Ejabberd auf ubuntu
Anliegend erstelle ich eine Anleitung für die Installation eines ejabberd auf einem Ubuntu Server.
Die Anleitung ist derzeit noch im Aufbau.
Für die Installation werde ich meine eigene Anleitung aufbauen, vorab würde ich diese Anleitung empfehlen
hagen-bauer.de/2018/01/ejabberd.html
Mit dieser Config sollte der Server laufen. Offene Ports in der Firewall 5222, 5280 (hinter Reverse Proxy), 5269
Einfach example.com gehen Euren host austauschen. Wichtig, meine Anleitung funktioniert nur mit einem vorgeschalteten Reverse Proxy
Als Reverse Proxy und als Firewall verwende ich die hier weit verbreitete Pfsense mit Squid als Reverse Proxy.
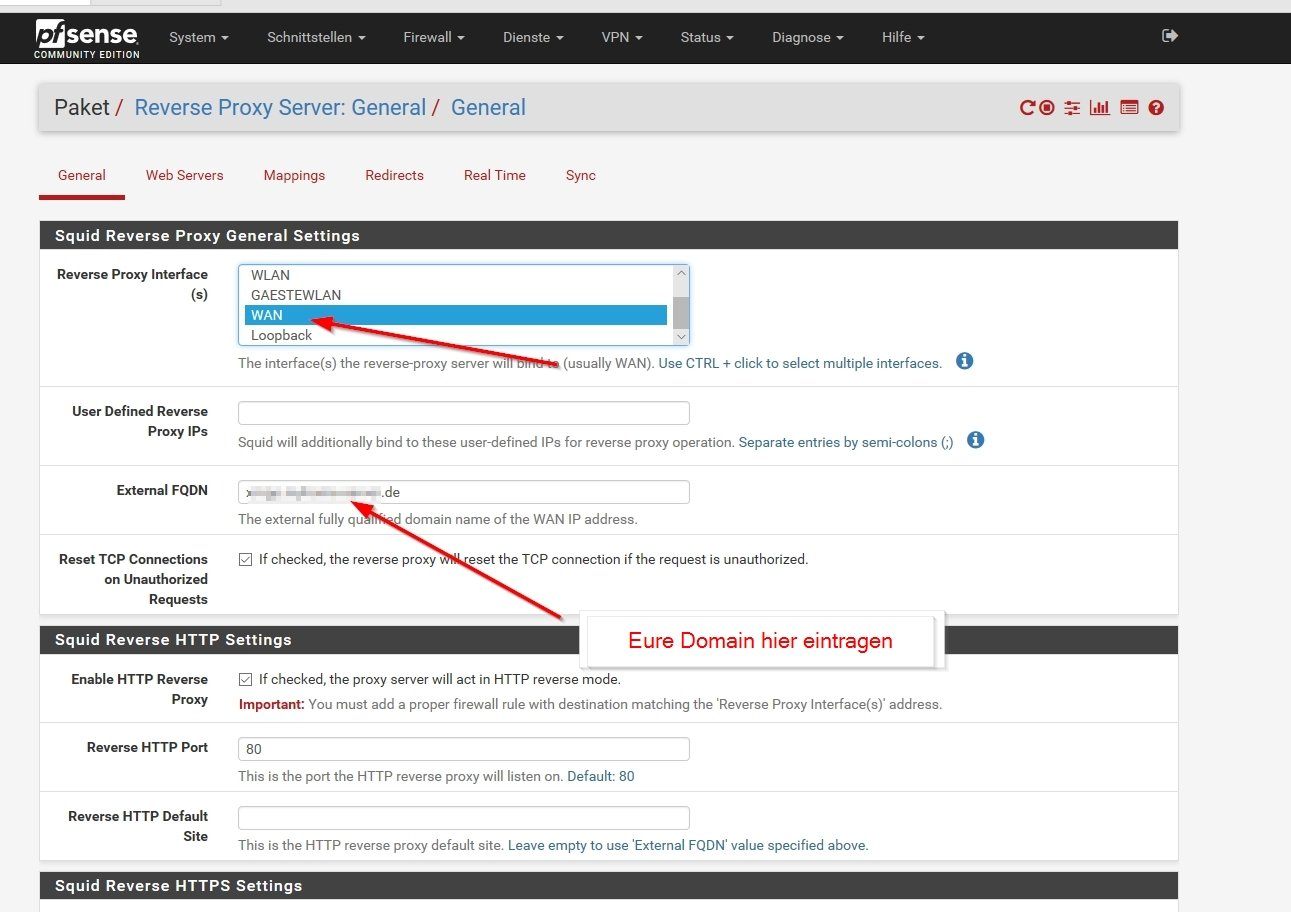
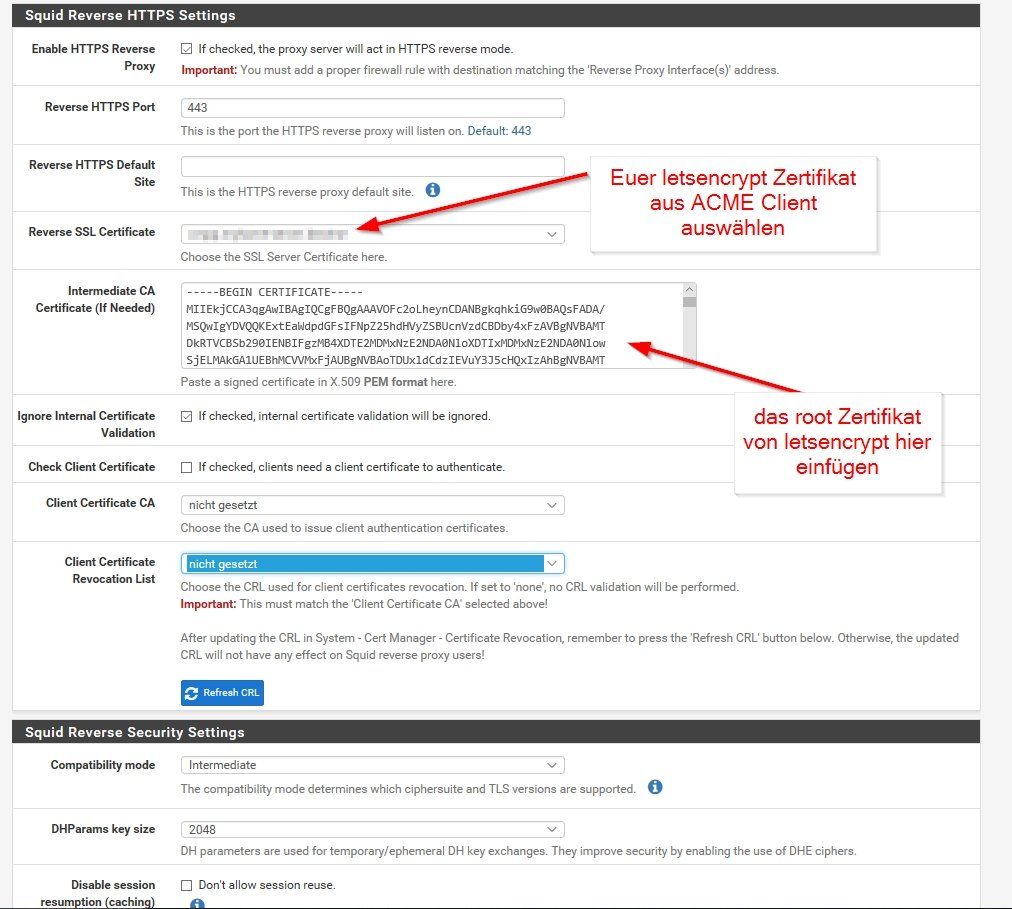
Die Einstellung im Squid Reverse Proxy der Pfsense.
