MikroTik S2S IPSec Tunnel - kein Ping der Gegenstelle möglich
Hallo zuammen,
ich experimentiere gerade mit zwei MikroTik Routern und VPN Techniken herum.
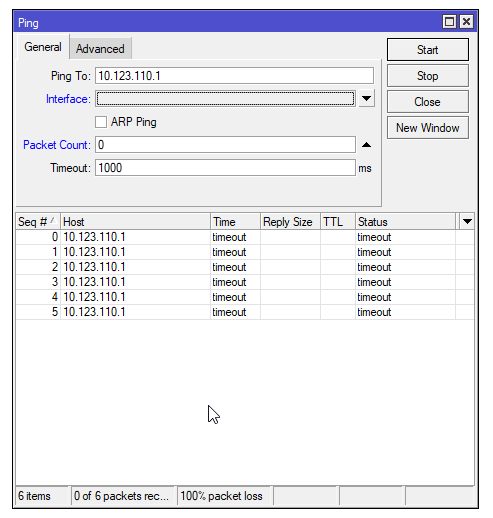
Ich schaffe es nicht, dass ich von der einen MikroTik die andere via IPSec Tunnel pingen kann.
Beim Ping einfach einen Timeout.
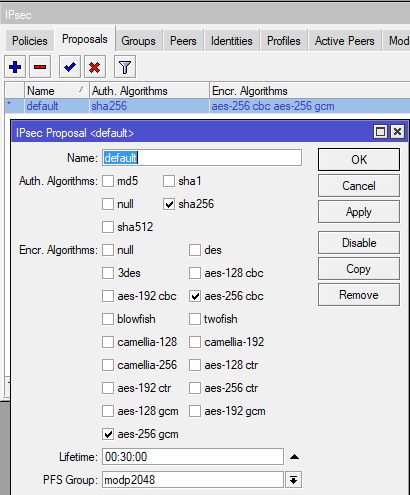
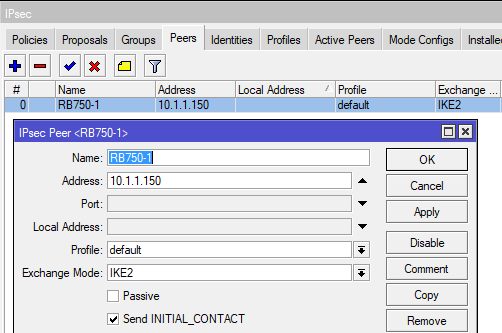
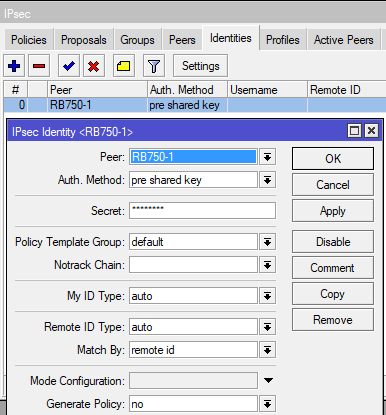
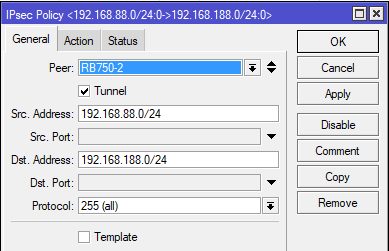
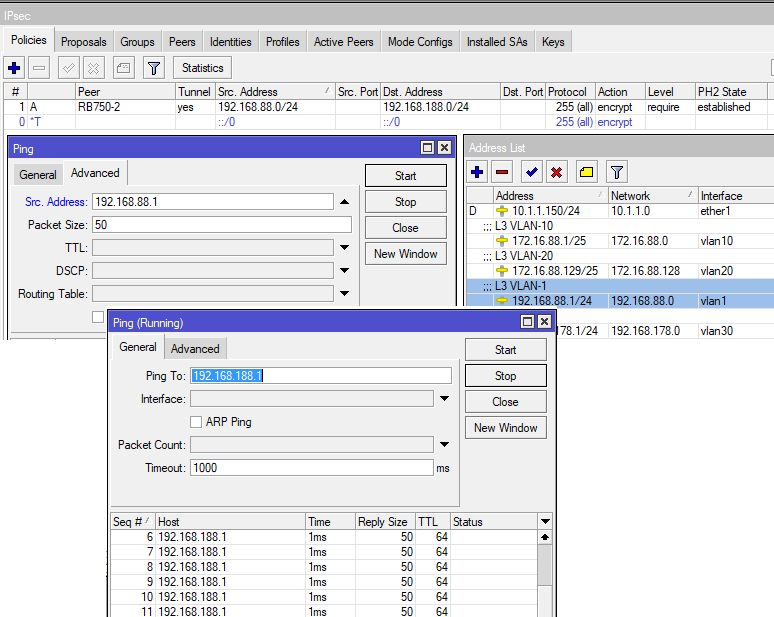
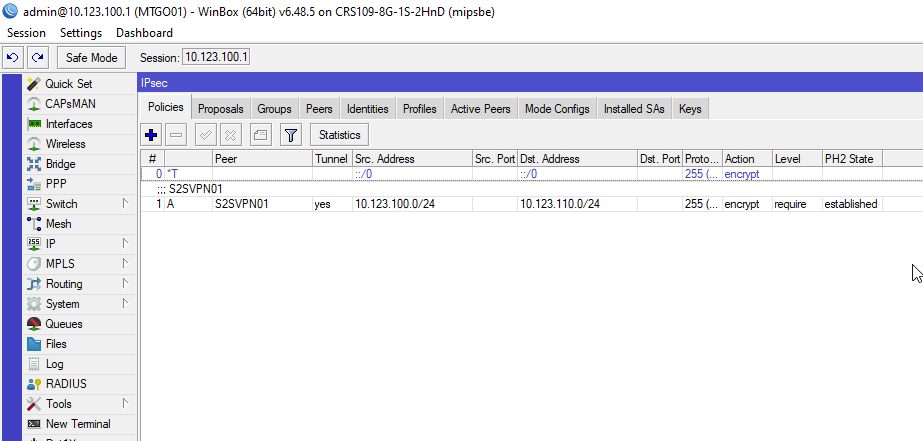
Tunnel baut sich auf:
Konfig Seite 1:
Konfig Seite 2:
Hoffe einer der MikroTik Experten hat einen Tip, was ich falsch mache.
mit freundlichen Grüßen
Nemesis
ich experimentiere gerade mit zwei MikroTik Routern und VPN Techniken herum.
Ich schaffe es nicht, dass ich von der einen MikroTik die andere via IPSec Tunnel pingen kann.
Beim Ping einfach einen Timeout.
Tunnel baut sich auf:

Konfig Seite 1:
# nov/21/2021 17:39:10 by RouterOS 6.48.5
# software id = H7LJ-IN76
#
# model = CRS109-8G-1S-2HnD
# serial number = 00000001
/interface bridge
add name=Loopback protocol-mode=none
add admin-mac=2C:C8:1B:86:B1:CF auto-mac=no comment=defconf name=bridge
/interface wireless
set [ find default-name=wlan1 ] band=2ghz-b/g/n channel-width=20/40mhz-XX \
disabled=no distance=indoors frequency=auto installation=indoor mode=\
ap-bridge ssid=WiFi wireless-protocol=802.11
/interface ethernet
set [ find default-name=ether1 ] name=ether1-gateway
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface wireless security-profiles
set [ find default=yes ] authentication-types=wpa-psk,wpa2-psk mode=\
dynamic-keys supplicant-identity=MikroTik wpa-pre-shared-key=\
PASSWORD wpa2-pre-shared-key=PASSWORD
/ip ipsec profile
add dh-group=ecp521 enc-algorithm=aes-256,aes-128 hash-algorithm=sha512 name=\
S2S-Profile
/ip ipsec peer
add address=192.168.240.25/32 comment=S2SVPN01 exchange-mode=ike2 name=\
S2SVPN01 profile=S2S-Profile
/ip ipsec proposal
add auth-algorithms=sha512 enc-algorithms=aes-256-gcm name=secure-proposal \
pfs-group=ecp521
/ip pool
add comment="LAN DHCP Pool" name=dhcp ranges=10.123.100.100-100.123.100.254
add comment="SSTP-VPN DHCP Pool" name="SSTP-VPN Pool" ranges=\
10.123.201.100-10.123.201.200
add comment="L2TP-VPN DHCP Pool" name="L2TP-VPN Pool" ranges=\
10.123.200.100-10.123.200.200
/ip dhcp-server
add address-pool=dhcp disabled=no interface=bridge name=defconf
/ppp profile
add bridge=bridge comment="SSTP-VPN Profil" dns-server=10.123.201.1 \
