OpenVPN Verbindung steht aber kein Internet
Guten Morgen 
ich nutze in meinem Netzwerk die pfSense welche auch super läuft und alles klappt.
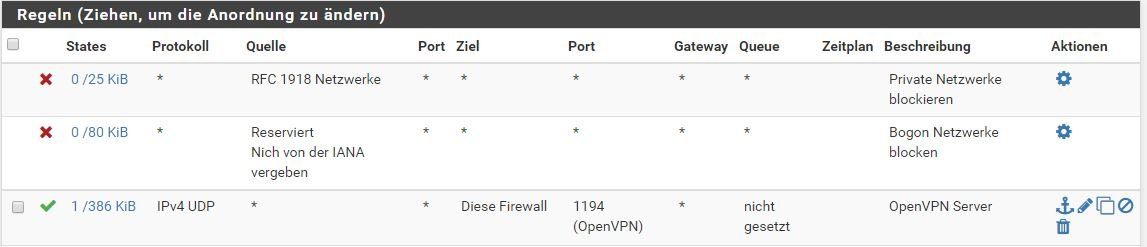
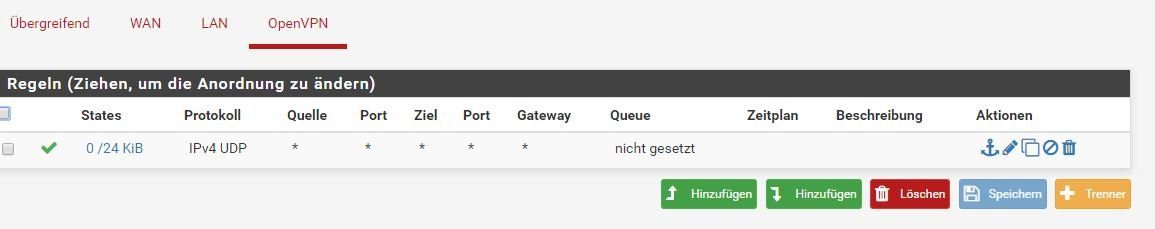
In der pfSense habe ich einen OpenVPN Server eingerichtet sowie die passenden Firewall Regeln.
Ich verbinde mich von meinem Client ( Iphone 8 ) zur pfSense und habe einen aktiven Tunnel . ABER es geht kein Traffic durch . Sprich ich kann weder die Fritzbox 192.168.178.1 noch die pfsense 192.168.110.1 oder andere Seiten aufrufen.
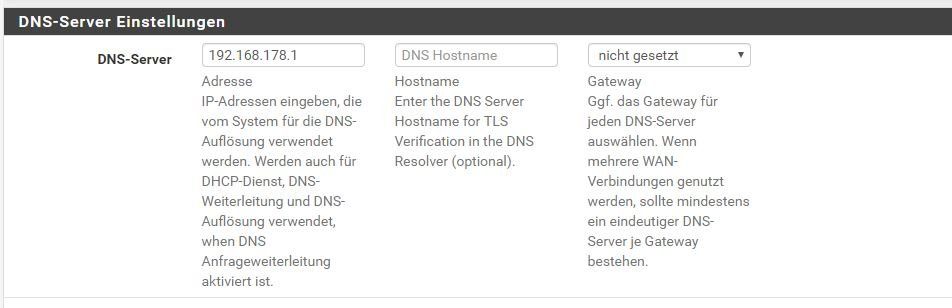
DNS macht der Windows Server 192.168.110.250.
Habe ich irgendwo einen Fehler gemacht?
Es soll der Gesamte Traffic durch den Tunnel.
