PFSense 2.3.1-RELEASE-p5 und IPSec Problem
Hallo zusammen,
leider bin ich etwas am verzweifeln. Ich bin dabei alle meine alten Monowalls durch Pfsense zu ersetzen. Nun habe ich jedoch Probleme beim IPSec. Ich habe mal die Einstellungen vom IPSec angehängt.
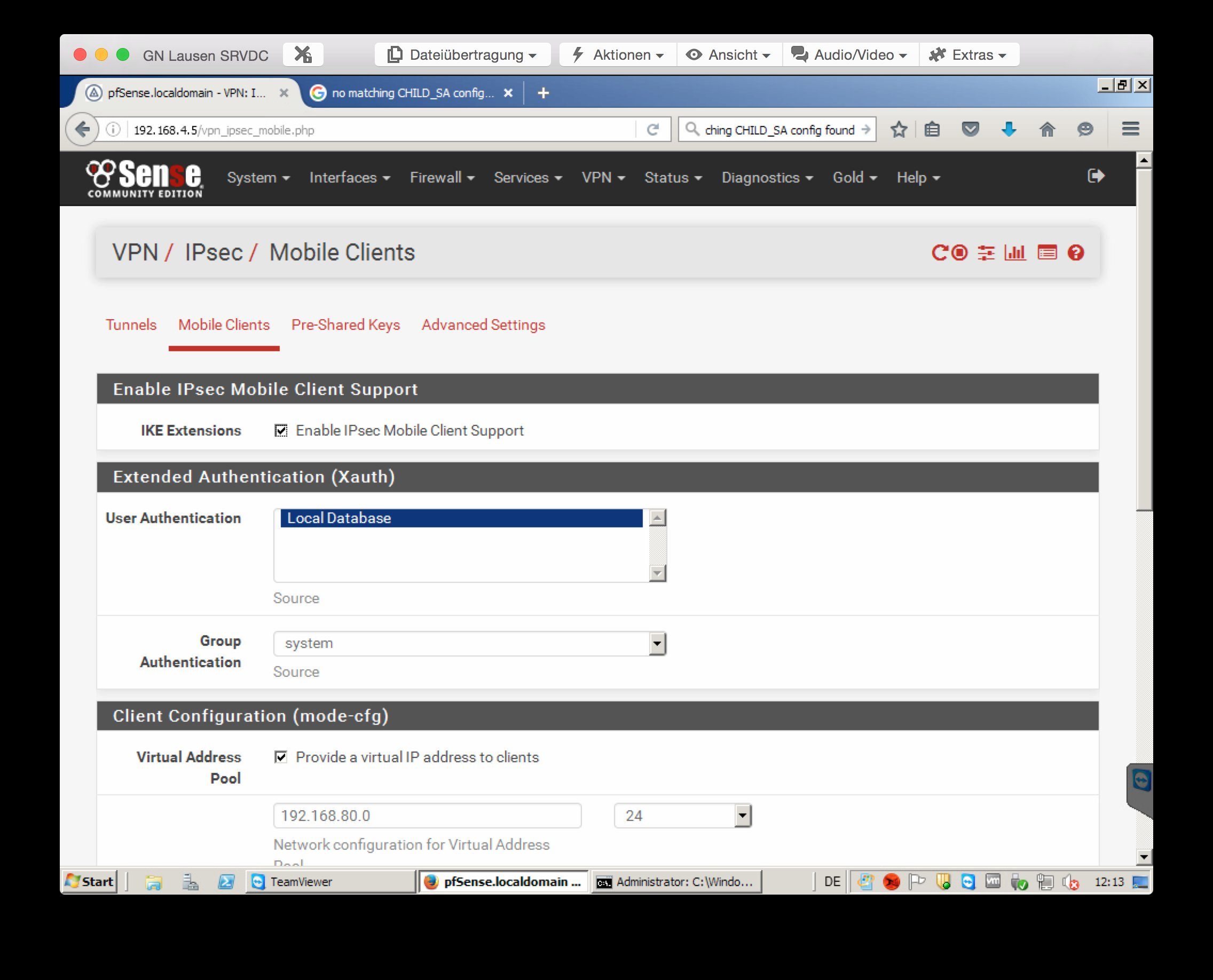
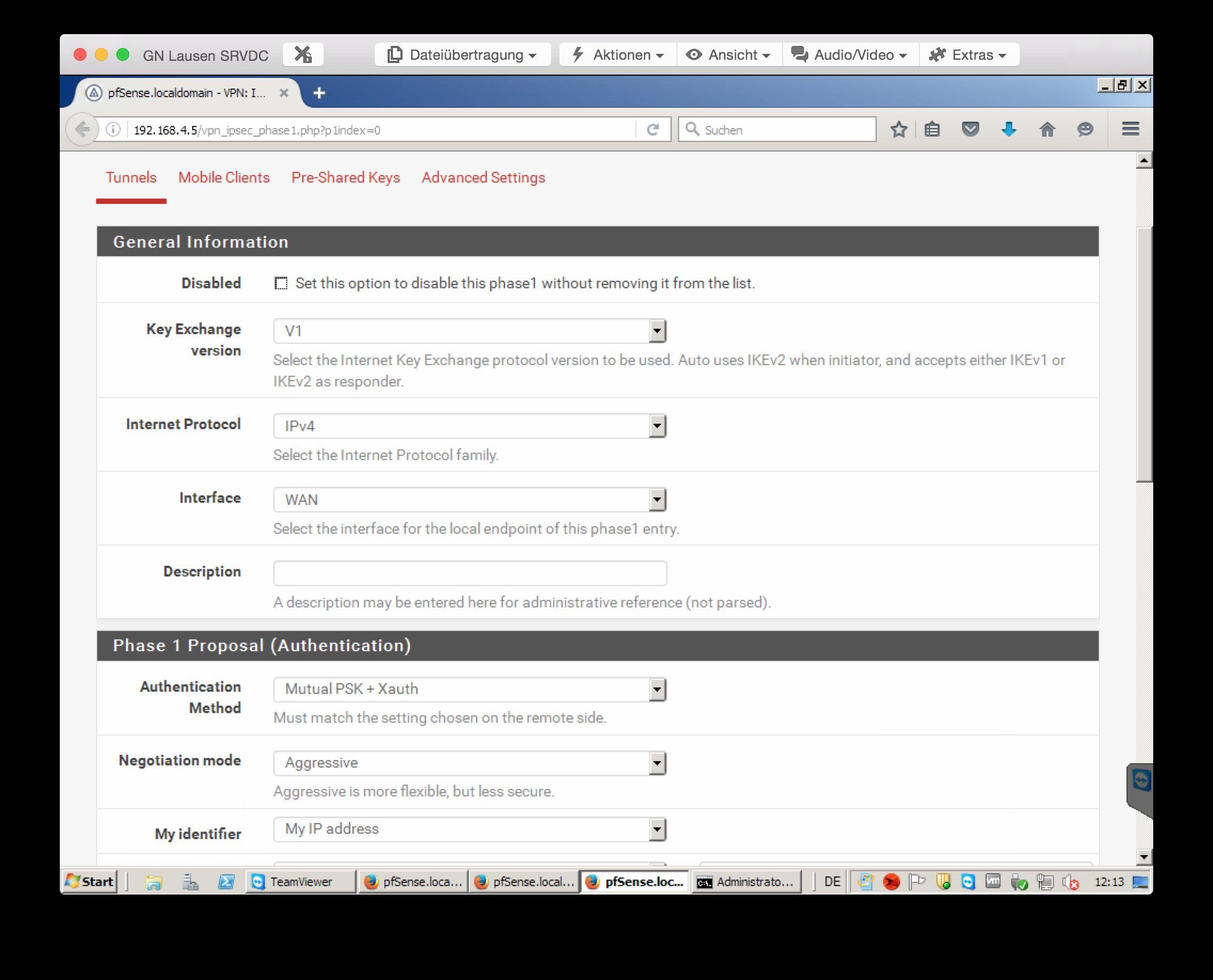
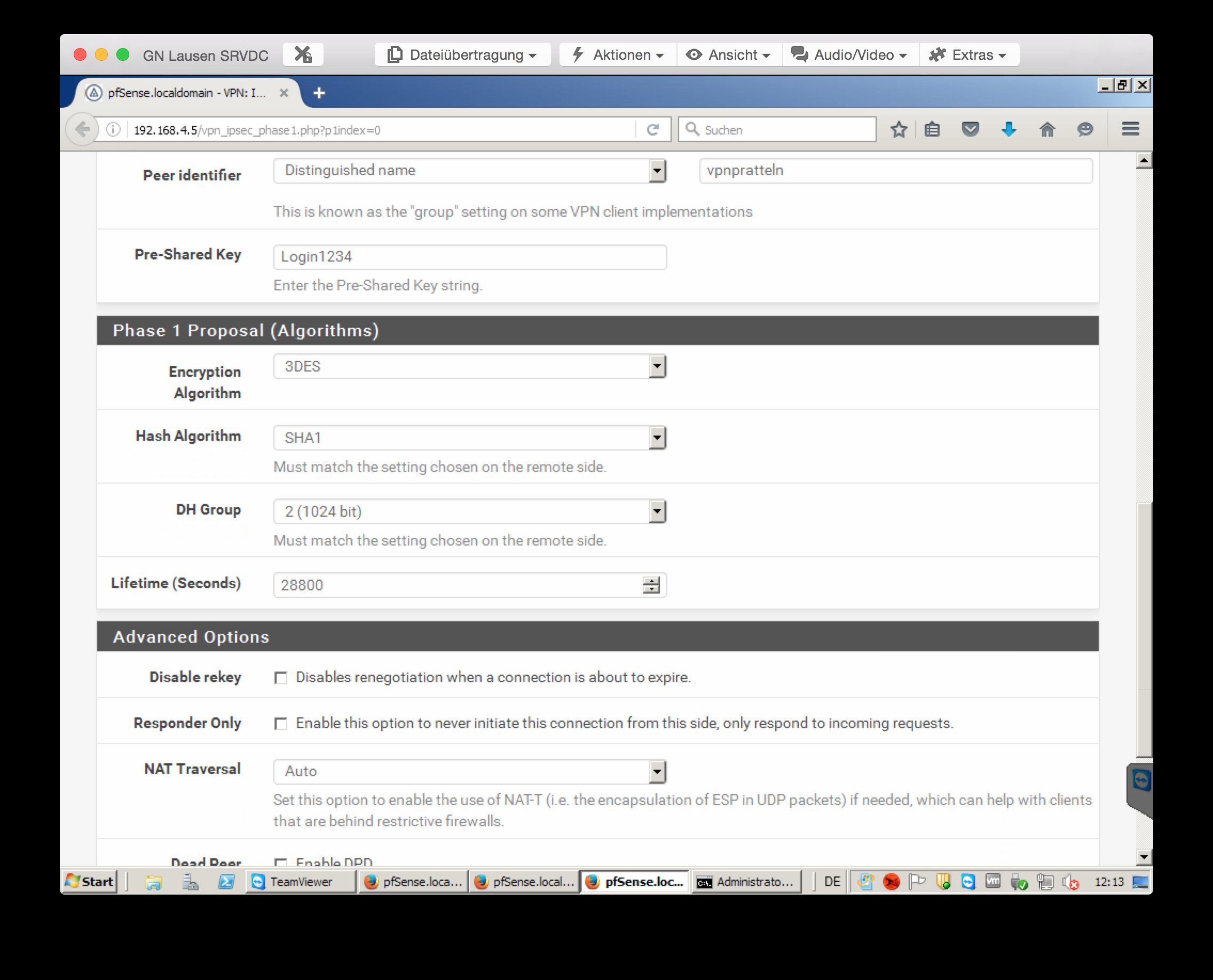
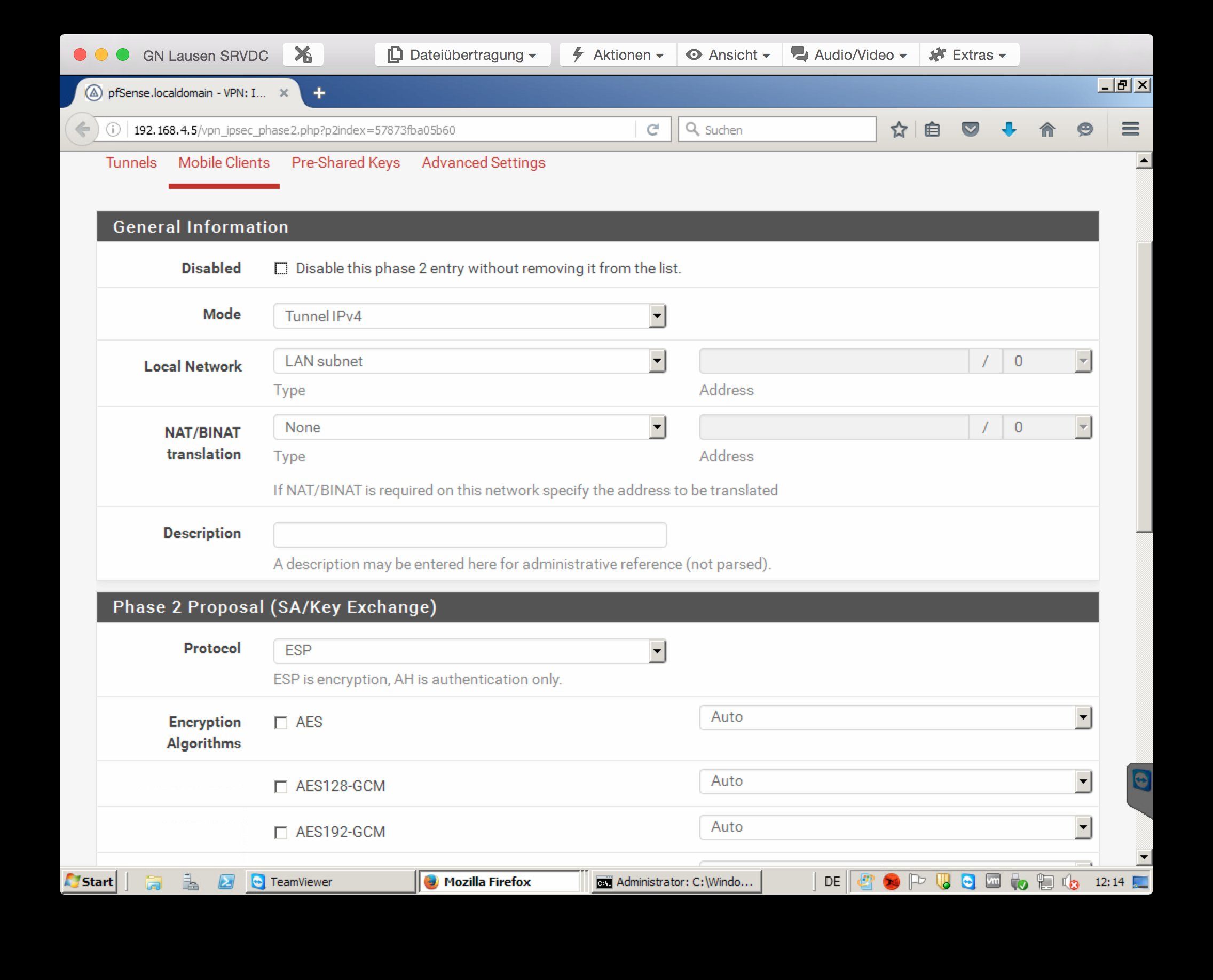
Bevor nun gleich der erste sagt, dass Passwort geht aber gar nicht. Das ganze ist gerade für mich eine Test PFsense um alles richtig einstellen zu können bevor ich wechsel. Aber zurück zum Thema. Ich habe nun unter System -> User Manager noch einen User angelegt und den in eine Gruppe VPN gesteckt welcher die IPsec Rechte hat. Ebenfalls habe ich die 2 Firewall Rules auf dem WAN Port erstellt. Wenn ich nun die Verbindung aufbauen will (Greenbow Client) passiert folgendes:
Log Greenbow Client:
20160725 11:13:28:353 Default (SA MaxMustermann-Test-P2) is opening.
