Pfsense VPN IPSEC zur FB 7530 ok zu 7590 nein
Hallo Leute,
Aktuell beschäftige ich mich mit dem Thema VPN Vernetzung Pfsense und Fritzboxen.
Ich habe seit längeren schon eine Aktive VPN IPSEC Verbindung zu einer FB 7530 laufen. Die Verbindung ist stabile und läuft.
Nun Wollte ich eine zweite FB 7590 mit aufnehmen in der Pfsense aber das klappt nicht es kommt keine verbindung zustande.
Zur FB 7530 wo die Verbindung klappt .
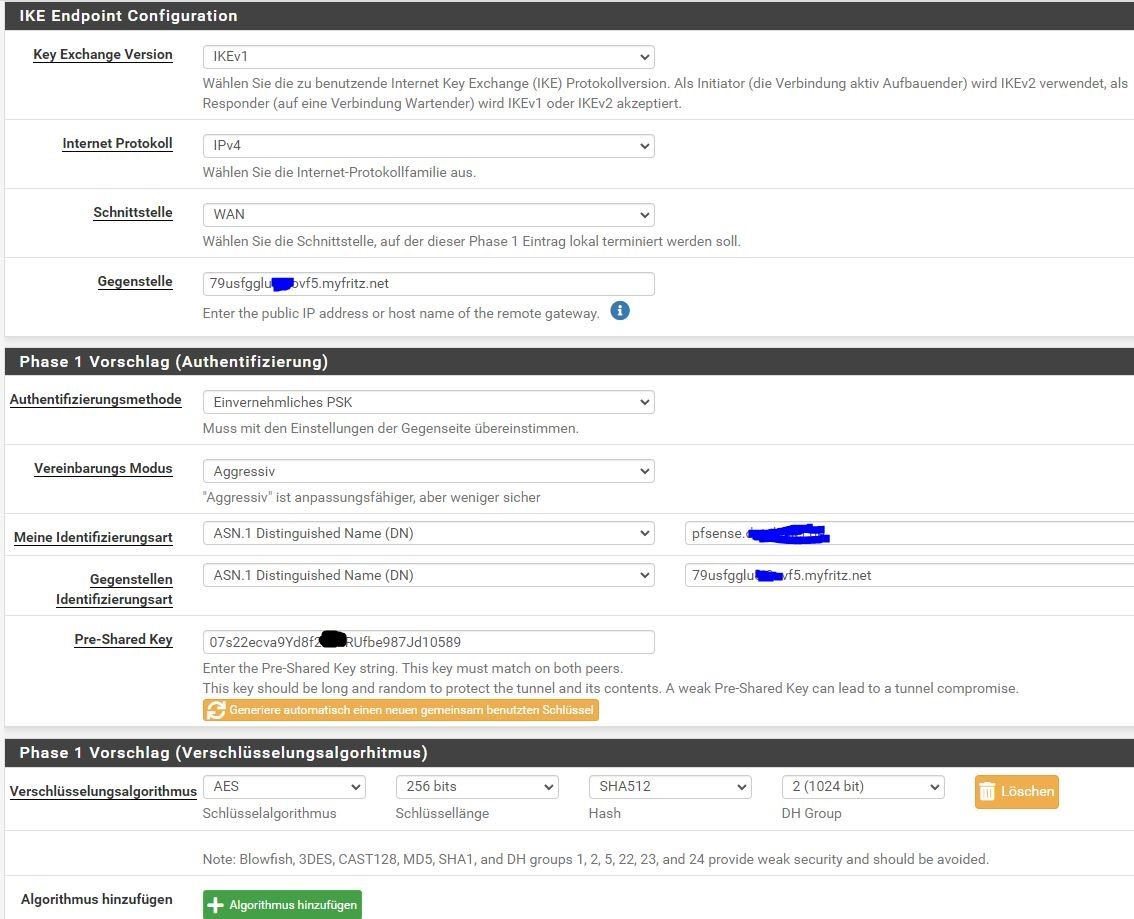
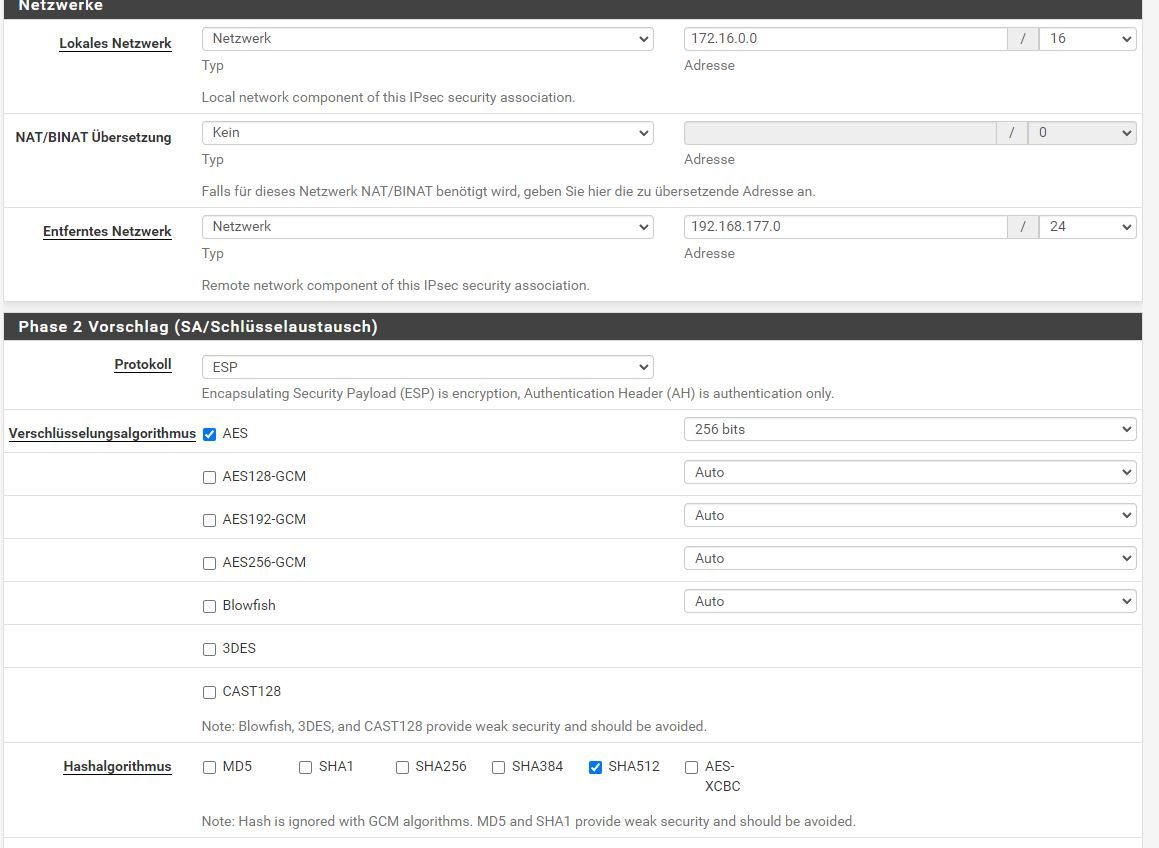
Zur 7590 dort klappt es nicht . alles gleich eingestellt außer ips und dyndns.
Was kann hier der Fehler sein?
Log:FB 7590
Log: FB 7530
Aktuell beschäftige ich mich mit dem Thema VPN Vernetzung Pfsense und Fritzboxen.
Ich habe seit längeren schon eine Aktive VPN IPSEC Verbindung zu einer FB 7530 laufen. Die Verbindung ist stabile und läuft.
Nun Wollte ich eine zweite FB 7590 mit aufnehmen in der Pfsense aber das klappt nicht es kommt keine verbindung zustande.
Zur FB 7530 wo die Verbindung klappt .


Zur 7590 dort klappt es nicht . alles gleich eingestellt außer ips und dyndns.
Was kann hier der Fehler sein?
Log:FB 7590
Dec 8 15:02:16 charon 18477 13[NET] <con4|1> sending packet: from 172.16.0.3[500] to 2.xxx.97.239[500] (377 bytes)
Dec 8 15:02:16 charon 18477 13[IKE] <con4|1> sending retransmit 2 of request message ID 0, seq 1
Dec 8 15:02:15 charon 18477 05[CFG] vici client 11 disconnected
Dec 8 15:02:15 charon 18477 02[CFG] vici client 11 requests: list-sas
Dec 8 15:02:15 charon 18477 05[CFG] vici client 11 registered for: list-sa
Dec 8 15:02:15 charon 18477 02[CFG] vici client 11 connected
Dec 8 15:02:10 charon 18477 08[CFG] vici client 7 disconnected
Dec 8 15:02:09 charon 18477 07[CFG] vici client 10 disconnected
Dec 8 15:02:09 charon 18477 07[CFG] vici client 10 requests: list-sas
Dec 8 15:02:09 charon 18477 06[CFG] vici client 10 registered for: list-sa
Dec 8 15:02:09 charon 18477 09[CFG] vici client 10 connected
Dec 8 15:02:09 charon 18477 11[NET] <con4|1> sending packet: from 172.16.0.3[500] to 2.xxx.97.239[500] (377 bytes)
Dec 8 15:02:09 charon 18477 11[IKE] <con4|1> sending retransmit 1 of request message ID 0, seq 1
Dec 8 15:02:07 charon 18477 14[CFG] vici client 9 disconnected
Dec 8 15:02:07 charon 18477 14[CFG] updated vici connection: con4
Dec 8 15:02:07 charon 18477 14[CFG] id = vfwxxxxxxx.myfritz.net
Dec 8 15:02:07 charon 18477 14[CFG] class = pre-shared key
Dec 8 15:02:07 charon 18477 14[CFG] remote:
Dec 8 15:02:07 charon 18477 14[CFG] id = pfsense.xxxxxller.de
Dec 8 15:02:07 charon 18477 14[CFG] class = pre-shared key
Dec 8 15:02:07 charon 18477 14[CFG] local:
Dec 8 15:02:07 charon 18477 14[CFG] if_id_out = 0
Dec 8 15:02:07 charon 18477 14[CFG] if_id_in = 0
Dec 8 15:02:07 charon 18477 14[CFG] proposals = IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_1024
Dec 8 15:02:07 charon 18477 14[CFG] rand_time = 2880
Dec 8 15:02:07 charon 18477 14[CFG] over_time = 2880
Dec 8 15:02:07 charon 18477 14[CFG] rekey_time = 0
Dec 8 15:02:07 charon 18477 14[CFG] reauth_time = 25920
Dec 8 15:02:07 charon 18477 14[CFG] keyingtries = 1
Dec 8 15:02:07 charon 18477 14[CFG] unique = UNIQUE_REPLACE
Dec 8 15:02:07 charon 18477 14[CFG] childless = 0
Dec 8 15:02:07 charon 18477 14[CFG] fragmentation = 2
Dec 8 15:02:07 charon 18477 14[CFG] dpd_timeout = 0
Dec 8 15:02:07 charon 18477 14[CFG] dpd_delay = 0
