RHEL9 Setup auf Virtualbox KernelPanic
Hallo Zusammen,
ich habe einen Windows 10 Laptop auf dem VirtualBox 6.1 installiert ist. Wollte mir nun eine RHEL9 VM installieren und habe das iso eingebunden: rhel-baseos-9.0-x86_64-boot.iso
Virtualbox Einstellungen
Hoffe jemand kann helfen, das ist der Fehler im Screenshot und hier die Virtualbox Logs:
vbox.log:
VBoxHardening.log:
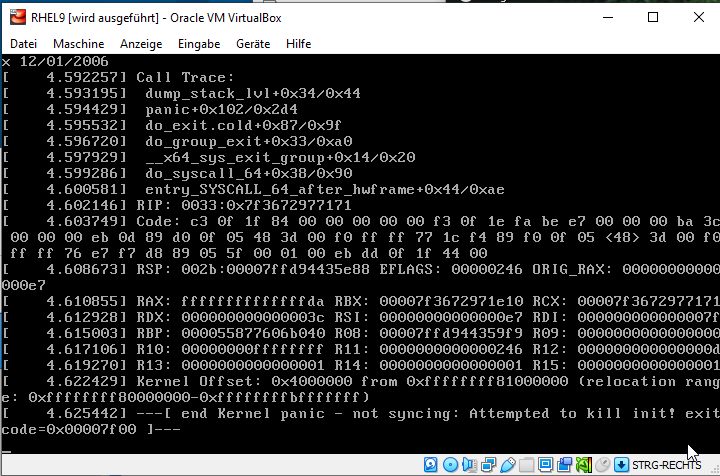
ich habe einen Windows 10 Laptop auf dem VirtualBox 6.1 installiert ist. Wollte mir nun eine RHEL9 VM installieren und habe das iso eingebunden: rhel-baseos-9.0-x86_64-boot.iso
Virtualbox Einstellungen
RAM: 4GB
Chipsatz: PIIX3
IO-APIC aktiviert
EFI deaktiviert
HArdware-Uhr in UTC aktiviert
Prozessoren:1 CPU (keine Änderung mit 2 oder mehr CPUs)
CPU Begrenzung 100% (auch hier keine Änderung bei Umstellung)
PAE/NX aktiviert.Hoffe jemand kann helfen, das ist der Fehler im Screenshot und hier die Virtualbox Logs:
vbox.log:
00:00:07.661172 VirtualBox VM 6.1.26 r145957 win.amd64 (Jul 28 2021 17:15:09) release log
00:00:07.661175 Log opened 2022-07-27T10:33:38.777818300Z
00:00:07.661176 Build Type: release
00:00:07.661178 OS Product: Windows 10
00:00:07.661179 OS Release: 10.0.19044
00:00:07.661179 OS Service Pack:
00:00:07.753670 DMI Product Name: HP ZBook Fury 15 G7 Mobile Workstation
00:00:07.756339 DMI Product Version:
00:00:07.756346 Firmware type: UEFI
00:00:07.756831 Secure Boot: VERR_PRIVILEGE_NOT_HELD
00:00:07.756840 Host RAM: 32348MB (31.5GB) total, 22103MB (21.5GB) available
00:00:07.756842 Executable: C:\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
00:00:07.756842 Process ID: 10840
00:00:07.756843 Package type: WINDOWS_64BITS_GENERIC
00:00:07.757725 Installed Extension Packs:
00:00:07.757750 Oracle VM VirtualBox Extension Pack (Version: 6.1.26 r145957; VRDE Module: VBoxVRDP)
00:00:07.758254 Console: Machine state changed to 'Starting'
00:00:07.758556 Qt version: 5.6.2
00:00:07.768056 GUI: UIMediumEnumerator: Medium-enumeration finished!
00:00:07.852610 SUP: seg #0: R 0x00000000 LB 0x00001000
00:00:07.852658 SUP: seg #1: R X 0x00001000 LB 0x0010a000
00:00:07.852668 SUP: seg #2: R 0x0010b000 LB 0x0004a000
00:00:07.852674 SUP: seg #3: RW 0x00155000 LB 0x00013000
00:00:07.852680 SUP: seg #4: R 0x00168000 LB 0x0000f000
00:00:07.852687 SUP: seg #5: RW 0x00177000 LB 0x00003000
00:00:07.852693 SUP: seg #6: R 0x0017a000 LB 0x0000b000
00:00:07.852699 SUP: seg #7: RWX 0x00185000 LB 0x00002000
00:00:07.852705 SUP: seg #8: R 0x00187000 LB 0x00007000
00:00:07.853140 SUP: Loaded VMMR0.r0 (C:\Program Files\Oracle\VirtualBox\VMMR0.r0) at 0xXXXXXXXXXXXXXXXX - ModuleInit at XXXXXXXXXXXXXXXX and ModuleTerm at XXXXXXXXXXXXXXXX using the native ring-0 loader
00:00:07.853162 SUP: VMMR0EntryEx located at XXXXXXXXXXXXXXXX and VMMR0EntryFast at XXXXXXXXXXXXXXXX
00:00:07.853169 SUP: windbg> .reload /f C:\Program Files\Oracle\VirtualBox\VMMR0.r0=0xXXXXXXXXXXXXXXXX
00:00:07.853965 Guest OS type: 'RedHat_64'
00:00:07.854459 fHMForced=true - No raw-mode support in this build!
00:00:07.856165 File system of 'C:\Users\cen1wa3\Downloads\rhel-baseos-9.0-x86_64-boot.iso' (DVD) is ntfs
00:00:07.856698 File system of 'C:\Users\cen1wa3\Downloads\rhel-baseos-9.0-x86_64-boot.iso' (DVD) is ntfs
00:00:07.857997 File system of 'C:\Users\cen1wa3\VirtualBox VMs\RHEL9\Snapshots' (snapshots) is unknown
00:00:07.858009 File system of 'C:\Users\cen1wa3\VirtualBox VMs\RHEL9\RHEL9.vmdk' is ntfs
00:00:08.054301 Shared Clipboard: Service loaded
00:00:08.054321 Shared Clipboard: Mode: Off
00:00:08.054557 Shared Clipboard: Service running in normal mode
00:00:08.064480 Drag and drop service loaded
00:00:08.064499 Drag and drop mode: Off
00:00:08.078007 ************************* CFGM dump *************************
00:00:08.078008 [/] (level 0)
00:00:08.078009 CpuExecutionCap <integer> = 0x0000000000000064 (100)
00:00:08.078011 EnablePAE <integer> = 0x0000000000000001 (1)
00:00:08.078011 HMEnabled <integer> = 0x0000000000000001 (1)
00:00:08.078012 MemBalloonSize <integer> = 0x0000000000000000 (0)
00:00:08.078012 Name <string> = "RHEL9" (cb=6)
00:00:08.078013 NumCPUs <integer> = 0x0000000000000001 (1)
00:00:08.078014 PageFusionAllowed <integer> = 0x0000000000000000 (0)
00:00:08.078014 RamHoleSize <integer> = 0x0000000020000000 (536 870 912, 512 MB)
00:00:08.078015 RamSize <integer> = 0x0000000080000000 (2 147 483 648, 2 048 MB)
00:00:08.078016 TimerMillies <integer> = 0x000000000000000a (10)
00:00:08.078016 UUID <bytes> = "dc 11 72 e5 3e 5e af 41 b0 55 2a 44 e0 f8 44 b6" (cb=16)
00:00:08.078020
00:00:08.078020 [/CPUM/] (level 1)
00:00:08.078021 GuestCpuName <string> = "host" (cb=5)
00:00:08.078022 NestedHWVirt <integer> = 0x0000000000000000 (0)
00:00:08.078022 PortableCpuIdLevel <integer> = 0x0000000000000000 (0)
00:00:08.078022 SpecCtrl <integer> = 0x0000000000000000 (0)
00:00:08.078023
00:00:08.078023 [/CPUM/IsaExts/] (level 2)
00:00:08.078024
00:00:08.078024 [/DBGC/] (level 1)
00:00:08.078024 GlobalInitScript <string> = "C:\Users\cen1wa3\.VirtualBox/dbgc-init" (cb=39)
00:00:08.078025 HistoryFile <string> = "C:\Users\cen1wa3\.VirtualBox/dbgc-history" (cb=42)
00:00:08.078026 LocalInitScript <string> = "C:\Users\cen1wa3\VirtualBox VMs\RHEL9/dbgc-init" (cb=48)
00:00:08.078026
00:00:08.078026 [/DBGF/] (level 1)
00:00:08.078027 Path <string> = "C:\Users\cen1wa3\VirtualBox VMs\RHEL9/debug/;C:\Users\cen1wa3\VirtualBox VMs\RHEL9/;cache*C:\Users\cen1wa3\VirtualBox VMs\RHEL9/dbgcache/;C:\Users\cen1wa3\" (cb=156)
00:00:08.078027
00:00:08.078027 [/Devices/] (level 1)
00:00:08.078028
00:00:08.078028 [/Devices/8237A/] (level 2)
00:00:08.078028
00:00:08.078028 [/Devices/8237A/0/] (level 3)
00:00:08.078029 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078029
00:00:08.078029 [/Devices/GIMDev/] (level 2)
00:00:08.078030
00:00:08.078030 [/Devices/GIMDev/0/] (level 3)
00:00:08.078031 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078031
00:00:08.078031 [/Devices/VMMDev/] (level 2)
00:00:08.078031
00:00:08.078032 [/Devices/VMMDev/0/] (level 3)
00:00:08.078032 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078033 PCIDeviceNo <integer> = 0x0000000000000004 (4)
00:00:08.078033 PCIFunctionNo <integer> = 0x0000000000000000 (0)
00:00:08.078034 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078034
00:00:08.078034 [/Devices/VMMDev/0/Config/] (level 4)
00:00:08.078035 GuestCoreDumpDir <string> = "C:\Users\cen1wa3\VirtualBox VMs\RHEL9\Snapshots" (cb=48)
00:00:08.078036
00:00:08.078036 [/Devices/VMMDev/0/LUN#0/] (level 4)
00:00:08.078037 Driver <string> = "HGCM" (cb=5)
00:00:08.078037
00:00:08.078037 [/Devices/VMMDev/0/LUN#0/Config/] (level 5)
00:00:08.078038 Object <integer> = 0x000000000818dea0 (135 847 584)
00:00:08.078039
00:00:08.078039 [/Devices/VMMDev/0/LUN#999/] (level 4)
00:00:08.078039 Driver <string> = "MainStatus" (cb=11)
00:00:08.078040
00:00:08.078040 [/Devices/VMMDev/0/LUN#999/Config/] (level 5)
00:00:08.078041 First <integer> = 0x0000000000000000 (0)
00:00:08.078041 Last <integer> = 0x0000000000000000 (0)
00:00:08.078041 papLeds <integer> = 0x00000000036c35d8 (57 423 320)
00:00:08.078042
00:00:08.078042 [/Devices/acpi/] (level 2)
00:00:08.078043
00:00:08.078043 [/Devices/acpi/0/] (level 3)
00:00:08.078043 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078044 PCIDeviceNo <integer> = 0x0000000000000007 (7)
00:00:08.078044 PCIFunctionNo <integer> = 0x0000000000000000 (0)
00:00:08.078045 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078045
00:00:08.078045 [/Devices/acpi/0/Config/] (level 4)
00:00:08.078046 CpuHotPlug <integer> = 0x0000000000000000 (0)
00:00:08.078047 FdcEnabled <integer> = 0x0000000000000000 (0)
00:00:08.078047 HostBusPciAddress <integer> = 0x0000000000000000 (0)
00:00:08.078047 HpetEnabled <integer> = 0x0000000000000000 (0)
00:00:08.078048 IOAPIC <integer> = 0x0000000000000001 (1)
00:00:08.078048 IocPciAddress <integer> = 0x0000000000010000 (65 536)
00:00:08.078049 NumCPUs <integer> = 0x0000000000000001 (1)
00:00:08.078049 Parallel0IoPortBase <integer> = 0x0000000000000000 (0)
00:00:08.078050 Parallel0Irq <integer> = 0x0000000000000000 (0)
00:00:08.078050 Parallel1IoPortBase <integer> = 0x0000000000000000 (0)
00:00:08.078051 Parallel1Irq <integer> = 0x0000000000000000 (0)
00:00:08.078051 Serial0IoPortBase <integer> = 0x0000000000000000 (0)
00:00:08.078051 Serial0Irq <integer> = 0x0000000000000000 (0)
00:00:08.078052 Serial1IoPortBase <integer> = 0x0000000000000000 (0)
00:00:08.078052 Serial1Irq <integer> = 0x0000000000000000 (0)
00:00:08.078052 ShowCpu <integer> = 0x0000000000000001 (1)
00:00:08.078053 ShowRtc <integer> = 0x0000000000000000 (0)
00:00:08.078053 SmcEnabled <integer> = 0x0000000000000000 (0)
00:00:08.078054
00:00:08.078054 [/Devices/acpi/0/LUN#0/] (level 4)
00:00:08.078054 Driver <string> = "ACPIHost" (cb=9)
00:00:08.078055
00:00:08.078055 [/Devices/acpi/0/LUN#0/Config/] (level 5)
00:00:08.078055
00:00:08.078056 [/Devices/ahci/] (level 2)
00:00:08.078056
00:00:08.078056 [/Devices/ahci/0/] (level 3)
00:00:08.078057 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078057 PCIDeviceNo <integer> = 0x000000000000000d (13)
00:00:08.078058 PCIFunctionNo <integer> = 0x0000000000000000 (0)
00:00:08.078058 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078059
00:00:08.078059 [/Devices/ahci/0/Config/] (level 4)
00:00:08.078059 Bootable <integer> = 0x0000000000000001 (1)
00:00:08.078060 PortCount <integer> = 0x0000000000000001 (1)
00:00:08.078060
00:00:08.078060 [/Devices/ahci/0/Config/Port0/] (level 5)
00:00:08.078061 Hotpluggable <integer> = 0x0000000000000000 (0)
00:00:08.078061
00:00:08.078061 [/Devices/ahci/0/LUN#0/] (level 4)
00:00:08.078062 Driver <string> = "VD" (cb=3)
00:00:08.078062
00:00:08.078062 [/Devices/ahci/0/LUN#0/Config/] (level 5)
00:00:08.078063 BlockCache <integer> = 0x0000000000000001 (1)
00:00:08.078063 Format <string> = "VMDK" (cb=5)
00:00:08.078064 Mountable <integer> = 0x0000000000000000 (0)
00:00:08.078064 Path <string> = "C:\Users\cen1wa3\VirtualBox VMs\RHEL9\RHEL9.vmdk" (cb=49)
00:00:08.078065 Type <string> = "HardDisk" (cb=9)
00:00:08.078065 UseNewIo <integer> = 0x0000000000000001 (1)
00:00:08.078065
00:00:08.078066 [/Devices/ahci/0/LUN#0/Config/Plugins/] (level 6)
00:00:08.078066
00:00:08.078067 [/Devices/ahci/0/LUN#0/Config/Plugins/VDPluginCrypt/] (level 7)
00:00:08.078067 Path <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.DLL" (cb=114)
00:00:08.078068
00:00:08.078068 [/Devices/ahci/0/LUN#999/] (level 4)
00:00:08.078069 Driver <string> = "MainStatus" (cb=11)
00:00:08.078069
00:00:08.078070 [/Devices/ahci/0/LUN#999/Config/] (level 5)
00:00:08.078070 DeviceInstance <string> = "ahci/0" (cb=7)
00:00:08.078071 First <integer> = 0x0000000000000000 (0)
00:00:08.078071 Last <integer> = 0x0000000000000000 (0)
00:00:08.078072 pConsole <integer> = 0x00000000036c21e0 (57 418 208)
00:00:08.078072 papLeds <integer> = 0x00000000036c29e0 (57 420 256)
00:00:08.078073 pmapMediumAttachments <integer> = 0x00000000036c35f8 (57 423 352)
00:00:08.078074
00:00:08.078074 [/Devices/apic/] (level 2)
00:00:08.078074
00:00:08.078075 [/Devices/apic/0/] (level 3)
00:00:08.078075 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078075
00:00:08.078076 [/Devices/apic/0/Config/] (level 4)
00:00:08.078076 IOAPIC <integer> = 0x0000000000000001 (1)
00:00:08.078077 Mode <integer> = 0x0000000000000003 (3)
00:00:08.078077 NumCPUs <integer> = 0x0000000000000001 (1)
00:00:08.078077
00:00:08.078077 [/Devices/e1000/] (level 2)
00:00:08.078078
00:00:08.078078 [/Devices/e1000/0/] (level 3)
00:00:08.078079 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078079 PCIDeviceNo <integer> = 0x0000000000000003 (3)
00:00:08.078079 PCIFunctionNo <integer> = 0x0000000000000000 (0)
00:00:08.078080 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078080
00:00:08.078080 [/Devices/e1000/0/Config/] (level 4)
00:00:08.078081 AdapterType <integer> = 0x0000000000000000 (0)
00:00:08.078081 CableConnected <integer> = 0x0000000000000001 (1)
00:00:08.078082 LineSpeed <integer> = 0x0000000000000000 (0)
00:00:08.078082 MAC <bytes> = "08 00 27 91 82 9a" (cb=6)
00:00:08.078083
00:00:08.078083 [/Devices/e1000/0/LUN#0/] (level 4)
00:00:08.078083 Driver <string> = "IntNet" (cb=7)
00:00:08.078084
00:00:08.078084 [/Devices/e1000/0/LUN#0/Config/] (level 5)
00:00:08.078085 IfPolicyPromisc <string> = "deny" (cb=5)
00:00:08.078085 IgnoreConnectFailure <integer> = 0x0000000000000000 (0)
00:00:08.078085 Network <string> = "HostInterfaceNetworking-Intel(R) Wi-Fi 6 AX201 160MHz" (cb=54)
00:00:08.078086 SharedMacOnWire <integer> = 0x0000000000000001 (1)
00:00:08.078086 Trunk <string> = "\DEVICE\{FB5AF5B5-8FF3-4CC3-9B4E-C01F8129AB07}" (cb=47)
00:00:08.078087 TrunkType <integer> = 0x0000000000000003 (3)
00:00:08.078087
00:00:08.078087 [/Devices/e1000/0/LUN#999/] (level 4)
00:00:08.078088 Driver <string> = "MainStatus" (cb=11)
00:00:08.078088
00:00:08.078088 [/Devices/e1000/0/LUN#999/Config/] (level 5)
00:00:08.078089 First <integer> = 0x0000000000000000 (0)
00:00:08.078090 Last <integer> = 0x0000000000000000 (0)
00:00:08.078090 papLeds <integer> = 0x00000000036c34b8 (57 423 032)
00:00:08.078091
00:00:08.078091 [/Devices/i8254/] (level 2)
00:00:08.078091
00:00:08.078091 [/Devices/i8254/0/] (level 3)
00:00:08.078092
00:00:08.078092 [/Devices/i8254/0/Config/] (level 4)
00:00:08.078092
00:00:08.078092 [/Devices/i8259/] (level 2)
00:00:08.078093
00:00:08.078093 [/Devices/i8259/0/] (level 3)
00:00:08.078093 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078094
00:00:08.078094 [/Devices/i8259/0/Config/] (level 4)
00:00:08.078094
00:00:08.078095 [/Devices/ichac97/] (level 2)
00:00:08.078095
00:00:08.078095 [/Devices/ichac97/0/] (level 3)
00:00:08.078096 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078096 PCIDeviceNo <integer> = 0x0000000000000005 (5)
00:00:08.078096 PCIFunctionNo <integer> = 0x0000000000000000 (0)
00:00:08.078097 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078097
00:00:08.078097 [/Devices/ichac97/0/AudioConfig/] (level 4)
00:00:08.078098
00:00:08.078098 [/Devices/ichac97/0/Config/] (level 4)
00:00:08.078098 Codec <string> = "AD1980" (cb=7)
00:00:08.078099 DebugEnabled <integer> = 0x0000000000000000 (0)
00:00:08.078099
00:00:08.078099 [/Devices/ichac97/0/LUN#0/] (level 4)
00:00:08.078100 Driver <string> = "AUDIO" (cb=6)
00:00:08.078100
00:00:08.078100 [/Devices/ichac97/0/LUN#0/AttachedDriver/] (level 5)
00:00:08.078101 Driver <string> = "HostAudioWas" (cb=13)
00:00:08.078101
00:00:08.078101 [/Devices/ichac97/0/LUN#0/AttachedDriver/Config/] (level 6)
00:00:08.078102 VmName <string> = "RHEL9" (cb=6)
00:00:08.078102 VmUuid <string> = "e57211dc-5e3e-41af-b055-2a44e0f844b6" (cb=37)
00:00:08.078103
00:00:08.078103 [/Devices/ichac97/0/LUN#0/Config/] (level 5)
00:00:08.078104 DriverName <string> = "HostAudioWas" (cb=13)
00:00:08.078104 InputEnabled <integer> = 0x0000000000000000 (0)
00:00:08.078104 OutputEnabled <integer> = 0x0000000000000001 (1)
00:00:08.078105
00:00:08.078105 [/Devices/ichac97/0/LUN#1/] (level 4)
00:00:08.078105 Driver <string> = "AUDIO" (cb=6)
00:00:08.078106
00:00:08.078106 [/Devices/ichac97/0/LUN#2/] (level 4)
00:00:08.078107 Driver <string> = "AUDIO" (cb=6)
00:00:08.078107
00:00:08.078107 [/Devices/ioapic/] (level 2)
00:00:08.078108
00:00:08.078108 [/Devices/ioapic/0/] (level 3)
00:00:08.078108 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078109
00:00:08.078109 [/Devices/ioapic/0/Config/] (level 4)
00:00:08.078109 NumCPUs <integer> = 0x0000000000000001 (1)
00:00:08.078110
00:00:08.078110 [/Devices/mc146818/] (level 2)
00:00:08.078110
00:00:08.078110 [/Devices/mc146818/0/] (level 3)
00:00:08.078111
00:00:08.078111 [/Devices/mc146818/0/Config/] (level 4)
00:00:08.078112 UseUTC <integer> = 0x0000000000000001 (1)
00:00:08.078112
00:00:08.078112 [/Devices/parallel/] (level 2)
00:00:08.078112
00:00:08.078113 [/Devices/pcarch/] (level 2)
00:00:08.078113
00:00:08.078113 [/Devices/pcarch/0/] (level 3)
00:00:08.078114 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078114
00:00:08.078114 [/Devices/pcarch/0/Config/] (level 4)
00:00:08.078115
00:00:08.078115 [/Devices/pcbios/] (level 2)
00:00:08.078115
00:00:08.078115 [/Devices/pcbios/0/] (level 3)
00:00:08.078116 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078116
00:00:08.078116 [/Devices/pcbios/0/Config/] (level 4)
00:00:08.078117 APIC <integer> = 0x0000000000000001 (1)
00:00:08.078118 BootDevice0 <string> = "FLOPPY" (cb=7)
00:00:08.078118 BootDevice1 <string> = "DVD" (cb=4)
00:00:08.078118 BootDevice2 <string> = "IDE" (cb=4)
00:00:08.078119 BootDevice3 <string> = "NONE" (cb=5)
00:00:08.078119 FloppyDevice <string> = "i82078" (cb=7)
00:00:08.078120 HardDiskDevice <string> = "piix3ide" (cb=9)
00:00:08.078120 IOAPIC <integer> = 0x0000000000000001 (1)
00:00:08.078120 LanBootRom <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\PXE-Intel.rom" (cb=100)
00:00:08.078121 McfgBase <integer> = 0x0000000000000000 (0)
00:00:08.078121 McfgLength <integer> = 0x0000000000000000 (0)
00:00:08.078122 NumCPUs <integer> = 0x0000000000000001 (1)
00:00:08.078122 PXEDebug <integer> = 0x0000000000000000 (0)
00:00:08.078123 SataHardDiskDevice <string> = "ahci" (cb=5)
00:00:08.078123 SataLUN1 <integer> = 0x0000000000000000 (0)
00:00:08.078123 UUID <bytes> = "dc 11 72 e5 3e 5e af 41 b0 55 2a 44 e0 f8 44 b6" (cb=16)
00:00:08.078124 UuidLe <integer> = 0x0000000000000001 (1)
00:00:08.078125
00:00:08.078125 [/Devices/pcbios/0/Config/NetBoot/] (level 5)
00:00:08.078126
00:00:08.078126 [/Devices/pcbios/0/Config/NetBoot/0/] (level 6)
00:00:08.078126 NIC <integer> = 0x0000000000000000 (0)
00:00:08.078127 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078127 PCIDeviceNo <integer> = 0x0000000000000003 (3)
00:00:08.078127 PCIFunctionNo <integer> = 0x0000000000000000 (0)
00:00:08.078128
00:00:08.078128 [/Devices/pci/] (level 2)
00:00:08.078128
00:00:08.078129 [/Devices/pci/0/] (level 3)
00:00:08.078129 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078129
00:00:08.078130 [/Devices/pci/0/Config/] (level 4)
00:00:08.078130 IOAPIC <integer> = 0x0000000000000001 (1)
00:00:08.078130
00:00:08.078131 [/Devices/pcibridge/] (level 2)
00:00:08.078131
00:00:08.078131 [/Devices/pckbd/] (level 2)
00:00:08.078132
00:00:08.078132 [/Devices/pckbd/0/] (level 3)
00:00:08.078132 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078132
00:00:08.078133 [/Devices/pckbd/0/Config/] (level 4)
00:00:08.078133
00:00:08.078133 [/Devices/pckbd/0/LUN#0/] (level 4)
00:00:08.078134 Driver <string> = "KeyboardQueue" (cb=14)
00:00:08.078134
00:00:08.078134 [/Devices/pckbd/0/LUN#0/AttachedDriver/] (level 5)
00:00:08.078135 Driver <string> = "MainKeyboard" (cb=13)
00:00:08.078135
00:00:08.078135 [/Devices/pckbd/0/LUN#0/AttachedDriver/Config/] (level 6)
00:00:08.078136 Object <integer> = 0x00000000035b6320 (56 320 800)
00:00:08.078137
00:00:08.078137 [/Devices/pckbd/0/LUN#0/Config/] (level 5)
00:00:08.078137 QueueSize <integer> = 0x0000000000000040 (64)
00:00:08.078138
00:00:08.078138 [/Devices/pckbd/0/LUN#1/] (level 4)
00:00:08.078138 Driver <string> = "MouseQueue" (cb=11)
00:00:08.078139
00:00:08.078139 [/Devices/pckbd/0/LUN#1/AttachedDriver/] (level 5)
00:00:08.078140 Driver <string> = "MainMouse" (cb=10)
00:00:08.078140
00:00:08.078140 [/Devices/pckbd/0/LUN#1/AttachedDriver/Config/] (level 6)
00:00:08.078141 Object <integer> = 0x00000000036c48f0 (57 428 208)
00:00:08.078141
00:00:08.078141 [/Devices/pckbd/0/LUN#1/Config/] (level 5)
00:00:08.078142 QueueSize <integer> = 0x0000000000000080 (128)
00:00:08.078142
00:00:08.078142 [/Devices/pcnet/] (level 2)
00:00:08.078143
00:00:08.078143 [/Devices/piix3ide/] (level 2)
00:00:08.078143
00:00:08.078144 [/Devices/piix3ide/0/] (level 3)
00:00:08.078144 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078145 PCIDeviceNo <integer> = 0x0000000000000001 (1)
00:00:08.078145 PCIFunctionNo <integer> = 0x0000000000000001 (1)
00:00:08.078145 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078146
00:00:08.078146 [/Devices/piix3ide/0/Config/] (level 4)
00:00:08.078146 Type <string> = "PIIX4" (cb=6)
00:00:08.078147
00:00:08.078147 [/Devices/piix3ide/0/LUN#0/] (level 4)
00:00:08.078147 Driver <string> = "VD" (cb=3)
00:00:08.078148
00:00:08.078148 [/Devices/piix3ide/0/LUN#0/Config/] (level 5)
00:00:08.078148 Format <string> = "RAW" (cb=4)
00:00:08.078149 Mountable <integer> = 0x0000000000000001 (1)
00:00:08.078149 Path <string> = "C:\Users\cen1wa3\Downloads\rhel-baseos-9.0-x86_64-boot.iso" (cb=59)
00:00:08.078150 ReadOnly <integer> = 0x0000000000000001 (1)
00:00:08.078150 Type <string> = "DVD" (cb=4)
00:00:08.078150
00:00:08.078150 [/Devices/piix3ide/0/LUN#0/Config/Plugins/] (level 6)
00:00:08.078151
00:00:08.078151 [/Devices/piix3ide/0/LUN#0/Config/Plugins/VDPluginCrypt/] (level 7)
00:00:08.078152 Path <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.DLL" (cb=114)
00:00:08.078152
00:00:08.078153 [/Devices/piix3ide/0/LUN#2/] (level 4)
00:00:08.078153 Driver <string> = "VD" (cb=3)
00:00:08.078153
00:00:08.078153 [/Devices/piix3ide/0/LUN#2/Config/] (level 5)
00:00:08.078154 Format <string> = "RAW" (cb=4)
00:00:08.078154 Mountable <integer> = 0x0000000000000001 (1)
00:00:08.078155 Path <string> = "C:\Users\cen1wa3\Downloads\rhel-baseos-9.0-x86_64-boot.iso" (cb=59)
00:00:08.078155 ReadOnly <integer> = 0x0000000000000001 (1)
00:00:08.078156 Type <string> = "DVD" (cb=4)
00:00:08.078156
00:00:08.078156 [/Devices/piix3ide/0/LUN#2/Config/Plugins/] (level 6)
00:00:08.078157
00:00:08.078157 [/Devices/piix3ide/0/LUN#2/Config/Plugins/VDPluginCrypt/] (level 7)
00:00:08.078157 Path <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.DLL" (cb=114)
00:00:08.078158
00:00:08.078158 [/Devices/piix3ide/0/LUN#999/] (level 4)
00:00:08.078159 Driver <string> = "MainStatus" (cb=11)
00:00:08.078159
00:00:08.078159 [/Devices/piix3ide/0/LUN#999/Config/] (level 5)
00:00:08.078160 DeviceInstance <string> = "piix3ide/0" (cb=11)
00:00:08.078160 First <integer> = 0x0000000000000000 (0)
00:00:08.078161 Last <integer> = 0x0000000000000003 (3)
00:00:08.078161 pConsole <integer> = 0x00000000036c21e0 (57 418 208)
00:00:08.078162 papLeds <integer> = 0x00000000036c29c0 (57 420 224)
00:00:08.078162 pmapMediumAttachments <integer> = 0x00000000036c35f8 (57 423 352)
00:00:08.078163
00:00:08.078163 [/Devices/serial/] (level 2)
00:00:08.078163
00:00:08.078163 [/Devices/usb-ehci/] (level 2)
00:00:08.078164
00:00:08.078164 [/Devices/usb-ehci/0/] (level 3)
00:00:08.078165 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078165 PCIDeviceNo <integer> = 0x000000000000000b (11)
00:00:08.078165 PCIFunctionNo <integer> = 0x0000000000000000 (0)
00:00:08.078166 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078166
00:00:08.078166 [/Devices/usb-ehci/0/Config/] (level 4)
00:00:08.078167
00:00:08.078167 [/Devices/usb-ehci/0/LUN#0/] (level 4)
00:00:08.078167 Driver <string> = "VUSBRootHub" (cb=12)
00:00:08.078168
00:00:08.078168 [/Devices/usb-ehci/0/LUN#0/Config/] (level 5)
00:00:08.078169
00:00:08.078169 [/Devices/usb-ehci/0/LUN#999/] (level 4)
00:00:08.078169 Driver <string> = "MainStatus" (cb=11)
00:00:08.078170
00:00:08.078170 [/Devices/usb-ehci/0/LUN#999/Config/] (level 5)
00:00:08.078170 First <integer> = 0x0000000000000000 (0)
00:00:08.078171 Last <integer> = 0x0000000000000000 (0)
00:00:08.078171 papLeds <integer> = 0x00000000036c35e8 (57 423 336)
00:00:08.078171
00:00:08.078172 [/Devices/usb-ohci/] (level 2)
00:00:08.078172
00:00:08.078172 [/Devices/usb-ohci/0/] (level 3)
00:00:08.078173 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078173 PCIDeviceNo <integer> = 0x0000000000000006 (6)
00:00:08.078173 PCIFunctionNo <integer> = 0x0000000000000000 (0)
00:00:08.078174 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078174
00:00:08.078174 [/Devices/usb-ohci/0/Config/] (level 4)
00:00:08.078175
00:00:08.078175 [/Devices/usb-ohci/0/LUN#0/] (level 4)
00:00:08.078176 Driver <string> = "VUSBRootHub" (cb=12)
00:00:08.078176
00:00:08.078176 [/Devices/usb-ohci/0/LUN#0/Config/] (level 5)
00:00:08.078177
00:00:08.078177 [/Devices/usb-ohci/0/LUN#999/] (level 4)
00:00:08.078177 Driver <string> = "MainStatus" (cb=11)
00:00:08.078178
00:00:08.078178 [/Devices/usb-ohci/0/LUN#999/Config/] (level 5)
00:00:08.078178 First <integer> = 0x0000000000000000 (0)
00:00:08.078179 Last <integer> = 0x0000000000000000 (0)
00:00:08.078179 papLeds <integer> = 0x00000000036c35e0 (57 423 328)
00:00:08.078179
00:00:08.078180 [/Devices/vga/] (level 2)
00:00:08.078180
00:00:08.078180 [/Devices/vga/0/] (level 3)
00:00:08.078181 PCIBusNo <integer> = 0x0000000000000000 (0)
00:00:08.078181 PCIDeviceNo <integer> = 0x0000000000000002 (2)
00:00:08.078181 PCIFunctionNo <integer> = 0x0000000000000000 (0)
00:00:08.078182 Trusted <integer> = 0x0000000000000001 (1)
00:00:08.078182
00:00:08.078182 [/Devices/vga/0/Config/] (level 4)
00:00:08.078183 3DEnabled <integer> = 0x0000000000000000 (0)
00:00:08.078184 CustomVideoModes <integer> = 0x0000000000000000 (0)
00:00:08.078184 FadeIn <integer> = 0x0000000000000001 (1)
00:00:08.078184 FadeOut <integer> = 0x0000000000000001 (1)
00:00:08.078185 HeightReduction <integer> = 0x0000000000000000 (0)
00:00:08.078185 LogoFile <string> = "" (cb=1)
00:00:08.078186 LogoTime <integer> = 0x0000000000000000 (0)
00:00:08.078186 MonitorCount <integer> = 0x0000000000000001 (1)
00:00:08.078186 ShowBootMenu <integer> = 0x0000000000000002 (2)
00:00:08.078187 VMSVGA3dEnabled <integer> = 0x0000000000000000 (0)
00:00:08.078187 VMSVGAEnabled <integer> = 0x0000000000000001 (1)
00:00:08.078187 VMSVGAPciBarLayout <integer> = 0x0000000000000001 (1)
00:00:08.078188 VMSVGAPciId <integer> = 0x0000000000000001 (1)
00:00:08.078188 VRamSize <integer> = 0x0000000001000000 (16 777 216, 16 MB)
00:00:08.078189
00:00:08.078189 [/Devices/vga/0/LUN#0/] (level 4)
00:00:08.078189 Driver <string> = "MainDisplay" (cb=12)
00:00:08.078190
00:00:08.078190 [/Devices/vga/0/LUN#0/Config/] (level 5)
00:00:08.078190 Object <integer> = 0x00000000036e2f00 (57 552 640)
00:00:08.078191
00:00:08.078191 [/Devices/vga/0/LUN#999/] (level 4)
00:00:08.078192 Driver <string> = "MainStatus" (cb=11)
00:00:08.078192
00:00:08.078192 [/Devices/vga/0/LUN#999/Config/] (level 5)
00:00:08.078193 First <integer> = 0x0000000000000000 (0)
00:00:08.078193 Last <integer> = 0x0000000000000000 (0)
00:00:08.078193 papLeds <integer> = 0x00000000036c35f0 (57 423 344)
00:00:08.078194
00:00:08.078194 [/Devices/virtio-net/] (level 2)
00:00:08.078194
00:00:08.078195 [/EM/] (level 1)
00:00:08.078195 TripleFaultReset <integer> = 0x0000000000000000 (0)
00:00:08.078195
00:00:08.078196 [/GIM/] (level 1)
00:00:08.078196 Provider <string> = "KVM" (cb=4)
00:00:08.078196
00:00:08.078196 [/HM/] (level 1)
00:00:08.078197 64bitEnabled <integer> = 0x0000000000000001 (1)
00:00:08.078198 EnableLargePages <integer> = 0x0000000000000001 (1)
00:00:08.078198 EnableNestedPaging <integer> = 0x0000000000000001 (1)
00:00:08.078199 EnableUX <integer> = 0x0000000000000001 (1)
00:00:08.078199 EnableVPID <integer> = 0x0000000000000001 (1)
00:00:08.078199 Exclusive <integer> = 0x0000000000000000 (0)
00:00:08.078200 HMForced <integer> = 0x0000000000000001 (1)
00:00:08.078200 IBPBOnVMEntry <integer> = 0x0000000000000000 (0)
00:00:08.078201 IBPBOnVMExit <integer> = 0x0000000000000000 (0)
00:00:08.078201 L1DFlushOnSched <integer> = 0x0000000000000001 (1)
00:00:08.078201 L1DFlushOnVMEntry <integer> = 0x0000000000000000 (0)
00:00:08.078202 LovelyMesaDrvWorkaround <integer> = 0x0000000000000001 (1)
00:00:08.078202 MDSClearOnSched <integer> = 0x0000000000000001 (1)
00:00:08.078203 MDSClearOnVMEntry <integer> = 0x0000000000000000 (0)
00:00:08.078203 SpecCtrlByHost <integer> = 0x0000000000000000 (0)
00:00:08.078203 UseNEMInstead <integer> = 0x0000000000000000 (0)
00:00:08.078204
00:00:08.078204 [/MM/] (level 1)
00:00:08.078204 CanUseLargerHeap <integer> = 0x0000000000000000 (0)
00:00:08.078205
00:00:08.078205 [/NEM/] (level 1)
00:00:08.078205 Allow64BitGuests <integer> = 0x0000000000000001 (1)
00:00:08.078206 LovelyMesaDrvWorkaround <integer> = 0x0000000000000001 (1)
00:00:08.078206
00:00:08.078206 [/PDM/] (level 1)
00:00:08.078207
00:00:08.078207 [/PDM/AsyncCompletion/] (level 2)
00:00:08.078207
00:00:08.078207 [/PDM/AsyncCompletion/File/] (level 3)
00:00:08.078208
00:00:08.078208 [/PDM/AsyncCompletion/File/BwGroups/] (level 4)
00:00:08.078208
00:00:08.078209 [/PDM/BlkCache/] (level 2)
00:00:08.078209 CacheSize <integer> = 0x0000000000500000 (5 242 880, 5 MB)
00:00:08.078210
00:00:08.078210 [/PDM/Devices/] (level 2)
00:00:08.078210
00:00:08.078210 [/PDM/Devices/VBoxEhci/] (level 3)
00:00:08.078211 Path <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR3.DLL" (cb=111)
00:00:08.078211 R0SearchPath <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64" (cb=96)
00:00:08.078212
00:00:08.078212 [/PDM/Devices/VBoxNvme/] (level 3)
00:00:08.078212 Path <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxNvmeR3.DLL" (cb=111)
00:00:08.078213 R0SearchPath <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64" (cb=96)
00:00:08.078213
00:00:08.078214 [/PDM/Drivers/] (level 2)
00:00:08.078214
00:00:08.078214 [/PDM/Drivers/DrvHostWebcam/] (level 3)
00:00:08.078214 Path <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.DLL" (cb=115)
00:00:08.078215
00:00:08.078215 [/PDM/Drivers/VBoxC/] (level 3)
00:00:08.078216 Path <string> = "VBoxC" (cb=6)
00:00:08.078216
00:00:08.078216 [/PDM/NetworkShaper/] (level 2)
00:00:08.078216
00:00:08.078216 [/PDM/NetworkShaper/BwGroups/] (level 3)
00:00:08.078217
00:00:08.078217 [/PDM/USB/] (level 2)
00:00:08.078217
00:00:08.078218 [/PDM/USB/VBoxUsbCardReader/] (level 3)
00:00:08.078218 Path <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbCardReaderR3.DLL" (cb=120)
00:00:08.078219
00:00:08.078219 [/PDM/USB/VBoxUsbWebcam/] (level 3)
00:00:08.078219 Path <string> = "C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbWebcamR3.DLL" (cb=116)
00:00:08.078220
00:00:08.078220 [/TM/] (level 1)
00:00:08.078220 UTCOffset <integer> = 0x0000000000000000 (0)
00:00:08.078220
00:00:08.078221 [/USB/] (level 1)
00:00:08.078221
00:00:08.078221 [/USB/USBProxy/] (level 2)
00:00:08.078221
00:00:08.078222 [/USB/USBProxy/GlobalConfig/] (level 3)
00:00:08.078222
00:00:08.078222 ********************* End of CFGM dump **********************
00:00:08.078259 HM: HMR3Init: Attempting fall back to NEM: VT-x is not available
00:00:08.126119 NEM: WHvCapabilityCodeHypervisorPresent is TRUE, so this might work...