20160725 11:13:28:353 Default (SA MaxMustermann-P1) SEND phase 1 Aggressive Mode [SA] [KEY_EXCH] [NONCE] [ID] [VID] [VID] [VID] [VID] [VID] [VID]
20160725 11:13:28:385 Default (SA MaxMustermann-P1) RECV phase 1 Aggressive Mode [HASH] [SA] [KEY_EXCH] [NONCE] [ID] [NAT_D] [NAT_D] [VID] [VID] [VID]
20160725 11:13:28:385 Default (SA MaxMustermann-P1) SEND phase 1 Aggressive Mode [HASH] [NAT_D] [NAT_D]
20160725 11:13:28:385 Default phase 1 done: initiator id 10.211.55.3, responder id 172.31.255.6
20160725 11:13:28:416 Default (SA MaxMustermann-P1) RECV Transaction Mode [HASH] [ATTRIBUTE]
20160725 11:13:28:416 Default (SA MaxMustermann-P1) SEND Transaction Mode [HASH] [ATTRIBUTE]
20160725 11:13:29:305 Default (SA MaxMustermann-P1) RECV Transaction Mode [HASH] [ATTRIBUTE]
20160725 11:13:29:305 Default (SA MaxMustermann-P1) SEND Transaction Mode [HASH] [ATTRIBUTE]
20160725 11:13:29:305 Default (SA MaxMustermann-Test-P2) SEND phase 2 Quick Mode [HASH] [SA] [NONCE] [ID] [ID]
20160725 11:13:29:336 Default (SA MaxMustermann-P1) RECV Informational [HASH] [NOTIFY] with INVALID_ID_INFORMATION error
20160725 11:13:30:350 Default (SA MaxMustermann-P1) SEND Informational [HASH] [DELETE]
20160725 11:13:30:350 Default <MaxMustermann-P1> deleted
Log Pfsense:
Jul 25 12:13:28 charon 09[NET] <11> received packet: from 213.200.xxx.xxx[56288] to 172.31.255.6[500] (372 bytes)
Jul 25 12:13:28 charon 09[ENC] <11> parsed AGGRESSIVE request 0 [ SA V V V V V V KE No ID ]
Jul 25 12:13:28 charon 09[IKE] <11> received draft-ietf-ipsec-nat-t-ike-00 vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received draft-ietf-ipsec-nat-t-ike-03 vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received NAT-T (RFC 3947) vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received DPD vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received XAuth vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> 213.200.xxx.xxx is initiating a Aggressive Mode IKE_SA
Jul 25 12:13:28 charon 09[CFG] <11> looking for XAuthInitPSK peer configs matching 172.31.255.6...213.200.xxx.xxx[10.211.55.3]
Jul 25 12:13:28 charon 09[CFG] <11> selected peer config "con1"
Jul 25 12:13:28 charon 09[ENC] <con1|11> generating AGGRESSIVE response 0 [ SA KE No ID V V V NAT-D NAT-D HASH ]
Jul 25 12:13:28 charon 09[NET] <con1|11> sending packet: from 172.31.255.6[500] to 213.200.xxx.xxx[56288] (384 bytes)
Jul 25 12:13:28 charon 09[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (100 bytes)
Jul 25 12:13:28 charon 09[ENC] <con1|11> parsed AGGRESSIVE request 0 [ HASH NAT-D NAT-D ]
Jul 25 12:13:28 charon 09[IKE] <con1|11> local host is behind NAT, sending keep alives
Jul 25 12:13:28 charon 09[IKE] <con1|11> remote host is behind NAT
Jul 25 12:13:28 charon 09[ENC] <con1|11> generating TRANSACTION request 4025523683 [ HASH CPRQ(X_USER X_PWD) ]
Jul 25 12:13:28 charon 09[NET] <con1|11> sending packet: from 172.31.255.6[4500] to 213.200.xxx.xxx[7896] (76 bytes)
Jul 25 12:13:28 charon 09[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (84 bytes)
Jul 25 12:13:28 charon 09[ENC] <con1|11> parsed TRANSACTION response 4025523683 [ HASH CPRP(X_USER X_PWD) ]
Jul 25 12:13:29 charon user 'MaxMustermann' authenticated
Jul 25 12:13:29 charon 09[IKE] <con1|11> XAuth-SCRIPT succeeded for user 'MaxMustermann'.
