Cisco router with zone based firewall and port forwarding

This tutorial is a short extension to the more comprehensive local Cisco Tutorial.
Due to several requests regarding port forwarding and combination with a secure DMZ segment it quickly shows a more detailed configuration of Ciscos modern, onboard Zone Based Firewall (ZFW) in IOS and IOS-XE in combination with port forwarding.
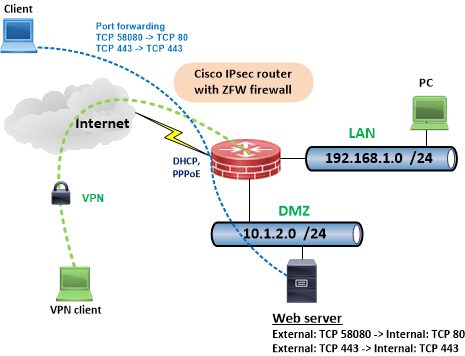
The basic configuration is kept intentionally simple, so that it can be used for more sophisticated ZFW setups as a blueprint.
The example shows a web- or private cloudserver in the DMZ zone which is accessible via port forwarding from the Internet. (HTTP with port translation)
Example zone rules are as follows and must be set to individual requirements:
- LAN --> Internet: All allowed with extended protocol inspection
- LAN --> DMZ: Only HTTP and HTTPS traffic allowed, no Ping (ICMP)
- DMZ --> Internet: Only HTTP, HTTPS, DNS, NTP and ICMP (Ping etc.) traffic allowed
- Internet --> DMZ: Only HTTP and HTTPS traffic allowed
❗️Relevant content related maps and profiles, as well as zone pairings use the same color to show their relationship in the configuration.
service timestamps debug datetime localtime
service timestamps log datetime localtime show-timezone year
!
hostname cisco
!
aaa new-model
!
clock timezone CET 1 0
clock summer-time CEST recurring last Sun Mar 2:00 last Sun Oct 3:00
!
!
ip dhcp excluded-address 192.168.1.1 192.168.1.10
ip dhcp excluded-address 192.168.1.250 192.168.1.254
ip dhcp excluded-address 10.1.2.1 10.1.2.10
ip dhcp excluded-address 10.1.2.50 10.1.2.254
!
ip dhcp pool LAN
network 192.168.1.0 255.255.255.0
default-router 192.168.1.1
domain-name cisco.home.arpa
dns-server 192.168.1.1
!
ip dhcp pool DMZ
network 10.1.2.0 255.255.255.0
default-router 10.1.2.1
domain-name cisco.home.arpa
dns-server 10.1.2.1
!
ip dhcp pool Server
host 10.1.2.55 255.255.255.0 -> Optional: Server gets static IP via Mac address reservation.
client-identifier 0102.42ba.67fb.4a
!
!
ip domain lookup source-interface GigabitEthernet4
ip domain name cisco.home.arpa
ip host server.cisco.home.arpa 10.1.2.55
!
lldp run
no cdp run
!
!
class-map type inspect match-any ALLOW_IN
match access-group name ALLOWv4
match access-group name ALLOWv6
class-map type inspect match-any ROUTER
match protocol tcp
match protocol udp
match protocol icmp
class-map type inspect match-any PORTFW
match access-group name PORTFW_ACL
class-map type inspect match-any LAN
match protocol dns
match protocol http
match protocol https
match protocol pop3s
match protocol pop3
match protocol imaps
match protocol imap3
match protocol imap
match protocol smtp
match protocol ssh
match protocol ntp
match protocol tcp
match protocol udp
match protocol icmp
class-map type inspect match-any DMZ -> Define protocols allowed for DMZ.
match protocol dns
match protocol http
match protocol https
match protocol ntp
match protocol icmp
class-map type inspect match-any LAN_DMZ
match protocol http
match protocol https
(class-map type inspect match-any DHCPv4 -> Optional: Only if WAN port is in DHCPv4 client mode! (See here)
match access-group name DHCPv4)
!
