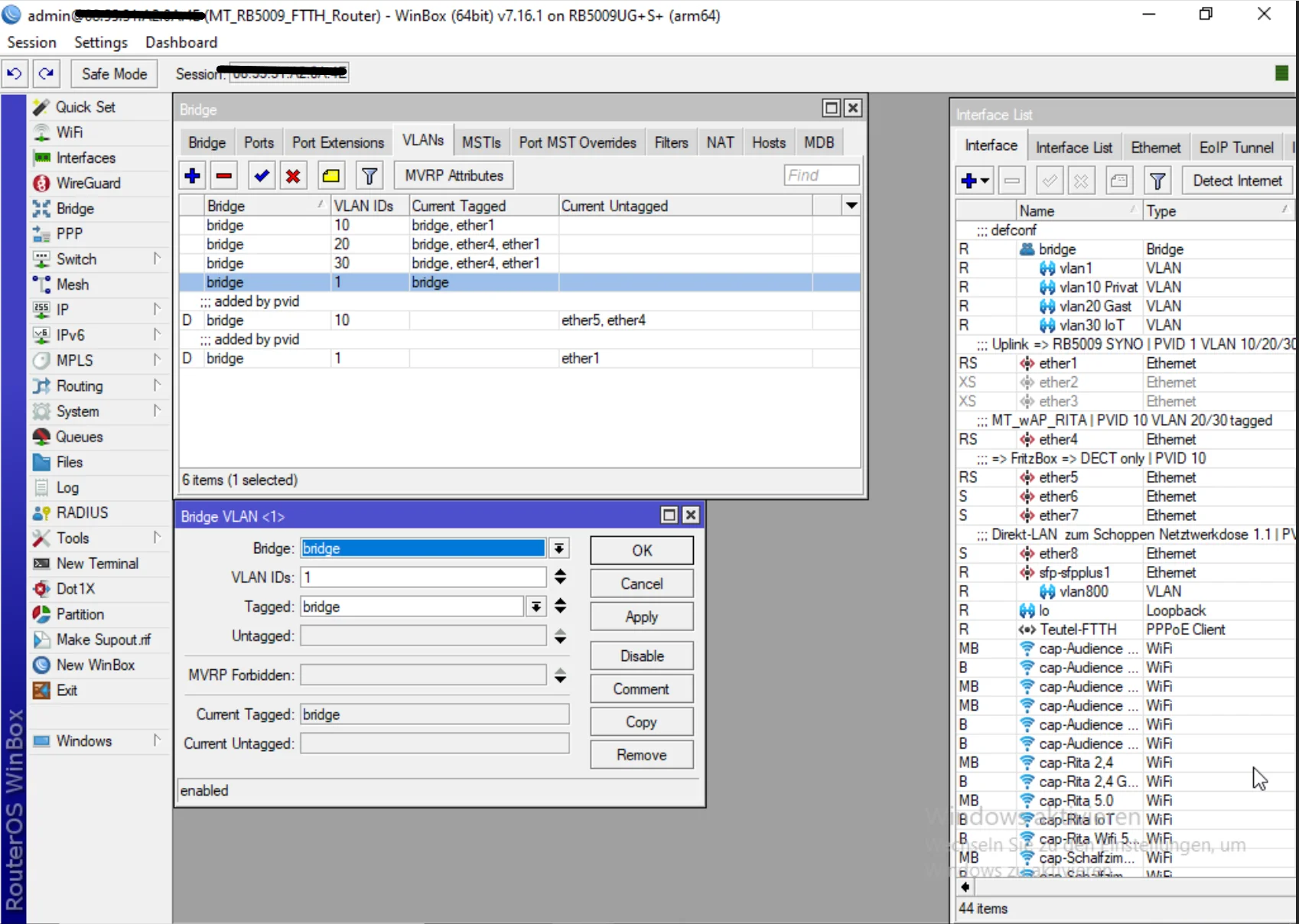
Soll ich davon auch solch Screenshots machen?
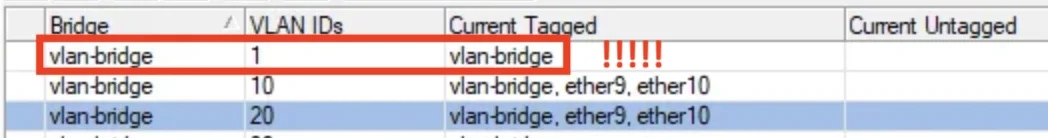
Alles gut. Soviel Vertrauen in dich haben wir hier schon... Einen Fehler sieht man oben aber noch: Das VLAN 10 darf dort niemals mit einem "D" als "added by pvid" dynamisch auftauchen wenn du nun auf 1 als Default VLAN umgestellt hast! Da ist irgendwo noch ein Fehler bzw. du hast vergessen diesen Eintrag dann ersatzlos zu löschen! Beim VLAN 1 als Default VLAN ist das normal, nicht aber bei VLAN 10.
Kann das immer noch zu dem Fehler führen, dass das VLAN 1 anfänglich dynamisch war?
Nein, sollte kein Fehler sein. Das ist nicht nur anfänglich so das ist immer so, weil es das 1er immer das Default VLAN istWarum die Clients nicht über die VLANs zwischen den Switches kommunizieren können
Wie gesagt, mit dem gleichen Backbone Setup hier mit RB2011 und 2mal RB750 im Testaufbau erwartungsgemäß OHNE jegliche Auffälligkeiten. Das ist ja auch ein klassisches Allerweltssetup wie es millionenfach in Firmen- und Heimnetzen zum Einsatz kommt. Das das fehlerlos funktioniert ist eigentlich auch klar, denn es sind ja alles absolute Standardfeatures die schon jahrelang stabil arbeiten die da konfiguriert sind. Kein Hexenwerk also...
es lag an der Synoloy.
Oha. In der Tat...darauf muss man erstmal kommen!Die Lernkurve bei Mikrotik ist sehr steil....
Na ja...stimmt ja eigentlich nicht wirklich, denn wenn andere Komponenten einen sauberen Netzwerk Betrieb torpedieren wäre das ja eine ganz falsche Schlussfolgerung.Aber nundenn... Hauptsache es rennt jetzt wie es soll. Case closed!! 👍