Jul 25 12:13:29 charon 09[IKE] <con1|11> XAuth authentication of 'MaxMustermann' successful
Jul 25 12:13:29 charon 09[ENC] <con1|11> generating TRANSACTION request 3017421628 [ HASH CPS(X_STATUS) ]
Jul 25 12:13:29 charon 09[NET] <con1|11> sending packet: from 172.31.255.6[4500] to 213.200.xxx.xxx[7896] (68 bytes)
Jul 25 12:13:29 charon 09[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (60 bytes)
Jul 25 12:13:29 charon 09[ENC] <con1|11> parsed TRANSACTION response 3017421628 [ HASH CP ]
Jul 25 12:13:29 charon 09[IKE] <con1|11> IKE_SA con1[11] established between 172.31.255.6[172.31.255.6]...213.200.xxx.xxx[10.211.55.3]
Jul 25 12:13:29 charon 09[IKE] <con1|11> scheduling reauthentication in 27966s
Jul 25 12:13:29 charon 09[IKE] <con1|11> maximum IKE_SA lifetime 28506s
Jul 25 12:13:29 charon 01[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (164 bytes)
Jul 25 12:13:29 charon 01[ENC] <con1|11> parsed QUICK_MODE request 1098492832 [ HASH SA No ID ID ]
Jul 25 12:13:29 charon 01[IKE] <con1|11> no matching CHILD_SA config found
Jul 25 12:13:29 charon 01[ENC] <con1|11> generating INFORMATIONAL_V1 request 2148196911 [ HASH N(INVAL_ID) ]
Jul 25 12:13:29 charon 01[NET] <con1|11> sending packet: from 172.31.255.6[4500] to 213.200.xxx.xxx[7896] (76 bytes)
Jul 25 12:13:30 charon 01[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (84 bytes)
Jul 25 12:13:30 charon 01[ENC] <con1|11> parsed INFORMATIONAL_V1 request 3884231992 [ HASH D ]
Jul 25 12:13:30 charon 01[IKE] <con1|11> received DELETE for IKE_SA con1[11]
Jul 25 12:13:30 charon 01[IKE] <con1|11> deleting IKE_SA con1[11] between 172.31.255.6[172.31.255.6]...213.200.xxx.xxx[10.211.55.3]
Eventuell hat ja jemand einen Tipp für mich.
Danke.
leider bin ich etwas am verzweifeln. Ich bin dabei alle meine alten Monowalls durch Pfsense zu ersetzen. Nun habe ich jedoch Probleme beim IPSec. Ich habe mal die Einstellungen vom IPSec angehängt.





Bevor nun gleich der erste sagt, dass Passwort geht aber gar nicht. Das ganze ist gerade für mich eine Test PFsense um alles richtig einstellen zu können bevor ich wechsel. Aber zurück zum Thema. Ich habe nun unter System -> User Manager noch einen User angelegt und den in eine Gruppe VPN gesteckt welcher die IPsec Rechte hat. Ebenfalls habe ich die 2 Firewall Rules auf dem WAN Port erstellt. Wenn ich nun die Verbindung aufbauen will (Greenbow Client) passiert folgendes:
Log Greenbow Client:
20160725 11:13:28:353 Default (SA MaxMustermann-Test-P2) is opening.