Dec 8 15:02:07 charon 18477 14[CFG] encap = 0
Dec 8 15:02:07 charon 18477 14[CFG] dscp = 0x00
Dec 8 15:02:07 charon 18477 14[CFG] aggressive = 1
Dec 8 15:02:07 charon 18477 14[CFG] mobike = 0
Dec 8 15:02:07 charon 18477 14[CFG] ppk_required = 0
Dec 8 15:02:07 charon 18477 14[CFG] ppk_id = (null)
Dec 8 15:02:07 charon 18477 14[CFG] send_cert = CERT_SEND_IF_ASKED
Dec 8 15:02:07 charon 18477 14[CFG] send_certreq = 1
Dec 8 15:02:07 charon 18477 14[CFG] remote_port = 500
Dec 8 15:02:07 charon 18477 14[CFG] local_port = 500
Dec 8 15:02:07 charon 18477 14[CFG] remote_addrs = vfxxxxxxp.myfritz.net
Dec 8 15:02:07 charon 18477 14[CFG] local_addrs = 172.16.0.3
Dec 8 15:02:07 charon 18477 14[CFG] version = 1
Dec 8 15:02:07 charon 18477 14[CFG] copy_dscp = out
Dec 8 15:02:07 charon 18477 14[CFG] copy_ecn = 1
Dec 8 15:02:07 charon 18477 14[CFG] copy_df = 1
Dec 8 15:02:07 charon 18477 14[CFG] sha256_96 = 0
Dec 8 15:02:07 charon 18477 14[CFG] hw_offload = no
Dec 8 15:02:07 charon 18477 14[CFG] remote_ts = 192.168.175.0/24|/0
Dec 8 15:02:07 charon 18477 14[CFG] local_ts = 172.16.0.0/16|/0
Dec 8 15:02:07 charon 18477 14[CFG] proposals = ESP:AES_CBC_256/HMAC_SHA2_512_256/MODP_1024/NO_EXT_SEQ
Dec 8 15:02:07 charon 18477 14[CFG] inactivity = 0
Dec 8 15:02:07 charon 18477 14[CFG] set_mark_out = 0/0
Dec 8 15:02:07 charon 18477 14[CFG] set_mark_in = 0/0
Dec 8 15:02:07 charon 18477 14[CFG] mark_out = 0/0
Dec 8 15:02:07 charon 18477 14[CFG] mark_in_sa = 0
Dec 8 15:02:07 charon 18477 14[CFG] mark_in = 0/0
Dec 8 15:02:07 charon 18477 14[CFG] if_id_out = 0
Dec 8 15:02:07 charon 18477 14[CFG] if_id_in = 0
Dec 8 15:02:07 charon 18477 14[CFG] interface = (null)
Dec 8 15:02:07 charon 18477 14[CFG] priority = 0
Dec 8 15:02:07 charon 18477 14[CFG] tfc = 0
Dec 8 15:02:07 charon 18477 14[CFG] reqid = 0
Dec 8 15:02:07 charon 18477 14[CFG] close_action = clear
Dec 8 15:02:07 charon 18477 14[CFG] start_action = hold
Dec 8 15:02:07 charon 18477 14[CFG] dpd_action = clear
Dec 8 15:02:07 charon 18477 14[CFG] policies_fwd_out = 0
Dec 8 15:02:07 charon 18477 14[CFG] policies = 1
Dec 8 15:02:07 charon 18477 14[CFG] mode = TUNNEL
Dec 8 15:02:07 charon 18477 14[CFG] ipcomp = 0
Dec 8 15:02:07 charon 18477 14[CFG] hostaccess = 0
Dec 8 15:02:07 charon 18477 14[CFG] updown = (null)
Dec 8 15:02:07 charon 18477 14[CFG] rand_packets = 0
Dec 8 15:02:07 charon 18477 14[CFG] life_packets = 0
Dec 8 15:02:07 charon 18477 14[CFG] rekey_packets = 0
Dec 8 15:02:07 charon 18477 14[CFG] rand_bytes = 0
Dec 8 15:02:07 charon 18477 14[CFG] life_bytes = 0
Dec 8 15:02:07 charon 18477 14[CFG] rekey_bytes = 0
Dec 8 15:02:07 charon 18477 14[CFG] rand_time = 360
Dec 8 15:02:07 charon 18477 14[CFG] life_time = 3600
Dec 8 15:02:07 charon 18477 14[CFG] rekey_time = 3240
Dec 8 15:02:07 charon 18477 14[CFG] child con4_4:
Dec 8 15:02:07 charon 18477 14[CFG] conn con4:
Dec 8 15:02:07 charon 18477 14[CFG] vici client 9 requests: load-conn
Dec 8 15:02:07 charon 18477 13[CFG] updated vici connection: bypass
Dec 8 15:02:07 charon 18477 13[CFG] remote:
Dec 8 15:02:07 charon 18477 13[CFG] local:
Dec 8 15:02:07 charon 18477 13[CFG] if_id_out = 0
Dec 8 15:02:07 charon 18477 13[CFG] if_id_in = 0
Dec 8 15:02:07 charon 18477 13[CFG] proposals = IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_CCM_16_128/AES_CCM_16_192/AES_CCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_CCM_12_128/AES_CCM_12_192/AES_CCM_12_256/AES_CCM_8_128/AES_CCM_8_192/AES_CCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