Unter: Paket / Reverse Proxy Server: General / General
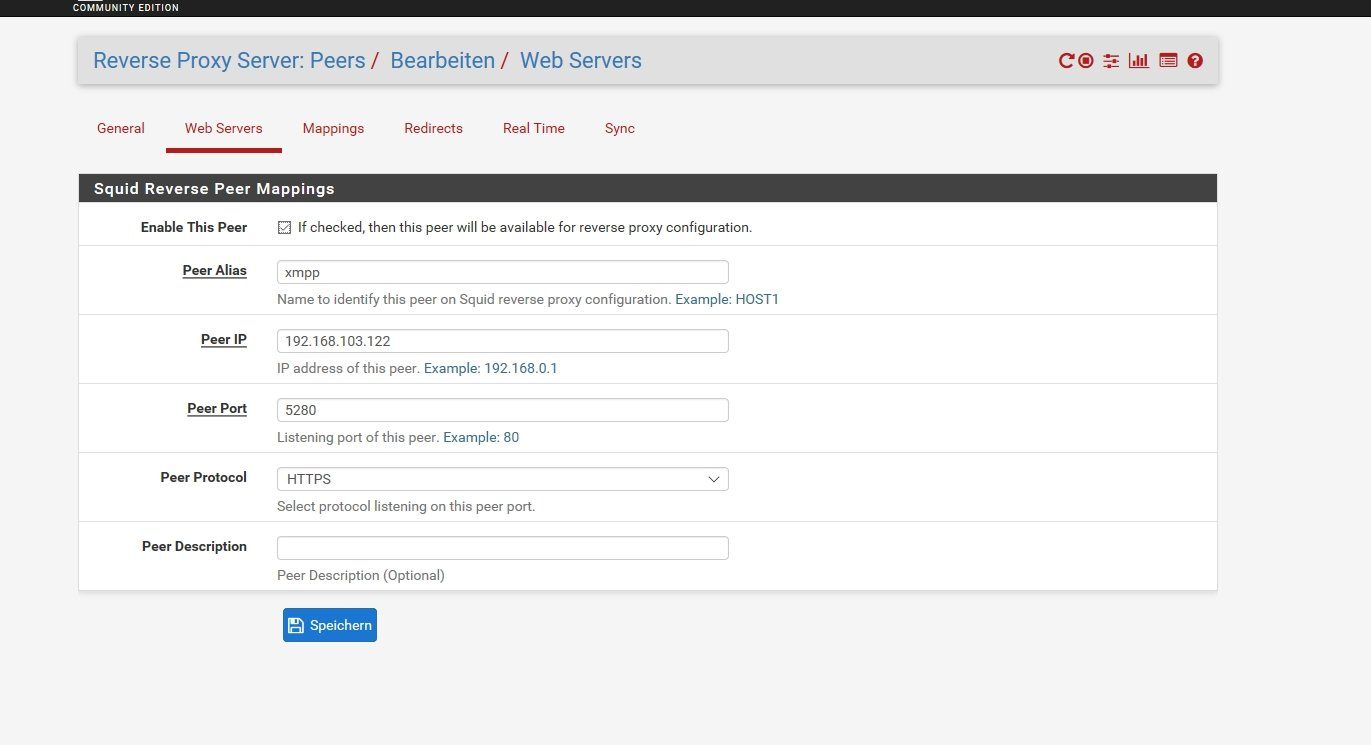
Unter: Paket / Reverse Proxy Server: Peers / Web Servers
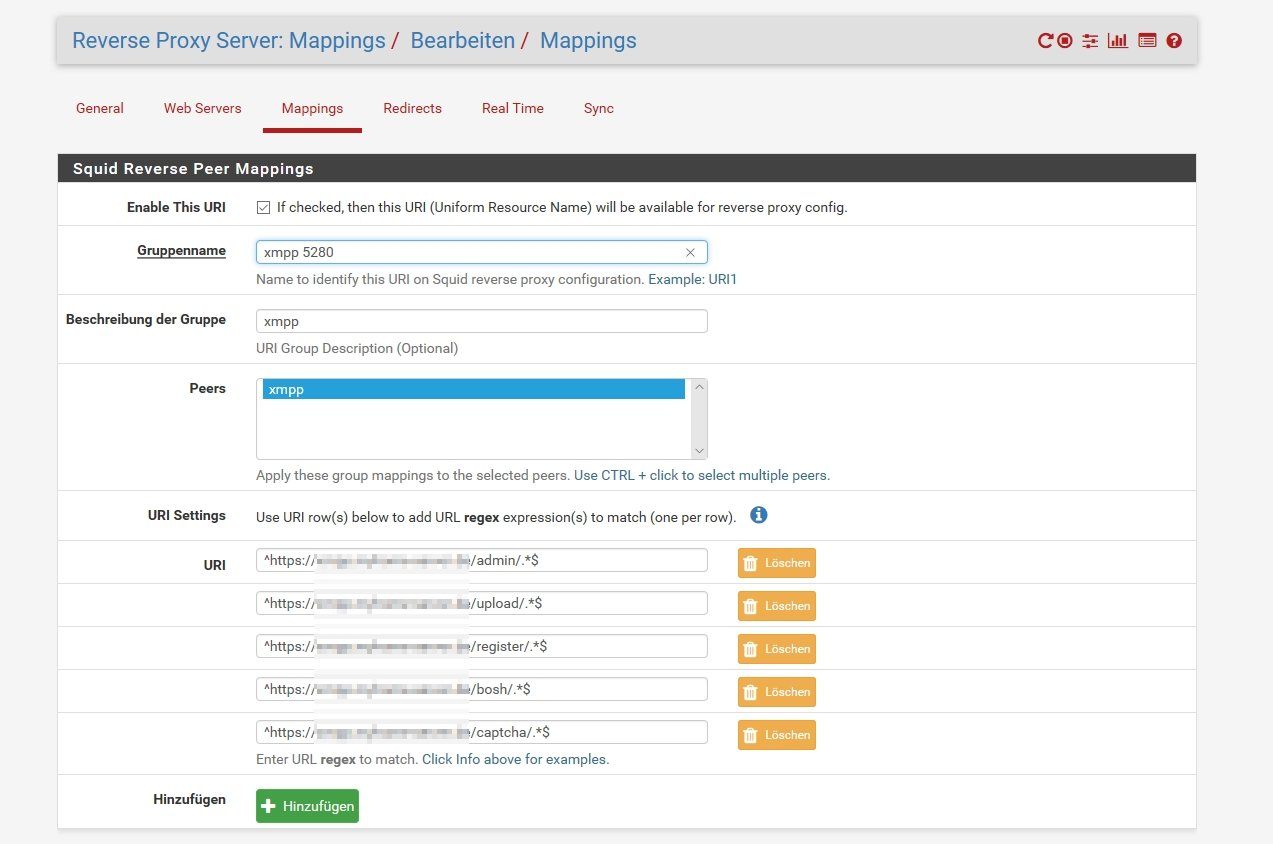
Unter: Paket / Reverse Proxy Server: Mappings / Mappings
Grundsätzliches vor der ejabberd Installation
eventuell müssen die sources list angepasst werden. Wir in der VM Installation anscheinend nicht mit auf dem Weg gebracht.