20160725 11:13:28:353 Default (SA MaxMustermann-P1) SEND phase 1 Aggressive Mode [SA] [KEY_EXCH] [NONCE] [ID] [VID] [VID] [VID] [VID] [VID] [VID]
20160725 11:13:28:385 Default (SA MaxMustermann-P1) RECV phase 1 Aggressive Mode [HASH] [SA] [KEY_EXCH] [NONCE] [ID] [NAT_D] [NAT_D] [VID] [VID] [VID]
20160725 11:13:28:385 Default (SA MaxMustermann-P1) SEND phase 1 Aggressive Mode [HASH] [NAT_D] [NAT_D]
20160725 11:13:28:385 Default phase 1 done: initiator id 10.211.55.3, responder id 172.31.255.6
20160725 11:13:28:416 Default (SA MaxMustermann-P1) RECV Transaction Mode [HASH] [ATTRIBUTE]
20160725 11:13:28:416 Default (SA MaxMustermann-P1) SEND Transaction Mode [HASH] [ATTRIBUTE]
20160725 11:13:29:305 Default (SA MaxMustermann-P1) RECV Transaction Mode [HASH] [ATTRIBUTE]
20160725 11:13:29:305 Default (SA MaxMustermann-P1) SEND Transaction Mode [HASH] [ATTRIBUTE]
20160725 11:13:29:305 Default (SA MaxMustermann-Test-P2) SEND phase 2 Quick Mode [HASH] [SA] [NONCE] [ID] [ID]
20160725 11:13:29:336 Default (SA MaxMustermann-P1) RECV Informational [HASH] [NOTIFY] with INVALID_ID_INFORMATION error
20160725 11:13:30:350 Default (SA MaxMustermann-P1) SEND Informational [HASH] [DELETE]
20160725 11:13:30:350 Default <MaxMustermann-P1> deleted
Log Pfsense:
Jul 25 12:13:28 charon 09[NET] <11> received packet: from 213.200.xxx.xxx[56288] to 172.31.255.6[500] (372 bytes)
Jul 25 12:13:28 charon 09[ENC] <11> parsed AGGRESSIVE request 0 [ SA V V V V V V KE No ID ]
Jul 25 12:13:28 charon 09[IKE] <11> received draft-ietf-ipsec-nat-t-ike-00 vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received draft-ietf-ipsec-nat-t-ike-03 vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received NAT-T (RFC 3947) vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received DPD vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> received XAuth vendor ID
Jul 25 12:13:28 charon 09[IKE] <11> 213.200.xxx.xxx is initiating a Aggressive Mode IKE_SA
Jul 25 12:13:28 charon 09[CFG] <11> looking for XAuthInitPSK peer configs matching 172.31.255.6...213.200.xxx.xxx[10.211.55.3]
Jul 25 12:13:28 charon 09[CFG] <11> selected peer config "con1"
Jul 25 12:13:28 charon 09[ENC] <con1|11> generating AGGRESSIVE response 0 [ SA KE No ID V V V NAT-D NAT-D HASH ]
Jul 25 12:13:28 charon 09[NET] <con1|11> sending packet: from 172.31.255.6[500] to 213.200.xxx.xxx[56288] (384 bytes)
Jul 25 12:13:28 charon 09[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (100 bytes)
Jul 25 12:13:28 charon 09[ENC] <con1|11> parsed AGGRESSIVE request 0 [ HASH NAT-D NAT-D ]
Jul 25 12:13:28 charon 09[IKE] <con1|11> local host is behind NAT, sending keep alives
Jul 25 12:13:28 charon 09[IKE] <con1|11> remote host is behind NAT
Jul 25 12:13:28 charon 09[ENC] <con1|11> generating TRANSACTION request 4025523683 [ HASH CPRQ(X_USER X_PWD) ]
Jul 25 12:13:28 charon 09[NET] <con1|11> sending packet: from 172.31.255.6[4500] to 213.200.xxx.xxx[7896] (76 bytes)
Jul 25 12:13:28 charon 09[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (84 bytes)
Jul 25 12:13:28 charon 09[ENC] <con1|11> parsed TRANSACTION response 4025523683 [ HASH CPRP(X_USER X_PWD) ]
Jul 25 12:13:29 charon user 'MaxMustermann' authenticated
Jul 25 12:13:29 charon 09[IKE] <con1|11> XAuth-SCRIPT succeeded for user 'MaxMustermann'.