Dec 8 15:02:07 charon 18477 13[CFG] rand_time = 1440
Dec 8 15:02:07 charon 18477 13[CFG] over_time = 1440
Dec 8 15:02:07 charon 18477 13[CFG] rekey_time = 14400
Dec 8 15:02:07 charon 18477 13[CFG] reauth_time = 0
Dec 8 15:02:07 charon 18477 13[CFG] keyingtries = 1
Dec 8 15:02:07 charon 18477 13[CFG] unique = UNIQUE_NO
Dec 8 15:02:07 charon 18477 13[CFG] childless = 0
Dec 8 15:02:07 charon 18477 13[CFG] fragmentation = 2
Dec 8 15:02:07 charon 18477 13[CFG] dpd_timeout = 0
Dec 8 15:02:07 charon 18477 13[CFG] dpd_delay = 0
Dec 8 15:02:07 charon 18477 13[CFG] encap = 0
Dec 8 15:02:07 charon 18477 13[CFG] dscp = 0x00
Dec 8 15:02:07 charon 18477 13[CFG] aggressive = 0
Dec 8 15:02:07 charon 18477 13[CFG] mobike = 1
Dec 8 15:02:07 charon 18477 13[CFG] ppk_required = 0
Dec 8 15:02:07 charon 18477 13[CFG] ppk_id = (null)
Dec 8 15:02:07 charon 18477 13[CFG] send_cert = CERT_SEND_IF_ASKED
Dec 8 15:02:07 charon 18477 13[CFG] send_certreq = 1
Dec 8 15:02:07 charon 18477 13[CFG] remote_port = 500
Dec 8 15:02:07 charon 18477 13[CFG] local_port = 500
Dec 8 15:02:07 charon 18477 13[CFG] remote_addrs = 127.0.0.1
Dec 8 15:02:07 charon 18477 13[CFG] local_addrs = %any
Dec 8 15:02:07 charon 18477 13[CFG] version = 0
Dec 8 15:02:07 charon 18477 13[CFG] copy_dscp = out
Dec 8 15:02:07 charon 18477 13[CFG] copy_ecn = 1
Dec 8 15:02:07 charon 18477 13[CFG] copy_df = 1
Dec 8 15:02:07 charon 18477 13[CFG] sha256_96 = 0
Dec 8 15:02:07 charon 18477 13[CFG] hw_offload = no
Dec 8 15:02:07 charon 18477 13[CFG] remote_ts = 172.16.5.0/24|/0
Dec 8 15:02:07 charon 18477 13[CFG] local_ts = 172.16.5.0/24|/0
Dec 8 15:02:07 charon 18477 13[CFG] proposals = ESP:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256, ESP:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/NO_EXT_SEQ
Dec 8 15:02:07 charon 18477 13[CFG] inactivity = 0
Dec 8 15:02:07 charon 18477 13[CFG] set_mark_out = 0/0
Dec 8 15:02:07 charon 18477 13[CFG] set_mark_in = 0/0
Dec 8 15:02:07 charon 18477 13[CFG] mark_out = 0/0
Dec 8 15:02:07 charon 18477 13[CFG] mark_in_sa = 0
Dec 8 15:02:07 charon 18477 13[CFG] mark_in = 0/0
Dec 8 15:02:07 charon 18477 13[CFG] if_id_out = 0
Dec 8 15:02:07 charon 18477 13[CFG] if_id_in = 0
Dec 8 15:02:07 charon 18477 13[CFG] interface = (null)
Dec 8 15:02:07 charon 18477 13[CFG] priority = 0
Dec 8 15:02:07 charon 18477 13[CFG] tfc = 0
Dec 8 15:02:07 charon 18477 13[CFG] reqid = 0
Dec 8 15:02:07 charon 18477 13[CFG] close_action = clear
Dec 8 15:02:07 charon 18477 13[CFG] start_action = hold
Dec 8 15:02:07 charon 18477 13[CFG] dpd_action = clear
Dec 8 15:02:07 charon 18477 13[CFG] policies_fwd_out = 0
Dec 8 15:02:07 charon 18477 13[CFG] policies = 1
Dec 8 15:02:07 charon 18477 13[CFG] mode = PASS
Dec 8 15:02:07 charon 18477 13[CFG] ipcomp = 0
Dec 8 15:02:07 charon 18477 13[CFG] hostaccess = 0
Dec 8 15:02:07 charon 18477 13[CFG] updown = (null)
Dec 8 15:02:07 charon 18477 13[CFG] rand_packets = 0
Dec 8 15:02:07 charon 18477 13[CFG] life_packets = 0
Dec 8 15:02:07 charon 18477 13[CFG] rekey_packets = 0
Dec 8 15:02:07 charon 18477 13[CFG] rand_bytes = 0
Dec 8 15:02:07 charon 18477 13[CFG] life_bytes = 0
Dec 8 15:02:07 charon 18477 13[CFG] rekey_bytes = 0
Dec 8 15:02:07 charon 18477 13[CFG] rand_time = 360
Dec 8 15:02:07 charon 18477 13[CFG] life_time = 3960