local-address=10.123.201.1 name=SSTP-VPN remote-address="SSTP-VPN Pool" \
use-encryption=required use-mpls=yes
add bridge=bridge change-tcp-mss=yes comment="L2TP-VPN Profil" dns-server=\
10.123.200.1 local-address=10.123.200.1 name=L2TP-VPN remote-address=\
"L2TP-VPN Pool" use-mpls=yes
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=ether6
add bridge=bridge comment=defconf interface=ether7
add bridge=bridge comment=defconf interface=ether8
add bridge=bridge comment=defconf interface=sfp1
add bridge=bridge comment=defconf interface=wlan1
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface l2tp-server server
set allow-fast-path=yes authentication=mschap2 ipsec-secret=\
SECRET \
keepalive-timeout=3600 max-mru=1460 max-mtu=1460 use-ipsec=required
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1-gateway list=WAN
/interface sstp-server server
set authentication=mschap2 certificate=SSTP-Server enabled=yes force-aes=yes \
keepalive-timeout=1800 max-mru=1400 max-mtu=1400 pfs=yes tls-version=\
only-1.2
/ip address
add address=10.123.100.1/24 comment=defconf interface=bridge network=\
10.123.100.0
add address=10.123.100.1 interface=Loopback network=10.123.100.1
/ip cloud
set ddns-enabled=yes ddns-update-interval=30m
/ip dhcp-client
add comment=defconf disabled=no interface=ether1-gateway
/ip dhcp-server network
add address=10.123.100.0/24 comment=defconf gateway=10.123.100.1 netmask=24
/ip dns
set allow-remote-requests=yes
/ip dns static
add address=10.123.100.1 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment="SSTP VPN" dst-port=443 log=yes \
protocol=tcp
add action=accept chain=input comment="L2TP IPSec VPN" dst-port=500,1701,4500 \
log=yes protocol=udp
add action=accept chain=input comment="L2TP IPSec VPN" log=yes protocol=\
ipsec-esp
add chain=input comment="S2SVPN01 ipsec-ike-natt" dst-port=4500 in-interface=\
ether1-gateway protocol=udp
add chain=forward comment=S2SVPN01 dst-address=10.123.100.0/24 in-interface=\
ether1-gateway ipsec-policy=in,ipsec src-address=10.123.110.0/24
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=accept chain=srcnat comment=S2SVPN01 dst-address=10.123.110.0/24 \
src-address=10.123.100.0/24
add action=accept chain=dstnat comment=S2SVPN01 dst-address=10.123.100.0/24 \
src-address=10.123.110.0/24
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=accept chain=srcnat out-interface-list=WAN src-address=\
10.123.200.0/24
add action=accept chain=srcnat out-interface-list=WAN src-address=\
10.123.201.0/24