1fire.help/article/ubuntu-18-04-lts-bionic-beaver-mirror-55.html
z.B. mit dem diesem Mirror, aus der kleinen Anleitung von oben
Ein brauchbarer Datei Explorer ist auch immer hilfreich
Installieren von Ejabberd hier die Version 18.06
Braucht man für die Captcha Anmeldung, falls nicht gewünscht, dann nicht installieren. Dauert ca. 10 Minuten
System Start vom ejabberd:
Jetzt meine Config von Unten unter (siehe Bild) einfügen:
Ich mache das eigentlich immer mit dem Windows Rechner über den Editor und schiebe dann die Änderungen via WinSCP auf den Ubuntu Rechner
Starten/stoppen vom ejabberd
So können wir den ersten Benutzer anlegen:
./ejabberdctl register benutzer myhome-server.de meinpasswort
Backup, z.B. wenn man auch mit dem gesamten Server umziehen möchte
./ejabberdctl backup /tmp/ejabberd-dbbackup
./ejabberdctl restore /tmp/ejabberd-dbbackup
falls es Probleme mit den OMEMO Keys oder mal mit den Avataren geben sollte, dann verschiebt man einfach den pubsub und dann werden die Keys verschoben und bei der nächsten Verbindung erneuert
mv /opt/ejabberd/database/ejabberd@localhost/pubsub* /tmp
als Sudo im root Verzeichnis ausführen
opt/ejabberd-18.06/bin/ejabberdctl delete_old_mam_messages all 90
gute default config ohne Reverse Proxy und Captcha
Hier meine Config:
Die Anleitung ist derzeit noch im Aufbau.
Für die Installation werde ich meine eigene Anleitung aufbauen, vorab würde ich diese Anleitung empfehlen
hagen-bauer.de/2018/01/ejabberd.html
Mit dieser Config sollte der Server laufen. Offene Ports in der Firewall 5222, 5280 (hinter Reverse Proxy), 5269
Einfach example.com gehen Euren host austauschen. Wichtig, meine Anleitung funktioniert nur mit einem vorgeschalteten Reverse Proxy
Als Reverse Proxy und als Firewall verwende ich die hier weit verbreitete Pfsense mit Squid als Reverse Proxy.
Die Einstellung im Squid Reverse Proxy der Pfsense.
Unter: Paket / Reverse Proxy Server: General / General


Unter: Paket / Reverse Proxy Server: Peers / Web Servers

Unter: Paket / Reverse Proxy Server: Mappings / Mappings

Grundsätzliches vor der ejabberd Installation
apt-get update && apt-get upgrade
Automatische Updates für Ubuntu
sudo apt-get install unattended-upgradeseventuell müssen die sources list angepasst werden. Wir in der VM Installation anscheinend nicht mit auf dem Weg gebracht.
1fire.help/article/ubuntu-18-04-lts-bionic-beaver-mirror-55.html
nano /etc/apt/sources.listz.B. mit dem diesem Mirror, aus der kleinen Anleitung von oben
deb http://mirror.1fire.de/ubuntu bionic main restricted universe multiverse
deb http://mirror.1fire.de/ubuntu bionic-updates main restricted universe multiverse
deb http://mirror.1fire.de/ubuntu bionic-security main restricted universe multiverse
deb http://mirror.1fire.de/ubuntu bionic-backports main restricted universe multiversesudo apt-get install mcInstallieren von Ejabberd hier die Version 18.06
mkdir install
cd install/
wget https://www.process-one.net/downloads/downloads-action.php?file=/ejabberd/18.06/ejabberd_18.06-0_amd64.deb
sudo dpkg -i downloads-action.php?file=%2Fejabberd%2F18.06%2Fejabberd_18.06-0_amd64.debsudo apt-get install imagemagick System Start vom ejabberd:
systemctl enable ejabberd.serviceJetzt meine Config von Unten unter (siehe Bild) einfügen:


Ich mache das eigentlich immer mit dem Windows Rechner über den Editor und schiebe dann die Änderungen via WinSCP auf den Ubuntu Rechner
Starten/stoppen vom ejabberd
etc/init.d/ejabberd start
/etc/init.d/ejabberd restart
/etc/init.d/ejabberd stopSo können wir den ersten Benutzer anlegen:
./ejabberdctl register benutzer myhome-server.de meinpasswort
Backup, z.B. wenn man auch mit dem gesamten Server umziehen möchte
./ejabberdctl backup /tmp/ejabberd-dbbackup
./ejabberdctl restore /tmp/ejabberd-dbbackup
falls es Probleme mit den OMEMO Keys oder mal mit den Avataren geben sollte, dann verschiebt man einfach den pubsub und dann werden die Keys verschoben und bei der nächsten Verbindung erneuert
mv /opt/ejabberd/database/ejabberd@localhost/pubsub* /tmp
als Sudo im root Verzeichnis ausführen
opt/ejabberd-18.06/bin/ejabberdctl delete_old_mam_messages all 90
gute default config ohne Reverse Proxy und Captcha
Hier meine Config:
###
###' ejabberd configuration file
###
###
### The parameters used in this configuration file are explained in more detail
### in the ejabberd Installation and Operation Guide.
### Please consult the Guide in case of doubts, it is included with
### your copy of ejabberd, and is also available online at
### http://www.process-one.net/en/ejabberd/docs/
### The configuration file is written in YAML.
### Refer to http://en.wikipedia.org/wiki/YAML for the brief description.
### However, ejabberd treats different literals as different types:
###
### - unquoted or single-quoted strings. They are called "atoms".
### Example: dog, 'Jupiter', '3.14159', YELLOW
###
### - numeric literals. Example: 3, -45.0, .0
###
### - quoted or folded strings.
### Examples of quoted string: "Lizzard", "orange".
### Example of folded string:
### > Art thou not Romeo,
### and a Montague?
###. =======
###' LOGGING
##
## loglevel: Verbosity of log files generated by ejabberd.
## 0: No ejabberd log at all (not recommended)
## 1: Critical
## 2: Error
## 3: Warning
## 4: Info
## 5: Debug
##
loglevel: 4
##
## rotation: Describe how to rotate logs. Either size and/or date can trigger
## log rotation. Setting count to N keeps N rotated logs. Setting count to 0
## does not disable rotation, it instead rotates the file and keeps no previous
## versions around. Setting size to X rotate log when it reaches X bytes.
## To disable rotation set the size to 0 and the date to ""
## Date syntax is taken from the syntax newsyslog uses in newsyslog.conf.
## Some examples:
## $D0 rotate every night at midnight
## $D23 rotate every day at 23:00 hr
## $W0D23 rotate every week on Sunday at 23:00 hr
## $W5D16 rotate every week on Friday at 16:00 hr
## $M1D0 rotate on the first day of every month at midnight
## $M5D6 rotate on every 5th day of the month at 6:00 hr
##
log_rotate_size: 10485760
log_rotate_date: ""
log_rotate_count: 1
##
## overload protection: If you want to limit the number of messages per second
## allowed from error_logger, which is a good idea if you want to avoid a flood
## of messages when system is overloaded, you can set a limit.
## 100 is ejabberd's default.
log_rate_limit: 100
##
## watchdog_admins: Only useful for developers: if an ejabberd process
## consumes a lot of memory, send live notifications to these XMPP
## accounts.
##
## watchdog_admins:
## - "admin@xmpp"
###. ===============
###' NODE PARAMETERS
##
## net_ticktime: Specifies net_kernel tick time in seconds. This options must have
## identical value on all nodes, and in most cases shouldn't be changed at all from
## default value.
##
## net_ticktime: 60
###. ================
###' SERVED HOSTNAMES
##
## hosts: Domains served by ejabberd.
## You can define one or several, for example:
## hosts:
## - "example.net"
## - "example.com"
## - "example.org"
##
hosts:
- "example.com"
##
## route_subdomains: Delegate subdomains to other XMPP servers.
## For example, if this ejabberd serves example.org and you want
## to allow communication with an XMPP server called im.example.org.
##
## route_subdomains: s2s
###. ============
###' Certificates
## List all available PEM files containing certificates for your domains,
## chains of certificates or certificate keys. Full chains will be built
## automatically by ejabberd.
##
certfiles:
## - "/opt/ejabberd-18.06/conf/server.pem"
- "/opt/ejabberd/conf/server.pem"
## - "/etc/letsencrypt/live/example.org/*.pem"
## - "/etc/letsencrypt/live/example.com/*.pem"
ca_file: "/opt/ejabberd-18.06/conf/cacert.pem"
###. =================
###' TLS configuration
## Note that the following configuration is the default
## configuration of the TLS driver, so you don't need to
## uncomment it.
##
define_macro:
'TLS_CIPHERS': "HIGH:!aNULL:!eNULL:!3DES:@STRENGTH"
'TLS_OPTIONS':
- "no_sslv3"
- "cipher_server_preference"
- "no_compression"
'DH_FILE': "/opt/ejabberd-18.06/conf/dhparams.pem" # generated with: openssl dhparam -out dhparams.pem 2048
##
c2s_dhfile: 'DH_FILE'
s2s_dhfile: 'DH_FILE'
c2s_ciphers: 'TLS_CIPHERS'
s2s_ciphers: 'TLS_CIPHERS'
c2s_protocol_options: 'TLS_OPTIONS'
s2s_protocol_options: 'TLS_OPTIONS'
###. ===============
###' LISTENING PORTS
##
## listen: The ports ejabberd will listen on, which service each is handled
## by and what options to start it with.
##
listen:
-
port: 5222
ip: "::"
module: ejabberd_c2s
## starttls: true
##
## To enforce TLS encryption for client connections,
## use this instead of the "starttls" option:
##
starttls_required: true
##
## Stream compression
##
## zlib: true
##
max_stanza_size: 65536
shaper: c2s_shaper
access: c2s
-
port: 5269
ip: "::"
module: ejabberd_s2s_in
max_stanza_size: 131072
shaper: s2s_shaper
-
port: 5280
ip: "::"
module: ejabberd_http
request_handlers:
"/ws": ejabberd_http_ws
"/bosh": mod_bosh
"/oauth": ejabberd_oauth
"/api": mod_http_api
"/upload": mod_http_upload
## "/pub/archive": mod_http_fileserver
web_admin: true
register: true
tls: true
http_bind: true
protocol_options: 'TLS_OPTIONS'
dhfile: 'DH_FILE'
ciphers: 'TLS_CIPHERS'