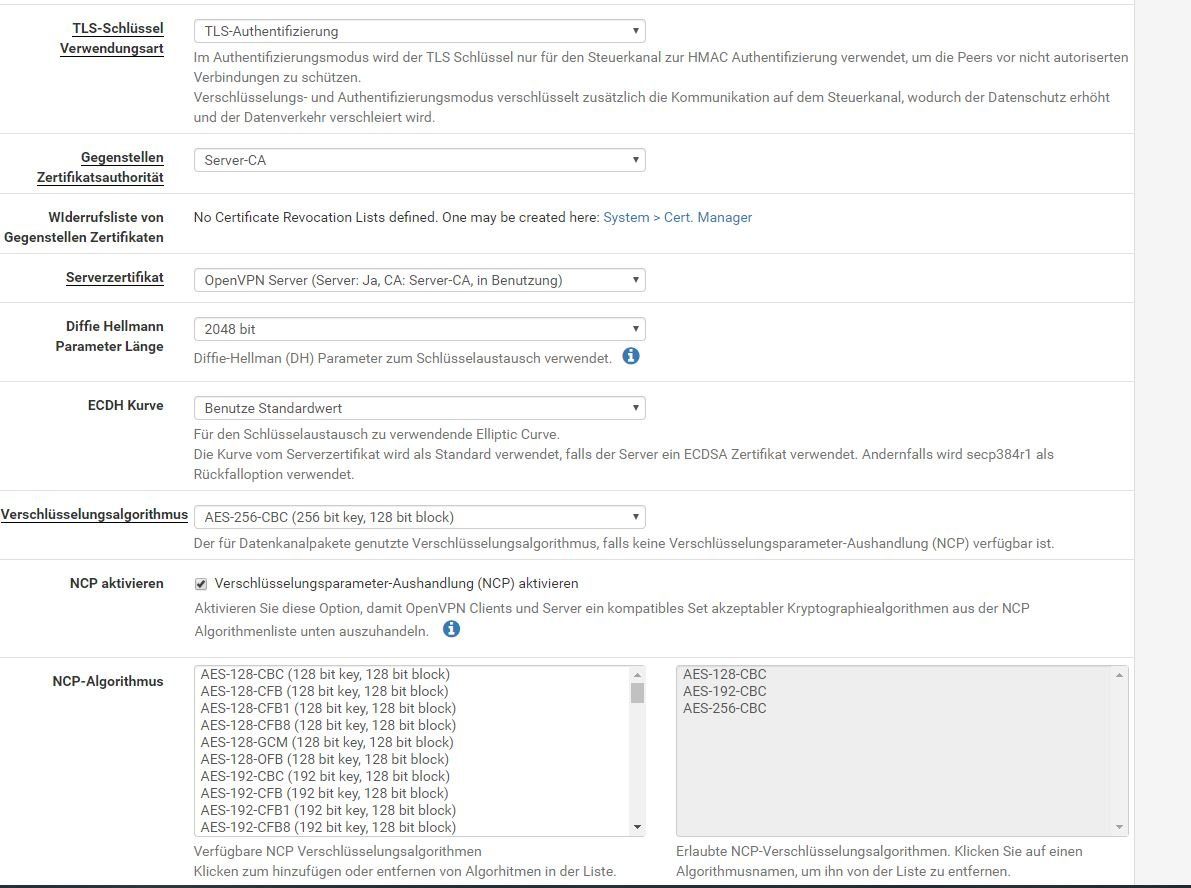
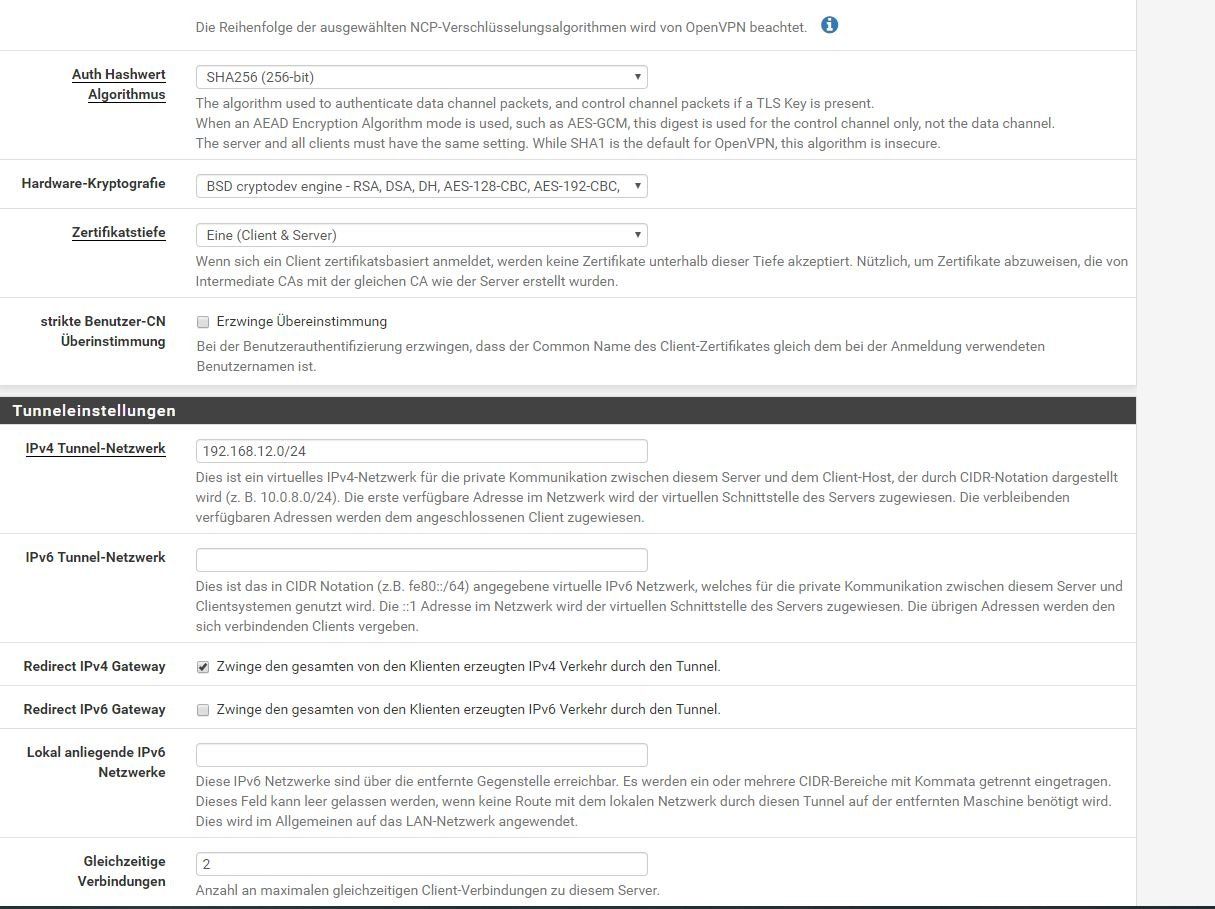
server.conf
client.ovpn
log vom Client


ich nutze in meinem Netzwerk die pfSense welche auch super läuft und alles klappt.
In der pfSense habe ich einen OpenVPN Server eingerichtet sowie die passenden Firewall Regeln.
Ich verbinde mich von meinem Client ( Iphone 8 ) zur pfSense und habe einen aktiven Tunnel . ABER es geht kein Traffic durch . Sprich ich kann weder die Fritzbox 192.168.178.1 noch die pfsense 192.168.110.1 oder andere Seiten aufrufen.
DNS macht der Windows Server 192.168.110.250.
Habe ich irgendwo einen Fehler gemacht?
Es soll der Gesamte Traffic durch den Tunnel.
server.conf
dev ovpns1
verb 1
dev-type tun
dev-node /dev/tun1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp4
cipher AES-256-CBC
auth SHA256
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
client-connect /usr/local/sbin/openvpn.attributes.sh
client-disconnect /usr/local/sbin/openvpn.attributes.sh
multihome
engine cryptodev
tls-server
server 192.168.12.0 255.255.255.0
client-config-dir /var/etc/openvpn-csc/server1
username-as-common-name
plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server1 1194
tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'OpenVPN+Server' 1"
lport 1194
management /var/etc/openvpn/server1.sock unix
max-clients 2
push "dhcp-option DOMAIN heimnetz.werk"
push "dhcp-option DNS 192.168.110.250"
push "block-outside-dns"
push "register-dns"
push "redirect-gateway def1"
client-to-client
ca /var/etc/openvpn/server1.ca
cert /var/etc/openvpn/server1.cert
