Pfsense VPN site-to-site multiple phase 2 child SA-Einträge
aktuell habe ich eine IPSec IKEv2 site-to-site VPN Verbindung zwischen einem Zyxel Router (hinter NAT) und einer pfSense.
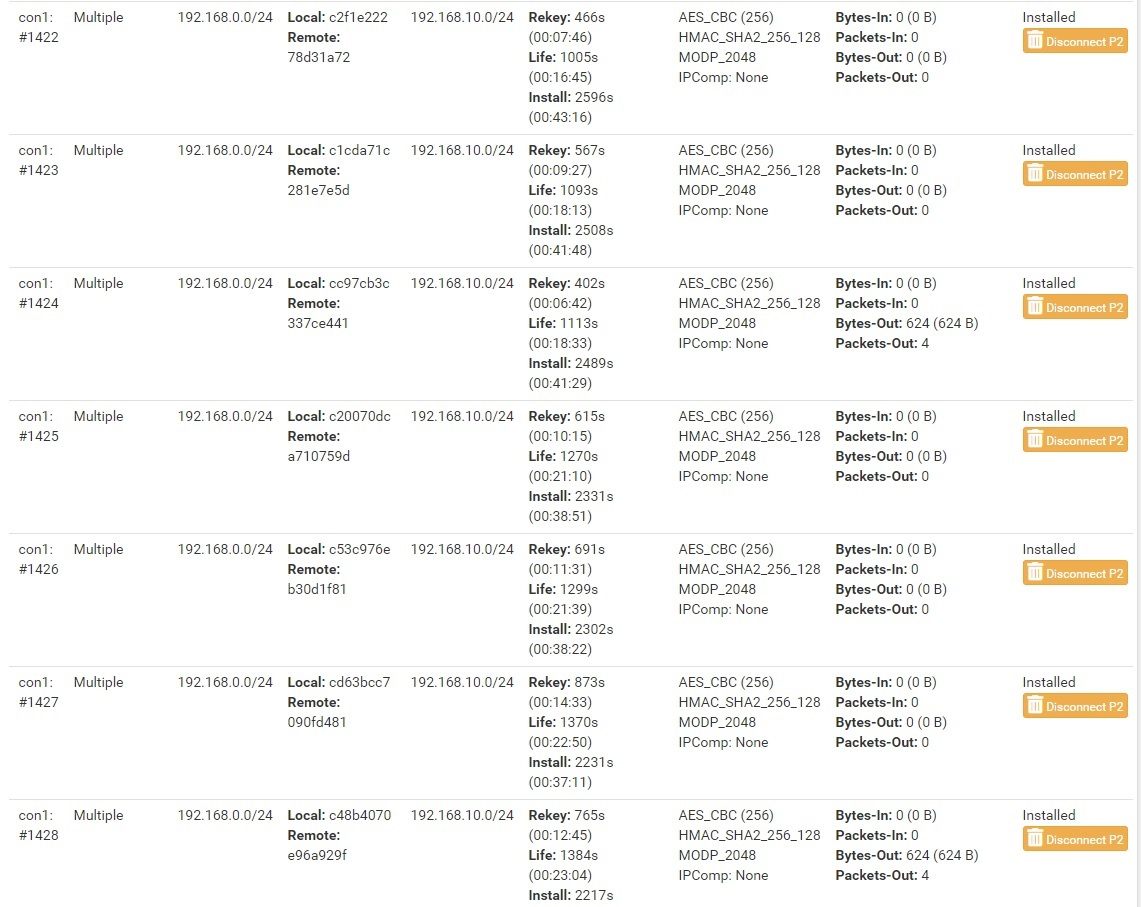
Bei Phase 2 habe ich 2 Einträge, für meine 2 Subnetze, jedoch kriege ich multiple child SA-Einträge für eines dieser(20/20).
Dadurch kann meine zweite Phase 2 Verbindung, sobald ein Rekey ansteht, keine erneute Verbindung aufbauen
Anbei ein Screenshot von den multiplen Einträgen.