captcha: true
##
## Direct-TLS for C2S (XEP-0368). A good practice is to forward
## traffic from port 443 to this port, possibly multiplexing it
## with HTTP using e.g. sslh [https://wiki.xmpp.org/web/Tech_pages/XEP-0368],
## so modern clients can bypass restrictive firewalls (in airports, hotels, etc.).
##
## -
## port: 5223
## ip: "::"
## module: ejabberd_c2s
## tls: true
## max_stanza_size: 65536
## shaper: c2s_shaper
## access: c2s
##
## ejabberd_service: Interact with external components (transports, ...)
##
## -
## port: 8888
## ip: "::"
## module: ejabberd_service
## access: all
## shaper_rule: fast
## ip: "127.0.0.1"
## privilege_access:
## roster: "both"
## message: "outgoing"
## presence: "roster"
## delegations:
## "urn:xmpp:mam:1":
## filtering: ["node"]
## "http://jabber.org/protocol/pubsub":
## filtering:
## hosts:
## "icq.example.org":
## password: "secret"
## "sms.example.org":
## password: "secret"
##
## ejabberd_stun: Handles STUN Binding requests
##
## -
## port: 3478
## transport: udp
## module: ejabberd_stun
##
## To handle XML-RPC requests that provide admin credentials:
##
## -
## port: 4560
## ip: "::"
## module: ejabberd_xmlrpc
## maxsessions: 10
## timeout: 5000
## access_commands:
## admin:
## commands: all
## options:
##
## To enable secure http upload
##
## -
## port: 5444
## ip: "::"
## module: ejabberd_http
## request_handlers:
## "/upload": mod_http_upload
## tls: true
## protocol_options: 'TLS_OPTIONS'
## dhfile: 'DH_FILE'
## ciphers: 'TLS_CIPHERS'
## Disabling digest-md5 SASL authentication. digest-md5 requires plain-text
## password storage (see auth_password_format option).
## disable_sasl_mechanisms: "digest-md5"
###. ==================
###' S2S GLOBAL OPTIONS
##
## s2s_use_starttls: Enable STARTTLS for S2S connections.
## Allowed values are: false, optional or required
## You must specify 'certfiles' option
##
s2s_use_starttls: required
##
## S2S whitelist or blacklist
##
## Default s2s policy for undefined hosts.
##
## s2s_access: s2s
##
## Outgoing S2S options
##
## Preferred address families (which to try first) and connect timeout
## in seconds.
##
## outgoing_s2s_families:
## - ipv4
## - ipv6
## outgoing_s2s_timeout: 190
###. ==============
###' AUTHENTICATION
##
## auth_method: Method used to authenticate the users.
## The default method is the internal.
## If you want to use a different method,
## comment this line and enable the correct ones.
##
auth_method: internal
##
## Store the plain passwords or hashed for SCRAM:
## auth_password_format: plain
auth_password_format: scram
##
## Define the FQDN if ejabberd doesn't detect it:
## fqdn: "server3.example.com"
##
## Authentication using external script
## Make sure the script is executable by ejabberd.
##
## auth_method: external
## extauth_program: "/path/to/authentication/script"
##
## Authentication using SQL
## Remember to setup a database in the next section.
##
## auth_method: sql
##
## Authentication using PAM
##
## auth_method: pam
## pam_service: "pamservicename"
##
## Authentication using LDAP
##
## auth_method: ldap
##
## List of LDAP servers:
## ldap_servers:
## - "localhost"
##
## Encryption of connection to LDAP servers:
## ldap_encrypt: none
## ldap_encrypt: tls
##
## Port to connect to on LDAP servers:
## ldap_port: 389
## ldap_port: 636
##
## LDAP manager:
## ldap_rootdn: "dc=example,dc=com"
##
## Password of LDAP manager:
## ldap_password: "fdfgdfg******"
##
## Search base of LDAP directory:
## ldap_base: "dc=example,dc=com"
##
## LDAP attribute that holds user ID:
## ldap_uids:
## - "mail": "%u@mail.example.org"
##
## LDAP filter:
## ldap_filter: "(objectClass=shadowAccount)"
##
## Anonymous login support:
## auth_method: anonymous
## anonymous_protocol: sasl_anon | login_anon | both
## allow_multiple_connections: true | false
##
## host_config:
## "public.example.org":
## auth_method: anonymous
## allow_multiple_connections: false
## anonymous_protocol: sasl_anon
##
## To use both anonymous and internal authentication:
##
## host_config:
## "public.example.org":
## auth_method:
## - internal
## - anonymous
###. ==============
###' DATABASE SETUP
## ejabberd by default uses the internal Mnesia database,
## so you do not necessarily need this section.
## This section provides configuration examples in case
## you want to use other database backends.
## Please consult the ejabberd Guide for details on database creation.
##
## MySQL server:
##
## sql_type: mysql
## sql_server: "server"
## sql_database: "database"
## sql_username: "username"
## sql_password: "password"
##
## If you want to specify the port:
## sql_port: 1234
##
## PostgreSQL server:
##
## sql_type: pgsql
## sql_server: "server"
## sql_database: "database"
## sql_username: "username"
## sql_password: "password"
##
## If you want to specify the port:
## sql_port: 1234
##
## If you use PostgreSQL, have a large database, and need a
## faster but inexact replacement for "select count(*) from users"
##
## pgsql_users_number_estimate: true
##
## SQLite:
##
## sql_type: sqlite
## sql_database: "/opt/ejabberd-18.06/database/ejabberd.db"
##
## ODBC compatible or MSSQL server:
##
## sql_type: odbc
## sql_server: "DSN=ejabberd;UID=ejabberd;PWD=ejabberd"
##
## Number of connections to open to the database for each virtual host
##
## sql_pool_size: 10
##
## Interval to make a dummy SQL request to keep the connections to the
## database alive. Specify in seconds: for example 28800 means 8 hours
##
## sql_keepalive_interval: undefined
##
## Use the new SQL schema
##
## new_sql_schema: true
###. ===============
###' TRAFFIC SHAPERS
shaper:
##
## The "normal" shaper limits traffic speed to 1000 B/s
##
normal: 1000
##
## The "fast" shaper limits traffic speed to 50000 B/s
##
fast: 50000
##
## This option specifies the maximum number of elements in the queue
## of the FSM. Refer to the documentation for details.
##
max_fsm_queue: 10000
###. ====================
###' ACCESS CONTROL LISTS
acl:
##
## The 'admin' ACL grants administrative privileges to XMPP accounts.
## You can put here as many accounts as you want.
##
admin:
user:
- "tester@example.com"
##
## Blocked users
##
## blocked:
## user:
## - "baduser@example.org"
## - "test"
## Local users: don't modify this.
##
local:
user_regexp: ""
##
## More examples of ACLs
##
## jabberorg:
## server:
## - "jabber.org"
## aleksey:
## user:
## - "aleksey@jabber.ru"
## test:
## user_regexp: "^test"
## user_glob: "test*"
##
## Loopback network
##
loopback:
ip:
- "127.0.0.0/8"
- "::1/128"
- "::FFFF:127.0.0.1/128"
##
## Bad XMPP servers
##
## bad_servers:
## server:
## - "xmpp.zombie.org"
## - "xmpp.spam.com"
##
## Define specific ACLs in a virtual host.
##
## host_config:
## "localhost":
## acl:
## admin:
## user:
## - "bob-local@localhost"
###. ============
###' SHAPER RULES
shaper_rules:
## Maximum number of simultaneous sessions allowed for a single user:
max_user_sessions: 10
## Maximum number of offline messages that users can have:
max_user_offline_messages:
- 5000: admin
- 100
## For C2S connections, all users except admins use the "normal" shaper
c2s_shaper:
- none: admin
- normal
## All S2S connections use the "fast" shaper
s2s_shaper: fast
###. ============
###' ACCESS RULES
access_rules:
## This rule allows access only for local users:
local:
- allow: local
## Only non-blocked users can use c2s connections:
c2s:
- deny: blocked
- allow
## Only admins can send announcement messages:
announce:
- allow: admin
## Only admins can use the configuration interface:
configure:
- allow: admin
## Only accounts of the local ejabberd server can create rooms:
muc_create:
- allow: local
## Only accounts on the local ejabberd server can create Pubsub nodes:
pubsub_createnode:
- allow: local
## In-band registration allows registration of any possible username.
## To disable in-band registration, replace 'allow' with 'deny'.
register:
- allow: all
## Only allow to register from localhost
## trusted_network:
## - allow: loopback
## Do not establish S2S connections with bad servers
## If you enable this you also have to uncomment "s2s_access: s2s"
## s2s:
## - deny:
## - ip: "XXX.XXX.XXX.XXX/32"
## - deny:
## - ip: "XXX.XXX.XXX.XXX/32"
## - allow
## ===============
## API PERMISSIONS
## ===============
##
## This section allows you to define who and using what method
## can execute commands offered by ejabberd.
##
## By default "console commands" section allow executing all commands
## issued using ejabberdctl command, and "admin access" section allows
## users in admin acl that connect from 127.0.0.1 to execute all
## commands except start and stop with any available access method
## (ejabberdctl, http-api, xmlrpc depending what is enabled on server).
##
## If you remove "console commands" there will be one added by
## default allowing executing all commands, but if you just change
## permissions in it, version from config file will be used instead
## of default one.
##
api_permissions:
"console commands":
from:
- ejabberd_ctl
who: all
what: "*"
"admin access":
who:
- access:
- allow:
- acl: loopback
- acl: admin
- oauth:
- scope: "ejabberd:admin"
- access:
- allow:
- acl: loopback
- acl: admin
what:
- "*"
- "!stop"
- "!start"
"public commands":
who:
- ip: "127.0.0.1/8"
what:
- "status"
- "connected_users_number"
## By default the frequency of account registrations from the same IP
## is limited to 1 account every 10 minutes. To disable, specify: infinity
## registration_timeout: 600
##
## Define specific Access Rules in a virtual host.
##
## host_config:
## "localhost":
## access:
## c2s:
## - allow: admin
## - deny
## register:
## - deny
###. ================
###' DEFAULT LANGUAGE
##
## language: Default language used for server messages.
##
language: "de"
##
## Set a different default language in a virtual host.
##
## host_config:
## "localhost":
## language: "ru"
###. =======
###' CAPTCHA
##
## Full path to a script that generates the image.
##
captcha_cmd: "/opt/ejabberd-18.06/lib/ejabberd-18.06/priv/bin/captcha.sh"
##
## Host for the URL and port where ejabberd listens for CAPTCHA requests.
##
## captcha_host: "xmpp:5280"
## captcha_host: "example.com:5280"
captcha_host: "https://example.com"