key /var/etc/openvpn/server1.key
dh /etc/dh-parameters.2048
tls-auth /var/etc/openvpn/server1.tls-auth 0
ncp-ciphers AES-128-CBC:AES-192-CBC:AES-256-CBC
comp-lzo no
persist-remote-ip
float
topology subnet
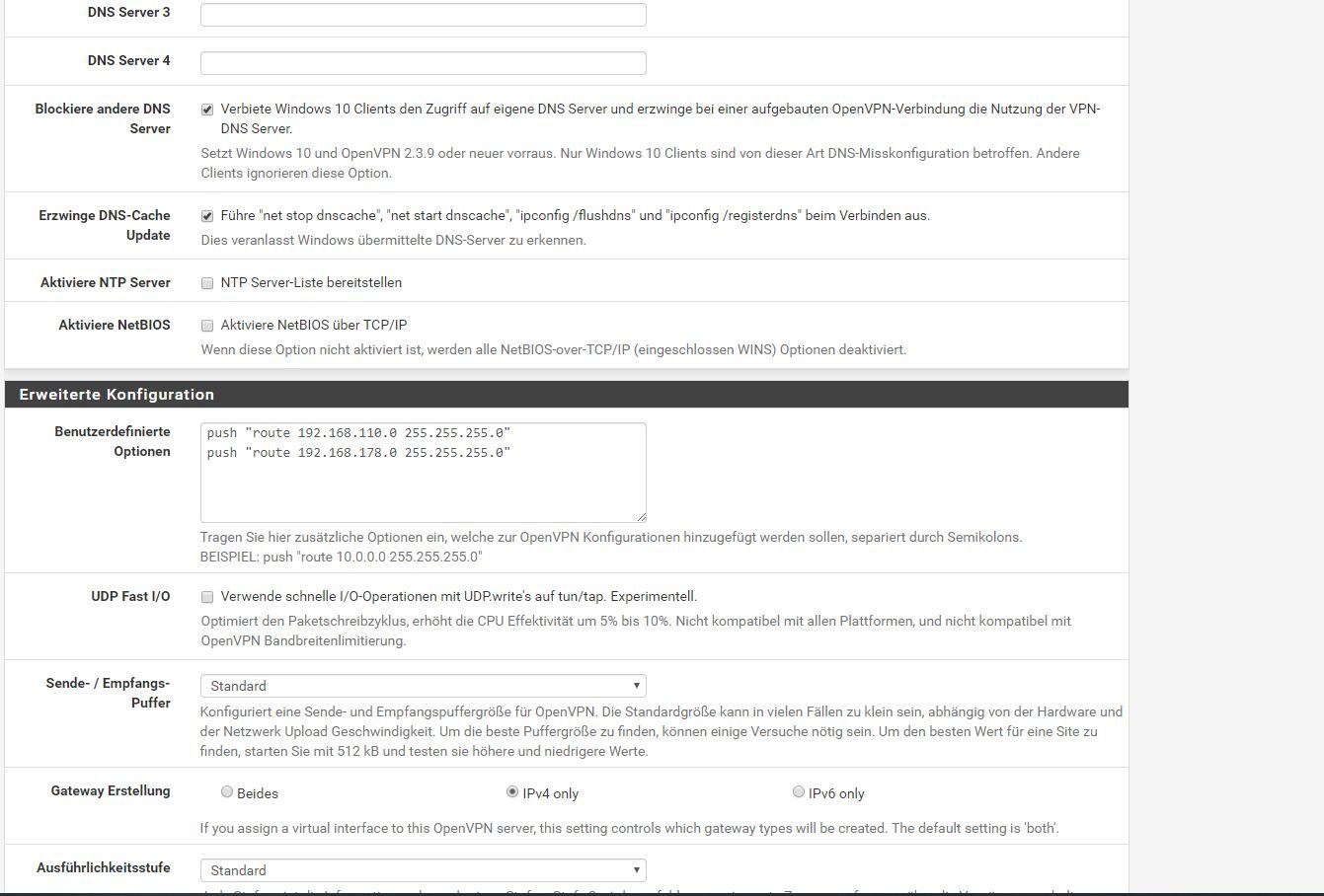
push "route 192.168.110.0 255.255.255.0"
push "route 192.168.178.0 255.255.255.0"
client.ovpn
persist-tun
persist-key
cipher AES-256-CBC
ncp-ciphers AES-128-CBC:AES-192-CBC:AES-256-CBC
auth SHA256
tls-client
client
remote DDNS ADRESSE 1194 udp
setenv opt block-outside-dns
verify-x509-name "OpenVPN Server" name
auth-user-pass
remote-cert-tls server
comp-lzo no
<ca>
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
-----END PRIVATE KEY-----
</key>
key-direction 1
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
-----END OpenVPN Static key V1-----
</tls-auth>log vom Client
2019-39-26 03:39:24 1
2019-39-26 03:39:24 ----- OpenVPN Start ----- OpenVPN core 3.2 ios arm64 64-bit PT_PROXY built on Oct 3 2018 06:35:04
2019-39-26 03:39:24 Frame=512/2048/512 mssfix-ctrl=1250
2019-39-26 03:39:24 UNUSED OPTIONS
0 [persist-tun]
1 [persist-key]
3 [ncp-ciphers] [AES-128-CBC:AES-192-CBC:AES-256-CBC]
5 [tls-client]
8 [block-outside-dns]
9 [verify-x509-name] [OpenVPN Server] [name]
2019-39-26 03:39:24 EVENT: RESOLVE
2019-39-26 03:39:24 Contacting [IP]:1194/UDP via UDP
2019-39-26 03:39:24 EVENT: WAIT
2019-39-26 03:39:24 Connecting to [....myfritz.net]:1194 (IP) via UDPv4
2019-39-26 03:39:24 EVENT: CONNECTING
2019-39-26 03:39:24 Tunnel Options:V4,dev-type tun,link-mtu 1570,tun-mtu 1500,proto UDPv4,comp-lzo,keydir 1,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-client