Dec 8 15:02:07 charon 18477 13[CFG] rekey_time = 3600
Dec 8 15:02:07 charon 18477 13[CFG] child bypasslan:
Dec 8 15:02:07 charon 18477 13[CFG] conn bypass:
Dec 8 15:02:07 charon 18477 13[CFG] vici client 9 requests: load-conn
Dec 8 15:02:07 charon 18477 14[CFG] vici client 9 requests: get-conns
Dec 8 15:02:07 charon 18477 13[CFG] vici client 9 requests: get-pools
Dec 8 15:02:07 charon 18477 14[CFG] vici client 9 requests: get-authorities
Dec 8 15:02:07 charon 18477 14[CFG] loaded IKE shared key with id 'ike-2' for: 'vfxxxxx.myfritz.net'
Dec 8 15:02:07 charon 18477 14[CFG] vici client 9 requests: load-shared
Dec 8 15:02:07 charon 18477 05[CFG] loaded IKE shared key with id 'ike-1' for: '79xxxxxx.myfritz.net'
Dec 8 15:02:07 charon 18477 05[CFG] vici client 9 requests: load-shared
Dec 8 15:02:07 charon 18477 14[CFG] loaded IKE shared key with id 'ike-0' for: '%any', 'vfxxxxxx.myfritz.net'
Dec 8 15:02:07 charon 18477 14[CFG] vici client 9 requests: load-shared
Dec 8 15:02:07 charon 18477 05[CFG] vici client 9 requests: get-shared
Dec 8 15:02:07 charon 18477 02[CFG] vici client 9 requests: get-keys
Dec 8 15:02:07 charon 18477 02[CFG] vici client 9 connected
Dec 8 15:02:07 charon 18477 05[CFG] vici client 8 disconnected
Dec 8 15:02:07 charon 18477 02[CFG] loaded 0 RADIUS server configurations
Dec 8 15:02:07 charon 18477 02[CFG] loaded 5 entries for attr plugin configuration
Dec 8 15:02:07 charon 18477 02[CFG] loaded attribute (27675): 68:65:69:6d:6e:65:74:7a:2e:77:65:72:6b
Dec 8 15:02:07 charon 18477 02[CFG] loaded attribute (27674): 68:65:69:6d:6e:65:74:7a:2e:77:65:72:6b
Dec 8 15:02:07 charon 18477 02[CFG] loaded attribute UNITY_SPLIT_INCLUDE: 00:00:00:00:00:00:00:00
Dec 8 15:02:07 charon 18477 02[CFG] loaded attribute INTERNAL_IP4_SUBNET: 00:00:00:00:00:00:00:00
Dec 8 15:02:07 charon 18477 02[CFG] loaded attribute INTERNAL_IP4_DNS: ac:10:0a:01
Dec 8 15:02:07 charon 18477 02[CFG] ipseckey plugin is disabled
Dec 8 15:02:07 charon 18477 02[CFG] vici client 8 requests: reload-settings
Dec 8 15:02:07 charon 18477 05[CFG] vici client 8 connected
Dec 8 15:02:05 charon 18477 09[NET] <con4|1> sending packet: from 172.16.0.3[500] to 2.xxx.97.239[500] (377 bytes)
Dec 8 15:02:05 charon 18477 09[ENC] <con4|1> generating AGGRESSIVE request 0 [ SA KE No ID V V V V V ]
Dec 8 15:02:05 charon 18477 09[CFG] <con4|1> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_1024
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> IKE_SA con4[1] state change: CREATED => CONNECTING
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> initiating Aggressive Mode IKE_SA con4[1] to 2.203.97.239
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> sending NAT-T (RFC 3947) vendor ID
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> sending FRAGMENTATION vendor ID
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> sending DPD vendor ID
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> sending XAuth vendor ID
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> activating ISAKMP_NATD task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> activating ISAKMP_CERT_POST task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> activating AGGRESSIVE_MODE task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> activating ISAKMP_CERT_PRE task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> activating ISAKMP_VENDOR task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> activating new tasks