##
## Limit CAPTCHA calls per minute for JID/IP to avoid DoS.
##
captcha_limit: 5
###. ====
###' ACME
##
## In order to use the acme certificate acquiring through "Let's Encrypt"
## an http listener has to be configured to listen to port 80 so that
## the authorization challenges posed by "Let's Encrypt" can be solved.
##
## A simple way of doing this would be to add the following in the listening
## section and to configure port forwarding from 80 to 5280 either via NAT
## (for ipv4 only) or using frontends such as haproxy/nginx/sslh/etc.
## -
## port: 5280
## ip: "::"
## module: ejabberd_http
acme:
## A contact mail that the ACME Certificate Authority can contact in case of
## an authorization issue, such as a server-initiated certificate revocation.
## It is not mandatory to provide an email address but it is highly suggested.
contact: "mailto:admin@xmpp"
## The ACME Certificate Authority URL.
## This could either be:
## - https://acme-v01.api.letsencrypt.org - (Default) for the production CA
## - https://acme-staging.api.letsencrypt.org - for the staging CA
## - http://localhost:4000 - for a local version of the CA
ca_url: "https://acme-v01.api.letsencrypt.org"
###. =======
###' MODULES
##
## Modules enabled in all ejabberd virtual hosts.
##
modules:
mod_adhoc: {}
mod_admin_extra: {}
mod_announce: # recommends mod_adhoc
access: announce
mod_blocking: {} # requires mod_privacy
mod_caps: {}
mod_carboncopy: {}
mod_client_state: {}
mod_configure: {} # requires mod_adhoc
## mod_delegation: {} # for xep0356
mod_disco: {}
## mod_echo: {}
## mod_irc: {}
mod_bosh: {}
## mod_http_fileserver:
## docroot: "/var/www"
## accesslog: "/opt/ejabberd-18.06/logs/access.log"
mod_http_upload:
## host: "@HOST@"
docroot: "@HOME@/upload"
put_url: "https://@HOST@/upload"
## thumbnail: false # otherwise needs ejabberd to be compiled with libgd support
mod_http_upload_quota:
max_days: 30
mod_last: {}
## XEP-0313: Message Archive Management
## You might want to setup a SQL backend for MAM because the mnesia database is
## limited to 2GB which might be exceeded on large servers
mod_mam: # for xep0313, mnesia is limited to 2GB, better use an SQL backend
default: roster
mod_muc:
host: "conference.@HOST@"
access:
- allow
access_admin:
- allow: admin
access_create: muc_create
access_persistent: muc_create
default_room_options:
allow_subscription: true
mod_muc_admin: {}
mod_muc_log: {}
mod_multicast: {}
mod_offline:
access_max_user_messages: max_user_offline_messages
mod_ping: {}
mod_pres_counter:
count: 5
interval: 60
mod_privacy: {}
mod_private: {}
## mod_proxy65: {}
mod_pubsub:
access_createnode: pubsub_createnode
## reduces resource comsumption, but XEP incompliant
ignore_pep_from_offline: true
## XEP compliant, but increases resource comsumption
## ignore_pep_from_offline: false
last_item_cache: false
max_items_node: 10
plugins:
- "flat"
- "pep" # pep requires mod_caps
force_node_config:
## Avoid using OMEMO by default because it
## introduces a lot of hard-to-track problems
## "eu.siacs.conversations.axolotl.*":
## access_model: whitelist
## Avoid buggy clients to make their bookmarks public
"storage:bookmarks":
access_model: whitelist
mod_push:
include_body: "New message"
## mod_push: {}
mod_push_keepalive: {}
mod_register:
##
## Protect In-Band account registrations with CAPTCHA.
##
captcha_protected: true
##
## Set the minimum informational entropy for passwords.
##
password_strength: 32
##
## After successful registration, the user receives
## a message with this subject and body.
##
welcome_message:
subject: "Moin!"
body: |-
Tach.
Willkommen auf meinem XMPP server.
##
## When a user registers, send a notification to
## these XMPP accounts.
##
## registration_watchers:
## - "admin1@example.org"
##
## Only clients in the server machine can register accounts
##
ip_access: all
## ip_access: trusted_network
##
## Local c2s or remote s2s users cannot register accounts
##
## access_from: deny
access: register
mod_register_web: {}
mod_roster: {}
mod_shared_roster: {}
## mod_stats: {}
## mod_time: {}
mod_vcard:
search: false
mod_vcard_xupdate: {}
mod_avatar: {}
mod_version: {}
mod_stream_mgmt: {}
## Non-SASL Authentication (XEP-0078) is now disabled by default
## because it's obsoleted and is used mostly by abandoned
## client software
## mod_legacy_auth: {}
## The module for S2S dialback (XEP-0220). Please note that you cannot
## rely solely on dialback if you want to federate with other servers,
## because a lot of servers have dialback disabled and instead rely on
## PKIX authentication. Make sure you have proper certificates installed
## and check your accessibility at https://check.messaging.one/
mod_s2s_dialback: {}
mod_http_api: {}
mod_fail2ban: {}
##
## Enable modules with custom options in a specific virtual host
##
## host_config:
## "localhost":
## modules:
## mod_echo:
## host: "mirror.localhost"
##
## Enable modules management via ejabberdctl for installation and
## uninstallation of public/private contributed modules
## (enabled by default)
##
allow_contrib_modules: true
###.
###'
### Local Variables:
### mode: yaml
### End:
### vim: set filetype=yaml tabstop=8 foldmarker=###',###. foldmethod=marker: Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 379912
Url: https://administrator.de/tutorial/ejabberd-auf-ubuntu-379912.html
Ausgedruckt am: 31.07.2025 um 07:07 Uhr
1 Kommentar