2019-39-26 03:39:24 Creds: Username/Password
2019-39-26 03:39:24 Peer Info:
IV_GUI_VER=net.openvpn.connect.ios 3.0.2-894
IV_VER=3.2
IV_PLAT=ios
IV_NCP=2
IV_TCPNL=1
IV_PROTO=2
IV_LZO_STUB=1
IV_COMP_STUB=1
IV_COMP_STUBv2=1
2019-39-26 03:39:24 VERIFY OK : depth=1
cert. version : 3
serial number : 00
issuer name : CN=internal-ca, C=DE, ST=THU, L=Soshausen, O=VPN, OU=IT
subject name : CN=internal-ca, C=DE, ST=THU, L=Soshausen, O=VPN, OU=IT
issued on : 2019-08-25 20:36:01
expires on : 2029-08-22 20:36:01
signed using : RSA with SHA-256
RSA key size : 2048 bits
basic constraints : CA=true
key usage : Key Cert Sign, CRL Sign
2019-39-26 03:39:24 VERIFY OK : depth=0
cert. version : 3
serial number : 01
issuer name : CN=internal-ca, C=DE, ST=THU, L=Soshausen, O=VPN, OU=IT
subject name : CN=OpenVPN Server, C=DE, ST=THU, L=Soshausen, O=VPN, OU=IT
issued on : 2019-08-25 20:39:01
expires on : 2029-08-22 20:39:01
signed using : RSA with SHA-256
RSA key size : 2048 bits
basic constraints : CA=false
cert. type : SSL Server
key usage : Digital Signature, Key Encipherment
ext key usage : TLS Web Server Authentication, ???
2019-39-26 03:39:24 SSL Handshake: TLSv1.2/TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384
2019-39-26 03:39:24 Session is ACTIVE
2019-39-26 03:39:24 EVENT: GET_CONFIG
2019-39-26 03:39:24 Sending PUSH_REQUEST to server...
2019-39-26 03:39:24 OPTIONS:
0 [dhcp-option] [DOMAIN] [heimnetz.werk]
1 [dhcp-option] [DNS] [192.168.110.250]
2 [block-outside-dns]