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> queueing QUICK_MODE task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> queueing ISAKMP_NATD task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> queueing ISAKMP_CERT_POST task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> queueing AGGRESSIVE_MODE task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> queueing ISAKMP_CERT_PRE task
Dec 8 15:02:05 charon 18477 09[IKE] <con4|1> queueing ISAKMP_VENDOR task
Dec 8 15:02:05 charon 18477 08[CFG] vici initiate CHILD_SA 'con4_4'
Dec 8 15:02:05 charon 18477 08[CFG] vici client 7 requests: initiate
Dec 8 15:02:05 charon 18477 09[CFG] vici client 7 registered for: control-log
Dec 8 15:02:05 charon 18477 11[CFG] vici client 7 connected
Dec 8 15:02:05 charon 18477 09[CFG] vici client 6 disconnected
Dec 8 15:02:05 charon 18477 11[CFG] vici client 6 requests: list-sas
Dec 8 15:02:05 charon 18477 11[CFG] vici client 6 registered for: list-sa
Dec 8 15:02:05 charon 18477 11[CFG] vici client 6 connected
Dec 8 15:02:04 charon 18477 11[CFG] vici client 5 disconnected
Dec 8 15:02:04 charon 18477 12[CFG] vici client 5 requests: list-sas
Dec 8 15:02:04 charon 18477 12[CFG] vici client 5 registered for: list-sa
Dec 8 15:02:04 charon 18477 11[CFG] vici client 5 connected
Dec 8 15:02:03 charon 18477 15[CFG] vici client 4 disconnected
Dec 8 15:02:03 charon 18477 11[CFG] vici client 4 requests: list-sas
Dec 8 15:02:03 charon 18477 15[CFG] vici client 4 registered for: list-sa
Dec 8 15:02:03 charon 18477 15[CFG] vici client 4 connectedLog: FB 7530
Dec 8 15:06:00 charon 18477 10[CFG] vici client 56 disconnected
Dec 8 15:06:00 charon 18477 07[CFG] vici client 56 requests: list-sas
Dec 8 15:06:00 charon 18477 10[CFG] vici client 56 registered for: list-sa
Dec 8 15:06:00 charon 18477 08[CFG] vici client 56 connected
Dec 8 15:05:58 charon 18477 08[CFG] vici client 54 disconnected
Dec 8 15:05:58 charon 18477 08[IKE] <con1|2> nothing to initiate
Dec 8 15:05:58 charon 18477 08[IKE] <con1|2> activating new tasks
Dec 8 15:05:58 charon 18477 08[NET] <con1|2> sending packet: from 172.16.0.3[4500] to 91.xxx.26.109[4500] (108 bytes)
Dec 8 15:05:58 charon 18477 08[ENC] <con1|2> generating QUICK_MODE request 3509667092 [ HASH ]
Dec 8 15:05:58 charon 18477 08[IKE] <con1|2> QUICK_MODE task
Dec 8 15:05:58 charon 18477 08[IKE] <con1|2> reinitiating already active tasks
Dec 8 15:05:58 charon 18477 08[CHD] <con1|2> CHILD_SA con1_1{3} state change: INSTALLING => INSTALLED
Dec 8 15:05:58 charon 18477 08[IKE] <con1|2> CHILD_SA con1_1{3} established with SPIs c3e49f74_i 5c7b3509_o and TS 172.16.0.0/16|/0 === 192.168.177.0/24|/0
Dec 8 15:05:58 charon 18477 08[CHD] <con1|2> SPI 0x5c7b3509, src 172.16.0.3 dst 91.xxx.26.109
Dec 8 15:05:58 charon 18477 08[CHD] <con1|2> adding outbound ESP SA
Dec 8 15:05:58 charon 18477 08[CHD] <con1|2> SPI 0xc3e49f74, src 91.xxx.26.109 dst 172.16.0.3
Dec 8 15:05:58 charon 18477 08[CHD] <con1|2> adding inbound ESP SA
Dec 8 15:05:58 charon 18477 08[CHD] <con1|2> using HMAC_SHA2_512_256 for integrity
Dec 8 15:05:58 charon 18477 08[CHD] <con1|2> using AES_CBC for encryption
Dec 8 15:05:58 charon 18477 08[CHD] <con1|2> CHILD_SA con1_1{3} state change: CREATED => INSTALLING
Dec 8 15:05:58 charon 18477 08[CFG] <con1|2> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_512_256/MODP_1024/NO_EXT_SEQ