00:00:08.126134 NEM: WHvCapabilityCodeExtendedVmExits = 0x00000000000003ff
00:00:08.126142 NEM: fExtendedMsrExit: 1
00:00:08.126149 NEM: fExtendedCpuIdExit: 1
00:00:08.126155 NEM: fExtendedXcptExit: 1
00:00:08.126164 NEM: Warning! Unknown VM exit definitions: 0x3ff
00:00:08.126171 NEM: Warning! Unknown feature definitions: 0x7f
00:00:08.126177 NEM: Supported exception exit bitmap: 0xf7dfb
00:00:08.126185 NEM: WHvCapabilityCodeProcessorVendor = 1 - Intel
00:00:08.126196 NEM: WHvCapabilityCodeProcessorFeatures = 0x081978cfe7f7859f
00:00:08.126203 NEM: Sse3Support: 1
00:00:08.126210 NEM: LahfSahfSupport: 1
00:00:08.126216 NEM: Ssse3Support: 1
00:00:08.126222 NEM: Sse4_1Support: 1
00:00:08.126228 NEM: Sse4_2Support: 1
00:00:08.126235 NEM: Sse4aSupport: 0
00:00:08.126242 NEM: XopSupport: 0
00:00:08.126248 NEM: PopCntSupport: 1
00:00:08.126255 NEM: Cmpxchg16bSupport: 1
00:00:08.126261 NEM: Altmovcr8Support: 0
00:00:08.126266 NEM: LzcntSupport: 1
00:00:08.126272 NEM: MisAlignSseSupport: 0
00:00:08.126278 NEM: MmxExtSupport: 0
00:00:08.126284 NEM: Amd3DNowSupport: 0
00:00:08.126290 NEM: ExtendedAmd3DNowSupport: 0
00:00:08.126297 NEM: Page1GbSupport: 1
00:00:08.126303 NEM: AesSupport: 1
00:00:08.126309 NEM: PclmulqdqSupport: 1
00:00:08.126316 NEM: PcidSupport: 1
00:00:08.126322 NEM: Fma4Support: 0
00:00:08.126328 NEM: F16CSupport: 1
00:00:08.126334 NEM: RdRandSupport: 1
00:00:08.126340 NEM: RdWrFsGsSupport: 1
00:00:08.126347 NEM: SmepSupport: 1
00:00:08.126353 NEM: EnhancedFastStringSupport: 1
00:00:08.126359 NEM: Bmi1Support: 1
00:00:08.126364 NEM: Bmi2Support: 1
00:00:08.126370 NEM: MovbeSupport: 1
00:00:08.126376 NEM: Npiep1Support: 1
00:00:08.126382 NEM: DepX87FPUSaveSupport: 1
00:00:08.126389 NEM: RdSeedSupport: 1
00:00:08.126395 NEM: AdxSupport: 1
00:00:08.126402 NEM: IntelPrefetchSupport: 1
00:00:08.126407 NEM: SmapSupport: 1
00:00:08.126413 NEM: HleSupport: 0
00:00:08.126419 NEM: RtmSupport: 0
00:00:08.126425 NEM: RdtscpSupport: 1
00:00:08.126431 NEM: ClflushoptSupport: 1
00:00:08.126437 NEM: ClwbSupport: 0
00:00:08.126444 NEM: ShaSupport: 0
00:00:08.126450 NEM: X87PointersSavedSupport: 0
00:00:08.126456 NEM: Warning! Unknown CPU features: 0x81978cfe7f7859f
00:00:08.126464 NEM: WHvCapabilityCodeProcessorClFlushSize = 2^8
00:00:08.126470 NEM: Warning! Unknown capability 0x4 returning: 3f 00 00 00 00 00 00 00
00:00:08.126733 NEM: Warning! Unknown capability 0x1003 returning: 3f 38 00 00 00 00 00 00
00:00:08.126748 NEM: Warning! Unknown capability 0x1004 returning: 1c f8 a5 a1 00 00 00 00
00:00:08.126755 NEM: Warning! Unknown capability 0x1005 returning: 00 c2 eb 0b 00 00 00 00
00:00:08.127228 NEM: VidGetHvPartitionId -> fun:0x2210af in:0x0 out:0x8
00:00:08.127238 NEM: VidStartVirtualProcessor -> fun:0x221184 in:0x4 out:0x0
00:00:08.127244 NEM: VidStopVirtualProcessor -> fun:0x221190 in:0x4 out:0x0
00:00:08.127252 NEM: VidMessageSlotHandleAndGetNext -> fun:0x2210ef in:0x8 out:0x0
00:00:08.127346 NEM: Created partition 0000000001a307c0.
00:00:08.127359 NEM: Adjusting APIC configuration from X2APIC to APIC max mode. X2APIC is not supported by the WinHvPlatform API!
00:00:08.127365 NEM: Disable Hyper-V if you need X2APIC for your guests!
00:00:08.127426 NEM: NEMR3Init: Active.
00:00:08.127440 MM: cbHyperHeap=0x200000 (2097152)
00:00:08.129414 CPUM: No hardware-virtualization capability detected
00:00:08.130606 CPUM: fXStateHostMask=0x7; initial: 0x7; host XCR0=0x1f
00:00:08.131859 CPUM: Matched host CPU INTEL 0x6/0xa5/0x2 Intel_Core7_CometLake with CPU DB entry 'Intel Core i7-6700K' (INTEL 0x6/0x5e/0x3 Intel_Core7_Skylake)
00:00:08.131917 CPUM: MXCSR_MASK=0xffff (host: 0xffff)
00:00:08.131934 CPUM: Microcode revision 0x000000EC
00:00:08.131949 CPUM: MSR/CPUID reconciliation insert: 0x0000010b IA32_FLUSH_CMD
00:00:08.131958 CPUM: MSR/CPUID reconciliation insert: 0x0000010a IA32_ARCH_CAPABILITIES
00:00:08.131967 CPUM: MSR fudge: 0x00000122 IA32_TSX_CTRL
00:00:08.131982 CPUM: SetGuestCpuIdFeature: Enabled PAE
00:00:08.131990 CPUM: SetGuestCpuIdFeature: Enabled SYSENTER/EXIT
00:00:08.131997 CPUM: SetGuestCpuIdFeature: Enabled SYSCALL/RET
00:00:08.132003 CPUM: SetGuestCpuIdFeature: Enabled PAE
00:00:08.132009 CPUM: SetGuestCpuIdFeature: Enabled LONG MODE
00:00:08.132015 CPUM: SetGuestCpuIdFeature: Enabled LAHF/SAHF
00:00:08.132021 CPUM: SetGuestCpuIdFeature: Enabled NX
00:00:08.133566 NEM: Successfully set up partition (device handle 0000000000000ea0, partition ID 0x8)
00:00:08.133595 NEM: Memory balance: 0xa2 out of 0x15e pages in use
00:00:08.133693 PGM: Host paging mode: AMD64+PGE+NX
00:00:08.133705 PGM: PGMPool: cMaxPages=1280 (u64MaxPages=1058)
00:00:08.133713 PGM: pgmR3PoolInit: cMaxPages=0x500 cMaxUsers=0xa00 cMaxPhysExts=0xa00 fCacheEnable=true
00:00:08.141868 TM: GIP - u32Mode=3 (Invariant) u32UpdateHz=93 u32UpdateIntervalNS=10741500 enmUseTscDelta=2 (Practically Zero) fGetGipCpu=0x1b cCpus=12
00:00:08.141893 TM: GIP - u64CpuHz=2 712 008 721 (0xa1a5f811) SUPGetCpuHzFromGip => 2 712 008 721
00:00:08.141903 TM: GIP - CPU: iCpuSet=0x0 idCpu=0x0 idApic=0x0 iGipCpu=0x0 i64TSCDelta=0 enmState=3 u64CpuHz=2712008721(*) cErrors=0
00:00:08.141910 TM: GIP - CPU: iCpuSet=0x1 idCpu=0x1 idApic=0x1 iGipCpu=0x7 i64TSCDelta=0 enmState=3 u64CpuHz=2712008718(*) cErrors=0
00:00:08.141917 TM: GIP - CPU: iCpuSet=0x2 idCpu=0x2 idApic=0x2 iGipCpu=0x2 i64TSCDelta=0 enmState=3 u64CpuHz=2712008534(*) cErrors=0
00:00:08.141923 TM: GIP - CPU: iCpuSet=0x3 idCpu=0x3 idApic=0x3 iGipCpu=0xa i64TSCDelta=0 enmState=3 u64CpuHz=2712008689(*) cErrors=0
00:00:08.141929 TM: GIP - CPU: iCpuSet=0x4 idCpu=0x4 idApic=0x4 iGipCpu=0x9 i64TSCDelta=0 enmState=3 u64CpuHz=2712008664(*) cErrors=0
00:00:08.141936 TM: GIP - CPU: iCpuSet=0x5 idCpu=0x5 idApic=0x5 iGipCpu=0x3 i64TSCDelta=0 enmState=3 u64CpuHz=2712008317(*) cErrors=0
00:00:08.141942 TM: GIP - CPU: iCpuSet=0x6 idCpu=0x6 idApic=0x6 iGipCpu=0x5 i64TSCDelta=0 enmState=3 u64CpuHz=2712008607(*) cErrors=0
00:00:08.141949 TM: GIP - CPU: iCpuSet=0x7 idCpu=0x7 idApic=0x7 iGipCpu=0xb i64TSCDelta=0 enmState=3 u64CpuHz=2712008692(*) cErrors=0
00:00:08.141955 TM: GIP - CPU: iCpuSet=0x8 idCpu=0x8 idApic=0x8 iGipCpu=0x8 i64TSCDelta=0 enmState=3 u64CpuHz=2712008660(*) cErrors=0
00:00:08.141962 TM: GIP - CPU: iCpuSet=0x9 idCpu=0x9 idApic=0x9 iGipCpu=0x1 i64TSCDelta=0 enmState=3 u64CpuHz=2711996835(*) cErrors=0
00:00:08.141968 TM: GIP - CPU: iCpuSet=0xa idCpu=0xa idApic=0xa iGipCpu=0x6 i64TSCDelta=0 enmState=3 u64CpuHz=2712008611(*) cErrors=0
00:00:08.141974 TM: GIP - CPU: iCpuSet=0xb idCpu=0xb idApic=0xb iGipCpu=0x4 i64TSCDelta=0 enmState=3 u64CpuHz=2712008524(*) cErrors=0
00:00:08.141995 TM: NEM overrides the /TM/TSCModeSwitchAllowed setting.
00:00:08.142007 TM: cTSCTicksPerSecond=2 712 008 721 (0xa1a5f811) enmTSCMode=4 (NativeApi)
00:00:08.142009 TM: TSCTiedToExecution=false TSCNotTiedToHalt=false
00:00:08.142479 EMR3Init: fIemExecutesAll=false fGuruOnTripleFault=true
00:00:08.142580 IEM: TargetCpu=CURRENT, Microarch=Intel_Core7_CometLake
00:00:08.142645 GIM: Using provider 'KVM' (Implementation version: 0)
00:00:08.142655 CPUM: SetGuestCpuIdFeature: Enabled Hypervisor Present bit
00:00:08.142705 AIOMgr: Default manager type is 'Async'
00:00:08.142714 AIOMgr: Default file backend is 'NonBuffered'
00:00:08.142964 BlkCache: Cache successfully initialized. Cache size is 5242880 bytes
00:00:08.142986 BlkCache: Cache commit interval is 10000 ms
00:00:08.142994 BlkCache: Cache commit threshold is 2621440 bytes
00:00:08.605442 PcBios: [SMP] BIOS with 1 CPUs
00:00:08.605466 PcBios: Using the 386+ BIOS image.
00:00:08.605513 PcBios: MPS table at 000e1300
00:00:08.607589 PcBios: Using LAN ROM 'C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\PXE-Intel.rom' with a size of 0xc000 bytes
00:00:08.607674 PcBios: fCheckShutdownStatusForSoftReset=true fClearShutdownStatusOnHardReset=true
00:00:08.625286 SUP: seg #0: R 0x00000000 LB 0x00001000
00:00:08.625303 SUP: seg #1: R X 0x00001000 LB 0x0001e000
00:00:08.625312 SUP: seg #2: R 0x0001f000 LB 0x0000c000
00:00:08.625318 SUP: seg #3: RW 0x0002b000 LB 0x00001000
00:00:08.625324 SUP: seg #4: R 0x0002c000 LB 0x00002000
00:00:08.625330 SUP: seg #5: RW 0x0002e000 LB 0x00001000
00:00:08.625336 SUP: seg #6: R 0x0002f000 LB 0x00001000
00:00:08.625342 SUP: seg #7: RWX 0x00030000 LB 0x00001000
00:00:08.625348 SUP: seg #8: R 0x00031000 LB 0x00002000
00:00:08.625391 SUP: Loaded VBoxDDR0.r0 (C:\Program Files\Oracle\VirtualBox\VBoxDDR0.r0) at 0xXXXXXXXXXXXXXXXX - ModuleInit at XXXXXXXXXXXXXXXX and ModuleTerm at XXXXXXXXXXXXXXXX using the native ring-0 loader
00:00:08.625400 SUP: windbg> .reload /f C:\Program Files\Oracle\VirtualBox\VBoxDDR0.r0=0xXXXXXXXXXXXXXXXX
00:00:08.625572 CPUM: SetGuestCpuIdFeature: Enabled xAPIC
00:00:08.625722 IOAPIC: Using implementation 2.0! Chipset type ICH9
00:00:08.625765 PIT: mode=3 count=0x10000 (65536) - 18.20 Hz (ch=0)
00:00:08.625949 VMMDev: cbDefaultBudget: 529 995 392 (1f971680)
00:00:08.640766 Shared Folders service loaded
00:00:08.651493 Guest Control service loaded
00:00:08.679473 VGA: Using the 386+ BIOS image.
00:00:08.681647 VD: VDInit finished with VINF_SUCCESS
00:00:08.700394 DrvVD: Flushes will be ignored
00:00:08.700405 DrvVD: Async flushes will be passed to the disk
00:00:08.701629 AIOMgr: Endpoint for file 'C:\Users\cen1wa3\VirtualBox VMs\RHEL9\RHEL9.vmdk' (flags 000c0723) created successfully
00:00:08.713814 AIOMgr: Async flushes not supported
00:00:08.713897 VD: Opening the disk took 12881274 ns
00:00:08.713971 AHCI: LUN#0: disk, PCHS=16383/16/63, total number of sectors 16777216
00:00:08.714239 AHCI#0: Reset the HBA
00:00:08.714251 VD#0: Cancelling all active requests
00:00:08.716453 DrvVD: Flushes will be ignored
00:00:08.716465 DrvVD: Async flushes will be passed to the disk
00:00:08.716553 VD: Opening the disk took 78130 ns
00:00:08.716578 PIIX3 ATA: LUN#0: CD/DVD, total number of sectors 392192, passthrough disabled
00:00:08.716619 PIIX3 ATA: LUN#1: no unit
00:00:08.716690 DrvVD: Flushes will be ignored
00:00:08.716701 DrvVD: Async flushes will be passed to the disk
00:00:08.716747 VD: Opening the disk took 37431 ns
00:00:08.716769 PIIX3 ATA: LUN#2: CD/DVD, total number of sectors 392192, passthrough disabled
00:00:08.716778 PIIX3 ATA: LUN#3: no unit
00:00:08.716850 PIIX3 ATA: Ctl#1: finished processing RESET
00:00:08.716890 PIIX3 ATA: Ctl#0: finished processing RESET
00:00:08.716970 E1000#0: Chip=82540EM LinkUpDelay=3000ms EthernetCRC=on GSO=enabled Itr=disabled ItrRx=enabled TID=disabled R0=enabled RC=disabled
00:00:08.717118 IntNet#0: szNetwork={HostInterfaceNetworking-Intel(R) Wi-Fi 6 AX201 160MHz} enmTrunkType=3 szTrunk={\DEVICE\{FB5AF5B5-8FF3-4CC3-9B4E-C01F8129AB07}} fFlags=0x8001 cbRecv=325632 cbSend=196608 fIgnoreConnectFailure=false
00:00:08.717665 AC97: Using codec 'AD1980'
00:00:08.762808 Audio: Found 8 devices for driver 'WasAPI'
00:00:08.762841 Audio: Device 'Headphones (Poly V4320 Series Stereo)':
00:00:08.762855 Audio: ID = {0.0.0.00000000}.{f77d0a8c-671e-4e8b-b4e4-c3a85e2f1fb4}
00:00:08.762856 Audio: Usage = output
00:00:08.762856 Audio: Flags = DEFAULT_OUT
00:00:08.762857 Audio: Input channels = 0
00:00:08.762857 Audio: Output channels = 2
00:00:08.762885 Audio: Device 'Headset (Poly V4320 Series Hands-Free AG Audio)':
00:00:08.762885 Audio: ID = {0.0.0.00000000}.{96647c91-ea9e-4899-87ac-42c54a6120dd}
00:00:08.762885 Audio: Usage = output
00:00:08.762886 Audio: Flags = NONE
00:00:08.762886 Audio: Input channels = 0
00:00:08.762886 Audio: Output channels = 1
00:00:08.762895 Audio: Device 'Headphones (Poly V4320 Series Stereo)':
00:00:08.762896 Audio: ID = {0.0.0.00000000}.{f77d0a8c-671e-4e8b-b4e4-c3a85e2f1fb4}
00:00:08.762896 Audio: Usage = output
00:00:08.762896 Audio: Flags = NONE
00:00:08.762896 Audio: Input channels = 0
00:00:08.762896 Audio: Output channels = 2
00:00:08.762924 Audio: Device 'Speakers (Realtek(R) Audio)':
00:00:08.762925 Audio: ID = {0.0.0.00000000}.{fc7b673c-ccd8-4b3a-8e4b-640ea5eab7f6}
00:00:08.762925 Audio: Usage = output
00:00:08.762925 Audio: Flags = NONE
00:00:08.762925 Audio: Input channels = 0
00:00:08.762926 Audio: Output channels = 2
00:00:08.762932 Audio: Device 'Stereo Mix (Realtek(R) Audio)':
00:00:08.762932 Audio: ID = {0.0.1.00000000}.{16d55b9b-421e-43ad-9f17-adf951a84869}
00:00:08.762933 Audio: Usage = input
00:00:08.762933 Audio: Flags = DEFAULT_IN
00:00:08.762933 Audio: Input channels = 2
00:00:08.762933 Audio: Output channels = 0
00:00:08.762940 Audio: Device 'Microphone Array (2- Intel® Smart Sound Technology (Intel® SST))':
00:00:08.762940 Audio: ID = {0.0.1.00000000}.{10dfed76-2efb-42d6-a471-8c97c956479d}
00:00:08.762940 Audio: Usage = input
00:00:08.762941 Audio: Flags = NONE
00:00:08.762941 Audio: Input channels = 4
00:00:08.762941 Audio: Output channels = 0
00:00:08.762947 Audio: Device 'Stereo Mix (Realtek(R) Audio)':
00:00:08.762947 Audio: ID = {0.0.1.00000000}.{16d55b9b-421e-43ad-9f17-adf951a84869}
00:00:08.762948 Audio: Usage = input
00:00:08.762948 Audio: Flags = NONE
00:00:08.762948 Audio: Input channels = 2
00:00:08.762948 Audio: Output channels = 0
00:00:08.762954 Audio: Device 'Headset (Poly V4320 Series Hands-Free AG Audio)':
00:00:08.762955 Audio: ID = {0.0.1.00000000}.{acbd093e-9f94-40aa-95f4-72ba1fe09869}
00:00:08.762955 Audio: Usage = input
00:00:08.762955 Audio: Flags = NONE
00:00:08.762955 Audio: Input channels = 1
00:00:08.762956 Audio: Output channels = 0
00:00:08.763264 AC97: Reset
00:00:08.763278 AC97: Mixer reset (EAID=0x809, EACS=0x9)
00:00:08.763287 AC97: Record select to left=mic, right=mic
00:00:08.778163 SUP: seg #0: R 0x00000000 LB 0x00001000
00:00:08.778177 SUP: seg #1: R X 0x00001000 LB 0x00002000
00:00:08.778184 SUP: seg #2: R 0x00003000 LB 0x00001000
00:00:08.778190 SUP: seg #3: RW 0x00004000 LB 0x00001000
00:00:08.778196 SUP: seg #4: R 0x00005000 LB 0x00002000
00:00:08.778202 SUP: seg #5: RWX 0x00007000 LB 0x00001000
00:00:08.778207 SUP: seg #6: R 0x00008000 LB 0x00002000
00:00:08.778229 SUP: Loaded VBoxEhciR0.r0 (C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR0.r0) at 0xXXXXXXXXXXXXXXXX - ModuleInit at XXXXXXXXXXXXXXXX and ModuleTerm at XXXXXXXXXXXXXXXX using the native ring-0 loader
00:00:08.778237 SUP: windbg> .reload /f C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR0.r0=0xXXXXXXXXXXXXXXXX
00:00:08.778992 PGM: The CPU physical address width is 39 bits
00:00:08.779031 PGM: PGMR3InitFinalize: 4 MB PSE mask 0000007fffffffff -> VINF_SUCCESS
00:00:08.779154 TM: TMR3InitFinalize: fTSCModeSwitchAllowed=false
00:00:08.779290 VMM: Thread-context hooks unavailable
00:00:08.779302 VMM: RTThreadPreemptIsPending() can be trusted
00:00:08.779309 VMM: Kernel preemption is possible
00:00:08.779320 EM: Exit history optimizations: enabled=true enabled-r0=true enabled-r0-no-preemption=false
00:00:08.779647 PcBios: SATA LUN#0 LCHS=1024/255/63
00:00:08.779694 APIC: fPostedIntrsEnabled=false fVirtApicRegsEnabled=false fSupportsTscDeadline=false
00:00:08.779730 TMR3UtcNow: nsNow=1 658 918 019 897 112 200 nsPrev=0 -> cNsDelta=1 658 918 019 897 112 200 (offLag=0 offVirtualSync=0 offVirtualSyncGivenUp=0, NowAgain=1 658 918 019 897 112 200)
00:00:08.779742 VMM: fUsePeriodicPreemptionTimers=false
00:00:08.779773 CPUM: Logical host processors: 12 present, 12 max, 12 online, online mask: 0000000000000fff
00:00:08.779774 CPUM: Physical host cores: 6
00:00:08.779774 ************************* CPUID dump ************************
00:00:08.779779 Raw Standard CPUID Leaves
00:00:08.779779 Leaf/sub-leaf eax ebx ecx edx
00:00:08.779781 Gst: 00000000/0000 00000016 756e6547 6c65746e 49656e69
00:00:08.779782 Hst: 00000016 756e6547 6c65746e 49656e69
00:00:08.779783 Gst: 00000001/0000 000a0652 00010800 801a2201 178bfbff
00:00:08.779784 Hst: 000a0652 0b100800 fefaf387 bfebfbff
00:00:08.779785 Gst: 00000002/0000 76036301 00f0b5ff 00000000 00c30000
00:00:08.779786 Hst: 76036301 00f0b5ff 00000000 00c30000
00:00:08.779787 Gst: 00000003/0000 00000000 00000000 00000000 00000000
00:00:08.779787 Hst: 00000000 00000000 00000000 00000000
00:00:08.779788 Gst: 00000004/0000 00000121 01c0003f 0000003f 00000000
00:00:08.779789 Hst: 1c004121 01c0003f 0000003f 00000000
00:00:08.779790 Gst: 00000004/0001 00000122 01c0003f 0000003f 00000000
00:00:08.779790 Hst: 1c004122 01c0003f 0000003f 00000000
00:00:08.779791 Gst: 00000004/0002 00000143 00c0003f 000003ff 00000000
00:00:08.779792 Hst: 1c004143 00c0003f 000003ff 00000000
00:00:08.779793 Gst: 00000004/0003 00000163 03c0003f 00002fff 00000002
00:00:08.779793 Hst: 1c03c163 03c0003f 00002fff 00000002
00:00:08.779794 Gst: 00000004/0004 00000000 00000000 00000000 00000000
00:00:08.779795 Hst: 00000000 00000000 00000000 00000000
00:00:08.779795 Gst: 00000005/0000 00000000 00000000 00000000 00000000
00:00:08.779796 Hst: 00000000 00000000 00000000 00000000
00:00:08.779797 Gst: 00000006/0000 00000000 00000000 00000000 00000000
00:00:08.779797 Hst: 000007f3 00000002 00000009 00000000
00:00:08.779798 Gst: 00000007/0000 00000000 00002401 00000000 30000400
00:00:08.779799 Hst: 00000000 009c67ab 00000000 bc000400
00:00:08.779800 Gst: 00000007/0001 00000000 00000000 00000000 00000000
00:00:08.779800 Hst: 00000000 00000000 00000000 00000000
00:00:08.779801 Gst: 00000008/0000 00000000 00000000 00000000 00000000
00:00:08.779801 Hst: 00000000 00000000 00000000 00000000
00:00:08.779802 Gst: 00000009/0000 00000000 00000000 00000000 00000000
00:00:08.779802 Hst: 00000000 00000000 00000000 00000000
00:00:08.779803 Gst: 0000000a/0000 00000000 00000000 00000000 00000000
00:00:08.779803 Hst: 07300404 00000000 00000000 00000603
00:00:08.779804 Gst: 0000000b/0000 00000000 00000001 00000100 00000000
00:00:08.779805 Hst: 00000001 00000002 00000100 0000000b
00:00:08.779805 Gst: 0000000b/0001 00000001 00000001 00000201 00000000
00:00:08.779806 Hst: 00000004 0000000c 00000201 0000000b
00:00:08.779807 Gst: 0000000b/0002 00000000 00000000 00000002 00000000
00:00:08.779807 Hst: 00000000 00000000 00000002 0000000b
00:00:08.779808 Gst: 0000000c/0000 00000000 00000000 00000000 00000000
00:00:08.779808 Hst: 00000000 00000000 00000000 00000000
00:00:08.779809 Gst: 0000000d/0000 00000000 00000000 00000000 00000000
00:00:08.779810 Hst: 0000001f 00000440 00000440 00000000
00:00:08.779811 Gst: 0000000d/0001 00000000 00000000 00000000 00000000
00:00:08.779811 Hst: 0000000f 000003c0 00000000 00000000
00:00:08.779812 Gst: 0000000d/0002 00000000 00000000 00000000 00000000
00:00:08.779812 Hst: 00000100 00000240 00000000 00000000
00:00:08.779829 Gst: 0000000d/0003 00000000 00000000 00000000 00000000
00:00:08.779830 Hst: 00000040 000003c0 00000000 00000000
00:00:08.779830 Gst: 0000000d/0004 00000000 00000000 00000000 00000000
00:00:08.779831 Hst: 00000040 00000400 00000000 00000000
00:00:08.779831 Gst: 0000000d/0005 00000000 00000000 00000000 00000000
00:00:08.779832 Hst: 00000000 00000000 00000000 00000000
00:00:08.779871 Gst: 0000000e/0000 00000000 00000000 00000000 00000000
00:00:08.779872 Hst: 00000000 00000000 00000000 00000000
00:00:08.779872 Gst: 0000000f/0000 00000000 00000000 00000000 00000000
00:00:08.779873 Hst: 00000000 00000000 00000000 00000000
00:00:08.779873 Gst: 00000010/0000 00000000 00000000 00000000 00000000
00:00:08.779874 Hst: 00000000 00000000 00000000 00000000
00:00:08.779889 Gst: 00000011/0000 00000000 00000000 00000000 00000000
00:00:08.779889 Hst: 00000000 00000000 00000000 00000000
00:00:08.779890 Gst: 00000012/0000 00000000 00000000 00000000 00000000
00:00:08.779890 Hst: 00000000 00000000 00000000 00000000
00:00:08.779891 Gst: 00000013/0000 00000000 00000000 00000000 00000000
00:00:08.779891 Hst: 00000000 00000000 00000000 00000000
00:00:08.779892 Gst: 00000014/0000 00000000 00000000 00000000 00000000
00:00:08.779892 Hst: 00000001 0000000f 00000003 00000000
00:00:08.779893 Hst: 00000015/0000 00000002 000000e2 00000000 00000000
00:00:08.779894 Hst: 00000016/0000 00000000 00000000 00000000 00000000
00:00:08.779894 Name: GenuineIntel
00:00:08.779895 Supports: 0x00000000-0x00000016
00:00:08.779897 Family: 6 Extended: 0 Effective: 6
00:00:08.779897 Model: 5 Extended: 10 Effective: 165
00:00:08.779898 Stepping: 2
00:00:08.779898 Type: 0 (primary)
00:00:08.779899 APIC ID: 0x00
00:00:08.779899 Logical CPUs: 1
00:00:08.779900 CLFLUSH Size: 8
00:00:08.779900 Brand ID: 0x00
00:00:08.779901 Features
00:00:08.779901 Mnemonic - Description = guest (host)
00:00:08.779902 FPU - x87 FPU on Chip = 1 (1)
00:00:08.779903 VME - Virtual 8086 Mode Enhancements = 1 (1)
00:00:08.779904 DE - Debugging extensions = 1 (1)
00:00:08.779904 PSE - Page Size Extension = 1 (1)
00:00:08.779905 TSC - Time Stamp Counter = 1 (1)
00:00:08.779905 MSR - Model Specific Registers = 1 (1)
00:00:08.779906 PAE - Physical Address Extension = 1 (1)
00:00:08.779906 MCE - Machine Check Exception = 1 (1)
00:00:08.779907 CX8 - CMPXCHG8B instruction = 1 (1)
00:00:08.779907 APIC - APIC On-Chip = 1 (1)
00:00:08.779908 SEP - SYSENTER and SYSEXIT Present = 1 (1)
00:00:08.779908 MTRR - Memory Type Range Registers = 1 (1)
00:00:08.779909 PGE - PTE Global Bit = 1 (1)
00:00:08.779909 MCA - Machine Check Architecture = 1 (1)
00:00:08.779910 CMOV - Conditional Move instructions = 1 (1)
00:00:08.779910 PAT - Page Attribute Table = 1 (1)
00:00:08.779911 PSE-36 - 36-bit Page Size Extension = 1 (1)
00:00:08.779911 PSN - Processor Serial Number = 0 (0)
00:00:08.779912 CLFSH - CLFLUSH instruction = 1 (1)
00:00:08.779912 DS - Debug Store = 0 (1)
00:00:08.779913 ACPI - Thermal Mon. & Soft. Clock Ctrl. = 0 (1)
00:00:08.779913 MMX - Intel MMX Technology = 1 (1)
00:00:08.779914 FXSR - FXSAVE and FXRSTOR instructions = 1 (1)
00:00:08.779914 SSE - SSE support = 1 (1)
00:00:08.779915 SSE2 - SSE2 support = 1 (1)
00:00:08.779916 SS - Self Snoop = 0 (1)
00:00:08.779916 HTT - Hyper-Threading Technology = 1 (1)
00:00:08.779917 TM - Therm. Monitor = 0 (1)
00:00:08.779917 PBE - Pending Break Enabled = 0 (1)
00:00:08.779918 SSE3 - SSE3 support = 1 (1)
00:00:08.779918 PCLMUL - PCLMULQDQ support (for AES-GCM) = 0 (1)
00:00:08.779919 DTES64 - DS Area 64-bit Layout = 0 (1)
00:00:08.779919 MONITOR - MONITOR/MWAIT instructions = 0 (0)
00:00:08.779920 CPL-DS - CPL Qualified Debug Store = 0 (0)
00:00:08.779920 VMX - Virtual Machine Extensions = 0 (0)
00:00:08.779921 SMX - Safer Mode Extensions = 0 (0)
00:00:08.779921 EST - Enhanced SpeedStep Technology = 0 (1)
00:00:08.779922 TM2 - Terminal Monitor 2 = 0 (1)
00:00:08.779922 SSSE3 - Supplemental Streaming SIMD Extensions 3 = 1 (1)
00:00:08.779922 CNTX-ID - L1 Context ID = 0 (0)
00:00:08.779923 SDBG - Silicon Debug interface = 0 (0)
00:00:08.779924 FMA - Fused Multiply Add extensions = 0 (1)
00:00:08.779924 CX16 - CMPXCHG16B instruction = 1 (1)
00:00:08.779924 TPRUPDATE - xTPR Update Control = 0 (1)
00:00:08.779925 PDCM - Perf/Debug Capability MSR = 0 (1)
00:00:08.779925 PCID - Process Context Identifiers = 1 (1)
00:00:08.779926 DCA - Direct Cache Access = 0 (0)
00:00:08.779926 SSE4_1 - SSE4_1 support = 1 (1)
00:00:08.779927 SSE4_2 - SSE4_2 support = 1 (1)
00:00:08.779927 X2APIC - x2APIC support = 0 (1)
00:00:08.779928 MOVBE - MOVBE instruction = 0 (1)
00:00:08.779928 POPCNT - POPCNT instruction = 0 (1)
00:00:08.779929 TSCDEADL - Time Stamp Counter Deadline = 0 (0)
00:00:08.779929 AES - AES instructions = 0 (1)
00:00:08.779930 XSAVE - XSAVE instruction = 0 (1)
00:00:08.779930 OSXSAVE - OSXSAVE instruction = 0 (1)
00:00:08.779931 AVX - AVX support = 0 (1)
00:00:08.779931 F16C - 16-bit floating point conversion instructions = 0 (1)