/ip ipsec identity
add comment=S2SVPN01 peer=S2SVPN01 secret=\
SECRET
/ip ipsec policy
add comment=S2SVPN01 dst-address=10.123.110.0/24 peer=S2SVPN01 proposal=\
secure-proposal src-address=10.123.100.0/24 tunnel=yes
/ip service
set winbox address=\
10.123.100.0/24,10.123.110.0/24,10.123.200.0/24,10.123.201.0/24
/lcd
set backlight-timeout=5m color-scheme=light time-interval=hour
/lcd interface pages
set 0 interfaces=\
ether1-gateway,ether2,ether3,ether4,ether5,ether6,ether7,ether8,sfp1
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name=MTGO01
/system ntp client
set enabled=yes server-dns-names=1.de.pool.ntp.org,2.de.pool.ntp.org
/system package update
set channel=long-term
/system scheduler
add comment=" " interval=1d name="Reboot Router every day" on-event=\
" /system reboot" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=aug/15/2021 start-time=05:00:00
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LANKonfig Seite 2:
# nov/21/2021 17:36:27 by RouterOS 6.48.5
# software id = XLU1-U5A7
#
# model = CRS109-8G-1S-2HnD
# serial number = 00000000
/interface bridge
add name=Loopback protocol-mode=none
add admin-mac=2C:C8:1B:86:A1:EF auto-mac=no comment=defconf name=bridge
/interface wireless
set [ find default-name=wlan1 ] band=2ghz-b/g/n channel-width=20/40mhz-XX \
country=germany disabled=no distance=indoors frequency=auto installation=\
indoor mode=ap-bridge ssid=WiFi wireless-protocol=802.11
/interface ethernet
set [ find default-name=ether1 ] name=ether1-gateway
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface wireless security-profiles
set [ find default=yes ] authentication-types=wpa-psk,wpa2-psk mode=\
dynamic-keys supplicant-identity=MikroTik wpa-pre-shared-key=\
PASSWORD wpa2-pre-shared-key=PASSWORD
/ip ipsec profile
add dh-group=ecp521 enc-algorithm=aes-256,aes-128 hash-algorithm=sha512 name=\
S2S-Profile
/ip ipsec peer
add address=192.168.240.26/32 comment=S2SVPN01 exchange-mode=ike2 name=\
S2SVPN01 profile=S2S-Profile
/ip ipsec proposal
add auth-algorithms=sha512 enc-algorithms=aes-256-gcm name=secure-proposal \
pfs-group=ecp521
/ip pool
add name=dhcp ranges=10.123.110.10-10.123.110.254
/ip dhcp-server
add address-pool=dhcp disabled=no interface=bridge name=defconf
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=ether6
add bridge=bridge comment=defconf interface=ether7
add bridge=bridge comment=defconf interface=ether8
add bridge=bridge comment=defconf interface=sfp1
add bridge=bridge comment=defconf interface=wlan1