Dec 8 15:05:58 charon 18477 08[CFG] <con1|2> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_512_256/MODP_1024/NO_EXT_SEQ
Dec 8 15:05:58 charon 18477 08[CFG] <con1|2> received proposals: ESP:AES_CBC_256/HMAC_SHA2_512_256/MODP_1024/NO_EXT_SEQ
Dec 8 15:05:58 charon 18477 08[CFG] <con1|2> proposal matches
Dec 8 15:05:58 charon 18477 08[CFG] <con1|2> selecting proposal:
Dec 8 15:05:58 charon 18477 08[ENC] <con1|2> parsed QUICK_MODE response 3509667092 [ HASH SA No KE ID ID ]
Dec 8 15:05:58 charon 18477 08[NET] <con1|2> received packet: from 91.xxx.26.109[4500] to 172.16.0.3[4500] (348 bytes)
Dec 8 15:05:57 charon 18477 08[NET] <con1|2> sending packet: from 172.16.0.3[4500] to 91.xxx.26.109[4500] (364 bytes)
Dec 8 15:05:57 charon 18477 08[ENC] <con1|2> generating QUICK_MODE request 3509667092 [ HASH SA No KE ID ID ]
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> 192.168.177.0/24|/0
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> proposing traffic selectors for other:
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> 172.16.0.0/16|/0
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> proposing traffic selectors for us:
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_512_256/MODP_1024/NO_EXT_SEQ
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_512_256/MODP_1024/NO_EXT_SEQ
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> activating QUICK_MODE task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> activating new tasks
Dec 8 15:05:57 charon 18477 08[NET] <con1|2> sending packet: from 172.16.0.3[4500] to 91.xxx.26.109[4500] (236 bytes)
Dec 8 15:05:57 charon 18477 08[ENC] <con1|2> generating AGGRESSIVE request 0 [ HASH NAT-D NAT-D ]
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> maximum IKE_SA lifetime 28022s
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> scheduling reauthentication in 25142s
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> IKE_SA con1[2] state change: CONNECTING => ESTABLISHED
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> IKE_SA con1[2] established between 172.16.0.3[pfsense.dxxx.de]...91.xxx.26.109[79xxxx.myfritz.net]
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> AGGRESSIVE_MODE task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> ISAKMP_VENDOR task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> reinitiating already active tasks
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> local host is behind NAT, sending keep alives
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_1024
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_1024
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> received proposals: IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_1024
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> proposal matches
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> selecting proposal:
Dec 8 15:05:57 charon 18477 08[ENC] <con1|2> received unknown vendor ID: a2:22:6f:c3:64:50:0f:56:34:ff:77:db:3b:74:f4:1b
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> received draft-ietf-ipsec-nat-t-ike-03 vendor ID
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> received NAT-T (RFC 3947) vendor ID
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> received DPD vendor ID
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> received XAuth vendor ID