00:00:08.779932 RDRAND - RDRAND instruction = 0 (1)
00:00:08.779932 HVP - Hypervisor Present (we're a guest) = 1 (1)
00:00:08.779933 Structured Extended Feature Flags Enumeration (leaf 7):
00:00:08.779934 Mnemonic - Description = guest (host)
00:00:08.779934 FSGSBASE - RDFSBASE/RDGSBASE/WRFSBASE/WRGSBASE instr. = 1 (1)
00:00:08.779934 TSCADJUST - Supports MSR_IA32_TSC_ADJUST = 0 (1)
00:00:08.779935 SGX - Supports Software Guard Extensions = 0 (0)
00:00:08.779935 BMI1 - Advanced Bit Manipulation extension 1 = 0 (1)
00:00:08.779936 HLE - Hardware Lock Elision = 0 (0)
00:00:08.779936 AVX2 - Advanced Vector Extensions 2 = 0 (1)
00:00:08.779937 FDP_EXCPTN_ONLY - FPU DP only updated on exceptions = 0 (0)
00:00:08.779937 SMEP - Supervisor Mode Execution Prevention = 0 (1)
00:00:08.779938 BMI2 - Advanced Bit Manipulation extension 2 = 0 (1)
00:00:08.779938 ERMS - Enhanced REP MOVSB/STOSB instructions = 0 (1)
00:00:08.779938 INVPCID - INVPCID instruction = 1 (1)
00:00:08.779939 RTM - Restricted Transactional Memory = 0 (0)
00:00:08.779939 PQM - Platform Quality of Service Monitoring = 0 (0)
00:00:08.779940 DEPFPU_CS_DS - Deprecates FPU CS, FPU DS values if set = 1 (1)
00:00:08.779940 MPE - Intel Memory Protection Extensions = 0 (1)
00:00:08.779941 PQE - Platform Quality of Service Enforcement = 0 (0)
00:00:08.779941 AVX512F - AVX512 Foundation instructions = 0 (0)
00:00:08.779941 RDSEED - RDSEED instruction = 0 (1)
00:00:08.779942 ADX - ADCX/ADOX instructions = 0 (1)
00:00:08.779942 SMAP - Supervisor Mode Access Prevention = 0 (1)
00:00:08.779943 CLFLUSHOPT - CLFLUSHOPT (Cache Line Flush) instruction = 0 (1)
00:00:08.779943 INTEL_PT - Intel Processor Trace = 0 (0)
00:00:08.779944 AVX512PF - AVX512 Prefetch instructions = 0 (0)
00:00:08.779944 AVX512ER - AVX512 Exponential & Reciprocal instructions = 0 (0)
00:00:08.779945 AVX512CD - AVX512 Conflict Detection instructions = 0 (0)
00:00:08.779945 SHA - Secure Hash Algorithm extensions = 0 (0)
00:00:08.779946 PREFETCHWT1 - PREFETCHWT1 instruction = 0 (0)
00:00:08.779946 UMIP - User mode insturction prevention = 0 (0)
00:00:08.779947 PKU - Protection Key for Usermode pages = 0 (0)
00:00:08.779947 OSPKE - CR4.PKU mirror = 0 (0)
00:00:08.779948 MAWAU - Value used by BNDLDX & BNDSTX = 0x0 (0x0)
00:00:08.779948 RDPID - Read processor ID support = 0 (0)
00:00:08.779949 SGX_LC - Supports SGX Launch Configuration = 0 (0)
00:00:08.779949 MD_CLEAR - Supports MDS related buffer clearing = 1 (1)
00:00:08.779950 IBRS_IBPB - IA32_SPEC_CTRL.IBRS and IA32_PRED_CMD.IBPB = 0 (1)
00:00:08.779950 STIBP - Supports IA32_SPEC_CTRL.STIBP = 0 (1)
00:00:08.779950 FLUSH_CMD - Supports IA32_FLUSH_CMD = 1 (1)
00:00:08.779951 ARCHCAP - Supports IA32_ARCH_CAP = 1 (1)
00:00:08.779951 CORECAP - Supports IA32_CORE_CAP = 0 (0)
00:00:08.779952 SSBD - Supports IA32_SPEC_CTRL.SSBD = 0 (1)
00:00:08.779953 Processor Extended State Enumeration (leaf 0xd):
00:00:08.779954 XSAVE area cur/max size by XCR0, guest: 0x0/0x0
00:00:08.779954 XSAVE area cur/max size by XCR0, host: 0x440/0x440
00:00:08.779955 Valid XCR0 bits, guest: 0x00000000`00000000
00:00:08.779955 Valid XCR0 bits, host: 0x00000000`0000001f ( x87 SSE YMM_Hi128 BNDREGS BNDCSR )
00:00:08.779957 XSAVE features, guest:
00:00:08.779957 XSAVE features, host: XSAVEOPT XSAVEC XGETBC1 XSAVES
00:00:08.779959 XSAVE area cur size XCR0|XSS, guest: 0x0
00:00:08.779960 XSAVE area cur size XCR0|XSS, host: 0x3c0
00:00:08.779960 Valid IA32_XSS bits, guest: 0x00000000`00000000
00:00:08.779961 Valid IA32_XSS bits, host: 0x00000000`00000000
00:00:08.779962 State #2, host: off=0x0240, cb=0x0100 IA32_XSS-bit -- YMM_Hi128
00:00:08.779963 State #3, host: off=0x03c0, cb=0x0040 IA32_XSS-bit -- BNDREGS
00:00:08.779964 State #4, host: off=0x0400, cb=0x0040 IA32_XSS-bit -- BNDCSR
00:00:08.779983 Unknown CPUID Leaves
00:00:08.779983 Leaf/sub-leaf eax ebx ecx edx
00:00:08.779984 Gst: 00000014/0001 00000000 00000000 00000000 00000000
00:00:08.779984 Hst: 02490002 003f3fff 00000000 00000000
00:00:08.779985 Gst: 00000014/0002 00000000 00000000 00000000 00000000
00:00:08.779986 Hst: 00000000 00000000 00000000 00000000
00:00:08.779986 Gst: 00000015/0000 00000000 00000000 00000000 00000000
00:00:08.779987 Hst: 00000002 000000e2 00000000 00000000
00:00:08.779988 Gst: 00000016/0000 00000000 00000000 00000000 00000000
00:00:08.779988 Hst: 00000000 00000000 00000000 00000000
00:00:08.779989 Raw Hypervisor CPUID Leaves
00:00:08.779989 Leaf/sub-leaf eax ebx ecx edx
00:00:08.779990 Gst: 40000000/0000 40000001 4b4d564b 564b4d56 0000004d
00:00:08.779991 Hst: 4000000b 7263694d 666f736f 76482074
00:00:08.779992 Gst: 40000001/0000 01000089 00000000 00000000 00000000
00:00:08.779992 Hst: 31237648 00000000 00000000 00000000
00:00:08.779993 Raw Extended CPUID Leaves
00:00:08.779993 Leaf/sub-leaf eax ebx ecx edx
00:00:08.779994 Gst: 80000000/0000 80000008 00000000 00000000 00000000
00:00:08.779994 Hst: 80000008 00000000 00000000 00000000
00:00:08.779995 Gst: 80000001/0000 00000000 00000000 00000001 28100800
00:00:08.779995 Hst: 00000000 00000000 00000121 2c100800
00:00:08.779996 Gst: 80000002/0000 65746e49 2952286c 726f4320 4d542865
00:00:08.779997 Hst: 65746e49 2952286c 726f4320 4d542865
00:00:08.779998 Gst: 80000003/0000 37692029 3830312d 20483035 20555043
00:00:08.779998 Hst: 37692029 3830312d 20483035 20555043
00:00:08.779999 Gst: 80000004/0000 2e322040 48473037 0000007a 00000000
00:00:08.780000 Hst: 2e322040 48473037 0000007a 00000000
00:00:08.780000 Gst: 80000005/0000 00000000 00000000 00000000 00000000
00:00:08.780001 Hst: 00000000 00000000 00000000 00000000
00:00:08.780001 Gst: 80000006/0000 00000000 00000000 01006040 00000000
00:00:08.780002 Hst: 00000000 00000000 01006040 00000000
00:00:08.780003 Gst: 80000007/0000 00000000 00000000 00000000 00000100
00:00:08.780003 Hst: 00000000 00000000 00000000 00000100
00:00:08.780004 Gst: 80000008/0000 00003027 00000000 00000000 00000000
00:00:08.780004 Hst: 00003027 00000000 00000000 00000000
00:00:08.780005 Ext Name:
00:00:08.780005 Ext Supports: 0x80000000-0x80000008
00:00:08.780005 Family: 0 Extended: 0 Effective: 0
00:00:08.780006 Model: 0 Extended: 0 Effective: 0
00:00:08.780006 Stepping: 0
00:00:08.780006 Brand ID: 0x000
00:00:08.780007 Ext Features
00:00:08.780007 Mnemonic - Description = guest (host)
00:00:08.780007 FPU - x87 FPU on Chip = 0 (0)
00:00:08.780008 VME - Virtual 8086 Mode Enhancements = 0 (0)
00:00:08.780008 DE - Debugging extensions = 0 (0)
00:00:08.780009 PSE - Page Size Extension = 0 (0)
00:00:08.780009 TSC - Time Stamp Counter = 0 (0)
00:00:08.780010 MSR - K86 Model Specific Registers = 0 (0)
00:00:08.780010 PAE - Physical Address Extension = 0 (0)
00:00:08.780011 MCE - Machine Check Exception = 0 (0)
00:00:08.780011 CX8 - CMPXCHG8B instruction = 0 (0)
00:00:08.780012 APIC - APIC On-Chip = 0 (0)
00:00:08.780012 SEP - SYSCALL/SYSRET = 1 (1)
00:00:08.780013 MTRR - Memory Type Range Registers = 0 (0)
00:00:08.780013 PGE - PTE Global Bit = 0 (0)
00:00:08.780014 MCA - Machine Check Architecture = 0 (0)
00:00:08.780014 CMOV - Conditional Move instructions = 0 (0)
00:00:08.780015 PAT - Page Attribute Table = 0 (0)
00:00:08.780015 PSE-36 - 36-bit Page Size Extension = 0 (0)
00:00:08.780016 NX - No-Execute/Execute-Disable = 1 (1)
00:00:08.780016 AXMMX - AMD Extensions to MMX instructions = 0 (0)
00:00:08.780017 MMX - Intel MMX Technology = 0 (0)
00:00:08.780017 FXSR - FXSAVE and FXRSTOR Instructions = 0 (0)
00:00:08.780018 FFXSR - AMD fast FXSAVE and FXRSTOR instructions = 0 (0)
00:00:08.780018 Page1GB - 1 GB large page = 0 (1)
00:00:08.780019 RDTSCP - RDTSCP instruction = 1 (1)
00:00:08.780019 LM - AMD64 Long Mode = 1 (1)
00:00:08.780020 3DNOWEXT - AMD Extensions to 3DNow = 0 (0)
00:00:08.780020 3DNOW - AMD 3DNow = 0 (0)
00:00:08.780021 LahfSahf - LAHF/SAHF support in 64-bit mode = 1 (1)
00:00:08.780021 CmpLegacy - Core multi-processing legacy mode = 0 (0)
00:00:08.780022 SVM - AMD Secure Virtual Machine extensions = 0 (0)
00:00:08.780022 EXTAPIC - AMD Extended APIC registers = 0 (0)
00:00:08.780023 CR8L - AMD LOCK MOV CR0 means MOV CR8 = 0 (0)
00:00:08.780023 ABM - AMD Advanced Bit Manipulation = 0 (1)
00:00:08.780023 SSE4A - SSE4A instructions = 0 (0)
00:00:08.780024 MISALIGNSSE - AMD Misaligned SSE mode = 0 (0)
00:00:08.780024 3DNOWPRF - AMD PREFETCH and PREFETCHW instructions = 0 (1)
00:00:08.780025 OSVW - AMD OS Visible Workaround = 0 (0)
00:00:08.780025 IBS - Instruct Based Sampling = 0 (0)
00:00:08.780026 XOP - Extended Operation support = 0 (0)
00:00:08.780026 SKINIT - SKINIT, STGI, and DEV support = 0 (0)
00:00:08.780027 WDT - AMD Watchdog Timer support = 0 (0)
00:00:08.780027 LWP - Lightweight Profiling support = 0 (0)
00:00:08.780028 FMA4 - Four operand FMA instruction support = 0 (0)
00:00:08.780028 NodeId - NodeId in MSR C001_100C = 0 (0)
00:00:08.780029 TBM - Trailing Bit Manipulation instructions = 0 (0)
00:00:08.780029 TOPOEXT - Topology Extensions = 0 (0)
00:00:08.780029 PRFEXTCORE - Performance Counter Extensions support = 0 (0)
00:00:08.780030 PRFEXTNB - NB Performance Counter Extensions support = 0 (0)
00:00:08.780030 DATABPEXT - Data-access Breakpoint Extension = 0 (0)
00:00:08.780031 PERFTSC - Performance Time Stamp Counter = 0 (0)
00:00:08.780031 PCX_L2I - L2I/L3 Performance Counter Extensions = 0 (0)
00:00:08.780032 MWAITX - MWAITX and MONITORX instructions = 0 (0)
00:00:08.780032 Full Name: "Intel(R) Core(TM) i7-10850H CPU @ 2.70GHz"
00:00:08.780033 TLB 2/4M Instr/Uni: res0 0 entries
00:00:08.780033 TLB 2/4M Data: res0 0 entries
00:00:08.780034 TLB 4K Instr/Uni: res0 0 entries
00:00:08.780034 TLB 4K Data: res0 0 entries
00:00:08.780034 L1 Instr Cache Line Size: 0 bytes
00:00:08.780035 L1 Instr Cache Lines Per Tag: 0
00:00:08.780035 L1 Instr Cache Associativity: res0
00:00:08.780035 L1 Instr Cache Size: 0 KB
00:00:08.780035 L1 Data Cache Line Size: 0 bytes
00:00:08.780036 L1 Data Cache Lines Per Tag: 0
00:00:08.780036 L1 Data Cache Associativity: res0
00:00:08.780036 L1 Data Cache Size: 0 KB
00:00:08.780036 L2 TLB 2/4M Instr/Uni: off 0 entries
00:00:08.780037 L2 TLB 2/4M Data: off 0 entries
00:00:08.780037 L2 TLB 4K Instr/Uni: off 0 entries
00:00:08.780037 L2 TLB 4K Data: off 0 entries
00:00:08.780038 L2 Cache Line Size: 0 bytes
00:00:08.780038 L2 Cache Lines Per Tag: 0
00:00:08.780038 L2 Cache Associativity: off
00:00:08.780038 L2 Cache Size: 0 KB
00:00:08.780039 TS - Temperature Sensor = 0 (0)
00:00:08.780040 FID - Frequency ID control = 0 (0)
00:00:08.780040 VID - Voltage ID control = 0 (0)
00:00:08.780041 TscInvariant - Invariant Time Stamp Counter = 1 (1)
00:00:08.780041 CBP - Core Performance Boost = 0 (0)
00:00:08.780042 EffFreqRO - Read-only Effective Frequency Interface = 0 (0)
00:00:08.780042 ProcFdbkIf - Processor Feedback Interface = 0 (0)
00:00:08.780042 ProcPwrRep - Core power reporting interface support = 0 (0)
00:00:08.780044 Physical Address Width: 39 bits
00:00:08.780044 Virtual Address Width: 48 bits
00:00:08.780044 Guest Physical Address Width: 0 bits
00:00:08.780044 Physical Core Count: 1
00:00:08.780045
00:00:08.780045 ******************** End of CPUID dump **********************
00:00:08.780056 VMEmt: Halt method global1 (5)
00:00:08.780120 VMEmt: HaltedGlobal1 config: cNsSpinBlockThresholdCfg=50000
00:00:08.780131 Changing the VM state from 'CREATING' to 'CREATED'
00:00:08.781393 Changing the VM state from 'CREATED' to 'POWERING_ON'
00:00:08.781454 AIOMgr: Endpoints without assigned bandwidth groups:
00:00:08.781498 AIOMgr: C:\Users\cen1wa3\VirtualBox VMs\RHEL9\RHEL9.vmdk
00:00:08.781691 Changing the VM state from 'POWERING_ON' to 'RUNNING'
00:00:08.781721 Console: Machine state changed to 'Running'
00:00:08.784389 VMMDev: Guest Log: BIOS: VirtualBox 6.1.26
00:00:08.784667 PCI: Setting up resources and interrupts
00:00:08.793785 PIT: mode=2 count=0x10000 (65536) - 18.20 Hz (ch=0)
00:00:08.808108 Display::i_handleDisplayResize: uScreenId=0 pvVRAM=0000000000000000 w=720 h=400 bpp=0 cbLine=0x0 flags=0x0 origin=0,0
00:00:08.815925 VMMDev: Guest Log: CPUID EDX: 0x178bfbff
00:00:08.816109 PIIX3 ATA: Ctl#0: RESET, DevSel=0 AIOIf=0 CmdIf0=0x00 (-1 usec ago) CmdIf1=0x00 (-1 usec ago)
00:00:08.816196 PIIX3 ATA: Ctl#0: finished processing RESET
00:00:08.819453 PIIX3 ATA: Ctl#1: RESET, DevSel=0 AIOIf=0 CmdIf0=0x00 (-1 usec ago) CmdIf1=0x00 (-1 usec ago)
00:00:08.819518 PIIX3 ATA: Ctl#1: finished processing RESET
00:00:08.823712 AHCI#0: Reset the HBA
00:00:08.823724 VD#0: Cancelling all active requests
00:00:08.823998 AHCI#0: Port 0 reset
00:00:08.824099 VD#0: Cancelling all active requests
00:00:08.825274 VMMDev: Guest Log: BIOS: AHCI 0-P#0: PCHS=16383/16/63 LCHS=1024/255/63 0x0000000001000000 sectors
00:00:08.827427 PIT: mode=2 count=0x48d3 (18643) - 64.00 Hz (ch=0)
00:00:08.829324 Display::i_handleDisplayResize: uScreenId=0 pvVRAM=000000000f7a0000 w=640 h=480 bpp=32 cbLine=0xA00 flags=0x0 origin=0,0
00:00:09.282376 GUI: UIMachineViewNormal::resendSizeHint: Restoring guest size-hint for screen 0 to 800x600
00:00:09.285195 GUI: 2D video acceleration is disabled
00:00:09.285308 GUI: HID LEDs sync is enabled
00:00:09.299940 GUI: UIMachineLogicNormal::sltCheckForRequestedVisualStateType: Requested-state=0, Machine-state=5
00:00:11.300777 Display::i_handleDisplayResize: uScreenId=0 pvVRAM=000000000f7a0000 w=640 h=480 bpp=0 cbLine=0x280 flags=0x0 origin=0,0
00:00:11.314108 PIT: mode=2 count=0x10000 (65536) - 18.20 Hz (ch=0)
00:00:11.314773 VMMDev: Guest Log: BIOS: Boot : bseqnr=1, bootseq=0231
00:00:11.315212 VMMDev: Guest Log: BIOS: Boot from Floppy 0 failed
00:00:11.315735 VMMDev: Guest Log: BIOS: Boot : bseqnr=2, bootseq=0023
00:00:11.317268 VMMDev: Guest Log: BIOS: Booting from CD-ROM...
00:00:11.322293 Display::i_handleDisplayResize: uScreenId=0 pvVRAM=0000000000000000 w=720 h=400 bpp=0 cbLine=0x0 flags=0x0 origin=0,0
00:00:11.386929 Display::i_handleDisplayResize: uScreenId=0 pvVRAM=000000000f7a0000 w=640 h=480 bpp=24 cbLine=0x780 flags=0x0 origin=0,0
00:00:15.687145 Display::i_handleDisplayResize: uScreenId=0 pvVRAM=0000000000000000 w=720 h=400 bpp=0 cbLine=0x0 flags=0x0 origin=0,0
00:00:16.327373 VMMDev: Guest Log: BIOS: KBD: unsupported int 16h function 03
00:00:16.327850 VMMDev: Guest Log: BIOS: AX=0305 BX=0000 CX=0000 DX=0000
00:00:16.328988 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=81
00:00:16.329549 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=81
00:00:16.330148 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=82
00:00:16.330709 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=82
00:00:16.331306 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=83
00:00:16.331892 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=83
00:00:16.332491 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=84
00:00:16.333050 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=84
00:00:16.333647 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=85
00:00:16.334205 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=85
00:00:16.335059 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=86
00:00:16.335673 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=86
00:00:16.336294 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=87
00:00:16.336902 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=87
00:00:16.337576 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=88
00:00:16.338140 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=88
00:00:16.338807 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=89
00:00:16.339388 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=89
00:00:16.339984 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=8a
00:00:16.340547 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=8a
00:00:16.341143 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=8b
00:00:16.341699 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=8b
00:00:16.342324 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=8c
00:00:16.342882 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=8c
00:00:16.343482 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=8d
00:00:16.344040 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=8d
00:00:16.344636 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=8e
00:00:16.345196 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=8e
00:00:16.345790 VMMDev: Guest Log: int13_harddisk_ext: function 41, unmapped device for ELDL=8f
00:00:16.346349 VMMDev: Guest Log: int13_harddisk: function 02, unmapped device for ELDL=8f
00:00:16.711538 GIM: KVM: VCPU 0: Enabled system-time struct. at 0x0000000076601000 - u32TscScale=0xbcca3a63 i8TscShift=-1 uVersion=2 fFlags=0x1 uTsc=0x501cfa49d uVirtNanoTS=0x1d8a48788 TscKHz=2712008
00:00:16.711582 TM: Host/VM is not suitable for using TSC mode 'RealTscOffset', request to change TSC mode ignored
00:00:16.804782 GIM: KVM: Enabled wall-clock struct. at 0x0000000076600000 - u32Sec=1658918027 u32Nano=921722749 uVersion=2
00:00:16.842711 PIT: mode=2 count=0x4a9 (1193) - 1000.15 Hz (ch=0)
00:00:16.960360 PIT: mode=0 count=0x10000 (65536) - 18.20 Hz (ch=0)
00:00:17.240412 OHCI: Software reset
00:00:17.265639 EHCI: Hardware reset
00:00:17.266423 EHCI: USB Operational
00:00:17.279372 OHCI: USB Reset
00:00:17.301559 EHCI: USB Suspended
00:00:17.332413 OHCI: Software reset
00:00:17.332677 OHCI: USB Operational
00:00:17.348181 OHCI: USB SuspendedVBoxHardening.log:
e50.5660: Log file opened: 6.1.26r145957 g_hStartupLog=0000000000000084 g_uNtVerCombined=0xa04a6400
e50.5660: \SystemRoot\System32\ntdll.dll:
e50.5660: CreationTime: 2022-07-19T05:55:10.595200800Z
e50.5660: LastWriteTime: 2022-07-19T05:55:10.642078900Z
e50.5660: ChangeTime: 2022-07-20T16:55:05.063776300Z
e50.5660: FileAttributes: 0x20
e50.5660: Size: 0x1ef3a8
e50.5660: NT Headers: 0xe8
e50.5660: Timestamp: 0x1000a5b9
e50.5660: Machine: 0x8664 - amd64
e50.5660: Timestamp: 0x1000a5b9
e50.5660: Image Version: 10.0
e50.5660: SizeOfImage: 0x1f8000 (2064384)
e50.5660: Resource Dir: 0x186000 LB 0x700a0
e50.5660: [Version info resource found at 0xd8! (ID/Name: 0x1; SubID/SubName: 0x409)]
e50.5660: [Raw version resource data: 0x1860f0 LB 0x380, codepage 0x0 (reserved 0x0)]
e50.5660: ProductName: Microsoft® Windows® Operating System
e50.5660: ProductVersion: 10.0.19041.1806
e50.5660: FileVersion: 10.0.19041.1806 (WinBuild.160101.0800)
e50.5660: FileDescription: NT Layer DLL
e50.5660: \SystemRoot\System32\kernel32.dll:
e50.5660: CreationTime: 2022-07-19T05:55:18.143584700Z
e50.5660: LastWriteTime: 2022-07-19T05:55:18.163718600Z
e50.5660: ChangeTime: 2022-07-20T16:55:01.963495100Z
e50.5660: FileAttributes: 0x20
e50.5660: Size: 0xbb058
e50.5660: NT Headers: 0xe8
e50.5660: Timestamp: 0x4d6d72d1
e50.5660: Machine: 0x8664 - amd64
e50.5660: Timestamp: 0x4d6d72d1
e50.5660: Image Version: 10.0
e50.5660: SizeOfImage: 0xbd000 (774144)
e50.5660: Resource Dir: 0xbb000 LB 0x520
e50.5660: [Version info resource found at 0x90! (ID/Name: 0x1; SubID/SubName: 0x409)]
e50.5660: [Raw version resource data: 0xbb0b0 LB 0x3a4, codepage 0x0 (reserved 0x0)]
e50.5660: ProductName: Microsoft® Windows® Operating System
e50.5660: ProductVersion: 10.0.19041.1806
e50.5660: FileVersion: 10.0.19041.1806 (WinBuild.160101.0800)
e50.5660: FileDescription: Windows NT BASE API Client DLL
e50.5660: \SystemRoot\System32\KernelBase.dll:
e50.5660: CreationTime: 2022-07-19T05:55:11.298326500Z
e50.5660: LastWriteTime: 2022-07-19T05:55:11.360827800Z
e50.5660: ChangeTime: 2022-07-20T16:55:04.418453400Z
e50.5660: FileAttributes: 0x20
e50.5660: Size: 0x2d0058
e50.5660: NT Headers: 0x100
e50.5660: Timestamp: 0x299341e8
e50.5660: Machine: 0x8664 - amd64
e50.5660: Timestamp: 0x299341e8
e50.5660: Image Version: 10.0
e50.5660: SizeOfImage: 0x2ce000 (2940928)
e50.5660: Resource Dir: 0x2a5000 LB 0x548
e50.5660: [Version info resource found at 0x90! (ID/Name: 0x1; SubID/SubName: 0x409)]
e50.5660: [Raw version resource data: 0x2a50b0 LB 0x3bc, codepage 0x0 (reserved 0x0)]
e50.5660: ProductName: Microsoft® Windows® Operating System
e50.5660: ProductVersion: 10.0.19041.1826
e50.5660: FileVersion: 10.0.19041.1826 (WinBuild.160101.0800)
e50.5660: FileDescription: Windows NT BASE API Client DLL
e50.5660: \SystemRoot\System32\apisetschema.dll:
e50.5660: CreationTime: 2019-12-07T09:08:13.518339400Z
e50.5660: LastWriteTime: 2019-12-07T09:08:13.518339400Z
e50.5660: ChangeTime: 2022-07-19T05:56:25.514604000Z
e50.5660: FileAttributes: 0x20
e50.5660: Size: 0x1f538
e50.5660: NT Headers: 0xd0
e50.5660: Timestamp: 0x31288ce0
e50.5660: Machine: 0x8664 - amd64
e50.5660: Timestamp: 0x31288ce0
e50.5660: Image Version: 10.0
e50.5660: SizeOfImage: 0x20000 (131072)
e50.5660: Resource Dir: 0x1f000 LB 0x408
e50.5660: [Version info resource found at 0x48! (ID/Name: 0x1; SubID/SubName: 0x409)]
e50.5660: [Raw version resource data: 0x1f060 LB 0x3a8, codepage 0x0 (reserved 0x0)]
e50.5660: ProductName: Microsoft® Windows® Operating System
e50.5660: ProductVersion: 10.0.19041.1
e50.5660: FileVersion: 10.0.19041.1 (WinBuild.160101.0800)
e50.5660: FileDescription: ApiSet Schema DLL
e50.5660: NtOpenDirectoryObject failed on \Driver: 0xc0000022
e50.5660: supR3HardenedWinFindAdversaries: 0x3
e50.5660: \SystemRoot\System32\drivers\SysPlant.sys:
e50.5660: CreationTime: 2021-07-20T13:41:23.315594100Z
e50.5660: LastWriteTime: 2021-12-06T12:33:04.399232700Z
e50.5660: ChangeTime: 2021-12-06T12:33:04.399232700Z
e50.5660: FileAttributes: 0x20
e50.5660: Size: 0x407f8
e50.5660: NT Headers: 0xe0
e50.5660: Timestamp: 0x607155cb
e50.5660: Machine: 0x8664 - amd64
e50.5660: Timestamp: 0x607155cb
e50.5660: Image Version: 5.0
e50.5660: SizeOfImage: 0x41000 (266240)
e50.5660: Resource Dir: 0x3f000 LB 0x3a8
e50.5660: [Version info resource found at 0x48! (ID/Name: 0x1; SubID/SubName: 0x409)]
e50.5660: [Raw version resource data: 0x3f060 LB 0x348, codepage 0x0 (reserved 0x0)]
e50.5660: ProductName: Symantec CMC Firewall
e50.5660: ProductVersion: 14.3.4540.2000
e50.5660: FileVersion: 14.3.4540.2000
e50.5660: FileDescription: Symantec CMC Firewall SysPlant
e50.5660: \SystemRoot\System32\drivers\symevent64x86.sys:
e50.5660: CreationTime: 2021-07-20T13:41:35.690592800Z
e50.5660: LastWriteTime: 2022-04-25T09:08:20.525420600Z
e50.5660: ChangeTime: 2022-04-26T05:55:25.934395000Z
e50.5660: FileAttributes: 0x20
e50.5660: Size: 0x187f8
e50.5660: NT Headers: 0xd8
e50.5660: Timestamp: 0x61786ab8
e50.5660: Machine: 0x8664 - amd64
e50.5660: Timestamp: 0x61786ab8
e50.5660: Image Version: 10.0
e50.5660: SizeOfImage: 0x24000 (147456)
e50.5660: Resource Dir: 0x22000 LB 0x3cc
e50.5660: [Version info resource found at 0x90! (ID/Name: 0x1; SubID/SubName: 0x409)]
e50.5660: [Raw version resource data: 0x220b8 LB 0x314, codepage 0x4e4 (reserved 0x0)]
e50.5660: ProductName: SYMEVENT
e50.5660: ProductVersion: 14.0.8.101
e50.5660: FileVersion: 14.0.8.101
e50.5660: FileDescription: Symantec Event Library
e50.5660: supR3HardenedWinInitAppBin(0x0): '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox'
e50.5660: Calling main()
e50.5660: SUPR3HardenedMain: pszProgName=VirtualBoxVM fFlags=0x2
e50.5660: supR3HardenedWinInitAppBin(0x2): '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox'
e50.5660: SUPR3HardenedMain: Respawn #1
e50.5660: System32: \Device\HarddiskVolume3\Windows\System32
e50.5660: WinSxS: \Device\HarddiskVolume3\Windows\WinSxS
e50.5660: KnownDllPath: C:\WINDOWS\System32
e50.5660: supR3HardenedWinInit: Performing a limited self purification...