!
policy-map type inspect LANtoInternet
description Traffic LAN to Internet
class type inspect LAN
inspect
class class-default
drop
policy-map type inspect LANtoDMZ
description Traffic LAN to DMZ
class type inspect LAN_DMZ
inspect
class class-default
drop
policy-map type inspect DMZtoInternet
description Traffic DMZ to Internet
class type inspect DMZ
inspect
class class-default
drop
policy-map type inspect InternetToDMZ
description Traffic Internet to DMZ
class type inspect PORTFW
inspect
class class-default
drop
policy-map type inspect RouterToInternet
description Router (and DHCPv4) traffic to Internet
(class type inspect DHCPv4 -> Optional: Only if WAN port is in DHCPv4 client mode! (See here)
pass )
class type inspect ROUTER
inspect
class class-default
drop
policy-map type inspect InternetToRouter
description Permitted traffic Internet to router
class type inspect ALLOW_IN
pass
class class-default
drop
!
zone security Internet
zone security LAN
zone security DMZ
!
zone-pair security LanToInternet source LAN destination Internet
description Traffic LAN to Internet
service-policy type inspect LANtoInternet
zone-pair security LanToDMZ source LAN destination DMZ
description Traffic LAN to DMZ
service-policy type inspect LANtoDMZ
zone-pair security InternetToRouter source Internet destination self
description Traffic Internet to Router
service-policy type inspect InternetToRouter
zone-pair security RouterToInternet source self destination Internet
description Traffic Router to Internet
service-policy type inspect RouterToInternet
zone-pair security DMZtoInternet source DMZ destination Internet
description Traffic DMZ to Internet
service-policy type inspect DMZtoInternet
zone-pair security InternetToDMZ source Internet destination DMZ
description Traffic Internet to DMZ
service-policy type inspect InternetToDMZ
!
!
interface Vlan1
description Local LAN
ip address 192.168.1.1 255.255.255.0
ip nat inside
zone-member security LAN
!
interface Vlan10
description DMZ
ip address 10.1.2.1 255.255.255.0
ip nat inside
zone-member security DMZ
!
interface GigabitEthernet4
description Internet Port
ip address dhcp -> Can also be PPPoE etc.
ip nat outside
zone-member security Internet
!
!
ip dns server
ip nat inside source static tcp 10.1.2.55 80 interface GigabitEthernet4 58080 extendable
-> Port forwarding (58080, external) and translation to 80 (internal)
ip nat inside source static tcp 10.1.2.55 443 interface GigabitEthernet4 443 extendable -> Port forwarding (443)
ip nat inside source route-map NONAT interface GigabitEthernet4 overload
!
!
ip access-list extended ALLOWv4
remark Allowed to WAN ip address (VPN)
(permit udp any eq bootps any eq bootpc) -> Optional: Only if WAN port in DHCPv4 client mode!
permit udp any any eq 1701
permit udp any any eq isakmp
permit udp any any eq non500-isakmp
permit esp any any
!
ipv6 access-list ALLOWv6
remark Allowed v6 to Firewall
permit udp any eq 547 any eq 546
!
(ip access-list extended DHCPv4 -> Optional ACL: Only if WAN port in DHCPv4 client mode!
remark Pass DHCPv4 WAN traffic
permit udp any eq bootpc any eq bootps)
!
ip access-list extended NAT
remark Allowed IPs for NAT
permit ip 192.168.1.0 0.0.0.255 any
permit ip 10.1.2.0 0.0.0.255 any
!
ip access-list extended PORTFW_ACL
remark Pass portforwarded traffic
permit tcp any host 10.1.2.55 eq 80
permit tcp any host 10.1.2.55 eq 443
!
route-map NONAT permit 10 -> Maps to extended ACL "NAT"
match ip address NAT
!
ntp source GigabitEthernet4
ntp server de.pool.ntp.org
!
end
Cisco ZFW design guide:
cisco.com/c/en/us/support/docs/security/ios-firewall/98628-zone- ...
ZFW firewall secured VPNs with Mikrotik and AVM FritzBox:
Cisco IPsec VPN with Mikrotik or FritzBox
Cisco router configuration tutorial:
Cisco 800, 900, ISR1100 Router Konfiguration mit xDSL, Kabel, FTTH Anschluss und VPN
Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 5247066805
Url: https://administrator.de/tutorial/cisco-router-with-zone-based-firewall-and-port-forwarding-5247066805.html
Ausgedruckt am: 16.07.2025 um 18:07 Uhr
Serie: Cisco-Tutorials
Cisco router with zone based firewall and port forwarding (englisch)Cisco IPsec VPN with Mikrotik or FritzBox (englisch)Cisco WLAN Access Points for Home Use: 1142N, 2702, 3702 and 3800 Comparison (englisch)Cisco, Mikrotik, pfSense site-to-site VPN with dynamic routing (englisch)1Cisco WLAN Access Points 3800, 3702, 2702 für den Heimgebrauch umrüsten124Cisco Telefon für All IP Anschluss, FritzBox und andere VoIP Anlagen fit machen183Cisco 800, 900, ISR1100 Router Konfiguration mit xDSL, Kabel, FTTH Anschluss und VPN285