Dec 8 15:05:57 charon 18477 08[ENC] <con1|2> parsed AGGRESSIVE response 0 [ SA KE No ID HASH N((24576)) V V V V V V NAT-D NAT-D ]
Dec 8 15:05:57 charon 18477 08[NET] <con1|2> received packet: from 91.xxx.26.109[500] to 172.16.0.3[500] (624 bytes)
Dec 8 15:05:57 charon 18477 08[NET] <con1|2> sending packet: from 172.16.0.3[500] to 91.xxx.26.109[500] (377 bytes)
Dec 8 15:05:57 charon 18477 08[ENC] <con1|2> generating AGGRESSIVE request 0 [ SA KE No ID V V V V V ]
Dec 8 15:05:57 charon 18477 11[CFG] vici client 55 disconnected
Dec 8 15:05:57 charon 18477 08[CFG] <con1|2> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_1024
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> IKE_SA con1[2] state change: CREATED => CONNECTING
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> initiating Aggressive Mode IKE_SA con1[2] to 91.xxx.26.109
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> sending draft-ietf-ipsec-nat-t-ike-02\n vendor ID
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> sending NAT-T (RFC 3947) vendor ID
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> sending FRAGMENTATION vendor ID
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> sending DPD vendor ID
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> sending XAuth vendor ID
Dec 8 15:05:57 charon 18477 05[CFG] vici initiate CHILD_SA 'con1_2'
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> activating ISAKMP_NATD task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> activating ISAKMP_CERT_POST task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> activating AGGRESSIVE_MODE task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> activating ISAKMP_CERT_PRE task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> activating ISAKMP_VENDOR task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> activating new tasks
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> queueing QUICK_MODE task
Dec 8 15:05:57 charon 18477 05[CFG] vici client 55 requests: initiate
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> queueing ISAKMP_NATD task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> queueing ISAKMP_CERT_POST task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> queueing AGGRESSIVE_MODE task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> queueing ISAKMP_CERT_PRE task
Dec 8 15:05:57 charon 18477 08[IKE] <con1|2> queueing ISAKMP_VENDOR task
Dec 8 15:05:57 charon 18477 12[CFG] vici client 55 registered for: control-log
Dec 8 15:05:57 charon 18477 12[CFG] vici client 55 connected
Dec 8 15:05:57 charon 18477 09[CFG] vici initiate CHILD_SA 'con1_1'
Dec 8 15:05:57 charon 18477 09[CFG] vici client 54 requests: initiate
Dec 8 15:05:57 charon 18477 08[CFG] vici client 54 registered for: control-log
Dec 8 15:05:57 charon 18477 09[CFG] vici client 54 connected
Dec 8 15:05:57 charon 18477 15[CFG] vici client 53 disconnected
Dec 8 15:05:57 charon 18477 09[CFG] vici client 53 requests: list-sas
Dec 8 15:05:57 charon 18477 02[CFG] vici client 53 registered for: list-sa
Dec 8 15:05:57 charon 18477 09[CFG] vici client 53 connectedBitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 4894833589
Url: https://administrator.de/forum/pfsense-vpn-ipsec-zur-fb-7530-ok-zu-7590-nein-4894833589.html
Ausgedruckt am: 18.07.2025 um 03:07 Uhr
4 Kommentare
Neuester Kommentar
Mahlzeit.