e50.5660: supHardNtVpScanVirtualMemory: enmKind=SELF_PURIFICATION
e50.5660: *0000000000000000-0000000000c7ffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000c80000-0000000000c80fff 0x0002/0x0002 0x0040000
e50.5660: 0000000000c81000-0000000000c8ffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000c90000-0000000000c90fff 0x0002/0x0002 0x0040000
e50.5660: 0000000000c91000-0000000000c9ffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000ca0000-0000000000cbcfff 0x0002/0x0002 0x0040000
e50.5660: 0000000000cbd000-0000000000cbffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000cc0000-0000000000d70fff 0x0000/0x0004 0x0020000
e50.5660: 0000000000d71000-0000000000d73fff 0x0104/0x0004 0x0020000
e50.5660: 0000000000d74000-0000000000dbffff 0x0004/0x0004 0x0020000
e50.5660: *0000000000dc0000-0000000000dc3fff 0x0002/0x0002 0x0040000
e50.5660: 0000000000dc4000-0000000000dcffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000dd0000-0000000000dd1fff 0x0004/0x0004 0x0020000
e50.5660: 0000000000dd2000-0000000000ddffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000de0000-0000000000deffff 0x0004/0x0004 0x0040000
e50.5660: 0000000000df0000-0000000000dfffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000e00000-0000000000fbefff 0x0000/0x0004 0x0020000
e50.5660: 0000000000fbf000-0000000000fc1fff 0x0004/0x0004 0x0020000
e50.5660: 0000000000fc2000-0000000000ffffff 0x0000/0x0004 0x0020000
e50.5660: *0000000001000000-00000000010c8fff 0x0002/0x0002 0x0040000
e50.5660: 00000000010c9000-00000000010cffff 0x0001/0x0000 0x0000000
e50.5660: *00000000010d0000-00000000010d1fff 0x0004/0x0004 0x0020000
e50.5660: 00000000010d2000-0000000001131fff 0x0000/0x0004 0x0020000
e50.5660: 0000000001132000-00000000011effff 0x0001/0x0000 0x0000000
e50.5660: *00000000011f0000-00000000011f5fff 0x0004/0x0004 0x0020000
e50.5660: 00000000011f6000-00000000012effff 0x0000/0x0004 0x0020000
e50.5660: *00000000012f0000-0000000001314fff 0x0004/0x0004 0x0020000
e50.5660: 0000000001315000-00000000013effff 0x0000/0x0004 0x0020000
e50.5660: 00000000013f0000-00000000014cffff 0x0001/0x0000 0x0000000
e50.5660: *00000000014d0000-00000000014defff 0x0004/0x0004 0x0020000
e50.5660: 00000000014df000-00000000014dffff 0x0000/0x0004 0x0020000
e50.5660: *00000000014e0000-00000000014e5fff 0x0000/0x0004 0x0020000
e50.5660: 00000000014e6000-00000000016defff 0x0004/0x0004 0x0020000
e50.5660: 00000000016df000-00000000016dffff 0x0000/0x0004 0x0020000
e50.5660: 00000000016e0000-000000007ffdffff 0x0001/0x0000 0x0000000
e50.5660: *000000007ffe0000-000000007ffe0fff 0x0002/0x0002 0x0020000
e50.5660: 000000007ffe1000-000000007ffeafff 0x0001/0x0000 0x0000000
e50.5660: *000000007ffeb000-000000007ffebfff 0x0002/0x0002 0x0020000
e50.5660: 000000007ffec000-00007ff4029affff 0x0001/0x0000 0x0000000
e50.5660: *00007ff4029b0000-00007ff4029b4fff 0x0002/0x0002 0x0040000
e50.5660: 00007ff4029b5000-00007ff402aaffff 0x0000/0x0002 0x0040000
e50.5660: *00007ff402ab0000-00007ff502acffff 0x0000/0x0004 0x0020000
e50.5660: *00007ff502ad0000-00007ff504acffff 0x0000/0x0004 0x0020000
e50.5660: 00007ff504ad0000-00007ff504ad0fff 0x0004/0x0004 0x0020000
e50.5660: 00007ff504ad1000-00007ff504adffff 0x0001/0x0000 0x0000000
e50.5660: *00007ff504ae0000-00007ff504ae0fff 0x0002/0x0002 0x0040000
e50.5660: 00007ff504ae1000-00007ff504aeffff 0x0001/0x0000 0x0000000
e50.5660: *00007ff504af0000-00007ff504b12fff 0x0002/0x0002 0x0040000
e50.5660: 00007ff504b13000-00007ff77f4effff 0x0001/0x0000 0x0000000
e50.5660: *00007ff77f4f0000-00007ff77f4f0fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f4f1000-00007ff77f567fff 0x0020/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f568000-00007ff77f568fff 0x0080/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f569000-00007ff77f5b1fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5b2000-00007ff77f5b4fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5b5000-00007ff77f5b7fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5b8000-00007ff77f5bafff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5bb000-00007ff77f5bbfff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5bc000-00007ff77f5bdfff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5be000-00007ff77f5befff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5bf000-00007ff77f607fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f608000-00007ffe6a27ffff 0x0001/0x0000 0x0000000
e50.5660: *00007ffe6a280000-00007ffe6a280fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\KernelBase.dll
e50.5660: 00007ffe6a281000-00007ffe6a395fff 0x0020/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\KernelBase.dll
e50.5660: 00007ffe6a396000-00007ffe6a50ffff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\KernelBase.dll
e50.5660: 00007ffe6a510000-00007ffe6a513fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\KernelBase.dll
e50.5660: 00007ffe6a514000-00007ffe6a514fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\KernelBase.dll
e50.5660: 00007ffe6a515000-00007ffe6a54dfff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\KernelBase.dll
e50.5660: 00007ffe6a54e000-00007ffe6c8affff 0x0001/0x0000 0x0000000
e50.5660: *00007ffe6c8b0000-00007ffe6c8b0fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\kernel32.dll
e50.5660: 00007ffe6c8b1000-00007ffe6c92efff 0x0020/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\kernel32.dll
e50.5660: 00007ffe6c92f000-00007ffe6c961fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\kernel32.dll
e50.5660: 00007ffe6c962000-00007ffe6c962fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\kernel32.dll
e50.5660: 00007ffe6c963000-00007ffe6c963fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\kernel32.dll
e50.5660: 00007ffe6c964000-00007ffe6c96cfff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\kernel32.dll
e50.5660: 00007ffe6c96d000-00007ffe6cb0ffff 0x0001/0x0000 0x0000000
e50.5660: *00007ffe6cb10000-00007ffe6cb10fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cb11000-00007ffe6cc2cfff 0x0020/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc2d000-00007ffe6cc75fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc76000-00007ffe6cc76fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc77000-00007ffe6cc78fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc79000-00007ffe6cc81fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc82000-00007ffe6cd07fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cd08000-00007ffffffeffff 0x0001/0x0000 0x0000000
e50.5660: kernel32.dll: timestamp 0x4d6d72d1 (rc=VINF_SUCCESS)
e50.5660: kernelbase.dll: timestamp 0x299341e8 (rc=VINF_SUCCESS)
e50.5660: VirtualBoxVM.exe: timestamp 0x61018314 (rc=VINF_SUCCESS)
e50.5660: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe: Signature #1/2: info status: 24202
e50.5660: '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe' has no imports
e50.5660: '\Device\HarddiskVolume3\Windows\System32\ntdll.dll' has no imports
e50.5660: supR3HardenedWinInit: SUPHARDNTVPKIND_SELF_PURIFICATION_LIMITED -> VINF_SUCCESS, cFixes=0
e50.5660: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe: Signature #1/2: info status: 24202
e50.5660: '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe' has no imports
e50.5660: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe)
e50.5660: supR3HardNtEnableThreadCreationEx:
e50.5660: supR3HardNtDisableThreadCreation: pvLdrInitThunk=00007ffe6cb84b00 pvNtTerminateThread=00007ffe6cbad990
e50.5660: supR3HardenedWinDoReSpawn(1): New child 1588.4300 [kernel32].
e50.5660: supR3HardNtChildGatherData: PebBaseAddress=00000000010c9000 cbPeb=0x388
e50.5660: supR3HardNtPuChFindNtdll: uNtDllParentAddr=00007ffe6cb10000 uNtDllChildAddr=00007ffe6cb10000
e50.5660: supR3HardenedWinSetupChildInit: uLdrInitThunk=00007ffe6cb84b00
e50.5660: supR3HardenedWinSetupChildInit: Initial context:
rax=0000000000000000 rbx=0000000000000000 rcx=00007ff77f4f7900 rdx=00000000010c9000
rsi=0000000000000000 rdi=0000000000000000 r8 =0000000000000000 r9 =0000000000000000
r10=0000000000000000 r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000 P1=0000000000000000 P2=0000000000000000
rip=00007ffe6cb62630 rsp=0000000000f9f978 rbp=0000000000000000 ctxflags=0010001b
cs=0033 ss=002b ds=0000 es=0000 fs=0000 gs=0000 eflags=00000200 mxcrx=00001f80
P3=0000000000000000 P4=0000000000000000 P5=0000000000000000 P6=0000000000000000
dr0=0000000000000000 dr1=0000000000000000 dr2=0000000000000000 dr3=0000000000000000
dr6=0000000000000000 dr7=0000000000000000 vcr=0000000000000000 dcr=0000000000000000
lbt=0000000000000000 lbf=0000000000000000 lxt=0000000000000000 lxf=0000000000000000
e50.5660: supR3HardenedWinSetupChildInit: Start child.
e50.5660: supR3HardNtChildWaitFor: Found expected request 0 (PurifyChildAndCloseHandles) after 2 ms.
e50.5660: supR3HardNtChildPurify: Startup delay kludge #1/0: 526 ms, 33 sleeps
e50.5660: supHardNtVpScanVirtualMemory: enmKind=CHILD_PURIFICATION
e50.5660: *0000000000000000-0000000000e5ffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000e60000-0000000000e7ffff 0x0004/0x0004 0x0020000
e50.5660: *0000000000e80000-0000000000e9cfff 0x0002/0x0002 0x0040000
e50.5660: 0000000000e9d000-0000000000e9ffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000ea0000-0000000000f9afff 0x0000/0x0004 0x0020000
e50.5660: 0000000000f9b000-0000000000f9dfff 0x0104/0x0004 0x0020000
e50.5660: 0000000000f9e000-0000000000f9ffff 0x0004/0x0004 0x0020000
e50.5660: *0000000000fa0000-0000000000fa3fff 0x0002/0x0002 0x0040000
e50.5660: 0000000000fa4000-0000000000faffff 0x0001/0x0000 0x0000000
e50.5660: *0000000000fb0000-0000000000fb1fff 0x0004/0x0004 0x0020000
e50.5660: 0000000000fb2000-0000000000ffffff 0x0001/0x0000 0x0000000
e50.5660: *0000000001000000-00000000010c8fff 0x0000/0x0004 0x0020000
e50.5660: 00000000010c9000-00000000010cbfff 0x0004/0x0004 0x0020000
e50.5660: 00000000010cc000-00000000011fffff 0x0000/0x0004 0x0020000
e50.5660: 0000000001200000-000000007ffdffff 0x0001/0x0000 0x0000000
e50.5660: *000000007ffe0000-000000007ffe0fff 0x0002/0x0002 0x0020000
e50.5660: 000000007ffe1000-000000007ffeafff 0x0001/0x0000 0x0000000
e50.5660: *000000007ffeb000-000000007ffebfff 0x0002/0x0002 0x0020000
e50.5660: 000000007ffec000-00007ff57172ffff 0x0001/0x0000 0x0000000
e50.5660: *00007ff571730000-00007ff571730fff 0x0002/0x0002 0x0040000
e50.5660: 00007ff571731000-00007ff57173ffff 0x0001/0x0000 0x0000000
e50.5660: *00007ff571740000-00007ff571762fff 0x0002/0x0002 0x0040000
e50.5660: 00007ff571763000-00007ff77f4effff 0x0001/0x0000 0x0000000
e50.5660: *00007ff77f4f0000-00007ff77f4f0fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f4f1000-00007ff77f567fff 0x0020/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f568000-00007ff77f568fff 0x0080/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f569000-00007ff77f5b1fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5b2000-00007ff77f5b2fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5b3000-00007ff77f5b3fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5b4000-00007ff77f5b8fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5b9000-00007ff77f5b9fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5ba000-00007ff77f5bafff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5bb000-00007ff77f5befff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f5bf000-00007ff77f607fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
e50.5660: 00007ff77f608000-00007ffe6cb0ffff 0x0001/0x0000 0x0000000
e50.5660: *00007ffe6cb10000-00007ffe6cb10fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cb11000-00007ffe6cc2cfff 0x0020/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc2d000-00007ffe6cc75fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc76000-00007ffe6cc81fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc82000-00007ffe6cc90fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc91000-00007ffe6cc91fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc92000-00007ffe6cc94fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cc95000-00007ffe6cd07fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
e50.5660: 00007ffe6cd08000-00007ffffffeffff 0x0001/0x0000 0x0000000
e50.5660: supR3HardNtChildPurify: Done after 528 ms and 0 fixes (loop #0).
e50.5660: supR3HardNtEnableThreadCreationEx:
1588.4300: Log file opened: 6.1.26r145957 g_hStartupLog=0000000000000004 g_uNtVerCombined=0xa04a6400
1588.4300: supR3HardenedVmProcessInit: uNtDllAddr=00007ffe6cb10000 g_uNtVerCombined=0xa04a6400 (stack ~0000000000f9f408)
1588.4300: ntdll.dll: timestamp 0x1000a5b9 (rc=VINF_SUCCESS)
1588.4300: New simple heap: #1 0000000001300000 LB 0x400000 (for 2064384 allocation)
1588.4300: supR3HardenedWinInitAppBin(0x0): '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox'
1588.4300: System32: \Device\HarddiskVolume3\Windows\System32
1588.4300: WinSxS: \Device\HarddiskVolume3\Windows\WinSxS
1588.4300: KnownDllPath: C:\WINDOWS\System32
1588.4300: supR3HardenedVmProcessInit: Opening vboxdrv stub...
1588.4300: supR3HardenedVmProcessInit: Restoring LdrInitializeThunk...
1588.4300: supR3HardenedVmProcessInit: Returning to LdrInitializeThunk...
1588.4300: Registered Dll notification callback with NTDLL.
1588.4300: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\kernel32.dll)
1588.4300: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\kernel32.dll
1588.4300: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\KERNEL32.DLL (Input=KERNEL32.DLL, rcNtResolve=0xc0150008) *pfFlags=0xffffffff pwszSearchPath=0000000000004001:<flags> [calling]
1588.4300: supR3HardenedDllNotificationCallback: load 00007ffe6a280000 LB 0x002ce000 C:\WINDOWS\System32\KERNELBASE.dll [fFlags=0x0]
1588.4300: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\KernelBase.dll)
1588.4300: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\KernelBase.dll
1588.4300: supR3HardenedDllNotificationCallback: load 00007ffe6c8b0000 LB 0x000bd000 C:\WINDOWS\System32\KERNEL32.DLL [fFlags=0x0]
1588.4300: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\kernel32.dll [lacks WinVerifyTrust]
1588.4300: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6c8b0000 'C:\WINDOWS\System32\KERNEL32.DLL'
1588.4300: supR3HardenedDllNotificationCallback: load 00007ff77f4f0000 LB 0x00118000 C:\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe [fFlags=0x0]
1588.4300: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe: Signature #1/2: info status: 24202
1588.4300: '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe' has no imports
1588.4300: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe)
1588.4300: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: supR3HardNtDisableThreadCreation: pvLdrInitThunk=00007ffe6cb84b00 pvNtTerminateThread=00007ffe6cbad990
e50.5660: supR3HardNtChildWaitFor: Found expected request 1 (CloseEvents) after 81 ms.
1588.4300: \SystemRoot\System32\ntdll.dll:
1588.4300: CreationTime: 2022-07-19T05:55:10.595200800Z
1588.4300: LastWriteTime: 2022-07-19T05:55:10.642078900Z
1588.4300: ChangeTime: 2022-07-20T16:55:05.063776300Z
1588.4300: FileAttributes: 0x20
1588.4300: Size: 0x1ef3a8
1588.4300: NT Headers: 0xe8
1588.4300: Timestamp: 0x1000a5b9
1588.4300: Machine: 0x8664 - amd64
1588.4300: Timestamp: 0x1000a5b9
1588.4300: Image Version: 10.0
1588.4300: SizeOfImage: 0x1f8000 (2064384)
1588.4300: Resource Dir: 0x186000 LB 0x700a0
1588.4300: [Version info resource found at 0xd8! (ID/Name: 0x1; SubID/SubName: 0x409)]
1588.4300: [Raw version resource data: 0x1860f0 LB 0x380, codepage 0x0 (reserved 0x0)]
1588.4300: ProductName: Microsoft® Windows® Operating System
1588.4300: ProductVersion: 10.0.19041.1806
1588.4300: FileVersion: 10.0.19041.1806 (WinBuild.160101.0800)
1588.4300: FileDescription: NT Layer DLL
1588.4300: \SystemRoot\System32\kernel32.dll:
1588.4300: CreationTime: 2022-07-19T05:55:18.143584700Z
1588.4300: LastWriteTime: 2022-07-19T05:55:18.163718600Z
1588.4300: ChangeTime: 2022-07-20T16:55:01.963495100Z
1588.4300: FileAttributes: 0x20
1588.4300: Size: 0xbb058
1588.4300: NT Headers: 0xe8
1588.4300: Timestamp: 0x4d6d72d1
1588.4300: Machine: 0x8664 - amd64
1588.4300: Timestamp: 0x4d6d72d1
1588.4300: Image Version: 10.0
1588.4300: SizeOfImage: 0xbd000 (774144)
1588.4300: Resource Dir: 0xbb000 LB 0x520
1588.4300: [Version info resource found at 0x90! (ID/Name: 0x1; SubID/SubName: 0x409)]
1588.4300: [Raw version resource data: 0xbb0b0 LB 0x3a4, codepage 0x0 (reserved 0x0)]
1588.4300: ProductName: Microsoft® Windows® Operating System
1588.4300: ProductVersion: 10.0.19041.1806
1588.4300: FileVersion: 10.0.19041.1806 (WinBuild.160101.0800)
1588.4300: FileDescription: Windows NT BASE API Client DLL
1588.4300: \SystemRoot\System32\KernelBase.dll:
1588.4300: CreationTime: 2022-07-19T05:55:11.298326500Z
1588.4300: LastWriteTime: 2022-07-19T05:55:11.360827800Z
1588.4300: ChangeTime: 2022-07-20T16:55:04.418453400Z
1588.4300: FileAttributes: 0x20
1588.4300: Size: 0x2d0058
1588.4300: NT Headers: 0x100
1588.4300: Timestamp: 0x299341e8
1588.4300: Machine: 0x8664 - amd64
1588.4300: Timestamp: 0x299341e8
1588.4300: Image Version: 10.0
1588.4300: SizeOfImage: 0x2ce000 (2940928)
1588.4300: Resource Dir: 0x2a5000 LB 0x548
1588.4300: [Version info resource found at 0x90! (ID/Name: 0x1; SubID/SubName: 0x409)]
1588.4300: [Raw version resource data: 0x2a50b0 LB 0x3bc, codepage 0x0 (reserved 0x0)]
1588.4300: ProductName: Microsoft® Windows® Operating System
1588.4300: ProductVersion: 10.0.19041.1826
1588.4300: FileVersion: 10.0.19041.1826 (WinBuild.160101.0800)
1588.4300: FileDescription: Windows NT BASE API Client DLL
1588.4300: \SystemRoot\System32\apisetschema.dll:
1588.4300: CreationTime: 2019-12-07T09:08:13.518339400Z
1588.4300: LastWriteTime: 2019-12-07T09:08:13.518339400Z
1588.4300: ChangeTime: 2022-07-19T05:56:25.514604000Z
1588.4300: FileAttributes: 0x20
1588.4300: Size: 0x1f538
1588.4300: NT Headers: 0xd0
1588.4300: Timestamp: 0x31288ce0
1588.4300: Machine: 0x8664 - amd64
1588.4300: Timestamp: 0x31288ce0
1588.4300: Image Version: 10.0
1588.4300: SizeOfImage: 0x20000 (131072)
1588.4300: Resource Dir: 0x1f000 LB 0x408
1588.4300: [Version info resource found at 0x48! (ID/Name: 0x1; SubID/SubName: 0x409)]
1588.4300: [Raw version resource data: 0x1f060 LB 0x3a8, codepage 0x0 (reserved 0x0)]
1588.4300: ProductName: Microsoft® Windows® Operating System
1588.4300: ProductVersion: 10.0.19041.1
1588.4300: FileVersion: 10.0.19041.1 (WinBuild.160101.0800)
1588.4300: FileDescription: ApiSet Schema DLL
1588.4300: NtOpenDirectoryObject failed on \Driver: 0xc0000022
1588.4300: supR3HardenedWinFindAdversaries: 0x3
1588.4300: \SystemRoot\System32\drivers\SysPlant.sys:
1588.4300: CreationTime: 2021-07-20T13:41:23.315594100Z
1588.4300: LastWriteTime: 2021-12-06T12:33:04.399232700Z
1588.4300: ChangeTime: 2021-12-06T12:33:04.399232700Z
1588.4300: FileAttributes: 0x20
1588.4300: Size: 0x407f8
1588.4300: NT Headers: 0xe0
1588.4300: Timestamp: 0x607155cb
1588.4300: Machine: 0x8664 - amd64
1588.4300: Timestamp: 0x607155cb
1588.4300: Image Version: 5.0
1588.4300: SizeOfImage: 0x41000 (266240)
1588.4300: Resource Dir: 0x3f000 LB 0x3a8
1588.4300: [Version info resource found at 0x48! (ID/Name: 0x1; SubID/SubName: 0x409)]
1588.4300: [Raw version resource data: 0x3f060 LB 0x348, codepage 0x0 (reserved 0x0)]
1588.4300: ProductName: Symantec CMC Firewall
1588.4300: ProductVersion: 14.3.4540.2000
1588.4300: FileVersion: 14.3.4540.2000
1588.4300: FileDescription: Symantec CMC Firewall SysPlant
1588.4300: \SystemRoot\System32\drivers\symevent64x86.sys:
1588.4300: CreationTime: 2021-07-20T13:41:35.690592800Z
1588.4300: LastWriteTime: 2022-04-25T09:08:20.525420600Z
1588.4300: ChangeTime: 2022-04-26T05:55:25.934395000Z
1588.4300: FileAttributes: 0x20
1588.4300: Size: 0x187f8
1588.4300: NT Headers: 0xd8
1588.4300: Timestamp: 0x61786ab8
1588.4300: Machine: 0x8664 - amd64
1588.4300: Timestamp: 0x61786ab8
1588.4300: Image Version: 10.0
1588.4300: SizeOfImage: 0x24000 (147456)
1588.4300: Resource Dir: 0x22000 LB 0x3cc
1588.4300: [Version info resource found at 0x90! (ID/Name: 0x1; SubID/SubName: 0x409)]
1588.4300: [Raw version resource data: 0x220b8 LB 0x314, codepage 0x4e4 (reserved 0x0)]
1588.4300: ProductName: SYMEVENT
1588.4300: ProductVersion: 14.0.8.101
1588.4300: FileVersion: 14.0.8.101
1588.4300: FileDescription: Symantec Event Library
1588.4300: supR3HardenedWinInitAppBin(0x0): '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox'
1588.4300: Calling main()
1588.4300: SUPR3HardenedMain: pszProgName=VirtualBoxVM fFlags=0x2
1588.4300: supR3HardenedWinInitAppBin(0x2): '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox'
1588.4300: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe: Signature #1/2: info status: 24202
1588.4300: '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe' has no imports
1588.4300: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe)
1588.4300: SUPR3HardenedMain: Respawn #2
1588.4300: supR3HardNtEnableThreadCreationEx:
1588.4300: supR3HardenedDllNotificationCallback: load 00007ffe6b450000 LB 0x00125000 C:\WINDOWS\System32\RPCRT4.dll [fFlags=0x0]
1588.4300: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll)
1588.4300: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll
1588.4300: supR3HardenedDllNotificationCallback: load 00007ffe6c590000 LB 0x0009c000 C:\WINDOWS\System32\sechost.dll [fFlags=0x0]
1588.4300: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #11 'rpcrt4.dll'.
1588.4300: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\sechost.dll)
1588.4300: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\sechost.dll
1588.4300: '\Device\HarddiskVolume3\Windows\System32\ntdll.dll' has no imports
1588.4300: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\ntdll.dll)
1588.4300: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\ntdll.dll
1588.4300: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
1588.4300: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
1588.4300: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll [lacks WinVerifyTrust]
1588.4300: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\ntdll.dll (Input=ntdll.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
1588.4300: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6cb10000 'C:\WINDOWS\System32\ntdll.dll'
1588.4300: supR3HardNtDisableThreadCreation: pvLdrInitThunk=00007ffe6cb84b00 pvNtTerminateThread=00007ffe6cbad990
1588.4300: supR3HardenedWinDoReSpawn(2): New child 2a58.348c [kernel32].
1588.4300: supR3HardNtChildGatherData: PebBaseAddress=00000000004a0000 cbPeb=0x388
1588.4300: supR3HardNtPuChFindNtdll: uNtDllParentAddr=00007ffe6cb10000 uNtDllChildAddr=00007ffe6cb10000
1588.4300: supR3HardenedWinSetupChildInit: uLdrInitThunk=00007ffe6cb84b00
1588.4300: supR3HardenedWinSetupChildInit: Initial context:
rax=0000000000000000 rbx=0000000000000000 rcx=00007ff77f4f7900 rdx=00000000004a0000
rsi=0000000000000000 rdi=0000000000000000 r8 =0000000000000000 r9 =0000000000000000
r10=0000000000000000 r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000 P1=0000000000000000 P2=0000000000000000
rip=00007ffe6cb62630 rsp=000000000073f918 rbp=0000000000000000 ctxflags=0010001b
cs=0033 ss=002b ds=0000 es=0000 fs=0000 gs=0000 eflags=00000200 mxcrx=00001f80
P3=0000000000000000 P4=0000000000000000 P5=0000000000000000 P6=0000000000000000
dr0=0000000000000000 dr1=0000000000000000 dr2=0000000000000000 dr3=0000000000000000
dr6=0000000000000000 dr7=0000000000000000 vcr=0000000000000000 dcr=0000000000000000
lbt=0000000000000000 lbf=0000000000000000 lxt=0000000000000000 lxf=0000000000000000
1588.4300: kernel32.dll: timestamp 0x4d6d72d1 (rc=VINF_SUCCESS)
1588.4300: supR3HardenedWinSetupChildInit: Start child.
1588.4300: supR3HardNtChildWaitFor: Found expected request 0 (PurifyChildAndCloseHandles) after 1 ms.