3 [register-dns]
4 [redirect-gateway] [def1]
5 [route] [192.168.110.0] [255.255.255.0]
6 [route] [192.168.178.0] [255.255.255.0]
7 [route-gateway] [192.168.12.1]
8 [topology] [subnet]
9 [ping] [10]
10 [ping-restart] [60]
11 [ifconfig] [192.168.12.2] [255.255.255.0]
12 [peer-id]
13 [cipher] [AES-128-CBC]
2019-39-26 03:39:24 PROTOCOL OPTIONS:
cipher: AES-128-CBC
digest: SHA256
compress: LZO_STUB
peer ID: 0
2019-39-26 03:39:24 EVENT: ASSIGN_IP
2019-39-26 03:39:24 NIP: preparing TUN network settings
2019-39-26 03:39:24 NIP: init TUN network settings with endpoint: IP
2019-39-26 03:39:24 NIP: adding IPv4 address to network settings 192.168.12.2/255.255.255.0
2019-39-26 03:39:24 NIP: adding (included) IPv4 route 192.168.12.0/24
2019-39-26 03:39:24 NIP: adding (included) IPv4 route 192.168.110.0/24
2019-39-26 03:39:24 NIP: adding (included) IPv4 route 192.168.178.0/24
2019-39-26 03:39:24 NIP: redirecting all IPv4 traffic to TUN interface
2019-39-26 03:39:24 NIP: adding match domain heimnetz.werk
2019-39-26 03:39:24 NIP: adding DNS 192.168.110.250
2019-39-26 03:39:24 Connected via NetworkExtensionTUN
2019-39-26 03:39:24 LZO-ASYM init swap=0 asym=1
2019-39-26 03:39:24 Comp-stub init swap=0
2019-39-26 03:39:24 EVENT: CONNECTED vpnuser@....myfritz.net:1194 (IP) via /UDPv4 on NetworkExtensionTUN/192.168.12.2/ gw=[/]








Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 488804
Url: https://administrator.de/forum/openvpn-verbindung-steht-aber-kein-internet-488804.html
Ausgedruckt am: 06.08.2025 um 10:08 Uhr
2 Kommentare
Neuester Kommentar