Anonymisiere mal den Bereich in den Codetags. Da sind noch einige Dinge erkennbar.
Das sieht komisch aus bei der 7590. hast du auf beiden Seiten dasselbe Subnetz?
Gruß
Marc
Anonymisiere mal den Bereich in den Codetags. Da sind noch einige Dinge erkennbar.
Dec 8 15:02:07 charon 18477 13[CFG] remote_ts = 172.16.5.0/24|/0
Dec 8 15:02:07 charon 18477 13[CFG] local_ts = 172.16.5.0/24|/0Das sieht komisch aus bei der 7590. hast du auf beiden Seiten dasselbe Subnetz?
Gruß
Marc
Das hier wundert mich auch etwas:
Bei "local_addrs" sollte ja eigentlich die eigene, externe IP stehen. Zumindest ist das bei meinen Tunneln im Firewall Log immer so.
Gruß
Marc
Dec 8 15:02:07 charon 18477 14[CFG] remote_addrs = vfxxxxxxp.myfritz.net
Dec 8 15:02:07 charon 18477 14[CFG] local_addrs = 172.16.0.3Bei "local_addrs" sollte ja eigentlich die eigene, externe IP stehen. Zumindest ist das bei meinen Tunneln im Firewall Log immer so.
Gruß
Marc
Hast du testweise mal das AES auf "Auto" gesetzt?
Im Gegensatz zur 2ten FB selected die erste keines der Proposals
Haben die FBs unterschiedliche FritzOS Versionen?
Der Fehler ist aber mit ziemlicher Sicherheit deine falsche FritzBox VPN Konfig Datei oder die der pfSense je nachdem von welcher Seite man es sieht.
Hier hast du einen gravierenden Fehler in der Phase 2 Konfig der FritzBox Datei begangen!
Dort gibst du das remote Netz der pfSense unter phase2remoteid mit einem ganz anderen IP Netz und 24 Bit Prefix an obwohl in der pfSense ein 16 Bit Prefix für deren lokales Netz (172.16.0.0) in der Phase 2 definiert ist.
Das kann dann niemals klappen weil es zu einem Phase 2 Mismatch beim Tunnelaufbau führt. Die P2 Parameter müssen verständlicherweise beidseitig gleich sein.
Also entweder musst du die pfSense in der Phase 2 auf die FritzBox anpassen oder umgegekehrt.
Was die remoteIP anbetrifft kann man das so machen. Die FBs arbeiten dann mit "0.0.0.0" rein als VPN Responder und die pfSense ist immer Initiator. Wie Kollege @radiogugu oben sagt wäre es konfigtechnisch besser auch die WAN IP der pfSense Firewall in der FritzBox statt 0.0.0.0 zu setzen. So können beide Seiten den Tunnel aufbauen bzw. auch VPN Initiator sein.
Im Gegensatz zur 2ten FB selected die erste keines der Proposals
selected proposal: ESP:AES_CBC_256/HMAC_SHA2_512_256/MODP_1024/NO_EXT_SEQ
Das gesamte Proposal Handshaking fehlt da. Ohne akzeptiertes Proposal kein Tunnel...Haben die FBs unterschiedliche FritzOS Versionen?
Der Fehler ist aber mit ziemlicher Sicherheit deine falsche FritzBox VPN Konfig Datei oder die der pfSense je nachdem von welcher Seite man es sieht.
Hier hast du einen gravierenden Fehler in der Phase 2 Konfig der FritzBox Datei begangen!
Dort gibst du das remote Netz der pfSense unter phase2remoteid mit einem ganz anderen IP Netz und 24 Bit Prefix an obwohl in der pfSense ein 16 Bit Prefix für deren lokales Netz (172.16.0.0) in der Phase 2 definiert ist.
Das kann dann niemals klappen weil es zu einem Phase 2 Mismatch beim Tunnelaufbau führt. Die P2 Parameter müssen verständlicherweise beidseitig gleich sein.
Also entweder musst du die pfSense in der Phase 2 auf die FritzBox anpassen oder umgegekehrt.
- phase2localid = 192.168.177.0 mask 255.255.255.0
- phase2remoteid = 172.16.0.0 mask 255.255.0.0
Was die remoteIP anbetrifft kann man das so machen. Die FBs arbeiten dann mit "0.0.0.0" rein als VPN Responder und die pfSense ist immer Initiator. Wie Kollege @radiogugu oben sagt wäre es konfigtechnisch besser auch die WAN IP der pfSense Firewall in der FritzBox statt 0.0.0.0 zu setzen. So können beide Seiten den Tunnel aufbauen bzw. auch VPN Initiator sein.