1588.4300: supR3HardNtChildPurify: Startup delay kludge #1/0: 517 ms, 33 sleeps
1588.4300: supHardNtVpScanVirtualMemory: enmKind=CHILD_PURIFICATION
1588.4300: *0000000000000000-00000000003fffff 0x0001/0x0000 0x0000000
1588.4300: *0000000000400000-000000000049ffff 0x0000/0x0004 0x0020000
1588.4300: 00000000004a0000-00000000004a2fff 0x0004/0x0004 0x0020000
1588.4300: 00000000004a3000-00000000005fffff 0x0000/0x0004 0x0020000
1588.4300: *0000000000600000-000000000061ffff 0x0004/0x0004 0x0020000
1588.4300: *0000000000620000-000000000063cfff 0x0002/0x0002 0x0040000
1588.4300: 000000000063d000-000000000063ffff 0x0001/0x0000 0x0000000
1588.4300: *0000000000640000-000000000073afff 0x0000/0x0004 0x0020000
1588.4300: 000000000073b000-000000000073dfff 0x0104/0x0004 0x0020000
1588.4300: 000000000073e000-000000000073ffff 0x0004/0x0004 0x0020000
1588.4300: *0000000000740000-0000000000743fff 0x0002/0x0002 0x0040000
1588.4300: 0000000000744000-000000000074ffff 0x0001/0x0000 0x0000000
1588.4300: *0000000000750000-0000000000751fff 0x0004/0x0004 0x0020000
1588.4300: 0000000000752000-000000007ffdffff 0x0001/0x0000 0x0000000
1588.4300: *000000007ffe0000-000000007ffe0fff 0x0002/0x0002 0x0020000
1588.4300: 000000007ffe1000-000000007ffeafff 0x0001/0x0000 0x0000000
1588.4300: *000000007ffeb000-000000007ffebfff 0x0002/0x0002 0x0020000
1588.4300: 000000007ffec000-00007ff5a5f8ffff 0x0001/0x0000 0x0000000
1588.4300: *00007ff5a5f90000-00007ff5a5f90fff 0x0002/0x0002 0x0040000
1588.4300: 00007ff5a5f91000-00007ff5a5f9ffff 0x0001/0x0000 0x0000000
1588.4300: *00007ff5a5fa0000-00007ff5a5fc2fff 0x0002/0x0002 0x0040000
1588.4300: 00007ff5a5fc3000-00007ff77f4effff 0x0001/0x0000 0x0000000
1588.4300: *00007ff77f4f0000-00007ff77f4f0fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f4f1000-00007ff77f567fff 0x0020/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f568000-00007ff77f568fff 0x0080/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f569000-00007ff77f5b1fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f5b2000-00007ff77f5b2fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f5b3000-00007ff77f5b3fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f5b4000-00007ff77f5b8fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f5b9000-00007ff77f5b9fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f5ba000-00007ff77f5bafff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f5bb000-00007ff77f5befff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f5bf000-00007ff77f607fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
1588.4300: 00007ff77f608000-00007ffe6cb0ffff 0x0001/0x0000 0x0000000
1588.4300: *00007ffe6cb10000-00007ffe6cb10fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
1588.4300: 00007ffe6cb11000-00007ffe6cc2cfff 0x0020/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
1588.4300: 00007ffe6cc2d000-00007ffe6cc75fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
1588.4300: 00007ffe6cc76000-00007ffe6cc81fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
1588.4300: 00007ffe6cc82000-00007ffe6cc90fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
1588.4300: 00007ffe6cc91000-00007ffe6cc91fff 0x0004/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
1588.4300: 00007ffe6cc92000-00007ffe6cc94fff 0x0008/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
1588.4300: 00007ffe6cc95000-00007ffe6cd07fff 0x0002/0x0080 0x1000000 \Device\HarddiskVolume3\Windows\System32\ntdll.dll
1588.4300: 00007ffe6cd08000-00007ffffffeffff 0x0001/0x0000 0x0000000
1588.4300: VirtualBoxVM.exe: timestamp 0x61018314 (rc=VINF_SUCCESS)
1588.4300: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe: Signature #1/2: info status: 24202
1588.4300: '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe' has no imports
1588.4300: '\Device\HarddiskVolume3\Windows\System32\ntdll.dll' has no imports
1588.4300: supR3HardNtChildPurify: Done after 556 ms and 0 fixes (loop #0).
1588.4300: supR3HardenedEarlyCompact: Removed heap 1 (0x00000001300000 LB 0x400000)
1588.4300: supR3HardNtEnableThreadCreationEx:
2a58.348c: Log file opened: 6.1.26r145957 g_hStartupLog=0000000000000004 g_uNtVerCombined=0xa04a6400
2a58.348c: supR3HardenedVmProcessInit: uNtDllAddr=00007ffe6cb10000 g_uNtVerCombined=0xa04a6400 (stack ~000000000073f3a8)
2a58.348c: ntdll.dll: timestamp 0x1000a5b9 (rc=VINF_SUCCESS)
2a58.348c: New simple heap: #1 0000000000860000 LB 0x400000 (for 2064384 allocation)
2a58.348c: supR3HardenedWinInitAppBin(0x0): '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox'
2a58.348c: System32: \Device\HarddiskVolume3\Windows\System32
2a58.348c: WinSxS: \Device\HarddiskVolume3\Windows\WinSxS
2a58.348c: KnownDllPath: C:\WINDOWS\System32
2a58.348c: supR3HardenedVmProcessInit: Opening vboxdrv...
2a58.348c: supR3HardenedVmProcessInit: Restoring LdrInitializeThunk...
2a58.348c: supR3HardenedVmProcessInit: Returning to LdrInitializeThunk...
2a58.348c: Registered Dll notification callback with NTDLL.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\kernel32.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\kernel32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\KERNEL32.DLL (Input=KERNEL32.DLL, rcNtResolve=0xc0150008) *pfFlags=0xffffffff pwszSearchPath=0000000000004001:<flags> [calling]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a280000 LB 0x002ce000 C:\WINDOWS\System32\KERNELBASE.dll [fFlags=0x0]
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\KernelBase.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\KernelBase.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6c8b0000 LB 0x000bd000 C:\WINDOWS\System32\KERNEL32.DLL [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\kernel32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6c8b0000 'C:\WINDOWS\System32\KERNEL32.DLL'
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ff77f4f0000 LB 0x00118000 C:\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe [fFlags=0x0]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe: Signature #1/2: info status: 24202
2a58.348c: '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe' has no imports
2a58.348c: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe
2a58.348c: supR3HardNtDisableThreadCreation: pvLdrInitThunk=00007ffe6cb84b00 pvNtTerminateThread=00007ffe6cbad990
1588.4300: supR3HardNtChildWaitFor: Found expected request 1 (CloseEvents) after 90 ms.
2a58.348c: \SystemRoot\System32\ntdll.dll:
2a58.348c: CreationTime: 2022-07-19T05:55:10.595200800Z
2a58.348c: LastWriteTime: 2022-07-19T05:55:10.642078900Z
2a58.348c: ChangeTime: 2022-07-20T16:55:05.063776300Z
2a58.348c: FileAttributes: 0x20
2a58.348c: Size: 0x1ef3a8
2a58.348c: NT Headers: 0xe8
2a58.348c: Timestamp: 0x1000a5b9
2a58.348c: Machine: 0x8664 - amd64
2a58.348c: Timestamp: 0x1000a5b9
2a58.348c: Image Version: 10.0
2a58.348c: SizeOfImage: 0x1f8000 (2064384)
2a58.348c: Resource Dir: 0x186000 LB 0x700a0
2a58.348c: [Version info resource found at 0xd8! (ID/Name: 0x1; SubID/SubName: 0x409)]
2a58.348c: [Raw version resource data: 0x1860f0 LB 0x380, codepage 0x0 (reserved 0x0)]
2a58.348c: ProductName: Microsoft® Windows® Operating System
2a58.348c: ProductVersion: 10.0.19041.1806
2a58.348c: FileVersion: 10.0.19041.1806 (WinBuild.160101.0800)
2a58.348c: FileDescription: NT Layer DLL
2a58.348c: \SystemRoot\System32\kernel32.dll:
2a58.348c: CreationTime: 2022-07-19T05:55:18.143584700Z
2a58.348c: LastWriteTime: 2022-07-19T05:55:18.163718600Z
2a58.348c: ChangeTime: 2022-07-20T16:55:01.963495100Z
2a58.348c: FileAttributes: 0x20
2a58.348c: Size: 0xbb058
2a58.348c: NT Headers: 0xe8
2a58.348c: Timestamp: 0x4d6d72d1
2a58.348c: Machine: 0x8664 - amd64
2a58.348c: Timestamp: 0x4d6d72d1
2a58.348c: Image Version: 10.0
2a58.348c: SizeOfImage: 0xbd000 (774144)
2a58.348c: Resource Dir: 0xbb000 LB 0x520
2a58.348c: [Version info resource found at 0x90! (ID/Name: 0x1; SubID/SubName: 0x409)]
2a58.348c: [Raw version resource data: 0xbb0b0 LB 0x3a4, codepage 0x0 (reserved 0x0)]
2a58.348c: ProductName: Microsoft® Windows® Operating System
2a58.348c: ProductVersion: 10.0.19041.1806
2a58.348c: FileVersion: 10.0.19041.1806 (WinBuild.160101.0800)
2a58.348c: FileDescription: Windows NT BASE API Client DLL
2a58.348c: \SystemRoot\System32\KernelBase.dll:
2a58.348c: CreationTime: 2022-07-19T05:55:11.298326500Z
2a58.348c: LastWriteTime: 2022-07-19T05:55:11.360827800Z
2a58.348c: ChangeTime: 2022-07-20T16:55:04.418453400Z
2a58.348c: FileAttributes: 0x20
2a58.348c: Size: 0x2d0058
2a58.348c: NT Headers: 0x100
2a58.348c: Timestamp: 0x299341e8
2a58.348c: Machine: 0x8664 - amd64
2a58.348c: Timestamp: 0x299341e8
2a58.348c: Image Version: 10.0
2a58.348c: SizeOfImage: 0x2ce000 (2940928)
2a58.348c: Resource Dir: 0x2a5000 LB 0x548
2a58.348c: [Version info resource found at 0x90! (ID/Name: 0x1; SubID/SubName: 0x409)]
2a58.348c: [Raw version resource data: 0x2a50b0 LB 0x3bc, codepage 0x0 (reserved 0x0)]
2a58.348c: ProductName: Microsoft® Windows® Operating System
2a58.348c: ProductVersion: 10.0.19041.1826
2a58.348c: FileVersion: 10.0.19041.1826 (WinBuild.160101.0800)
2a58.348c: FileDescription: Windows NT BASE API Client DLL
2a58.348c: \SystemRoot\System32\apisetschema.dll:
2a58.348c: CreationTime: 2019-12-07T09:08:13.518339400Z
2a58.348c: LastWriteTime: 2019-12-07T09:08:13.518339400Z
2a58.348c: ChangeTime: 2022-07-19T05:56:25.514604000Z
2a58.348c: FileAttributes: 0x20
2a58.348c: Size: 0x1f538
2a58.348c: NT Headers: 0xd0
2a58.348c: Timestamp: 0x31288ce0
2a58.348c: Machine: 0x8664 - amd64
2a58.348c: Timestamp: 0x31288ce0
2a58.348c: Image Version: 10.0
2a58.348c: SizeOfImage: 0x20000 (131072)
2a58.348c: Resource Dir: 0x1f000 LB 0x408
2a58.348c: [Version info resource found at 0x48! (ID/Name: 0x1; SubID/SubName: 0x409)]
2a58.348c: [Raw version resource data: 0x1f060 LB 0x3a8, codepage 0x0 (reserved 0x0)]
2a58.348c: ProductName: Microsoft® Windows® Operating System
2a58.348c: ProductVersion: 10.0.19041.1
2a58.348c: FileVersion: 10.0.19041.1 (WinBuild.160101.0800)
2a58.348c: FileDescription: ApiSet Schema DLL
2a58.348c: NtOpenDirectoryObject failed on \Driver: 0xc0000022
2a58.348c: supR3HardenedWinFindAdversaries: 0x3
2a58.348c: \SystemRoot\System32\drivers\SysPlant.sys:
2a58.348c: CreationTime: 2021-07-20T13:41:23.315594100Z
2a58.348c: LastWriteTime: 2021-12-06T12:33:04.399232700Z
2a58.348c: ChangeTime: 2021-12-06T12:33:04.399232700Z
2a58.348c: FileAttributes: 0x20
2a58.348c: Size: 0x407f8
2a58.348c: NT Headers: 0xe0
2a58.348c: Timestamp: 0x607155cb
2a58.348c: Machine: 0x8664 - amd64
2a58.348c: Timestamp: 0x607155cb
2a58.348c: Image Version: 5.0
2a58.348c: SizeOfImage: 0x41000 (266240)
2a58.348c: Resource Dir: 0x3f000 LB 0x3a8
2a58.348c: [Version info resource found at 0x48! (ID/Name: 0x1; SubID/SubName: 0x409)]
2a58.348c: [Raw version resource data: 0x3f060 LB 0x348, codepage 0x0 (reserved 0x0)]
2a58.348c: ProductName: Symantec CMC Firewall
2a58.348c: ProductVersion: 14.3.4540.2000
2a58.348c: FileVersion: 14.3.4540.2000
2a58.348c: FileDescription: Symantec CMC Firewall SysPlant
2a58.348c: \SystemRoot\System32\drivers\symevent64x86.sys:
2a58.348c: CreationTime: 2021-07-20T13:41:35.690592800Z
2a58.348c: LastWriteTime: 2022-04-25T09:08:20.525420600Z
2a58.348c: ChangeTime: 2022-04-26T05:55:25.934395000Z
2a58.348c: FileAttributes: 0x20
2a58.348c: Size: 0x187f8
2a58.348c: NT Headers: 0xd8
2a58.348c: Timestamp: 0x61786ab8
2a58.348c: Machine: 0x8664 - amd64
2a58.348c: Timestamp: 0x61786ab8
2a58.348c: Image Version: 10.0
2a58.348c: SizeOfImage: 0x24000 (147456)
2a58.348c: Resource Dir: 0x22000 LB 0x3cc
2a58.348c: [Version info resource found at 0x90! (ID/Name: 0x1; SubID/SubName: 0x409)]
2a58.348c: [Raw version resource data: 0x220b8 LB 0x314, codepage 0x4e4 (reserved 0x0)]
2a58.348c: ProductName: SYMEVENT
2a58.348c: ProductVersion: 14.0.8.101
2a58.348c: FileVersion: 14.0.8.101
2a58.348c: FileDescription: Symantec Event Library
2a58.348c: supR3HardenedWinInitAppBin(0x0): '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox'
2a58.348c: Calling main()
2a58.348c: SUPR3HardenedMain: pszProgName=VirtualBoxVM fFlags=0x2
2a58.348c: supR3HardenedWinInitAppBin(0x2): '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox'
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe: Signature #1/2: info status: 24202
2a58.348c: '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe' has no imports
2a58.348c: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe)
2a58.348c: SUPR3HardenedMain: Final process, opening VBoxDrv...
2a58.348c: supR3HardenedEarlyCompact: Removed heap 1 (0x00000000860000 LB 0x400000)
2a58.348c: supR3HardNtEnableThreadCreationEx:
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSupLib.dll: Signature #1/2: info status: 24202
2a58.348c: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSupLib.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSupLib.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxSupLib.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSupLib.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe673d0000 LB 0x00005000 C:\Program Files\Oracle\VirtualBox\VBoxSupLib.DLL [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSupLib.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSupLib.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxSupLib.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe673d0000 'C:\Program Files\Oracle\VirtualBox\VBoxSupLib.DLL'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSupLib.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxSupLib.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe673d0000 'C:\Program Files\Oracle\VirtualBox\VBoxSupLib.DLL'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe673d0000 'C:\Program Files\Oracle\VirtualBox\VBoxSupLib.DLL'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #29 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\wintrust.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\wintrust.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\msvcrt.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\msvcrt.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\Wintrust.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6b240000 LB 0x0009e000 C:\WINDOWS\System32\msvcrt.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6b450000 LB 0x00125000 C:\WINDOWS\System32\RPCRT4.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a720000 LB 0x00067000 C:\WINDOWS\System32\Wintrust.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wintrust.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a910000 LB 0x00100000 C:\WINDOWS\System32\ucrtbase.dll [fFlags=0x0]
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\ucrtbase.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\ucrtbase.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6aa10000 LB 0x00156000 C:\WINDOWS\System32\CRYPT32.dll [fFlags=0x0]
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\crypt32.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\crypt32.dll
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-synch-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-synch-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-synch-l1-2-0'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-fibers-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-fibers-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-fibers-l1-1-1'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-fibers-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-fibers-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-fibers-l1-1-1'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-synch-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-synch-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-synch-l1-2-0'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-localization-l1-2-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-localization-l1-2-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-localization-l1-2-1'
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\msasn1.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\msasn1.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe69e20000 LB 0x00012000 C:\WINDOWS\SYSTEM32\MSASN1.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msasn1.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a720000 'C:\WINDOWS\system32\Wintrust.dll'
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\bcrypt.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\bcrypt.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\bcrypt.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a6f0000 LB 0x00027000 C:\WINDOWS\System32\bcrypt.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\bcrypt.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a6f0000 'C:\WINDOWS\system32\bcrypt.dll'
2a58.348c: bcrypt.dll loaded at 00007ffe6a6f0000, BCryptOpenAlgorithmProvider at 00007ffe6a6f51e0, preloading providers:
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\bcryptprimitives.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\bcryptprimitives.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\bcryptprimitives.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a550000 LB 0x00082000 C:\WINDOWS\System32\bcryptprimitives.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\bcryptprimitives.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a550000 'C:\WINDOWS\system32\bcryptprimitives.dll'
2a58.348c: BCryptOpenAlgorithmProvider(,'MD2',0,0) -> 0x0 (hAlgo=0000000000d81830)
2a58.348c: BCryptOpenAlgorithmProvider(,'MD4',0,0) -> 0x0 (hAlgo=0000000000d81eb0)
2a58.348c: BCryptOpenAlgorithmProvider(,'MD5',0,0) -> 0x0 (hAlgo=0000000000d821d0)
2a58.348c: BCryptOpenAlgorithmProvider(,'SHA1',0,0) -> 0x0 (hAlgo=0000000000d824f0)
2a58.348c: BCryptOpenAlgorithmProvider(,'SHA256',0,0) -> 0x0 (hAlgo=0000000000d82810)
2a58.348c: BCryptOpenAlgorithmProvider(,'SHA512',0,0) -> 0x0 (hAlgo=0000000000d82b30)
2a58.348c: BCryptOpenAlgorithmProvider(,'RSA',0,0) -> 0x0 (hAlgo=0000000000d82e50)
2a58.348c: BCryptOpenAlgorithmProvider(,'DSA',0,0) -> 0x0 (hAlgo=0000000000d83170)
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\cryptsp.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\cryptsp.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe69bf0000 LB 0x00018000 C:\WINDOWS\SYSTEM32\CRYPTSP.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptsp.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #18 'bcrypt.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\rsaenh.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\rsaenh.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'bcrypt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'bcrypt.dll' -> '\Device\HarddiskVolume3\Windows\System32\bcrypt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\bcrypt.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe691b0000 LB 0x00034000 C:\WINDOWS\system32\rsaenh.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\cryptbase.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\cryptbase.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe69b20000 LB 0x0000c000 C:\WINDOWS\SYSTEM32\CRYPTBASE.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptbase.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\kernel32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\kernel32.dll (Input=kernel32.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6c8b0000 'C:\WINDOWS\System32\kernel32.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wintrust.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\WINTRUST.DLL (Input=WINTRUST.DLL, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a720000 'C:\WINDOWS\System32\WINTRUST.DLL'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\CRYPT32.dll (rcNtResolve=0xc0150008) *pfFlags=0x2 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\CRYPT32.dll'
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6b2e0000 LB 0x0001d000 C:\WINDOWS\System32\imagehlp.dll [fFlags=0x0]
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\imagehlp.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\imagehlp.dll
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6c590000 LB 0x0009c000 C:\WINDOWS\System32\sechost.dll [fFlags=0x0]
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #11 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\sechost.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\sechost.dll
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #10 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\gpapi.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\gpapi.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe68990000 LB 0x00023000 C:\WINDOWS\SYSTEM32\gpapi.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gpapi.dll [lacks WinVerifyTrust]
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\profapi.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\profapi.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a170000 LB 0x0001f000 C:\WINDOWS\SYSTEM32\profapi.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\profapi.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'crypt32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\cryptnet.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\cryptnet.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'crypt32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'crypt32.dll' -> '\Device\HarddiskVolume3\Windows\System32\crypt32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\cryptnet.dll (Input=cryptnet.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe61c80000 LB 0x00031000 C:\WINDOWS\System32\cryptnet.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\cryptnet.dll (rcNtResolve=0xc0150008) *pfFlags=0x2 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\cryptnet.dll (rcNtResolve=0xc0150008) *pfFlags=0x2 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\cryptnet.dll (rcNtResolve=0xc0150008) *pfFlags=0x2 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\cryptnet.dll (rcNtResolve=0xc0150008) *pfFlags=0x2 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\cryptnet.dll (rcNtResolve=0xc0150008) *pfFlags=0x2 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\cryptnet.dll (rcNtResolve=0xc0150008) *pfFlags=0x2 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cryptnet.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61c80000 'C:\WINDOWS\System32\cryptnet.dll'
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6bba0000 LB 0x000ae000 C:\WINDOWS\System32\advapi32.dll [fFlags=0x0]
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'sechost.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #27 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\advapi32.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\advapi32.dll
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'sechost.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'sechost.dll' -> '\Device\HarddiskVolume3\Windows\System32\sechost.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\sechost.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\crypt32.dll (Input=crypt32.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000000 pwszName=\SystemRoot\System32\ntdll.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: New context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=354B227DADEAEC20A485E962996E22B5479742B8
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\rpcrt4.dll (Input=rpcrt4.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6b450000 'C:\WINDOWS\System32\rpcrt4.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\crypt32.dll (Input=crypt32.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package0516~31bf3856ad364e35~amd64~~10.0.19041.1826.cat'; file='\SystemRoot\System32\ntdll.dll'
2a58.348c: g_pfnWinVerifyTrust=00007ffe6a721ea0
2a58.348c: supR3HardenedScreenImage/preload: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll [redoing WinVerifyTrust]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\crypt32.dll (Input=crypt32.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedScreenImage/preload: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\crypt32.dll'
2a58.348c: supR3HardenedScreenImage/preload: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wintrust.dll [redoing WinVerifyTrust]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\crypt32.dll (Input=crypt32.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedScreenImage/preload: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\wintrust.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\crypt32.dll (Input=crypt32.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\advapi32.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\cryptnet.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\profapi.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\gpapi.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\sechost.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\imagehlp.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\cryptbase.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\crypt32.dll (Input=crypt32.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\cryptsp.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\bcryptprimitives.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\bcrypt.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\msasn1.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\ucrtbase.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 24202) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSupLib.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 24202) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.exe'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\KernelBase.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\kernel32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\system32\crypt32.dll'
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2cefdedc7165bf00 CN=SI0VM05747.de.bosch.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf5876967654990b7 CN=FE-C-003XT.fe.de.bosch.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x5ad46780fa5df300 DC=com, DC=microsoft, CN=Microsoft Root Certificate Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xea5386456178582b C=ZA, ST=Western Cape, L=Durbanville, O=Thawte, OU=Thawte Certification, CN=Thawte Timestamping CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd60940f5f643b400 DC=com, DC=Bosch, CN=PKI, CN=BoschCA-DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3be670c1bd02a900 OU=Copyright (c) 1997 Microsoft Corp., OU=Microsoft Corporation, CN=Microsoft Root Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe991ee72b03db500 C=US, O=Symantec Corporation, CN=Symantec Enterprise Mobile Root for Microsoft
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4d3835aa4180b200 C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft Root Certificate Authority 2011
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x646e3fe3ba08df00 C=US, O=MSFT, CN=Microsoft Authenticode(tm) Root Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x357a29080824af00 C=US, O=VeriSign, Inc., OU=VeriSign Trust Network, OU=(c) 2006 VeriSign, Inc. - For authorized use only, CN=VeriSign Class 3 Public Primary Certification Authority - G5
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xece4e4289e08b900 C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft Root Certificate Authority 2010
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf3bb4d7e894b420 C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft ECC TS Root Certificate Authority 2018
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe04d56e32ec3911c CN=FE-C-003XT.fe.de.bosch.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x43a9cc371ff5385a O=Microsoft Trust Network, OU=Microsoft Corporation, OU=Microsoft Time Stamping Service Root, OU=Copyright (c) 1997 Microsoft Corp.
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2e2d2c7c68f0202e O=VeriSign Trust Network, OU=VeriSign, Inc., OU=VeriSign Time Stamping Service Root, OU=NO LIABILITY ACCEPTED, (c)97 VeriSign, Inc.
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa9bab0af360cc000 DC=com, DC=Bosch, CN=PKI, CN=Bosch-CA-DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3ac9217d54a5c100 CN=osd.bosch.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xcec3d46562b9be8e C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft ECC Product Root Certificate Authority 2018
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xca58a05dd401ae00 C=US, ST=Washington, L=Redmond, O=Microsoft Corporation, CN=Microsoft Time Stamp Root Certificate Authority 2014
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x61a3a33f81aace00 C=US, ST=UT, L=Salt Lake City, O=The USERTRUST Network, OU=http://www.usertrust.com, CN=UTN-USERFirst-Object
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbbde687390e6bf00 C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Trusted Root G4
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x83085097e9afdf00 O=Digital Signature Trust Co., CN=DST Root CA X3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3714f47324e8ad00 C=US, O=Internet Security Research Group, CN=ISRG Root X1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd944bca189a00 C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc6fa4243b695b600 C=US, O=Entrust, Inc., OU=www.entrust.net/CPS is incorporated by reference, OU=(c) 2006 Entrust, Inc., CN=Entrust Root Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa671e9fec832b700 C=US, O=Starfield Technologies, Inc., OU=Starfield Class 2 Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa8de7211e13be200 C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbebef0d2217f0bfb C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6f2ebe0e24cfa600 OU=GlobalSign Root CA - R2, O=GlobalSign, CN=GlobalSign
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x14018a1bf29e595c C=US, O=VeriSign, Inc., OU=Class 3 Public Primary Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1b8578514b74ac00 C=US, O=WFA Hotspot 2.0, CN=Hotspot 2.0 Trust Root CA - 03
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x59faf1086271bf00 C=US, ST=Arizona, L=Scottsdale, O=GoDaddy.com, Inc., CN=Go Daddy Root Certificate Authority - G2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3401b15e3761c700 C=US, O=VeriSign, Inc., OU=VeriSign Trust Network, OU=(c) 2008 VeriSign, Inc. - For authorized use only, CN=VeriSign Universal Root Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xdc1801b225aea100 C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 2 G3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x507e9fec029ab000 CN=Continentale Mail CA M1, L=Dortmund, ST=Germany, C=DE, Email=postmaster@continentale.de, O=Continentale Krankenversicherung auf Gegenseitigkeit, OU=IK4-SV
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x441930e7b5e2ca00 C=DE, ST=Berlin, L=Berlin, O=Dentons, OU=Dentons, CN=Dentons Root CA, Email=x509-ca@dentons.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x66eac58ea952c100 C=DE, ST=Baden-Wuerttemberg, L=Reutlingen, O=Kittelberger media solutions GmbH, OU=ID/CA, CN=Kittelberger CA, Email=sysadmin@kittelberger.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x12dd0e32ecfb500 C=DE, O=DATEV eG, CN=CA DATEV STD 95
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xad3772a82e25c700 DC=com, DC=daimlerchrysler, DC=mbtech-group, CN=MBtech_Root_CA2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7bdd57656070f000 DC=COM, DC=JSHFIRM, CN=JSHFIRM-JSHCERTSRV-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6b6461cb46a0a800 CN=CPA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7b37cec31576ed00 C=GB, O=ODETTE International Ltd., CN=ODETTE Root
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x774be61ad7bbbe00 C=DE, O=Siemens, SRN=ZZZZZZV1, OU=Copyright (C) Siemens AG 2011 All Rights Reserved, CN=Siemens Trust Center Root-CA V2.0
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x655ce5f8f054b800 C=TW, ST=Taiwan, L=Taichung City, O=CoPower Industrial Corp., CN=co-power.com.tw
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x68af09543f4ca800 DC=local, DC=cognitas, CN=cognitas-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8a6a4efb2816a900 C=DE, ST=Hessen, L=Giessen, O=INI GmbH, Email=kontakt@iniu.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xcc60c47713f0b200 C=DE, ST=Nordrhein-Westfalen, L=Koeln, O=TUEV Rheinland i-sec GmbH, OU=TUEV Rheinland i-sec GmbH, CN=TUEV Rheinland i-sec GmbH Mail CA, Email=pki@i-sec.tuv.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x121a6f7758a9c300 DC=com, DC=adit-jv, CN=ADIT Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2cffc9c0cbb38d00 DC=com, DC=boschhuayu-steering, CN=boschhuayu-steering-BHSHS02296-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xebb55177c4bed200 C=DE, ST=Bayern, L=Augsburg, O=RENK AG, OU=RENK AG, CN=RENK.BIZ
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x5bb6017d32c7d200 CN=Hidria Root CA SHA2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x12e715b0dfb1bd00 DC=local, DC=streetscooter, CN=StreetScooter GmbH
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xeee47662fbc69a00 CN=AMD Corporate Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1b10e33a02c39b00 C=DE, O=Deutsche Bahn, OU=Public Key Services, CN=DB Root CA 1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x86bfabd793679600 DC=local, DC=aat, CN=AAT-CA-LON
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8f2c148cbf62b400 C=CZ, L=Ceske Budejovice, O=dataPartner s. r. o., CN=dataPartner Root CA, Email=kontakt@datapartner.cz
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xae104e51d4b49500 DC=COM, DC=LW, CN=LathamandWatkinsRootCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xed71294e3ebff300 DC=local, DC=Ferchau, CN=FERCHAU Zertifikatsstelle
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7815e9804713a500 DC=local, DC=Wesa, CN=Wesa-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9d82278b074fc200 C=DE, O=Daimler AG, CN=Corp-Root-CA-G2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xaa32438658208100 C=DE, O=PKI-1-Verwaltung, CN=PCA-1-Verwaltung-20
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x418a6f9390fbb300 DC=local, DC=phgroup, CN=Prohome-Kft-Root-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x94946b5d6cd7f628 CN=mail.koenen.de, OU=Gateway, O=Koenen GmbH, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x227db69beed7ce00 C=DE, ST=Bayern, L=Nuernberg, O=Sparda-Datenverarbeitung eG, OU=SY-MNS-MSEC, CN=Sparda-Datenverarbeitung Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3b9f1e349458bd00 Email=ikt@hbw.de, C=DE, ST=Bavaria, L=Munich, O=hbw.de, OU=hbw - Haus der Bayerischen Wirtschaft, CN=hbw.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc18b3bd48bf580de C=DE, L=Ottersberg/Pliening, O=Hologram Industries Research GmbH, OU=Certificate Authority, CN=Hologram Industrie CA, Email=ca@hi-research.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xdc676f5f0f3bd400 C=DE, O=EDAG GmbH & Co. KGaA, OU=EDAG GmbH & Co. KGaA, CN=EDAG GmbH & Co. KGaA CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3ed0861eb44fd100 DC=de, DC=neimcke-ts, CN=neimcke-ts-DATEISERVER-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1369a5aa8dfa9400 DC=com, DC=Deloitte, CN=Deloitte SHA2 Level 1 CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9c7b131bcbbfb100 C=DE, ST=BY, L=Graefelfing, O=Sartena, CN=ca_chr, Email=chr@sartena.org
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbb0ff40157aead00 C=de, L=Freiburg, O=embex GmbH, OU=Gateway, CN=fw01.embex.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xafbd096546a697ad CN=mailgateway, OU=Gateway, O=WTI GmbH, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x31aabac9c0abda00 DC=com, DC=stites, CN=stites-STITESROOTCA-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf3718d4a6608e800 DC=ch, DC=snb, CN=Configuration, CN=Services, CN=Public Key Services, CN=AIA, CN=SNB Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2fc674c1cb15f800 DC=tw, DC=com, DC=txc, CN=txc-PCAD2-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa4043421d52ad300 CN=McGlincheyRootCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe58a37f83dc6ce00 C=local, O=wpsskp, CN=SGP ROOT CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x12218654c799ce00 OU=Support, ST=Thueringen, Email=kanzlei@liedtke-patent.de, O=Liedtke & Partner, CN=mail1.liedtke-patent.de, L=Erfurt, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe9f447ccfb50b900 C=DE, ST=Baden-Wuerttemberg, L=Ravensburg, O=Schuler, CN=Schuler CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd352c3939929e800 CN=KW-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe7ee1a97ce0ccd00 L=Bonnemain, O=Delta Dore, CN=Delta Dore
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xb1f1ed8b3da358e0 C=DE, ST=Saxony, L=Lauta, O=Programmierbare Logik & Systeme GmbH, OU=CA, CN=CA Programmierbare Logik & Systeme GmbH
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc90c7a0fb7f2db00 C=DE, ST=Bayern, O=Ingenieurbuero Teichgraeber, OU=Certificate Authority, CN=Michael Teichgraeber, Email=mteichgraeber@gmx.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8d415c0f556db600 C=TN, O=ANCE, OU=Certification & PKI, CN=Agence Nationale de Certification Electronique, Email=ance@certification.tn
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1bde2318efe5b800 C=DE, ST=Baden-Wuerttemberg, L=Reutlingen, O=Kittelberger media solutions GmbH, OU=ID/CA, CN=SysAdmin, Email=sysadmin@kittelberger.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x684f3820aa688200 C=DE, O=PKI-1-Verwaltung, CN=PCA-1-Verwaltung-14
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4fe6bfbd0c66be00 C=DE, O=Brose, CN=BroseRootCA2015
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2d2f0a83fe77bd00 DC=net, DC=osram, CN=OSRAM Root CA 2011
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf4f8f1450f10e200 CN=MAIWALD-CA, OU=IT, O=Maiwald Patentanwalts GmbH, C=49
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xfe9e55cfd278100 DC=com, DC=smbtrials, CN=SMB-AUTH-01
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbb671b518318db00 C=DE, O=Werkstoffzentrum Rheinbach GmbH, OU=IT-Security, CN=WZR - Common Root CA - 2010
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9952194434ceab00 DC=local, DC=aat, CN=AAT-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x39b51e0af9ca200 CN=BCG-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe7d1cc0250c1b300 CN=Goodwin-Root-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3e1d513a443c9800 C=DE, O=Allianz Group, CN=Allianz Group Root CA II
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1abacbe8064bac00 C=DE, O=HvS-Consulting AG, CN=HvS Root-CA I
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4c810f3d3932b000 C=DE, ST=NRW, L=Bonn, O=steep GmbH, OU=ITSM, CN=steep S/MIME Root CA, Email=it@steep.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd71519e43fd5ba00 C=CA, ST=Ontario, L=Toronto, O=Echoworx Corporation, OU=Certification Services, CN=Echoworx Root CA2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xabf53f6e156be500 CN=PU Offline Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9147c6699b469400 DC=de, DC=itk-engineering, CN=ITK-ROOT-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc80944791f6c0204 C=DE, L=Ottobrunn, O=IABG, CN=IABG-Corporate-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8ff19aab7152e300 CN=kuglermaag.com, O=KUGLER MAAG CIE GmbH, L=Kornwestheim, C=DE, Email=mathias.klugt@kuglermaag.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf4d314599572ab7 CN=astaro1.stadt-mh.de, OU=Gateway, O=Stadt-MH, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf28e30a938bcd600 CN=secmail-ca.xnetsolutions.de, Email=secmail-ca@xnetsolutions.de, OU=SX-MailCrypt, O=XnetSolutions KG, L=Herrenberg, ST=Baden-Wuerrtemberg, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3e0ae9d1eeb1a900 C=DE, ST=BW, L=Mannheim, O=Hays AG, OU=Corporate Technology, CN=Hays AG X.509 CA, Email=x509-ca@hays.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x735b8bfd86a8b800 C=DE, O=Brose, CN=Brose-CA-Root-07
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x5f2b294f0fa7fc00 C=de, O=swm, CN=SWM Root CA V2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbd8e26f92da2b800 C=DE, ST=Baden-Wuerttemberg, O=1&1 Mail & Media GmbH, OU=Trust Center, CN=WEB.DE TrustCenter, Email=trust@web.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1361de89649ea500 C=Germany, ST=Bavaria, L=Nuernberg, OU=90441 Nürnberg, OU=Holbeinstr. 23, OU=GER, CN=Murata Elektronik GmbH
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x676bd54406d8e300 O=Group, OU=APPLICATIONS, OU=iPKI, CN=2014-2044 BNPP Root
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x81704894f11736ae CN=mail.mpatent.eu, OU=Gateway, O=Kudlek & Grunert Patentanwälte, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4531670f4ac9d400 DC=de, DC=uvb-online, CN=UVB e.V. Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x915268dde9c79500 CN=Lionbridge Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xfd9333ce0da8ef00 CN=Validated Advice CA 2020, ST=NRW, C=DE, L=Dinslaken