Jul 25 12:13:29 charon 09[IKE] <con1|11> XAuth authentication of 'MaxMustermann' successful
Jul 25 12:13:29 charon 09[ENC] <con1|11> generating TRANSACTION request 3017421628 [ HASH CPS(X_STATUS) ]
Jul 25 12:13:29 charon 09[NET] <con1|11> sending packet: from 172.31.255.6[4500] to 213.200.xxx.xxx[7896] (68 bytes)
Jul 25 12:13:29 charon 09[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (60 bytes)
Jul 25 12:13:29 charon 09[ENC] <con1|11> parsed TRANSACTION response 3017421628 [ HASH CP ]
Jul 25 12:13:29 charon 09[IKE] <con1|11> IKE_SA con1[11] established between 172.31.255.6[172.31.255.6]...213.200.xxx.xxx[10.211.55.3]
Jul 25 12:13:29 charon 09[IKE] <con1|11> scheduling reauthentication in 27966s
Jul 25 12:13:29 charon 09[IKE] <con1|11> maximum IKE_SA lifetime 28506s
Jul 25 12:13:29 charon 01[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (164 bytes)
Jul 25 12:13:29 charon 01[ENC] <con1|11> parsed QUICK_MODE request 1098492832 [ HASH SA No ID ID ]
Jul 25 12:13:29 charon 01[IKE] <con1|11> no matching CHILD_SA config found
Jul 25 12:13:29 charon 01[ENC] <con1|11> generating INFORMATIONAL_V1 request 2148196911 [ HASH N(INVAL_ID) ]
Jul 25 12:13:29 charon 01[NET] <con1|11> sending packet: from 172.31.255.6[4500] to 213.200.xxx.xxx[7896] (76 bytes)
Jul 25 12:13:30 charon 01[NET] <con1|11> received packet: from 213.200.xxx.xxx[7896] to 172.31.255.6[4500] (84 bytes)
Jul 25 12:13:30 charon 01[ENC] <con1|11> parsed INFORMATIONAL_V1 request 3884231992 [ HASH D ]
Jul 25 12:13:30 charon 01[IKE] <con1|11> received DELETE for IKE_SA con1[11]
Jul 25 12:13:30 charon 01[IKE] <con1|11> deleting IKE_SA con1[11] between 172.31.255.6[172.31.255.6]...213.200.xxx.xxx[10.211.55.3]
Eventuell hat ja jemand einen Tipp für mich.
Danke.
Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 310831
Url: https://administrator.de/forum/pfsense-2-3-1-release-p5-und-ipsec-problem-310831.html
Ausgedruckt am: 19.07.2025 um 07:07 Uhr
1 Kommentar
Die beiden hiesigen Tutorials zu dem Thema hast du genau gelesen ??
IPsec VPNs einrichten mit Cisco, Mikrotik, pfSense Firewall, FritzBox, Smartphone sowie Shrew Client Software (Kapitel: IPsec VPN Einwahl pfSense / M0n0wall Firewall-Router )
und insbesondere:
IPsec VPN Praxis mit Standort Vernetzung Cisco, Mikrotik, pfSense, FritzBox u.a
Das sollte eigentlich alle deine Fragen beantworten ?!

Es müssten eigentlich drei Regeln sein:
IPsec VPNs einrichten mit Cisco, Mikrotik, pfSense Firewall, FritzBox, Smartphone sowie Shrew Client Software (Kapitel: IPsec VPN Einwahl pfSense / M0n0wall Firewall-Router )
und insbesondere:
IPsec VPN Praxis mit Standort Vernetzung Cisco, Mikrotik, pfSense, FritzBox u.a
Das sollte eigentlich alle deine Fragen beantworten ?!
Jul 25 12:13:29 charon 01[IKE] <con1|11> no matching CHILD_SA config found
Zeigt das irgendwo die Definition eines deiner lokalen IP Netze in den SA Konfigs fehlt !Ebenfalls habe ich die 2 Firewall Rules auf dem WAN Port erstellt.
WAS für Regeln hast du hier erstellt ?? Leider fehlen die im Posting Es müssten eigentlich drei Regeln sein:
- PASS, Source: Any, Destination: WAN IP Address, Port UDP 500
- PASS, Source: Any, Destination: WAN IP Address, Port UDP 4500
- PASS, Source: Any, Destination: WAN IP Address, Protocoll ESP