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1-gateway list=WAN
/ip address
add address=10.123.110.1/24 comment=defconf interface=bridge network=\
10.123.110.0
add address=10.123.110.1 interface=Loopback network=10.123.110.1
/ip cloud
set ddns-enabled=yes ddns-update-interval=30m
/ip dhcp-client
add comment=defconf disabled=no interface=ether1-gateway
/ip dhcp-server network
add address=10.123.110.0/24 comment=defconf gateway=10.123.110.1 netmask=24
/ip dns
set allow-remote-requests=yes
/ip dns static
add address=10.123.110.1 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add chain=input comment="S2SVPN01 ipsec-ike-natt" dst-port=4500 in-interface=\
ether1-gateway protocol=udp
add chain=forward comment=S2SVPN01 dst-address=10.123.110.0/24 in-interface=\
ether1-gateway ipsec-policy=in,ipsec src-address=10.123.100.0/24
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=accept chain=srcnat comment=S2SVPN01 dst-address=10.123.100.0/24 \
src-address=10.123.110.0/24
add action=accept chain=dstnat comment=S2SVPN01 dst-address=10.123.110.0/24 \
src-address=10.123.100.0/24
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
/ip ipsec identity
add comment=S2SVPN01 peer=S2SVPN01 secret=\
SECRET
/ip ipsec policy
add comment=S2SVPN01 dst-address=10.123.100.0/24 peer=S2SVPN01 proposal=\
secure-proposal src-address=10.123.110.0/24 tunnel=yes
/ip service
set winbox address=\
10.123.100.0/24,10.123.110.0/24,10.123.200.0/24,10.123.201.0/24
/lcd
set backlight-timeout=5m color-scheme=light time-interval=hour
/lcd interface pages
set 0 interfaces=\
ether1-gateway,ether2,ether3,ether4,ether5,ether6,ether7,ether8,sfp1
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name=MTBB01
/system ntp client
set enabled=yes server-dns-names=1.de.pool.ntp.org,2.de.pool.ntp.org
/system package update
set channel=long-term
/system scheduler
add comment=" " interval=1d name="Reboot Router every day" on-event=\
" /system reboot" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=aug/15/2021 start-time=05:00:00
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LANHoffe einer der MikroTik Experten hat einen Tip, was ich falsch mache.
mit freundlichen Grüßen
Nemesis
Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 1536809446
Url: https://administrator.de/forum/mikrotik-s2s-ipsec-tunnel-kein-ping-der-gegenstelle-moeglich-1536809446.html
Ausgedruckt am: 24.07.2025 um 07:07 Uhr
4 Kommentare
Neuester Kommentar
Hättest die Konfigs gar nicht alle posten müssen denn die Lösung ist kinderleicht...