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3c53844c390a9200 C=DE, ST=NRW, L=Bonn, O=BaFin, OU=IT 7, CN=BaFin Secure Mail Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x11026db0fa7ab100 C=DE, O=BASF, CN=BASF Root CA 2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9e353910cf539f00 Email=it@dreiss.de, C=DE, ST=Baden-Wuerttemberg, L=Stuttgart, O=DREISS Patentanwaelte PartG mbB, OU=IT, CN=DREISS mailCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x406cb4c8a323a900 DC=local, DC=aat, CN=aat-LONAD03-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xaa19af39cb0fac00 DC=com, DC=uaes, CN=UAESRootCA2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3c53668bc331af00 C=BG
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xed68ac233432db00 C=DE, O=PRETTL Group, CN=PRETTL Global Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x27080eb9e11b900 C=DE, ST=Bavaria, L=Munich 80796, O=KSNH Patentanwaelte Klunker.Schmitt-Nilson.Hirsch, OU=KSNH Trustcenter, CN=KSNH::SMIME CA ROOT, Email=ksnh-ca@ksnh.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x81888e957ae6cd00 C=SE, O=Scania AB (publ), OU=Scania CV AB (publ), OU=Scania IT AB, CN=Scania Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9cbaed8850dac00 DC=local, DC=top, CN=Unitech
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x790f406f5bfdd400 C=DE, O=Bundesbank, OU=Bundesbank PKI, CN=Bundesbank Root CA 2015 II for Central Bank Issues, Email=pki@bundesbank.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8bbc70907929ac00 C=RU, O=Sollers, CN=Sollers Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xb87dace9691aba00 CN=Continentale Root JCA, L=Dortmund, ST=Germany, C=DE, Email=julia-pm@en.continentale.de, O=Continentale Krankenversicherung aG, OU=IK
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4cbd5f07e046ba00 CN=Riscure-ROOTCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xebdaf6daa490c500 DC=net, DC=swatchgroup, CN=Swatch Group Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf063b2399f2a9f00 C=HU, ST=Pest, O=HLB Klient, OU=IT, CN=Klient CA, Email=cadmin@klient.hu
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf956f283f7afb500 CN=igg-DOMCON-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x297eff563deeb400 DC=com, DC=pedrazachb, DC=pedraza, CN=pedraza-MANX-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbab415bd1e249800 C=US, OU=www.xrampsecurity.com, O=XRamp Security Services Inc, CN=XRamp Global Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xcb7d2ba3dd0ff900 C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com Root Certification Authority RSA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x37d74338c344c100 CN=seppmail.berlin-patent.net, Email=office@berlin-patent.net, OU=Patentattorneys GHZS, O=Patentattorneys GHZS, L=Berlin, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8cdabe2904a4e200 DC=NET, DC=VOITH, CN=VoithRootCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd7ad00cd0b93bc00 DC=local, DC=aleo, CN=aleo solar Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2fd077297c5a203e C=ES, O=StartCom CA, CN=StartCom Certification Authority ECC
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8b939e307f25c900 DC=group, DC=hv, CN=Hirschvogel Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x309bd61d0518a000 C=DE, ST=Nordrhein-Westfalen, L=Paderborn, O=Scenario Management International AG, CN=CA, Email=info@scmi.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x31ae72c74210188 C=US, O=VeriSign, Inc., OU=Class 2 Public Primary Certification Authority - G2, OU=(c) 1998 VeriSign, Inc. - For authorized use only, OU=VeriSign Trust Network
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa77e582301cec600 DC=com, DC=deloitte, CN=Deloitte Level 1 CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4fa4cd08cac4ff00 C=DE, O=SECUDE GmbH, CN=SECUDE Trustfactory ROOT
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3f33140d0aa0b900 C=DE, O=Carl Zeiss AG, CN=Carl Zeiss AG Root-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3e1016c6cb2cb000 C=DE, ST=Deutschland, L=Luebeck, O=MEN@NET GmbH, CN=MEN@NET Email Certificate Authority, Email=root-ca@menatnet.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x5e7f2e0e0f46e700 DC=com, DC=adit-jv, CN=ADIT Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf32463a1f675ee00 DC=local, DC=schneider, CN=SchneiderSchwegler
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa50b662ecf85a600 CN=LewisBrisbois Global CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x26edc7c0b23ab800 C=CZ, O=Česká pošta, s.p. [IČ 47114983], CN=PostSignum Root QCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd175b517f512ba00 Email=certificate_services@daimler.com, C=DE, ST=Baden-Wuerttemberg, L=Stuttgart, O=Daimler AG, OU=Global Information Security, CN=Corp-Root-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xcf7d09b8719fc800 DC=com, DC=pattishall, CN=Pattishall-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xced60d4db5c8d100 CN=Steering-Column-Offline-Root-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc3f08e9b8780ab00 C=DE, O=TC TrustCenter GmbH, OU=TC TrustCenter Class 2 CA, CN=TC TrustCenter Class 2 CA II
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x835895095e01a800 C=DE, L=Kernen, O=Ing.Buero Ch.Baeder, CN=cbaeder.de, Email=dialog@cbaeder.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe6dbc3d8f092bd00 DC=local, DC=HRISBS, CN=HRICA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4d2097ab9c2fb400 C=de, L=Darmstadt, O=Mechatronic AG, OU=Gateway, CN=meda1029.mechatronic.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x18fbded6016ad600 DC=de, DC=wima, CN=WIMA-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbe7ea0828d66c600 C=CZ
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x50a2cbd8758dc700 C=RU, O=Kaspersky, CN=Kaspersky Root CA G3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6b0c668b94c9d700 C=DE, ST=Hessen, L=Kronberg, O=EUROSEC GmbH Chiffriertechnik & Sicherheit, CN=EUROSEC Certificate Authority G2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x953bc090c22bc000 C=DE, ST=Baden-Wuerttemberg, L=Stuttgart, O=Landesbank Baden-Wuerttemberg, CN=LBBW W04 Root CA G1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe0112affae7ca900 C=Germany, ST=Hessen, L=Eschborn, O=Vodafone AG, CN=VodafoneMail
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6d1c73d3669a700 C=DE, ST=Bayern, L=Muenchen, O=Siemens, SRN=ZZZZZZA1, OU=Siemens Trust Center, CN=Siemens Root CA V3.0 2016
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x881799327f9ab700 DC=intern, DC=conplement, CN=conplementDC2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x72e76894ccf7b400 C=DE, ST=BW, L=Esslingen am Neckar, O=Teams Design GmbH, OU=IT, CN=Teams Design, Email=info@teams-design.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd7becfd0fddacb00 DC=local, DC=aat, CN=AAT-CA-LON
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x963809313e28e00 C=DE, O=Krauss-Maffei Wegmann GmbH & Co KG, CN=Krauss-Maffei Wegmann SecureMail Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xed6ce3810bdb9a00 C=NL, ST=Noord-Brabant, L=Eindhoven, O=NXP B.V., OU=IT, CN=NXP ROOT CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x737540608178cf00 CN=IAV-CA-ROOT-02, L=Berlin, ST=Berlin, C=DE, Email=cert_authority@iav.de, O=IAV GmbH, OU=IAV Certificate Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc03fb369c42cc00 C=de, O=Infineon Technologies AG, CN=Infineon Technologies AG Root CA 2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x762e0032b619b00 CN=SecureMail.noerr.com, OU=IT-Department, O=Noerr LLP, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x32b7a6c2845f8500 DC=de, DC=ewkgmbh, CN=DEWRootCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x363f522f28e7d900 C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root G2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xda5f1cc8fc5ca000 C=CZ, O=Česká pošta, s.p. [IČ 47114983], CN=PostSignum Root QCA 2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xb6b25b1eb652d400 DC=de, DC=enbw-kk, CN=EnKK Root CAv01
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4ec1e774ddf4bd00 C=DE, O=BASF, CN=BASF Root CA 21
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xdfe40c8a603fe800 C=US, O=FTI Consulting Inc, CN=FTIANNRoot2013
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa7aeb3d7a287ec00 DC=hld, DC=root, CN=Schaeffler Group Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf444417a00c9bdd C=DE, O=Deutsche Telekom AG, OU=T-TeleSec Trust Center, CN=Deutsche Telekom Root CA 1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x624cbd11f17ac900 DC=ivmwien, CN=IVMCert
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa3c705462c409400 CN=HEPOL-EVG-CA, L=Willy-Brandt-Allee 20, 65197 Wiesbaden, ST=Hessen, C=DE, Email=administration-ikt.evg@polizei.hessen.de, O=Landespolizei Hessen, OU=HEPOL
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbd7920f6f641d900 DC=local, DC=paravan, CN=paravan-SPAAI001-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x878de2ee14799c00 DC=local, DC=alfatec, CN=alfatec-ALDC2-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x76af89b5553faa00 C=CZ, O=První certifikační autorita, a.s., CN=I.CA Root CA/RSA, SRN=NTRCZ-26439395
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x860d75e3b7b2b500 Email=exchangeadministrator@allenovery.com, C=GB, ST=London, L=London, O=Allen & Overy LLP, OU=IT, CN=allenovery.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1d98741521a8b800 OU=Organizational CA, O=MESCOTREE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x66b006eda821c800 CN=TUEV NORD ROOTCAv3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xcfafba2daebcca00 DC=cn, DC=ntd, CN=ntd-CNIDC-V01-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x35c08652b63c8b00 CN=ADP Employer Services GmbH Internal Root CA, O=ADP Employer Services GmbH, L=Bremen, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa5d7f50f2ed2a800 C=DE, ST=Niedersachsen, L=Oldenburg, O=OFFIS e.V., CN=OFFIS SelfCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3f94ab1ea3869200 C=de, O=Lufthansa, OU=Lufthansa CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe0af9e2cbb4bc600 C=DE, ST=BaWue, L=Stuttgart, O=Moenkemoeller & Co. GmbH, OU=IT, CN=Moenkemoeller SMIME CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc9dbe17554fcc100 C=CH, ST=AG, L=Windisch, O=Fachhochschule Nordwestschweiz, OU=Hochschule fuer Technik, CN=FHNW HT, Email=ict.windisch@fhnw.ch
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x85492685d0acb100 C=DE, ST=BY, L=Munich, O=SupplyON AG, OU=CIT, CN=SupplyOn AG Trusted Root CA-01, Email=it-supplyon@supplyon.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x881799327f9ab700 DC=intern, DC=conplement, CN=conplementDC2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4dcfda428b23dd00 C=DE, ST=BW, L=Mannheim, O=IB-Patent, OU=IT, CN=IB-Patent Root CA2, Email=it@ib-patent.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xdd650219dd965cfd C=DE, ST=Bavaria, L=Hoehenkirchen, O=Lauterbach GmbH, CN=Lauterbach ROOT CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xddd529a4a293bc00 C=TW, OU=IT, CN=TPEV_Cert
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x73b47db04e629a00 C=US, ST=Massachusetts, L=Boston, O=Hinckley Allen, CN=Hinckley Allen Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1cbb3fd4fda7c300 C=DE, ST=Bavaria, L=Ingolstadt, O=AUDI AG, CN=AUDI AG securEmail Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6652688a8dc5af00 Email=help_desk@epam.com, C=BY, ST=MSQ, L=Minsk, O=EPAm Systems, LLC, OU=IT Department, CN=EPAm Root Enterprise CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7adfbc62eb638a00 DC=qualified-root-ca, CN=InfoNotary TSP Root, C=BG, L=Sofia, O=InfoNotary PLC, OU=Qualified TSP
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x81c7745c79190378 C=DE, ST=BW, L=REUTLINGEN, O=NMI, OU=IT, CN=�
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x992d6156a36dbf19 C=US, O=VeriSign, Inc., OU=Class 1 Public Primary Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x85e8c519851cc400 DC=grupo, DC=Clarkemodet, CN=Clarkemodet Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x28d5588cc9deb700 DC=com, DC=vattenfall, CN=Vattenfall Root Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd27f177930ef9e00 C=DE, O=PKI-1-Verwaltung, CN=PCA-1-Verwaltung-15
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x616aebab0ef7bd00 C=DE, O=mocon GmbH, CN=mocon CA, Email=mocon-ca@mocon.net
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x837b020b211ef700 DC=Local, DC=Isodraht, CN=Isodraht-RootCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x756975ee7ec5d200 C=US, ST=MO, L=Kansas City, O=Shook, Hardy & Bacon LLP, OU=SHB, CN=Secure-Server.SHB.COM, Email=secure-server@SHB.COM
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9a8faccc1b01c600 CN=Klueber Lubrication Muenchen KG - (root)
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9dc53bdad3cfe600 C=RS, O=Halcom a.d. Beograd
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xb71a9b1647b7ac00 C=DE, O=DATEV eG, CN=Root CA DATEV PE 01
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3dea0e2f4c8bd100 DC=com, DC=boschhuayu-steering, CN=boschhuayu-steering-BHSHV00176-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xcfb22061f662ac00 C=DK, O=TDC, CN=TDC OCES CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xdfbd114d7054bb00 C=DE, ST=Bavaria, L=Munich, O=EUROMARKPAT Germany, OU=EUROMARKPAT SecIT, CN=EUROMARKPAT SecIT eMail CA, Email=secit@euromarkpat.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x55fae0e1d374b600 DC=com, DC=hwhlaw, CN=HWHCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x860d75e3b7b2b500 CN=allenovery.com, O=Allen & Overy LLP, OU=IT, L=London, ST=London, C=GB, Email=ExchangeAdministration@allenovery.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9e70c3d31314ad00 O=Bayer, OU=BayerBBS, CN=Secure Mail CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x452b4252af9a200 C=de, L=Muenchen, O=m patent group, OU=Gateway, CN=mail.mpatent.eu
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x59f17834c348a000 C=US, O=Interplex Industries, CN=Interplex
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd806d8ad1c86b300 C=DE, ST=Bavaria, L=Erlangen, O=Ertec GmbH, CN=ertec CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd58314dee234c600 CN=SafeGuard MailGateway CA, OU=GLS IT Services, O=GLS, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6969109580eac100 C=DE, ST=Berlin, L=Berlin, O=KPMG AG, OU=KPMG IT Service GmbH, CN=KPMG DE SecurEmail CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x121a3d2944e3c700 DC=local, DC=lt, CN=lt-DC1-Root-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf7a487a26ce3af00 DC=local, DC=trplaw, CN=trplaw-TRP-FILE-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x86a1510b4b2eb600 DC=de, DC=al-h-Konzern, CN=KONZERN-ROOT
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x5b71fe4c3867b600 DC=local, DC=tracetronic, CN=TraceTronic-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc1c25865fe35bb00 C=DE, ST=Germany, O=Diehl BGT Defence GmbH & Co. KG, OU=IT-Services, CN=DBD SSL-Certificates, Email=ssl-certificates@diehl-bgt-defence.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xb308794a9320b100 CN=Bode Meitinger Patentanwalts GmbH, O=Bode Meitinger Patentanwalts GmbH, OU=IT, ST=Bayern, C=DE, L=München, Email=support@bodemeitinger.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe69db528a1cd9b00 C=DE, L=Sondershausen, O=Thermik Geraetebau GmbH, CN=Thermik Geraetebau GmbH CA, Email=info@thermik.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x30b278221c1ab700 CN=Experience One CA, O=Experience One AG, L=Stuttgart, ST=Baden Wuerttemberg, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xeba6e78eca88d700 CN=Goldberg Segalla Root Certificate Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8904ffff5a0a9658 C=de, L=Stuttgart, O=SCHOKOLADE Filmproduktion GmbH, OU=Gateway, CN=remote.schokolade.tv
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf48ab893c75aa200 CN=ELV-EQ-3 ROOT CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xfe348be439bf600 C=US, O=Intel Corporation, CN=Intel Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf6a60e29636ea400 CN=VJP MailGateway CA, OU=IT-Department, O=VJP Viering Jentschura & Partner, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8baadb92481ed500 DC=com, DC=musala, CN=MUSALA-ROOT-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc8e6dcd3a1798a00 DC=de, DC=strama, CN=StramaRootCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x58d75bf11243d000 CN=IB-Patent CA, O=IB-Patent.de, OU=IT, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xda25a49609f9c400 CN=SafeGuard MailGateway CA, OU=IT Security, O=Treuhand Oldenburg und Partner OHG, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xff4c17421d17b500 C=DE, O=DATEV eG, CN=CA DATEV BT 95
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6983f17458c8700 CN=CA.wnj.com, Email=postmaster@wnj.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xb3a885392ba8ce00 O=AREVA GROUP, CN=AREVA - ROOT CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x86cc1523ccec8f00 C=DE, ST=Baden-Wuerttemberg, L=Berg/Ravensburg, O=Otten, Roth, Dobler & Partner mbB, OU=IT, CN=CA ravenspat
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6f1ec7faae909800 C=BE, CN=Belgium Root CA4
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9f6399c00cedf600 DC=com, DC=vwg, DC=VWPKI, CN=VW-CA-ROOT-03
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x90af44962377a400 C=DE, O=TC TrustCenter GmbH, OU=TC TrustCenter Universal CA, CN=TC TrustCenter Universal CA I
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x884321a0a784c300 CN=HighTec EDV - Systeme GmbH, O=HighTec EDV-Systeme GmbH, ST=Saarland, C=DE, L=Saarbrücken, Email=info@hightec-rt.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xb3c52f6aaf75ae00 C=de, L=Bad Laasphe, O=Heinrich Wagner Sinto, OU=Gateway, CN=astaro.hws-intranet.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x255f878369f2c700 CN=SafeGuard MailGateway CA, OU=IT Services, O=Silver Atena GmbH, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9d1307aadf7fa000 CN=securemail.scanlab.de, Email=info@scanlab.de, OU=Team-IT, O=SCANLAB AG, L=Puchheim, ST=Bavaria, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf78a201ec532a700 DC=br, DC=com, DC=dannemann, CN=DSBIM
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf13766acc92ab000 DC=local, DC=jauch, CN=Jauch-Root-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xba60da459874ab00 C=DE, O=Fraunhofer SIT, CN=Volksverschluesselung Root CA G02
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe15f9e385ae2cc00 CN=Plasticard-ZFT; CA, O=Plasticard-ZFT GmbH; Dresden, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8336525ec231b400 C=DE, O=DGN Deutsches Gesundheitsnetz Service GmbH, CN=dgnservice Root 7:PN
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa7aeb3d7a287ec00 DC=hld, DC=root, CN=Schaeffler Group Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe968280ccf3db300 DC=de, DC=swm, DC=intra, CN=SWM Root CA V3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x65155de7e283d700 C=US, O=Fossa.me, CN=Fossa.me Root F1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd42f99b8abb6ba00 C=HU, ST=Tolna, L=Tolna, O=Fastron Hungaria Kft., CN=Fastron Hungaria Kft., Email=fastron@fastron.co.hu
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x82d7ff8fd00a800 CN=Oulun yliopisto root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa31a8e49827fa000 DC=LAN, DC=ONE4ALL, CN=ONE4ALL-QSCDEPKP001-CA-1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6de7a1b64e64a000 C=DE, O=Freistaat Bayern, CN=Bayern-Root-CA-2019
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x62738e40c250c000 CN=ROOTCA-SNEU
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x779a2935c5facc00 C=DE, L=Filderstadt, O=CSM GmbH, OU=Development, CN=CSM Root, Email=csmca@csm.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf265e19e1b3cc400 C=BG, ST=SOFIA, O=DPLF, OU=IT, CN=DPLF root CA, Email=it@dplawfirm.bg, CN=DPLF root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3c6968cc7276f000 C=DE, ST=BW, L=Mannheim, O=IB-Patent, OU=IB-Patent, CN=IB-Patent Root CA, Email=it@ib-patent.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc65be6ac9fde8200 DC=se, DC=components, CN=Precomp Solutions CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xcd904ba7d5ebd300 CN=pix.lsg-law.de, OU=Gateway, O=Kanzlei Lorenz Seidler Gossel, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x509b00fab782d700 C=DE, ST=Baden Wuerttemberg, L=Bad Saulgau, O=OSW Technische Dokumentation Verlag GmbH, CN=CA-OSW-ROOT, Email=administrator@osw-doku.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6d30f2b73249f00 DC=com, DC=vwg, DC=VWPKI, CN=VW-CA-ROOT-05
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x33b8a6235b3da300 C=DE, ST=Hessen, L=Neu-Isenburg, O=Lufthansa AirPlus Servicekarten GmbH, OU=Lufthansa AirPlus Servicekarten GmbH, CN=Lufthansa AirPlus Servicekarten GmbH - MailRootCA, Email=security@airplus.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa24cde50eb3fb500 DC=sb, DC=compa, CN=compa-W2K8-DC-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4f639cc1e62eba00 CN=bcg.com, O=The Boston Consulting Group, OU=Global Services, L=Boston, ST=MA, C=US, Email=WWITSecurity@bcg.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf08d55c3eb36d000 CN=Bosch BKK Secure E-Mail CA, OU=IT, O=Bosch BKK, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe18fa87c2de7b900 DC=de, DC=secoit, CN=SECOIT Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xcbaeb56713729700 C=BM, O=QuoVadis Limited, OU=Root Certification Authority, CN=QuoVadis No Reliance Root CA G2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x59ee8ca0d29e8d00 DC=local, DC=eurofins, DC=area2, DC=germany, CN=Eurofins Germany CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe0da7c1f6603db00 C=HU, ST=Budapest, L=Budapest, O=SBGK, CN=SBGK, Email=CAadmin@sbgk.hu
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x35f6a0f537c7cf00 DC=local, DC=infopulse, CN=Infopulse RootCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7c151838d487c000 CN=Questel Root Certificate Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6b4b81c1ae499200 L=Hamburg, O=BCD Travel Germany GmbH, CN=BCD Travel RootCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x748c3518bb8c9a00 C=DE, O=Bundesagentur fuer Arbeit, CN=BA-Class-1-Root-CA-3:PN
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7df5f7834ead00 C=DE, ST=Bayern, L=Hammerbach, O=Ingenieurbüro Peter Pöltl, CN=Ingenieurbüro Peter Pöltl CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x977eded6c63afb9 C=DE, O=SAP-AG, CN=SSO_CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xaab16455e04c8c00 DC=LOCAL, DC=IAVGROUP, CN=IAV-Root-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1198766b77bcb600 C=DE, ST=BW, L=Reutlingen, O=KB, OU=ID, CN=Kittelberger CA, Email=sysadmin@kittelberger.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9f6ab4d68c44ef00 C=BG, ST=SOFIA, O=AFA, OU=IT, CN=AFA MAIL, Email=it@afa.bg, CN=AFA MAIL
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6dd12900ed90c900 CN=firewall.dom.local, OU=Gateway, O=Cadilac Laser GmbH, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x860d75e3b7b2b500 CN=allenovery.com, O=Allen & Overy LLP, OU=IT, L=London, ST=London, C=GB, Email=ExchangeAdministration@allenovery.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa78117e63d3cd000 C=DE, ST=Bavaria, L=Munich, O=EUROMARKPAT Germany, OU=EUROMARKPAT SecIT, CN=EUROMARKPAT SecIT eMail CA, Email=secit@euromarkpat.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1c97986f8efcb600 C=DE, ST=BY, O=IC/ONE GmbH, CN=CA IC1, Email=ca@ic-one.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7fce8009e43fce00 CN=Zert.-Instanz von Plasticard-ZFT, O=Plasticard-ZFT GmbH, C=DE, L=Dresden, Email=trust@plasticard.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8f361fc631858d00 DC=tw, DC=com, DC=dinkle, DC=tw, CN=tw-DC02-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xccc0d9c0cde8b900 DC=netz, DC=hbw, CN=HBW-CA1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbb6e19f43fdcce00 C=PT, O=MULTICERT - Serviços de Certificação Electrónica S.A., CN=MULTICERT Root Certification Authority 01
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x13babfadbd66e400 C=CA, ST=Ontario, L=Toronto, O=McMillan LLP, OU=Information Systems, CN=McMillan-ESA-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbd8e3d30ddfa8f00 C=local, O=stww2k, CN=Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x13d9962ef116e300 CN=SafeGuard MailGateway CA, O=jhcn, C=net
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x80b48fb827fec700 O=Bayer Group, OU=Bayer Business Services, CN=Bayer Group Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xad1b41cafce4cc00 C=DE, O=mVISE AG, CN=mVISE AG Root R1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x691bfdb44d4cb100 C=DE, O=PKI-1-Verwaltung, CN=PCA-1-Verwaltung-11
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xba2d2ca8dc6dd100 DC=local, DC=fritsch, CN=Moritz
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe104185c08e2d500 C=IT, ST=Monza e Brianza, L=Agrate Brianza, O=STMicroelectronics, OU=APG Bosch Prod Eng Group, CN=STM
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x23335b995a1fb800 C=DE, O=CMS Hasche Sigle, CN=CMS HS Secure Mail CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x82586bf13a2c9500 DC=local, DC=cirosec, CN=cirosec Root CA 01
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2b9c7698abb0c900 C=DE, O=ZF Friedrichshafen AG, CN=ZF E-Mail Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6ad7de9ce873b500 DC=local, DC=aat, CN=AAT-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x792ddfb3206ae800 C=SI, O=Kolektor Group, CN=Kolektor SHA2 Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2f5346bc81cdb200 C=DE, O=Bundesagentur fuer Arbeit, CN=BA-Class-1-Root-CA-2:PN
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4ed527554493e800 DC=local, DC=eurotec, CN=eurotec-EUDC-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd78e86b2bf20f578 DC=com, DC=Ford, CN=Device Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xaf28b446e07ae00 C=DE, O=Kern-Liebers, CN=KLCA-ROOT
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x486dd65566b5d500 CN=SafeGuard MailGateway CA, OU=IT, O=Simon Hegele GmbH, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xfc0dafc9d81bcc00 Email=ca@umsystem.edu, C=US, ST=Missouri, L=Columbia, O=University of Missouri, OU=Information Technology, CN=University of Missouri Root Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3b0a0abd06d69500 DC=DE, DC=BTMT, CN=BTMT-GmbH-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x19d6d400d706dd00 C=DE, O=DATEV eG, CN=CA DATEV EM 02
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x5f1ffe6f2bc5ab00 C=DE, O=RWE, CN=RWE Corporate Root CA, OU=RWE Basis PKI
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x667de70faf84bf00 C=DE, ST=BW, L=Stuttgart, O=B&W Engineering und Datensysteme GmbH, CN=BuW_Engineering-CA, Email=support@buw-eng.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x127888e4dbe7e600 CN=ABLE Root CA 1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xca76c8579b3eb700 DC=de, DC=smartest-net, CN=mail.smartest-net.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa80f7aaca16eab00 DC=de, DC=horvath, CN=HORVATHROOTCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xdfc09ce0a380ab00 DC=com, DC=goldbergsegalla, CN=goldbergsegalla-BUFECA01-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf5394a718b5bd300 DC=de, DC=tara-systems, O=TARA Systems GmbH, OU=TARA Systems Root CA, CN=TARA Systems Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3681dc8b8eadb500 ST=Baden-Wuerttemberg, L=Stuttgart, O=Daimler AG, CN=Daimler AG - SecureMail CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa30f97bee70dbe00 C=DE, ST=Baden-Wuerttemberg, L=Stuttgart, O=Dr. Ing. h.c. F. Porsche AG, OU=PIKS Postmaster-Team, CN=Porsche E-Mail CA, Email=postmaster-team@porsche.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x365c4c802214ae00 CN=TW, O=Towers Watson, OU=Security Solutions, L=Philadelphia, ST=Pennsylvania, C=US, Email=TW.IT.Security.Solutions@towerswatson.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x46efc1c36c31e200 CN=StampIT Global Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x36e40d6ba6b3cd00 C=SI, O=Hidria, CN=Hidria Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd2056530264f9c00 O=ZF, OU=ZF IT, CN=ZF Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x99add4a1a4c6ea00 C=ES, ST=MADRID, L=MADRID, OU=see current address at www.camerfirma.com/address, OU=CHAMBERS OF COMMERCE ROOT - 2016, SRN=A82743287
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4f69dfa79af4be00 C=DE, ST=Saxony, L=Lauta, O=Programmierbare Logik & Systeme GmbH, OU=CA, CN=CA Programmierbare Logik & Systeme GmbH v2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x38c36b5a7d1ec100 C=DE, O=Deutsche Rentenversicherung, OU=NQ Root CA, CN=DRV Root CA 2018a
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x907a994ceacbbd00 C=DE, O=Finanz Informatik, OU=PKI, CN=Finanz Informatik Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc623decd2c6ba300 DC=com, DC=meelogic, DC=ad, CN=ad-SVW0021-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4d5e2d8f961bb400 CN=securemail, O=Elektrobit Automotive GmbH, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8c0301f6579ea200 C=AT, O=Toveno, CN=Toveno, Email=Certification.Authority@toveno.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4db48fe4e752dd00 DC=de, DC=cetecom, CN=cetecom-DCESSEN01-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xef2d8ff062c0e000 C=DE, O=DATEV eG, CN=Root CA DATEV PE 02
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xb5d0f64b5974b400 DC=net, DC=pj-technologies, DC=ad, CN=FPJ-DC-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa2a786fee7fdb100 C=DE, O=DATEV eG, CN=CA DATEV STD 97
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x69bbb8bb2b1fcd00 C=DE, O=TUV Rheinland Group, CN=TUV ROOT CA 2009
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6956dde4ea49a600 CN=ParkerHannifin
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7a8459535ec2d000 C=DE, L=65795 Hattersheim, O=GWK Gesellschaft fuer Informationstechnologie mbH, CN=GWK Gesellschaft fuer Informationstechnologie mbH, Email=b.weber@gwk-gmbh.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x715b6494b0d4d769 C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting, OU=Certification Services Division, CN=Thawte Personal Freemail CA, Email=personal-freemail@thawte.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xea9fa225a95ec200 CN=PATEC-Offline-Root-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf2aa891a83afb800 CN=Volvo Group Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xba18f6692cf5de00 C=DE, O=RWE, OU=RWE Basis PKI, CN=RWE Root CA Corporate 2007
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc427a9f810dac800 C=TN, CN=Tunisian Root Certificate Authority - TunRootCA1, O=National Digital Certification Agency
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7aa4257195d6c100 DC=com, DC=smbtrials, CN=smbtrials-SMB-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7605945cb1ecb700 C=DE, ST=NRW, L=Dusseldorf, O=Renesas Electronics Europe, CN=Renesas Electronics
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xde5380a002e4d000 C=DE, L=Pforzheim, O=Strohheker Kunststoffteile und Metallwaren GmbH, CN=STROHHEKERGRUPPE-ROOT-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x767c9a5880e0bd00 CN=GateD, OU=Gateway, O=IMS Gear GmbH, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x609a04529adcdf00 DC=cn, DC=ntd, CN=NTD-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7f477cde34e7c600 CN=Stadtverwaltung Offenbach am Main E-Mail CA, L=Berliner Strasse 100 63065 Offenbach am Main, ST=Hessen, C=DE, Email=informationstechnik@offenbach.de, O=Stadtverwaltung Offenbach am Main, OU=Hauptamt IuK
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe8dce1a9802acd00 CN=Softdevelop.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8ec32033407fbe00 CN=SERCA-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4b20f4c38330bb00 C=DE, ST=Saarland, L=St. Ingbert, O=iMAR, OU=Certificate Authority, CN=iMAR GmbH, Email=admin@imar-navigation.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc2ce8c3c0283be00 CN=DATAGROUP Email CA, OU=IT, O=DATAGROUP IT Services Holding AG, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa2f3ffee16b5bc00 DC=hk, DC=com, DC=wih, CN=Wongs
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x17296a3c4890a300 C=US, ST=Washington, L=Seattle, O=getaCert - www.getacert.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe1865f32cf35ce00 CN=ALTRAN-ROOT-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xec7d46e2c022ce00 O=Root CA, OU=http://www.cacert.org, CN=CA Cert Signing Authority, Email=support@cacert.org
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe6180e20c4a8d100 Email=Eduard.Soellner@wolf-woelfel.de, C=DE, ST=Bayern, L=Georgensgmuend, O=Wolf + Woelfel GmbH, OU=Georgensgmuend, CN=wolf-woelfel.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x53b2849c08f3cc00 DC=de, DC=vrndstedt, CN=DUS-CERT01-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf4954a8eeb62a500 CN=CONNECT-ROOT-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2a244a1cb717d800 C=CH, O=WISeKey, OU=OISTE Foundation Endorsed, CN=OISTE WISeKey Global Root GB CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x22f0875e3e67f000 DC=de, DC=sinc-intern, CN=sinccert
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe516a16f4689e400 DC=com, DC=vattenfall, CN=Vattenfall Root CA 2017
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc0b4d327bf45ca00 DC=local, DC=Sitronic, CN=Sitronic-Zert
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe2f6e0c655f6ac00 CN=SafeGuard MailGateway CA, OU=IT-ADMINISTRATION, O=KNH PATENTANWAELTE, C=de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x25ff25c6fc0aaa00 DC=de, DC=salt-solutions, CN=SWUCERTAUTH1-CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x69b8234cc738c600 C=HU, ST=Budapest, L=Budapest, O=settlersroot, OU=settlersroot, CN=settlersroot.hu, Email=sadmin@settlers.hu
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc1f25807d35fb600 DC=com, DC=etfsinc, CN=etfs-ca
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa85dc1884f37a700 C=DE, L=Reutlingen, O=Reutlingen University, OU=rbz, CN=rbz_CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x9e3b1eb232f19400 C=CA, O=Royal Bank of Canada - Banque Royale du Canada, OU=Royal Bank of Canada Root CA-AC Centrale Banque Royale du Canada
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7d690f4bdebded00 O=Alliance, CN=Alliance Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x96a3ea35a424a700 CN=Airbus Root PKI CA, L=(none), OU=AIRBUS, O=EADS
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x5ef417bf307c800 C=DE, ST=Baden-Wuerttemberg, L=Stuttgart, O=Robert-Bosch-Krankenhaus GmbH, CN=RBK RCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xea5ef130d8e2bb00 CN=mckinsey.com, O=McKinsey & Company, OU=mckinsey.com, Email=administrators@mckinsey.com
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x94b602d1603b100 CN=sxmailcrypt, Email=kanzlei@liedtke-patent.de, OU=Support, O=Liedtke & Partner, L=Erfurt, ST=Thueringen, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf747e24cb1d1de00 C=KR, ST=Radius, L=Somewhere, O=ASE Korea, Inc., Email=dwlim@asekr.com, CN=ASEKR CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xcc9d696163739a00 CN=Root CA 1:PN, OU=Zertifizierungsstelle, O=Bundesnotarkammer, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe84e71681e4da900 DC=local, DC=mbf-firm, CN=MichaelBestRootCA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2527e574c910c300 C=DE, L=65795 Hattersheim, O=for you Insurance Services GmbH, OU=Internet Operations, CN=for you Insurance Services Root CA, Email=bernd.weber@for-you.insuranceservices.de
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x2ca429a5c4c6a700 C=IT, L=Milan, O=Actalis S.p.A./03358520967, CN=Actalis Authentication Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3d993fde1950a700 C=US, O=IdenTrust, CN=IdenTrust Commercial Root CA 1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6b7bdc34cd37bb00 C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x57ba5395b561bf00 C=BM, O=QuoVadis Limited, OU=Root Certification Authority, CN=QuoVadis Root Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe248b7eeee4af00 C=CH, O=SwissSign AG, CN=SwissSign Gold CA - G2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x780679907625cc00 OU=GlobalSign Root CA - R3, O=GlobalSign, CN=GlobalSign
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3d98ab22bb04a300 C=IE, O=Baltimore, OU=CyberTrust, CN=Baltimore CyberTrust Root
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xeae16ef49d40be00 C=GB, ST=Greater Manchester, L=Salford, O=Comodo CA Limited, CN=AAA Certificate Services
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xea33d3c14ab5d900 C=DE, ST=Baden-Wuerttemberg (BW), L=Stuttgart, O=Deutscher Sparkassen Verlag GmbH, CN=S-TRUST Authentication and Encryption Root CA 2005:PN
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xbab415bd1e249800 C=US, OU=www.xrampsecurity.com, O=XRamp Security Services Inc, CN=XRamp Global Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd60940f5f643b400 DC=com, DC=Bosch, CN=PKI, CN=BoschCA-DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa3ce8d99e60eda00 C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x560ad29254e89100 C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO RSA Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x67db7cef8732e500 C=DE, O=DATEV eG, CN=CA DATEV STD 02
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x1aa17632bdf2e900
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xda5f1cc8fc5ca000 C=CZ, O=Česká pošta, s.p. [IČ 47114983], CN=PostSignum Root QCA 2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3178d37f87f1c400 C=CH, O=SwissSign AG, CN=SwissSign Silver CA - G2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6ae028812741ae00 C=DE, ST=Bavaria, L=Munich, O=BSH Hausgeraete GmbH , CN=BSH Root Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd45980fbf0a0ac00 C=US, O=thawte, Inc., OU=Certification Services Division, OU=(c) 2006 thawte, Inc. - For authorized use only, CN=thawte Primary Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x94fb3f125608a800 C=CZ, CN=I.CA - Standard Certification Authority, 09/2009, O=První certifikační autorita, a.s., OU=I.CA - Provider of Certification Services
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc9edb72b684ba00 C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2009 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - G2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x298be035a30bab00 C=DE, O=Deutsche Telekom AG, OU=T-TeleSec Trust Center, CN=Deutsche Telekom Root CA 2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3466b0ef7b84a400 C=DE, ST=Bavaria, L=Munich, O=BSH Hausgeraete GmbH , CN=BSH Root Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x65c5f0f45f02c200 DC=net, DC=ZF-Lenksysteme, OU=PKI, CN=ZFLS-CA-DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xce3493bee81cce00 C=BR, O=ICP-Brasil, OU=Instituto Nacional de Tecnologia da Informacao - ITI, CN=Autoridade Certificadora Raiz Brasileira v1
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xec1f8292427bc400 C=DE, O=D-Trust GmbH, CN=D-TRUST Root CA 3 2013
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x7c4fd32ec1b1ce00 C=PL, O=Unizeto Sp. z o.o., CN=Certum CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xdb2cd5c20d0aaf00 C=US, O=VeriSign, Inc., OU=VeriSign Trust Network, OU=(c) 1999 VeriSign, Inc. - For authorized use only, CN=VeriSign Class 2 Public Primary Certification Authority - G3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xd4fbe673e5ccc600 C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert High Assurance EV Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x363d9b00b34fcb00 C=CH, O=WISeKey, OU=Copyright (c) 2005, OU=OISTE Foundation Endorsed, CN=OISTE WISeKey Global Root GA CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x73e85f1bda5faa00 C=DE, O=T-Systems Enterprise Services GmbH, OU=T-Systems Trust Center, CN=T-TeleSec GlobalRoot Class 2
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x99a96449d739c700 C=US, O=Symantec Corporation, OU=Symantec Trust Network, CN=Symantec Class 1 Public Primary Certification Authority - G6
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xb28612a94b4dad00 O=Entrust.net, OU=www.entrust.net/CPS_2048 incorp. by ref. (limits liab.), OU=(c) 1999 Entrust.net Limited, CN=Entrust.net Certification Authority (2048)
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf8491584e4cdb300 C=DE, O=D-Trust GmbH, CN=D-TRUST Root Class 2 CA 2007
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xea8e67100ecbb300 C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 3 G3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8563c805e9cccd00 C=US, O=Symantec Corporation, OU=Symantec Trust Network, CN=Symantec Class 2 Public Primary Certification Authority - G6
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x64acc0b265e5b000 C=si, O=state-institutions, OU=sigen-ca
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x466cbc09db88c100 C=IL, O=StartCom Ltd., OU=Secure Digital Certificate Signing, CN=StartCom Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x91a085eefe26df00 C=DE, O=DATEV eG, CN=CA DATEV BT 03
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x30e0c22d9ccbd300 C=SI, O=Republika Slovenija
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe8985fec4712d200 C=AT, L=Vienna, ST=Austria, O=ARGE DATEN - Austrian Society for Data Protection, OU=GLOBALTRUST Certification Service, CN=GLOBALTRUST, Email=info@globaltrust.info
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x67a526528cfbe400 C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-Root-05, CN=A-Trust-Root-05
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x3b2a6f973b859500 CN=Atos TrustedRoot 2011, O=Atos, C=DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc30e361765128000 C=US, ST=New Jersey, L=Jersey City, O=The USERTRUST Network, CN=USERTrust RSA Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x4297e24fc722b300 C=ES, O=Agencia Catalana de Certificacio (NIF Q-0801176-I), OU=Serveis Publics de Certificacio, OU=Vegeu https://www.catcert.net/verarrel (c)03, OU=Jerarquia Entitats de Certificacio Catalanes, CN=EC-ACC
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x16921f393194ce00 C=DE, O=DATEV eG, CN=CA DATEV STD 03
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x491857ead79dde00 C=US, O=The Go Daddy Group, Inc., OU=Go Daddy Class 2 Certification Authority
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa7f9b4b9d484dd00 C=US, O=VeriSign, Inc., OU=VeriSign Trust Network, OU=(c) 1999 VeriSign, Inc. - For authorized use only, CN=VeriSign Class 1 Public Primary Certification Authority - G3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xe69c54164257cc00 C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf2e98e1050bea000 C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 1 G3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xa9bab0af360cc000 DC=com, DC=Bosch, CN=PKI, CN=Bosch-CA-DE
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xc2ba72a37dfbe300 C=PL, O=Unizeto Technologies S.A., OU=Certum Certification Authority, CN=Certum Trusted Network CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x6d4bbe735e24c400 C=HU, L=Budapest, O=NetLock Kft., OU=Tanúsítványkiadók (Certification Services), CN=NetLock Arany (Class Gold) Főtanúsítvány
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x8043e4ce150ead00 C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root CA
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0x331d58625ee2dc00 C=US, O=GeoTrust Inc., OU=(c) 2008 GeoTrust Inc. - For authorized use only, CN=GeoTrust Primary Certification Authority - G3
2a58.348c: supR3HardenedWinIsDesiredRootCA: Adding 0xf2e6331af7b700 C=SE, O=AddTrust AB, OU=AddTrust External TTP Network, CN=AddTrust External CA Root
2a58.348c: supR3HardenedWinRetrieveTrustedRootCAs: cAdded=442
2a58.348c: SUPR3HardenedMain: Load Runtime...
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll: Signature #1/2: info status: 24202
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcp100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'rpcrt4.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'ws2_32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ws2_32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ws2_32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ws2_32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #26 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\ws2_32.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\ws2_32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll: Signature #1/2: info status: 24202
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll: Signature #1/2: info status: 24202
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll: Signature #1/2: info status: 24202
2a58.348c: Detected WinVerifyTrust recursion: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll) WinVerifyTrust
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxRT.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000a01:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 000000006a820000 LB 0x000d2000 C:\Program Files\Oracle\VirtualBox\MSVCR100.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 000000006ab90000 LB 0x00098000 C:\Program Files\Oracle\VirtualBox\MSVCP100.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6b580000 LB 0x0006b000 C:\WINDOWS\System32\WS2_32.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ws2_32.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe09cd0000 LB 0x005e0000 C:\Program Files\Oracle\VirtualBox\VBoxRT.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxRT.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxRT.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxRT.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxRT.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxRT.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxRT.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxRT.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxRT.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxRT.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09cd0000 'C:\Program Files\Oracle\VirtualBox\VBoxRT.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 24202) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wintrust.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\Wintrust.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a720000 'C:\WINDOWS\system32\Wintrust.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\system32\crypt32.dll'
2a58.348c: SUPR3HardenedMain: Load TrustedMain...
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.dll: Signature #1/2: info status: 24202
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'opengl32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'uicommon.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'vboxrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'msvcp100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'qt5corevbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'qt5guivbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'qt5widgetsvbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'qt5openglvbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #10 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #11 'ole32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #12 'oleaut32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #13 'winmm.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'winmm.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'winmm.dll' -> '\Device\HarddiskVolume3\Windows\System32\winmm.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcrt.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\winmm.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\winmm.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #21 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\oleaut32.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\oleaut32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'combase.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'combase.dll' -> '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rcNtRedir=0xc0150008]
2a58.348c: Detected WinVerifyTrust recursion: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\combase.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\combase.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp_win.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp_win.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rcNtRedir=0xc0150008]
2a58.348c: Detected WinVerifyTrust recursion: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\crypt32.dll (Input=crypt32.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #21 'rpcrt4.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #49 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #50 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #51 'combase.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\ole32.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\ole32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'combase.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'combase.dll' -> '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\combase.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: Detected WinVerifyTrust recursion: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #37 'gdi32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\user32.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\user32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: Detected WinVerifyTrust recursion: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #9 'win32u.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\gdi32.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\gdi32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'win32u.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'win32u.dll' -> '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rcNtRedir=0xc0150008]
2a58.348c: Detected WinVerifyTrust recursion: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: '\Device\HarddiskVolume3\Windows\System32\win32u.dll' has no imports
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\win32u.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\win32u.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'win32u.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'win32u.dll' -> '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\win32u.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #37 'gdi32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\user32.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5openglvbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5openglvbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5openglvbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5OpenGLVBox.dll: Signature #1/2: info status: 24202
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'win32u.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'win32u.dll' -> '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\win32u.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'qt5widgetsvbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'qt5guivbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'qt5corevbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'msvcr100.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5OpenGLVBox.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5OpenGLVBox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5widgetsvbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5widgetsvbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5widgetsvbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll: Signature #1/2: info status: 24202
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5corevbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5corevbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5corevbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll: Signature #1/2: info status: 24202
2a58.348c: Detected WinVerifyTrust recursion: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'ole32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'advapi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'ws2_32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'msvcp100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'msvcr100.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5guivbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5guivbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5guivbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll: Signature #1/2: info status: 24202
2a58.348c: Detected WinVerifyTrust recursion: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'ole32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'opengl32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'qt5corevbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'msvcp100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'msvcr100.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5widgetsvbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5widgetsvbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5widgetsvbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll: Signature #1/2: info status: 24202
2a58.348c: Detected WinVerifyTrust recursion: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'qt5guivbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'qt5corevbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'msvcp100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'msvcr100.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 24202 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shell32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'shell32.dll' -> '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rcNtRedir=0xc0150008]
2a58.348c: Detected WinVerifyTrust recursion: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #72 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #74 'gdi32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\shell32.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\shell32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5corevbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5corevbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5corevbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5guivbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5guivbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5guivbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5corevbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5corevbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5corevbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'opengl32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'opengl32.dll' -> '\Device\HarddiskVolume3\Windows\System32\opengl32.dll' [rcNtRedir=0xc0150008]
2a58.348c: Detected WinVerifyTrust recursion: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\opengl32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'advapi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'glu32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 22900 (\Device\HarddiskVolume3\Windows\System32\opengl32.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\opengl32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ole32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'mpr.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'mpr.dll' -> '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rcNtRedir=0xc0150008]
2a58.348c: Detected WinVerifyTrust recursion: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\mpr.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\mpr.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ws2_32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ws2_32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ws2_32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ws2_32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\advapi32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ole32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shell32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'shell32.dll' -> '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shell32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'glu32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'glu32.dll' -> '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rcNtRedir=0xc0150008]
2a58.348c: Detected WinVerifyTrust recursion: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'opengl32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 22900 (\Device\HarddiskVolume3\Windows\System32\glu32.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\glu32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\advapi32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp_win.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp_win.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'opengl32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'opengl32.dll' -> '\Device\HarddiskVolume3\Windows\System32\opengl32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 22900 (0x5974)) on \Device\HarddiskVolume3\Windows\System32\opengl32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'qt5guivbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'qt5corevbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'msvcp100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'msvcr100.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5guivbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5guivbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5guivbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll [redoing WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shell32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'shell32.dll' -> '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shell32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5corevbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5corevbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5corevbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5guivbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5guivbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5guivbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/Imports: 0 (was 24202) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5corevbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5corevbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5corevbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll [redoing WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/Imports: 0 (was 24202) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'uicommon.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'uicommon.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\uicommon.dll' [rcNtRedir=0xc0150008]
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\UICommon.dll: Signature #1/2: info status: 24202
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'vboxrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcr100.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'qt5corevbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'qt5guivbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'qt5widgetsvbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'advapi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'ole32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #9 'oleaut32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #10 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\UICommon.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\UICommon.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'opengl32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'opengl32.dll' -> '\Device\HarddiskVolume3\Windows\System32\opengl32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 22900 (0x5974)) on \Device\HarddiskVolume3\Windows\System32\opengl32.dll [redoing WinVerifyTrust]
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000494 pwszName=\Device\HarddiskVolume3\Windows\System32\opengl32.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=B4171C0BCE32E15678A635F6C1468B16A3DEDB0C
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\oleaut32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ole32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\advapi32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5widgetsvbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5widgetsvbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5widgetsvbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5guivbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5guivbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5guivbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5corevbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5corevbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5corevbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Features-Package0312~31bf3856ad364e35~amd64~~10.0.19041.1806.cat'; file='\Device\HarddiskVolume3\Windows\System32\opengl32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedScreenImage/Imports: 0 (was 22900) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\opengl32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VirtualBoxVM.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000a01:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\opengl32.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\UICommon.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5OpenGLVBox.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\winmm.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (Unknown Status 22900 (0x5974)) on \Device\HarddiskVolume3\Windows\System32\glu32.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\mpr.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a790000 LB 0x00022000 C:\WINDOWS\System32\win32u.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\win32u.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a7c0000 LB 0x0009d000 C:\WINDOWS\System32\msvcp_win.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a5e0000 LB 0x0010b000 C:\WINDOWS\System32\gdi32full.dll [fFlags=0x0]
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #33 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #35 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #36 'win32u.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\gdi32full.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\gdi32full.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6bae0000 LB 0x0002a000 C:\WINDOWS\System32\GDI32.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6bc50000 LB 0x001a0000 C:\WINDOWS\System32\USER32.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6b720000 LB 0x00354000 C:\WINDOWS\System32\combase.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\combase.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe3b1a0000 LB 0x0002c000 C:\WINDOWS\SYSTEM32\GLU32.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (Unknown Status 22900 (0x5974)) on \Device\HarddiskVolume3\Windows\System32\glu32.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe30cd0000 LB 0x00127000 C:\WINDOWS\SYSTEM32\OPENGL32.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\opengl32.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6be40000 LB 0x00744000 C:\WINDOWS\System32\SHELL32.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shell32.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6b5f0000 LB 0x0012a000 C:\WINDOWS\System32\ole32.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ole32.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe41b80000 LB 0x0001d000 C:\WINDOWS\SYSTEM32\MPR.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\mpr.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 000000006a2b0000 LB 0x00565000 C:\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe096d0000 LB 0x005f7000 C:\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 0000000069d40000 LB 0x00561000 C:\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (Unknown Status 24202 (0x5e8a)) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6b380000 LB 0x000cd000 C:\WINDOWS\System32\OLEAUT32.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\oleaut32.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe03bb0000 LB 0x02316000 C:\Program Files\Oracle\VirtualBox\UICommon.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\UICommon.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 000000006aa60000 LB 0x00054000 C:\Program Files\Oracle\VirtualBox\Qt5OpenGLVBox.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5OpenGLVBox.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe5e6e0000 LB 0x00027000 C:\WINDOWS\SYSTEM32\WINMM.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\winmm.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe1edf0000 LB 0x001c8000 C:\Program Files\Oracle\VirtualBox\VirtualBoxVM.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VirtualBoxVM.dll
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\kernel32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'win32u.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'win32u.dll' -> '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\win32u.dll [redoing WinVerifyTrust]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedScreenImage/Imports: WinVerifyTrust not available, rescheduling \Device\HarddiskVolume3\Windows\System32\win32u.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [redoing WinVerifyTrust]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedScreenImage/Imports: WinVerifyTrust not available, rescheduling \Device\HarddiskVolume3\Windows\System32\user32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll [redoing WinVerifyTrust]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedScreenImage/Imports: WinVerifyTrust not available, rescheduling \Device\HarddiskVolume3\Windows\System32\gdi32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp_win.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp_win.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll [redoing WinVerifyTrust]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedScreenImage/Imports: WinVerifyTrust not available, rescheduling \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\kernel32.dll (Input=kernel32, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6c8b0000 'C:\WINDOWS\System32\kernel32.dll'
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-string-l1-1-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-string-l1-1-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-string-l1-1-0'
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-datetime-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-datetime-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-datetime-l1-1-1'
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-localization-obsolete-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-localization-obsolete-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-localization-obsolete-l1-2-0'
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\imm32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #25 'win32u.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\imm32.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\imm32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'win32u.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'win32u.dll' -> '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\win32u.dll [redoing WinVerifyTrust]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedScreenImage/Imports: WinVerifyTrust not available, rescheduling \Device\HarddiskVolume3\Windows\System32\win32u.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll [redoing WinVerifyTrust]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedScreenImage/Imports: WinVerifyTrust not available, rescheduling \Device\HarddiskVolume3\Windows\System32\user32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\IMM32.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000009:<flags> [calling]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6bdf0000 LB 0x00030000 C:\WINDOWS\System32\IMM32.DLL [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\imm32.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6bdf0000 'C:\WINDOWS\system32\IMM32.DLL'
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\imm32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\imm32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\imm32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\imm32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\advapi32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\ADVAPI32.DLL (Input=ADVAPI32.DLL, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6bba0000 'C:\WINDOWS\System32\ADVAPI32.DLL'
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\imm32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\imm32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 22900 (0x5974) '\Device\HarddiskVolume3\Windows\System32\glu32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 22900 (was 22900) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\mpr.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=Unknown Status 24202 (0x5e8a) '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 24202 (was 24202) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rescheduled]
2a58.348c: Detected loader lock ownership: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=0 for '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rescheduled]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe1edf0000 'C:\Program Files\Oracle\VirtualBox\VirtualBoxVM.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\imm32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\gdi32full.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000498 pwszName=\Device\HarddiskVolume3\Windows\System32\glu32.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=8DD21BB0BC55257A0C778F7A2D24BA87D12879DB
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Features-Package0312~31bf3856ad364e35~amd64~~10.0.19041.1806.cat'; file='\Device\HarddiskVolume3\Windows\System32\glu32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 22900) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\glu32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\mpr.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\shell32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 24202) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5WidgetsVBox.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\win32u.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\gdi32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\user32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\combase.dll'
2a58.348c: SUPR3HardenedMain: Calling TrustedMain (00007ffe1edf16c0)...
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #32 'combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #33 'msvcp_win.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #35 'wldp.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\windows.storage.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\windows.storage.dll
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\wldp.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\wldp.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe69bb0000 LB 0x00030000 C:\WINDOWS\SYSTEM32\Wldp.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wldp.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe681c0000 LB 0x00794000 C:\WINDOWS\SYSTEM32\windows.storage.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\windows.storage.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6c970000 LB 0x000ad000 C:\WINDOWS\System32\SHCORE.dll [fFlags=0x0]
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #42 'combase.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\SHCore.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\SHCore.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6ba80000 LB 0x00055000 C:\WINDOWS\System32\shlwapi.dll [fFlags=0x0]
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcrt.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\shlwapi.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\shlwapi.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'combase.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'combase.dll' -> '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\combase.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'wldp.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'wldp.dll' -> '\Device\HarddiskVolume3\Windows\System32\wldp.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wldp.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp_win.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp_win.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'combase.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'combase.dll' -> '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\combase.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\shlwapi.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\SHCore.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\wldp.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\windows.storage.dll'
2a58.348c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\platforms\qwindows.dll: Signature #1/2: info status: 24202
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'ole32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'imm32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'winmm.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'oleaut32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'advapi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'qt5guivbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #9 'qt5corevbox.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #10 'msvcr100.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\platforms\qwindows.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\platforms\qwindows.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5corevbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5corevbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5corevbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5CoreVBox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'qt5guivbox.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'qt5guivbox.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\qt5guivbox.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\Qt5GuiVBox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\advapi32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shell32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'shell32.dll' -> '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shell32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\oleaut32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'winmm.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'winmm.dll' -> '\Device\HarddiskVolume3\Windows\System32\winmm.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\winmm.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'imm32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'imm32.dll' -> '\Device\HarddiskVolume3\Windows\System32\imm32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\imm32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ole32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\platforms\qwindows.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\platforms\qwindows.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe175b0000 LB 0x0012e000 C:\Program Files\Oracle\VirtualBox\platforms\qwindows.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\platforms\qwindows.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe175b0000 'C:\Program Files\Oracle\VirtualBox\platforms\qwindows.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\kernel.appcore.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\kernel.appcore.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe68970000 LB 0x00012000 C:\WINDOWS\SYSTEM32\kernel.appcore.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\kernel.appcore.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\kernel.appcore.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000600 pwszName=\Device\HarddiskVolume3\Windows\System32\uxtheme.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=701BFCEE1A399A1718E6AD19A8B89B9E45D98837
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package05113~31bf3856ad364e35~amd64~~10.0.19041.1826.cat'; file='\Device\HarddiskVolume3\Windows\System32\uxtheme.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #33 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #34 'user32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\uxtheme.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\uxtheme.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\uxtheme.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000009:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\uxtheme.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe677e0000 LB 0x0009e000 C:\WINDOWS\system32\uxtheme.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\uxtheme.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe677e0000 'C:\WINDOWS\system32\uxtheme.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6bc50000 'C:\WINDOWS\system32\user32.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shell32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\shell32.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\SHCore.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\SHCore.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6c970000 'C:\WINDOWS\system32\SHCore.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: error opening 'C:\WINDOWS\system32\wintab32.dll': 0 (NtPath=\??\C:\WINDOWS\system32\wintab32.dll; Input=C:\WINDOWS\system32\wintab32.dll; rcNtGetDll=0x0
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0xc0000034 'C:\WINDOWS\system32\wintab32.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\winmm.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\winmm.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe5e6e0000 'C:\WINDOWS\system32\winmm.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\winmm.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\winmm.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe5e6e0000 'C:\WINDOWS\system32\winmm.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shell32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\shell32.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\uxtheme.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\uxtheme.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe677e0000 'C:\WINDOWS\system32\uxtheme.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\advapi32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\advapi32.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6bba0000 'C:\WINDOWS\system32\advapi32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #13 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\userenv.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\userenv.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\userenv.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\userenv.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6a130000 LB 0x0002e000 C:\WINDOWS\system32\userenv.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\userenv.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a130000 'C:\WINDOWS\system32\userenv.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\kernel32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\kernel32.dll (Input=kernel32, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6c8b0000 'C:\WINDOWS\System32\kernel32.dll'
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6ca20000 LB 0x000a9000 C:\WINDOWS\System32\clbcatq.dll [fFlags=0x0]
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #30 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\clbcatq.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\clbcatq.dll
2a58.a98: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.a98: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.a98: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.a98: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\clbcatq.dll'
2a58.a98: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxC.dll: Signature #1/2: info status: 24202
2a58.a98: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcp100.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'vboxrt.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'advapi32.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'ole32.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'oleaut32.dll'.
2a58.a98: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxC.dll) WinVerifyTrust
2a58.a98: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxC.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\oleaut32.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ole32.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\advapi32.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxC.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.a98: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxC.dll
2a58.a98: supR3HardenedDllNotificationCallback: load 00007ffe09300000 LB 0x003c1000 C:\Program Files\Oracle\VirtualBox\VBoxC.dll [fFlags=0x0]
2a58.a98: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxC.dll
2a58.a98: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09300000 'C:\Program Files\Oracle\VirtualBox\VBoxC.dll'
2a58.a98: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxProxyStub.dll: Signature #1/2: info status: 24202
2a58.a98: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'advapi32.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'shlwapi.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'ole32.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'oleaut32.dll'.
2a58.a98: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'rpcrt4.dll'.