Dort muss als Source IP natürlich immer die eigene LAN IP zwingend eingetragen werden, ansonsten würde der MT die WAN IP als Source nehmen und dein Ping landet dann im Nirwana !!
Der MT hat ja mehrere IPs zur Auswahl und du musst ihm schon genau sagen WELCHE er bei einem Ping verwenden soll.
Bei einem IPsec VPN geht nur das durch den Tunnel das gegenseitig in den Phase 2 SAs definiert wurde !!
Ich schaffe es nicht, dass ich von der einen MikroTik die andere via IPSec Tunnel pingen kann.
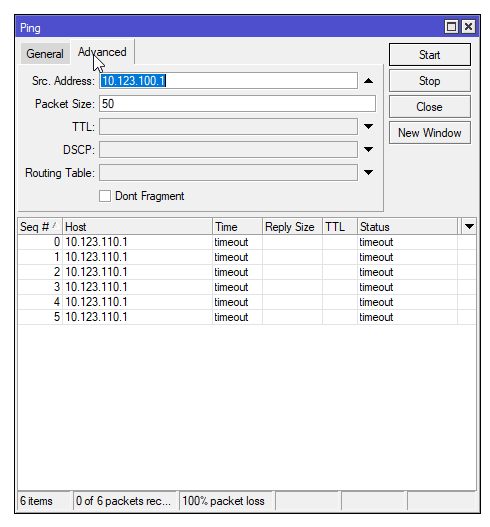
Das liegt ganz sicher daran das du wie viele andere sehr wahrscheinlich den klassischen Anfänger Fehler gemacht hast und vergessen hast unter Advanced eine Source IP Adresse beim Ping Tool auf dem MT einzutragen !!Dort muss als Source IP natürlich immer die eigene LAN IP zwingend eingetragen werden, ansonsten würde der MT die WAN IP als Source nehmen und dein Ping landet dann im Nirwana !!
Der MT hat ja mehrere IPs zur Auswahl und du musst ihm schon genau sagen WELCHE er bei einem Ping verwenden soll.
Bei einem IPsec VPN geht nur das durch den Tunnel das gegenseitig in den Phase 2 SAs definiert wurde !!
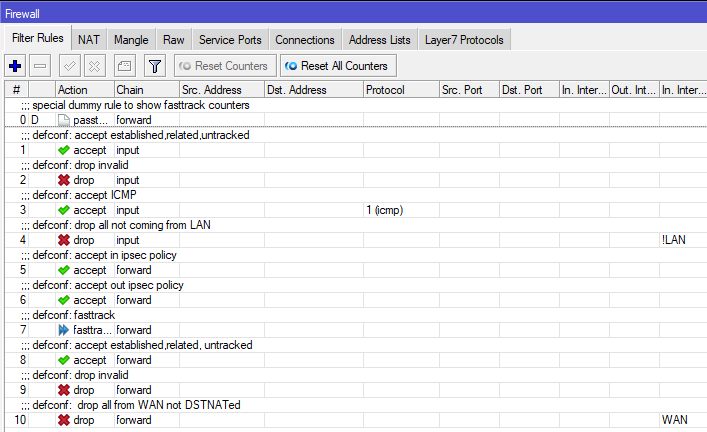
Dann läuft da irgendwas schief in deiner Firewall das die eintweder diese IP netze filtert oder ICMP (Ping) filtert !
Benutzt du die klassisches Default Konfig ?? (eth1 Router Ports mit Standard Firewall Setup) Oder betreibst du die MTs als nackte Router ohne Default Konfig ?
Mit der klassischen Default Konfig kommt so ein Setup mit IKEv2 sofort zum Fliegen...
Benutzt du die klassisches Default Konfig ?? (eth1 Router Ports mit Standard Firewall Setup) Oder betreibst du die MTs als nackte Router ohne Default Konfig ?
Mit der klassischen Default Konfig kommt so ein Setup mit IKEv2 sofort zum Fliegen...