2a58.a98: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxProxyStub.dll) WinVerifyTrust
2a58.a98: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxProxyStub.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\oleaut32.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ole32.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shlwapi.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'shlwapi.dll' -> '\Device\HarddiskVolume3\Windows\System32\shlwapi.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shlwapi.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\advapi32.dll
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.a98: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.a98: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxProxyStub.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.a98: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxProxyStub.dll
2a58.a98: supR3HardenedDllNotificationCallback: load 00007ffe0cf60000 LB 0x000ef000 C:\Program Files\Oracle\VirtualBox\VBoxProxyStub.dll [fFlags=0x0]
2a58.a98: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxProxyStub.dll
2a58.a98: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe0cf60000 'C:\Program Files\Oracle\VirtualBox\VBoxProxyStub.dll'
2a58.a98: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\oleaut32.dll
2a58.a98: supR3HardenedMonitor_LdrLoadDll: pName=C:\Windows\System32\oleaut32.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.a98: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6b380000 'C:\Windows\System32\oleaut32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6bae0000 'C:\WINDOWS\system32\gdi32.dll'
2a58.5588: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.5588: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.5588: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxPuelMainVM.dll: Signature #1/2: info status: 24202
2a58.5588: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.5588: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.5588: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.5588: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxPuelMainVM.dll) WinVerifyTrust
2a58.5588: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxPuelMainVM.dll
2a58.5588: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.5588: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.5588: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.5588: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.5588: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxPuelMainVM.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.5588: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxPuelMainVM.dll
2a58.5588: supR3HardenedDllNotificationCallback: load 00007ffe64f40000 LB 0x0000e000 C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxPuelMainVM.DLL [fFlags=0x0]
2a58.5588: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxPuelMainVM.dll
2a58.5588: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe64f40000 'C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxPuelMainVM.DLL'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shell32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\shell32.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe6b0c0000 LB 0x00115000 C:\WINDOWS\System32\MSCTF.dll [fFlags=0x0]
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #10 'oleaut32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #36 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #37 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #38 'imm32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\msctf.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\msctf.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'imm32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'imm32.dll' -> '\Device\HarddiskVolume3\Windows\System32\imm32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\imm32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\oleaut32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\msctf.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=00000000000009f4 pwszName=\Device\HarddiskVolume3\Windows\System32\DataExchange.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=F602E8855BCD942955FA9DBB13C4E4D44C41A311
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package0510~31bf3856ad364e35~amd64~~10.0.19041.1706.cat'; file='\Device\HarddiskVolume3\Windows\System32\DataExchange.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #26 'd3d11.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #27 'dcomp.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\DataExchange.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\DataExchange.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'dcomp.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'dcomp.dll' -> '\Device\HarddiskVolume3\Windows\System32\dcomp.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcp_win.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\dcomp.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\dcomp.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'd3d11.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'd3d11.dll' -> '\Device\HarddiskVolume3\Windows\System32\d3d11.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp_win.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp_win.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'win32u.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'win32u.dll' -> '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\win32u.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #26 'dxgi.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #28 'win32u.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\d3d11.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\d3d11.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'win32u.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'win32u.dll' -> '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\win32u.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'dxgi.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'dxgi.dll' -> '\Device\HarddiskVolume3\Windows\System32\dxgi.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'win32u.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\dxgi.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\dxgi.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'win32u.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'win32u.dll' -> '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\win32u.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\dataexchange.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\DataExchange.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\d3d11.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\dcomp.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\dxgi.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe689e0000 LB 0x000f3000 C:\WINDOWS\system32\dxgi.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\dxgi.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe66440000 LB 0x00263000 C:\WINDOWS\system32\d3d11.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\d3d11.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe666b0000 LB 0x001e4000 C:\WINDOWS\system32\dcomp.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\dcomp.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe368a0000 LB 0x0003e000 C:\WINDOWS\system32\dataexchange.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\DataExchange.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6bae0000 'C:\WINDOWS\System32\gdi32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe368a0000 'C:\WINDOWS\system32\dataexchange.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #30 'rpcrt4.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #43 'combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #45 'msvcp_win.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\twinapi.appcore.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\twinapi.appcore.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe63ef0000 LB 0x00200000 C:\WINDOWS\system32\twinapi.appcore.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\twinapi.appcore.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp_win.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp_win.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'combase.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'combase.dll' -> '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\combase.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rpcrt4.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\twinapi.appcore.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'dwmapi.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'shlwapi.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'version.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'gdi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'advapi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'ole32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #9 'oleaut32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\NVIDIA Corporation\nview\nviewH64.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\NVIDIA Corporation\nview\nviewH64.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\oleaut32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ole32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shell32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'shell32.dll' -> '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shell32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\user32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'version.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'version.dll' -> '\Device\HarddiskVolume3\Windows\System32\version.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\version.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\version.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shlwapi.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'shlwapi.dll' -> '\Device\HarddiskVolume3\Windows\System32\shlwapi.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shlwapi.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'dwmapi.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'dwmapi.dll' -> '\Device\HarddiskVolume3\Windows\System32\dwmapi.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #20 'win32u.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #21 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #22 'gdi32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\dwmapi.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\dwmapi.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'gdi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'gdi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\gdi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\gdi32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'win32u.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'win32u.dll' -> '\Device\HarddiskVolume3\Windows\System32\win32u.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\NVIDIA Corporation\nview\nViewH64.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000009:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\NVIDIA Corporation\nview\nviewH64.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\dwmapi.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\version.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe678f0000 LB 0x0002f000 C:\WINDOWS\SYSTEM32\dwmapi.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\dwmapi.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe64210000 LB 0x0000a000 C:\WINDOWS\SYSTEM32\VERSION.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\version.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe24ea0000 LB 0x002aa000 C:\Program Files\NVIDIA Corporation\nview\nViewH64.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\NVIDIA Corporation\nview\nviewH64.dll
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-synch-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-synch-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-synch-l1-2-0'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-fibers-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-fibers-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-fibers-l1-1-1'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-synch-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-synch-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-synch-l1-2-0'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-fibers-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-fibers-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-fibers-l1-1-1'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-localization-l1-2-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-localization-l1-2-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-localization-l1-2-1'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\kernel32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\kernel32.dll (Input=kernel32, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6c8b0000 'C:\WINDOWS\System32\kernel32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe24ea0000 'C:\Program Files\NVIDIA Corporation\nview\nViewH64.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\SHCore.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\Shcore.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6c970000 'C:\WINDOWS\system32\Shcore.dll'
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\ntmarta.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\ntmarta.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe68db0000 LB 0x00033000 C:\WINDOWS\SYSTEM32\ntmarta.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ntmarta.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\ntmarta.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000aec pwszName=\Device\HarddiskVolume3\Windows\System32\OneCoreCommonProxyStub.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=8A033EA9725377134FA1DA72E486B0C8019FEC7A
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package~31bf3856ad364e35~amd64~~10.0.19041.1706.cat'; file='\Device\HarddiskVolume3\Windows\System32\OneCoreCommonProxyStub.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\OneCoreCommonProxyStub.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\OneCoreCommonProxyStub.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Windows\System32\OneCoreCommonProxyStub.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\OneCoreCommonProxyStub.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe634d0000 LB 0x0007d000 C:\Windows\System32\OneCoreCommonProxyStub.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\OneCoreCommonProxyStub.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe634d0000 'C:\Windows\System32\OneCoreCommonProxyStub.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000b44 pwszName=\Device\HarddiskVolume3\Windows\System32\actxprxy.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=5B0656CDBB93657462B502DAEFFB6AE9AE932720
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\crypt32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\crypt32.dll (Input=crypt32.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package0518~31bf3856ad364e35~amd64~~10.0.19041.1766.cat'; file='\Device\HarddiskVolume3\Windows\System32\actxprxy.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\actxprxy.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\actxprxy.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Windows\System32\ActXPrxy.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\actxprxy.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe62f20000 LB 0x000a1000 C:\Windows\System32\ActXPrxy.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\actxprxy.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe62f20000 'C:\Windows\System32\ActXPrxy.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'rpcrt4.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #12 'combase.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\OneCoreUAPCommonProxyStub.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\OneCoreUAPCommonProxyStub.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'combase.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'combase.dll' -> '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\combase.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Windows\System32\OneCoreUAPCommonProxyStub.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\OneCoreUAPCommonProxyStub.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe60db0000 LB 0x007c9000 C:\Windows\System32\OneCoreUAPCommonProxyStub.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\OneCoreUAPCommonProxyStub.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe60db0000 'C:\Windows\System32\OneCoreUAPCommonProxyStub.dll'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-string-l1-1-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-string-l1-1-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-string-l1-1-0'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-datetime-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-datetime-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-datetime-l1-1-1'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-localization-obsolete-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-localization-obsolete-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-localization-obsolete-l1-2-0'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #15 'oleaut32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #17 'rpcrt4.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #20 'coreuicomponents.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #21 'coremessaging.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\TextInputFramework.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\TextInputFramework.dll
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #35 'coremessaging.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #40 'rpcrt4.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #48 'shcore.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\CoreUIComponents.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\CoreUIComponents.dll
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #20 'ws2_32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\CoreMessaging.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\CoreMessaging.dll
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'combase.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #24 'rpcrt4.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #32 'bcryptprimitives.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\WinTypes.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\WinTypes.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe66fa0000 LB 0x000f2000 C:\WINDOWS\System32\CoreMessaging.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\CoreMessaging.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe658c0000 LB 0x00154000 C:\WINDOWS\SYSTEM32\wintypes.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\WinTypes.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe66c40000 LB 0x0035e000 C:\WINDOWS\System32\CoreUIComponents.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\CoreUIComponents.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe55c60000 LB 0x000f9000 C:\WINDOWS\SYSTEM32\textinputframework.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\TextInputFramework.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'bcryptprimitives.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'bcryptprimitives.dll' -> '\Device\HarddiskVolume3\Windows\System32\bcryptprimitives.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\bcryptprimitives.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'combase.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'combase.dll' -> '\Device\HarddiskVolume3\Windows\System32\combase.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\combase.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ws2_32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ws2_32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ws2_32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ws2_32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shcore.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'shcore.dll' -> '\Device\HarddiskVolume3\Windows\System32\shcore.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\SHCore.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'coremessaging.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'coremessaging.dll' -> '\Device\HarddiskVolume3\Windows\System32\coremessaging.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\CoreMessaging.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'coremessaging.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'coremessaging.dll' -> '\Device\HarddiskVolume3\Windows\System32\coremessaging.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\CoreMessaging.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'coreuicomponents.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'coreuicomponents.dll' -> '\Device\HarddiskVolume3\Windows\System32\coreuicomponents.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\CoreUIComponents.dll [lacks WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\WinTypes.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\CoreMessaging.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\CoreUIComponents.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\TextInputFramework.dll'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(ext-ms-win-rtcore-ntuser-window-ext-l1-1-0.dll) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=ext-ms-win-rtcore-ntuser-window-ext-l1-1-0.dll (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6bc50000 'ext-ms-win-rtcore-ntuser-window-ext-l1-1-0.dll'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(ext-ms-win-rtcore-ntuser-integration-l1-1-0.dll) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=ext-ms-win-rtcore-ntuser-integration-l1-1-0.dll (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6bc50000 'ext-ms-win-rtcore-ntuser-integration-l1-1-0.dll'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-com-l1-1-0.dll) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-com-l1-1-0.dll (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6b720000 'api-ms-win-core-com-l1-1-0.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msctf.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\MSCTF.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000009:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6b0c0000 'C:\WINDOWS\System32\MSCTF.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\dwmapi.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\dwmapi.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe678f0000 'C:\WINDOWS\system32\dwmapi.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\uxtheme.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\uxtheme.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe677e0000 'C:\WINDOWS\system32\uxtheme.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\TextShaping.dll)
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\TextShaping.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe63870000 LB 0x000ac000 C:\WINDOWS\SYSTEM32\TextShaping.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\TextShaping.dll [avoiding WinVerifyTrust]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\TextShaping.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\dwmapi.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\SYSTEM32\dwmapi.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000009:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe678f0000 'C:\WINDOWS\SYSTEM32\dwmapi.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6b5f0000 'C:\WINDOWS\System32\ole32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6b380000 'C:\WINDOWS\System32\OLEAUT32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000b80 pwszName=\Device\HarddiskVolume3\Windows\System32\wbem\wbemprox.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=D5E9B4B8E891F6D9AAF89D119CB8AAE1934ED673
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package04~31bf3856ad364e35~amd64~~10.0.19041.1706.cat'; file='\Device\HarddiskVolume3\Windows\System32\wbem\wbemprox.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'ws2_32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #18 'wbemcomn.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\wbem\wbemprox.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\wbem\wbemprox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'wbemcomn.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'wbemcomn.dll' -> '\Device\HarddiskVolume3\Windows\System32\wbemcomn.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000bf4 pwszName=\Device\HarddiskVolume3\Windows\System32\wbemcomn.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=B97C1D711C478066C1314800E4F6D26F93811194
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package04~31bf3856ad364e35~amd64~~10.0.19041.1706.cat'; file='\Device\HarddiskVolume3\Windows\System32\wbemcomn.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\wbemcomn.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\wbemcomn.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ws2_32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ws2_32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ws2_32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ws2_32.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\wbem\wbemprox.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wbem\wbemprox.dll
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wbemcomn.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe58d10000 LB 0x00090000 C:\WINDOWS\SYSTEM32\wbemcomn.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wbemcomn.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe58da0000 LB 0x00011000 C:\WINDOWS\system32\wbem\wbemprox.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wbem\wbemprox.dll
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(API-MS-Win-Core-LocalRegistry-L1-1-0.dll) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=API-MS-Win-Core-LocalRegistry-L1-1-0.dll (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000009:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'API-MS-Win-Core-LocalRegistry-L1-1-0.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe58da0000 'C:\WINDOWS\system32\wbem\wbemprox.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000c08 pwszName=\Device\HarddiskVolume3\Windows\System32\wbem\wbemsvc.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=8CA332CD27CD01F33F85EB4BED516FAA617B555A
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package04~31bf3856ad364e35~amd64~~10.0.19041.1706.cat'; file='\Device\HarddiskVolume3\Windows\System32\wbem\wbemsvc.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\wbem\wbemsvc.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\wbem\wbemsvc.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\wbem\wbemsvc.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wbem\wbemsvc.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe57e10000 LB 0x00014000 C:\WINDOWS\system32\wbem\wbemsvc.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wbem\wbemsvc.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe57e10000 'C:\WINDOWS\system32\wbem\wbemsvc.dll'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-localization-l1-2-0.dll) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-localization-l1-2-0.dll (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000009:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-localization-l1-2-0.dll'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-localization-obsolete-l1-1-0.dll) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-localization-obsolete-l1-1-0.dll (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000009:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-localization-obsolete-l1-1-0.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000c34 pwszName=\Device\HarddiskVolume3\Windows\System32\wbem\fastprox.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=184DC69A17259EC62BC6A74793DCE28D7CC5A1AC
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package04~31bf3856ad364e35~amd64~~10.0.19041.1706.cat'; file='\Device\HarddiskVolume3\Windows\System32\wbem\fastprox.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #20 'wbemcomn.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\wbem\fastprox.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\wbem\fastprox.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'wbemcomn.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'wbemcomn.dll' -> '\Device\HarddiskVolume3\Windows\System32\wbemcomn.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wbemcomn.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\wbem\fastprox.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wbem\fastprox.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe58200000 LB 0x0010b000 C:\WINDOWS\system32\wbem\fastprox.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wbem\fastprox.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe58200000 'C:\WINDOWS\system32\wbem\fastprox.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000a78 pwszName=\Device\HarddiskVolume3\Windows\System32\amsi.dll
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=4E037358D3BFB2BDA56CED3A1B6A631D12D37E28
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package05~31bf3856ad364e35~amd64~~10.0.19041.1766.cat'; file='\Device\HarddiskVolume3\Windows\System32\amsi.dll'
2a58.348c: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #14 'rpcrt4.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\amsi.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\amsi.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\amsi.dll (Input=amsi.dll, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\amsi.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe56810000 LB 0x00020000 C:\WINDOWS\System32\amsi.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\amsi.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe56810000 'C:\WINDOWS\System32\amsi.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'oleaut32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'advapi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'ole32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Windows Defender\MpOAV.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Windows Defender\MpOAV.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Windows Defender\MpOav.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Windows Defender\MpOAV.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe565d0000 LB 0x00044000 C:\Program Files\Windows Defender\MpOav.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Windows Defender\MpOAV.dll
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-synch-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-synch-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-synch-l1-2-0'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-fibers-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-fibers-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-fibers-l1-1-1'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-synch-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-synch-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-synch-l1-2-0'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-fibers-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-fibers-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-fibers-l1-1-1'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-localization-l1-2-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-localization-l1-2-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-localization-l1-2-1'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\version.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\version.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000009:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe64210000 'C:\WINDOWS\system32\version.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe565d0000 'C:\Program Files\Windows Defender\MpOav.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'wintrust.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'crypt32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'rpcrt4.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'user32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'advapi32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'ole32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'shlwapi.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #9 'userenv.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #10 'shell32.dll'.
2a58.348c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #11 'oleaut32.dll'.
2a58.348c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files (x86)\Symantec\Symantec Endpoint Protection\14.3.7388.4000.105\Bin64\symamsi.dll) WinVerifyTrust
2a58.348c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files (x86)\Symantec\Symantec Endpoint Protection\14.3.7388.4000.105\Bin64\symamsi.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shell32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'shell32.dll' -> '\Device\HarddiskVolume3\Windows\System32\shell32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'userenv.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'userenv.dll' -> '\Device\HarddiskVolume3\Windows\System32\userenv.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\userenv.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'shlwapi.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'shlwapi.dll' -> '\Device\HarddiskVolume3\Windows\System32\shlwapi.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shlwapi.dll
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'crypt32.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'crypt32.dll' -> '\Device\HarddiskVolume3\Windows\System32\crypt32.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'wintrust.dll'...
2a58.348c: supR3HardenedWinVerifyCacheProcessImportTodos: 'wintrust.dll' -> '\Device\HarddiskVolume3\Windows\System32\wintrust.dll' [rcNtRedir=0xc0150008]
2a58.348c: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\wintrust.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files (x86)\Symantec\Symantec Endpoint Protection\14.3.7388.4000.105\bin64\symamsi.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files (x86)\Symantec\Symantec Endpoint Protection\14.3.7388.4000.105\Bin64\symamsi.dll
2a58.348c: supR3HardenedDllNotificationCallback: load 00007ffe564e0000 LB 0x000e4000 C:\Program Files (x86)\Symantec\Symantec Endpoint Protection\14.3.7388.4000.105\bin64\symamsi.dll [fFlags=0x0]
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files (x86)\Symantec\Symantec Endpoint Protection\14.3.7388.4000.105\Bin64\symamsi.dll
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-synch-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-synch-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-synch-l1-2-0'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-fibers-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-fibers-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-fibers-l1-1-1'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-synch-l1-2-0) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-synch-l1-2-0 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-synch-l1-2-0'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-fibers-l1-1-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-fibers-l1-1-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-fibers-l1-1-1'
2a58.348c: supR3HardenedIsApiSetDll: ApiSetQueryApiSetPresence(api-ms-win-core-localization-l1-2-1) -> 0x0, fPresent=1
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=api-ms-win-core-localization-l1-2-1 (rcNtResolve=0x0) *pfFlags=0x0 pwszSearchPath=0000000000000801:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6a280000 'api-ms-win-core-localization-l1-2-1'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe564e0000 'C:\Program Files (x86)\Symantec\Symantec Endpoint Protection\14.3.7388.4000.105\bin64\symamsi.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6bba0000 'C:\WINDOWS\System32\ADVAPI32.dll'
2a58.598c: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll: Signature #1/2: info status: 24202
2a58.598c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.598c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.598c: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.598c: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll) WinVerifyTrust
2a58.598c: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll
2a58.598c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.598c: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.598c: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.598c: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.598c: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxVMM.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.598c: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll
2a58.598c: supR3HardenedDllNotificationCallback: load 00007ffde7520000 LB 0x0037d000 C:\Program Files\Oracle\VirtualBox\VBoxVMM.DLL [fFlags=0x0]
2a58.598c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll
2a58.598c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffde7520000 'C:\Program Files\Oracle\VirtualBox\VBoxVMM.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6b5f0000 'C:\WINDOWS\system32\ole32.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000df0 pwszName=\Device\HarddiskVolume3\Windows\System32\NetSetupShim.dll
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=BAC8C290E6A586220883FAD5DCDC734D078E5A36
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package05112~31bf3856ad364e35~amd64~~10.0.19041.1741.cat'; file='\Device\HarddiskVolume3\Windows\System32\NetSetupShim.dll'
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcp_win.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #31 'rpcrt4.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #32 'oleaut32.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #34 'ws2_32.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #35 'netsetupapi.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #36 'setupapi.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #37 'devrtl.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\NetSetupShim.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\NetSetupShim.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'devrtl.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'devrtl.dll' -> '\Device\HarddiskVolume3\Windows\System32\devrtl.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000e04 pwszName=\Device\HarddiskVolume3\Windows\System32\devrtl.dll
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=14277C1223BB514B07ED4CDDA4F2EA5BFA8BD59B
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Desktop-Required-Package0516~31bf3856ad364e35~amd64~~10.0.19041.1826.cat'; file='\Device\HarddiskVolume3\Windows\System32\devrtl.dll'
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\devrtl.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\devrtl.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'setupapi.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'setupapi.dll' -> '\Device\HarddiskVolume3\Windows\System32\setupapi.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #28 'rpcrt4.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #35 'cfgmgr32.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #41 'bcrypt.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\setupapi.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\setupapi.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'netsetupapi.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'netsetupapi.dll' -> '\Device\HarddiskVolume3\Windows\System32\netsetupapi.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'bcrypt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'bcrypt.dll' -> '\Device\HarddiskVolume3\Windows\System32\bcrypt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\bcrypt.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'cfgmgr32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'cfgmgr32.dll' -> '\Device\HarddiskVolume3\Windows\System32\cfgmgr32.dll' [rcNtRedir=0xc0150008]
2a58.1658: Detected WinVerifyTrust recursion: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\cfgmgr32.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\cfgmgr32.dll)
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\cfgmgr32.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcrt.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #17 'rpcrt4.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\NetSetupApi.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\NetSetupApi.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ws2_32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'ws2_32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ws2_32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ws2_32.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp_win.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp_win.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Windows\System32\NetSetupShim.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\NetSetupShim.dll
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\NetSetupApi.dll
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\devrtl.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe6a230000 LB 0x0004e000 C:\WINDOWS\System32\cfgmgr32.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cfgmgr32.dll [avoiding WinVerifyTrust]
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe58620000 LB 0x00026000 C:\Windows\System32\NetSetupApi.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\NetSetupApi.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe6ac50000 LB 0x0046f000 C:\WINDOWS\System32\setupapi.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\setupapi.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe55520000 LB 0x00014000 C:\Windows\System32\DEVRTL.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\devrtl.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe47750000 LB 0x00078000 C:\Windows\System32\NetSetupShim.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\NetSetupShim.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe47750000 'C:\Windows\System32\NetSetupShim.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\cfgmgr32.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcrt.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #23 'rpcrt4.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #24 'nsi.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #25 'winnsi.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\NetSetupEngine.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\NetSetupEngine.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'winnsi.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'winnsi.dll' -> '\Device\HarddiskVolume3\Windows\System32\winnsi.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'rpcrt4.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'nsi.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\winnsi.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\winnsi.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'nsi.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'nsi.dll' -> '\Device\HarddiskVolume3\Windows\System32\nsi.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'nsi.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'nsi.dll' -> '\Device\HarddiskVolume3\Windows\System32\nsi.dll' [rcNtRedir=0xc0150008]
2a58.1658: Detected WinVerifyTrust recursion: rc=VINF_SUCCESS '\Device\HarddiskVolume3\Windows\System32\nsi.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\nsi.dll)
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\nsi.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\nsi.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcrt.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Windows\System32\NetSetupEngine.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\NetSetupEngine.dll
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\winnsi.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe6be30000 LB 0x00008000 C:\WINDOWS\System32\NSI.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\nsi.dll [avoiding WinVerifyTrust]
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe64850000 LB 0x0000b000 C:\WINDOWS\SYSTEM32\WINNSI.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\winnsi.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe38210000 LB 0x000ca000 C:\Windows\System32\NetSetupEngine.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\NetSetupEngine.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe38210000 'C:\Windows\System32\NetSetupEngine.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardenedWinVerifyCacheProcessWvtTodos: 0 (was 0) fWinVerifyTrust=1 for '\Device\HarddiskVolume3\Windows\System32\nsi.dll'
2a58.4a54: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedClipboard.dll: Signature #1/2: info status: 24202
2a58.4a54: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.4a54: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.4a54: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcp100.dll'.
2a58.4a54: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'vboxvmm.dll'.
2a58.4a54: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'vboxrt.dll'.
2a58.4a54: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'user32.dll'.
2a58.4a54: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedClipboard.dll) WinVerifyTrust
2a58.4a54: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedClipboard.dll
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxvmm.dll'...
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxvmm.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxvmm.dll' [rcNtRedir=0xc0150008]
2a58.4a54: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.4a54: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.4a54: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxSharedClipboard.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.4a54: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedClipboard.dll
2a58.4a54: supR3HardenedDllNotificationCallback: load 00007ffe64e60000 LB 0x00010000 C:\Program Files\Oracle\VirtualBox\VBoxSharedClipboard.DLL [fFlags=0x0]
2a58.4a54: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedClipboard.dll
2a58.4a54: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe64e60000 'C:\Program Files\Oracle\VirtualBox\VBoxSharedClipboard.DLL'
2a58.56c8: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDragAndDropSvc.dll: Signature #1/2: info status: 24202
2a58.56c8: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.56c8: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.56c8: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcp100.dll'.
2a58.56c8: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'vboxrt.dll'.
2a58.56c8: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDragAndDropSvc.dll) WinVerifyTrust
2a58.56c8: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDragAndDropSvc.dll
2a58.56c8: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.56c8: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.56c8: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.56c8: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.56c8: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.56c8: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.56c8: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll
2a58.56c8: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxDragAndDropSvc.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.56c8: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDragAndDropSvc.dll
2a58.56c8: supR3HardenedDllNotificationCallback: load 00007ffe63820000 LB 0x0000d000 C:\Program Files\Oracle\VirtualBox\VBoxDragAndDropSvc.DLL [fFlags=0x0]
2a58.56c8: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDragAndDropSvc.dll
2a58.56c8: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe63820000 'C:\Program Files\Oracle\VirtualBox\VBoxDragAndDropSvc.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\Shell32.dll'
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxVMM.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffde7520000 'C:\Program Files\Oracle\VirtualBox\VBoxVMM.DLL'
2a58.1658: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.dll: Signature #1/2: info status: 24202
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'user32.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'ole32.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'oleaut32.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'oleaut32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'oleaut32.dll' -> '\Device\HarddiskVolume3\Windows\System32\oleaut32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe36750000 LB 0x00041000 C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe36750000 'C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.DLL'
2a58.1658: supR3HardenedDllNotificationCallback: Unload 00007ffe36750000 LB 0x00041000 C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.DLL [flags=0x0]
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: hFile=0000000000000e38 pwszName=\Device\HarddiskVolume3\Windows\System32\WinHvPlatform.dll
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: Cached context 00000000014522a0
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: hCatAdmin=00000000014522a0
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: cbHash=20 wszDigest=CFF1A1590C53D6E12EEC0DDBA64D6189D81C99C1
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile: WinVerifyTrust => 0x0; cat='C:\WINDOWS\system32\CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\Microsoft-Windows-Client-Features-Package03~31bf3856ad364e35~amd64~~10.0.19041.1766.cat'; file='\Device\HarddiskVolume3\Windows\System32\WinHvPlatform.dll'
2a58.1658: supR3HardNtViCallWinVerifyTrustCatFile -> 0 (org 22900)
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'vid.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\WinHvPlatform.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\WinHvPlatform.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vid.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vid.dll' -> '\Device\HarddiskVolume3\Windows\System32\vid.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\vid.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\vid.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\WinHvPlatform.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\WinHvPlatform.dll
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\vid.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe4e0b0000 LB 0x0001b000 C:\WINDOWS\SYSTEM32\vid.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\vid.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe43df0000 LB 0x00026000 C:\WINDOWS\system32\WinHvPlatform.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\WinHvPlatform.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe43df0000 'C:\WINDOWS\system32\WinHvPlatform.dll'
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\vid.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\vid.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe4e0b0000 'C:\WINDOWS\system32\vid.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: '\Device\HarddiskVolume3\Windows\System32\ntdll.dll' has no imports
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\ntdll.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\ntdll.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\NTDLL.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6cb10000 'C:\WINDOWS\system32\NTDLL.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD.dll: Signature #1/2: info status: 24202
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxvmm.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'vboxrt.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'vboxddu.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'vboxdd2.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #6 'user32.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #7 'setupapi.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #8 'ws2_32.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #9 'ole32.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #10 'iphlpapi.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'iphlpapi.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'iphlpapi.dll' -> '\Device\HarddiskVolume3\Windows\System32\iphlpapi.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\IPHLPAPI.DLL) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\IPHLPAPI.DLL
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ole32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'ole32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ole32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'ws2_32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'ws2_32.dll' -> '\Device\HarddiskVolume3\Windows\System32\ws2_32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\ws2_32.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'setupapi.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'setupapi.dll' -> '\Device\HarddiskVolume3\Windows\System32\setupapi.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\setupapi.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxdd2.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxdd2.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxdd2.dll' [rcNtRedir=0xc0150008]
2a58.1658: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD2.dll: Signature #1/2: info status: 24202
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD2.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD2.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxddu.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxddu.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxddu.dll' [rcNtRedir=0xc0150008]
2a58.1658: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDDU.dll: Signature #1/2: info status: 24202
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'user32.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #4 'setupapi.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #5 'advapi32.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDDU.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDDU.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxvmm.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxvmm.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxvmm.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'advapi32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'advapi32.dll' -> '\Device\HarddiskVolume3\Windows\System32\advapi32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'setupapi.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'setupapi.dll' -> '\Device\HarddiskVolume3\Windows\System32\setupapi.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\setupapi.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'user32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'user32.dll' -> '\Device\HarddiskVolume3\Windows\System32\user32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxDD.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD.dll
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDDU.dll
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD2.dll
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\IPHLPAPI.DLL
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe3e920000 LB 0x00066000 C:\Program Files\Oracle\VirtualBox\VBoxDDU.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDDU.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffde62b0000 LB 0x0085c000 C:\Program Files\Oracle\VirtualBox\VBoxDD2.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD2.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe69650000 LB 0x0003b000 C:\WINDOWS\SYSTEM32\IPHLPAPI.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\IPHLPAPI.DLL
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffde6b10000 LB 0x00a03000 C:\Program Files\Oracle\VirtualBox\VBoxDD.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffde6b10000 'C:\Program Files\Oracle\VirtualBox\VBoxDD.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe36750000 LB 0x00041000 C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe36750000 'C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxHostWebcam.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxC.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxC.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe09300000 'C:\Program Files\Oracle\VirtualBox\VBoxC.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxDD2.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxDD2.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffde62b0000 'C:\Program Files\Oracle\VirtualBox\VBoxDD2.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR3.dll: Signature #1/2: info status: 24202
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR3.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR3.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR3.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR3.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe48800000 LB 0x00018000 C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR3.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR3.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe48800000 'C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxEhciR3.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxNvmeR3.dll: Signature #1/2: info status: 24202
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxNvmeR3.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxNvmeR3.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxNvmeR3.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxNvmeR3.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe48660000 LB 0x00012000 C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxNvmeR3.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxNvmeR3.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe48660000 'C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxNvmeR3.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbCardReaderR3.dll: Signature #1/2: info status: 24202
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbCardReaderR3.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbCardReaderR3.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbCardReaderR3.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbCardReaderR3.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe3eb40000 LB 0x00018000 C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbCardReaderR3.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbCardReaderR3.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe3eb40000 'C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbCardReaderR3.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbWebcamR3.dll: Signature #1/2: info status: 24202
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbWebcamR3.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbWebcamR3.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbWebcamR3.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbWebcamR3.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe3e620000 LB 0x00019000 C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbWebcamR3.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbWebcamR3.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe3e620000 'C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VBoxUsbWebcamR3.DLL'
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\rsaenh.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\rsaenh.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1df0: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedFolders.dll: Signature #1/2: info status: 24202
2a58.1df0: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1df0: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1df0: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxvmm.dll'.
2a58.1df0: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'vboxrt.dll'.
2a58.1df0: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedFolders.dll) WinVerifyTrust
2a58.1df0: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedFolders.dll
2a58.1df0: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1df0: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1df0: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxvmm.dll'...
2a58.1df0: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxvmm.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxvmm.dll' [rcNtRedir=0xc0150008]
2a58.1df0: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll
2a58.1df0: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1df0: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1df0: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxSharedFolders.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1df0: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedFolders.dll
2a58.1df0: supR3HardenedDllNotificationCallback: load 00007ffe3e600000 LB 0x00014000 C:\Program Files\Oracle\VirtualBox\VBoxSharedFolders.DLL [fFlags=0x0]
2a58.1df0: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxSharedFolders.dll
2a58.1df0: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe3e600000 'C:\Program Files\Oracle\VirtualBox\VBoxSharedFolders.DLL'
2a58.5b04: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestControlSvc.dll: Signature #1/2: info status: 24202
2a58.5b04: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.5b04: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.5b04: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcp100.dll'.
2a58.5b04: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'vboxvmm.dll'.
2a58.5b04: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #3 'vboxrt.dll'.
2a58.5b04: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestControlSvc.dll) WinVerifyTrust
2a58.5b04: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestControlSvc.dll
2a58.5b04: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.5b04: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.5b04: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxvmm.dll'...
2a58.5b04: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxvmm.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxvmm.dll' [rcNtRedir=0xc0150008]
2a58.5b04: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxVMM.dll
2a58.5b04: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.5b04: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.5b04: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.5b04: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.5b04: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxGuestControlSvc.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.5b04: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestControlSvc.dll
2a58.5b04: supR3HardenedDllNotificationCallback: load 00007ffe595d0000 LB 0x0000c000 C:\Program Files\Oracle\VirtualBox\VBoxGuestControlSvc.DLL [fFlags=0x0]
2a58.5b04: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestControlSvc.dll
2a58.5b04: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe595d0000 'C:\Program Files\Oracle\VirtualBox\VBoxGuestControlSvc.DLL'
2a58.39c4: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestPropSvc.dll: Signature #1/2: info status: 24202
2a58.39c4: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.39c4: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.39c4: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'msvcp100.dll'.
2a58.39c4: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #2 'vboxrt.dll'.
2a58.39c4: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestPropSvc.dll) WinVerifyTrust
2a58.39c4: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestPropSvc.dll
2a58.39c4: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.39c4: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.39c4: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp100.dll'...
2a58.39c4: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcp100.dll' [rcNtRedir=0xc0150008]
2a58.39c4: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.39c4: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.39c4: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\VBoxGuestPropSvc.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.39c4: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestPropSvc.dll
2a58.39c4: supR3HardenedDllNotificationCallback: load 00007ffe488e0000 LB 0x0000d000 C:\Program Files\Oracle\VirtualBox\VBoxGuestPropSvc.DLL [fFlags=0x0]
2a58.39c4: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\VBoxGuestPropSvc.dll
2a58.39c4: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe488e0000 'C:\Program Files\Oracle\VirtualBox\VBoxGuestPropSvc.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.dll: Signature #1/2: info status: 24202
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcr100.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #1 'vboxrt.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'vboxrt.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'vboxrt.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\vboxrt.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcr100.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcr100.dll' -> '\Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\msvcr100.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.DLL (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe55400000 LB 0x0000a000 C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.DLL [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe55400000 'C:\Program Files\Oracle\VirtualBox\ExtensionPacks\Oracle_VM_VirtualBox_Extension_Pack\win.amd64\VDPluginCrypt.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #0 'msvcp_win.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #16 'rpcrt4.dll'.
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #28 'devobj.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\MMDevAPI.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\MMDevAPI.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'devobj.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'devobj.dll' -> '\Device\HarddiskVolume3\Windows\System32\devobj.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6aa10000 'C:\WINDOWS\System32\crypt32.dll'
2a58.1658: supR3HardenedWinVerifyCacheScheduleImports: Import todo: #18 'cfgmgr32.dll'.
2a58.1658: supHardenedWinVerifyImageByHandle: -> 0 (\Device\HarddiskVolume3\Windows\System32\devobj.dll) WinVerifyTrust
2a58.1658: supR3HardenedWinVerifyCacheInsert: \Device\HarddiskVolume3\Windows\System32\devobj.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'rpcrt4.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'rpcrt4.dll' -> '\Device\HarddiskVolume3\Windows\System32\rpcrt4.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'msvcp_win.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'msvcp_win.dll' -> '\Device\HarddiskVolume3\Windows\System32\msvcp_win.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\msvcp_win.dll
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: Processing 'cfgmgr32.dll'...
2a58.1658: supR3HardenedWinVerifyCacheProcessImportTodos: 'cfgmgr32.dll' -> '\Device\HarddiskVolume3\Windows\System32\cfgmgr32.dll' [rcNtRedir=0xc0150008]
2a58.1658: supR3HardenedScreenImage/Imports: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\cfgmgr32.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\MMDevApi.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000002009:<flags> [calling]
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\MMDevAPI.dll
2a58.1658: supR3HardenedScreenImage/NtCreateSection: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\devobj.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe69fe0000 LB 0x0002c000 C:\WINDOWS\System32\DEVOBJ.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\devobj.dll
2a58.1658: supR3HardenedDllNotificationCallback: load 00007ffe61b30000 LB 0x00085000 C:\WINDOWS\System32\MMDevApi.dll [fFlags=0x0]
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\MMDevAPI.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61b30000 'C:\WINDOWS\System32\MMDevApi.dll'
2a58.1658: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\MMDevAPI.dll
2a58.1658: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\System32\MMDEVAPI.DLL (Input=MMDEVAPI.DLL, rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe61b30000 'C:\WINDOWS\System32\MMDEVAPI.DLL'
2a58.1658: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe691b0000 'C:\WINDOWS\system32\rsaenh.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedScreenImage/LdrLoadDll: cache hit (VINF_SUCCESS) on \Device\HarddiskVolume3\Windows\System32\shell32.dll
2a58.348c: supR3HardenedMonitor_LdrLoadDll: pName=C:\WINDOWS\system32\shell32.dll (rcNtResolve=0xc0150008) *pfFlags=0x0 pwszSearchPath=0000000000000001:<flags> [calling]
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll'
2a58.348c: supR3HardenedMonitor_LdrLoadDll: returns rcNt=0x0 hMod=00007ffe6be40000 'C:\WINDOWS\system32\shell32.dll' 
Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 3461907630
Url: https://administrator.de/forum/rhel9-setup-auf-virtualbox-kernelpanic-3461907630.html
Ausgedruckt am: 15.07.2025 um 04:07 Uhr