Weiß jemand woran es liegen könnte? SA lifetime Konfiguration stimmen beim Zyxel und Pfsense überein. Die gleichen Einstellungen hatte ich bereits vorher problemlos mit einer site-to-site Verbindung zwischen Zyxel und Lancom(statt Pfsense) verwendet.
Content-ID: 7002498628
Url: https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html
Ausgedruckt am: 13.07.2025 um 16:07 Uhr
- Kommentarübersicht - Bitte anmelden
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7002829829
[content:7002498628#7002829829]
Screenshot Peer Übersicht wäre ggf. hilfreich. Und... wie immer: Was steht im pfSense IPsec Log?? (Dort im Log Setup ggf. die Reihenfolge auf "Aktuelles zuerst" ändern und vorab löschen damit alte Einträge nicht verwirren)
Zyxel Log wäre auch hilfreich.
Weitere Details findest du im hiesigen IKEv2 Tutorial für die pfSense und OPNsense:
IPsec IKEv2 Standort VPN Vernetzung mit Cisco, pfSense OPNsense und Mikrotik
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7016747640
[content:7002498628#7016747640]
Was ich bisher getan habe: Zyxel(hinter NAT) SA lifetime für Phase 1 und Phase 2 auf 90% der pfSense Werte reduziert, damit die Rekey Anfrage stets vom Zyxel aus erfolgt.
Beide Phase 2 SA sind komplett identisch.
Hier die Log:
May 4 17:31:32 charon 35095 15[KNL] creating rekey job for CHILD_SA ESP/0xce240976/pfsenseip
May 4 17:31:32 charon 35095 11[IKE] <con1|133> queueing CHILD_REKEY task
May 4 17:31:32 charon 35095 11[IKE] <con1|133> activating new tasks
May 4 17:31:32 charon 35095 11[IKE] <con1|133> activating CHILD_REKEY task
May 4 17:31:32 charon 35095 11[CFG] <con1|133> proposing traffic selectors for us:
May 4 17:31:32 charon 35095 11[CFG] <con1|133> 192.168.0.0/24|/0
May 4 17:31:32 charon 35095 11[CFG] <con1|133> 192.168.3.0/24|/0
May 4 17:31:32 charon 35095 11[CFG] <con1|133> proposing traffic selectors for other:
May 4 17:31:32 charon 35095 11[CFG] <con1|133> 192.168.10.0/24|/0
May 4 17:31:32 charon 35095 11[CFG] <con1|133> 192.168.10.0/24|/0
May 4 17:31:32 charon 35095 11[CFG] <con1|133> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:31:32 charon 35095 11[IKE] <con1|133> establishing CHILD_SA con1{1637} reqid 2
May 4 17:31:32 charon 35095 11[CHD] <con1|133> CHILD_SA con1{1627} state change: INSTALLED => REKEYING
May 4 17:31:32 charon 35095 11[ENC] <con1|133> generating CREATE_CHILD_SA request 348 [ N(REKEY_SA) N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 4 17:31:32 charon 35095 11[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (512 bytes)
May 4 17:31:33 charon 35095 11[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (496 bytes)
May 4 17:31:33 charon 35095 11[ENC] <con1|133> parsed CREATE_CHILD_SA response 348 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 4 17:31:33 charon 35095 11[IKE] <con1|133> received ESP_TFC_PADDING_NOT_SUPPORTED notify
May 4 17:31:33 charon 35095 11[IKE] <con1|133> received NON_FIRST_FRAGMENTS_ALSO notify
May 4 17:31:33 charon 35095 11[IKE] <con1|133> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 4 17:31:33 charon 35095 11[CFG] <con1|133> selecting proposal:
May 4 17:31:33 charon 35095 11[CFG] <con1|133> proposal matches
May 4 17:31:33 charon 35095 11[CFG] <con1|133> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:31:33 charon 35095 11[CFG] <con1|133> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:31:33 charon 35095 11[CFG] <con1|133> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:31:33 charon 35095 11[CFG] <con1|133> selecting traffic selectors for us:
May 4 17:31:33 charon 35095 11[CFG] <con1|133> config: 192.168.0.0/24|/0, received: 192.168.0.0/24|/0 => match: 192.168.0.0/24|/0
May 4 17:31:33 charon 35095 11[CFG] <con1|133> config: 192.168.3.0/24|/0, received: 192.168.0.0/24|/0 => no match
May 4 17:31:33 charon 35095 11[CFG] <con1|133> selecting traffic selectors for other:
May 4 17:31:33 charon 35095 11[CFG] <con1|133> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 4 17:31:33 charon 35095 11[CFG] <con1|133> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 4 17:31:33 charon 35095 11[CHD] <con1|133> CHILD_SA con1{1637} state change: CREATED => INSTALLING
May 4 17:31:33 charon 35095 11[CHD] <con1|133> using AES_CBC for encryption
May 4 17:31:33 charon 35095 11[CHD] <con1|133> using HMAC_SHA2_256_128 for integrity
May 4 17:31:33 charon 35095 11[CHD] <con1|133> adding inbound ESP SA
May 4 17:31:33 charon 35095 11[CHD] <con1|133> SPI 0xc5bbc159, src zyxelip dst pfsenseip
May 4 17:31:33 charon 35095 11[CHD] <con1|133> registering outbound ESP SA
May 4 17:31:33 charon 35095 11[CHD] <con1|133> SPI 0x4072e77a, src pfsenseip dst zyxelip
May 4 17:31:33 charon 35095 11[IKE] <con1|133> inbound CHILD_SA con1{1637} established with SPIs c5bbc159_i 4072e77a_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:31:33 charon 35095 11[CHD] <con1|133> CHILD_SA con1{1637} state change: INSTALLING => INSTALLED
May 4 17:31:33 charon 35095 11[CHD] <con1|133> adding outbound ESP SA
May 4 17:31:33 charon 35095 11[CHD] <con1|133> SPI 0x4072e77a, src pfsenseip dst zyxelip
May 4 17:31:33 charon 35095 11[IKE] <con1|133> outbound CHILD_SA con1{1637} established with SPIs c5bbc159_i 4072e77a_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:31:33 charon 35095 11[CHD] <con1|133> CHILD_SA con1{1627} state change: REKEYING => REKEYED
May 4 17:31:33 charon 35095 11[IKE] <con1|133> reinitiating already active tasks
May 4 17:31:33 charon 35095 11[IKE] <con1|133> CHILD_REKEY task
May 4 17:31:33 charon 35095 11[IKE] <con1|133> closing CHILD_SA con1{1627} with SPIs ce240976_i (4032 bytes) 6eaafb32_o (0 bytes) and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:31:33 charon 35095 11[IKE] <con1|133> sending DELETE for ESP CHILD_SA with SPI ce240976
May 4 17:31:33 charon 35095 11[CHD] <con1|133> CHILD_SA con1{1627} state change: REKEYED => DELETING
May 4 17:31:33 charon 35095 11[ENC] <con1|133> generating INFORMATIONAL request 349 [ D ]
May 4 17:31:33 charon 35095 11[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:31:33 charon 35095 15[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:31:33 charon 35095 15[ENC] <con1|133> parsed INFORMATIONAL request 551 [ D ]
May 4 17:31:33 charon 35095 15[IKE] <con1|133> received DELETE for ESP CHILD_SA with SPI 6eaafb32
May 4 17:31:33 charon 35095 15[IKE] <con1|133> CHILD_SA closed
May 4 17:31:33 charon 35095 15[ENC] <con1|133> generating INFORMATIONAL response 551 [ ]
May 4 17:31:33 charon 35095 15[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:31:33 charon 35095 15[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:31:33 charon 35095 15[ENC] <con1|133> parsed INFORMATIONAL response 349 [ ]
May 4 17:31:33 charon 35095 15[IKE] <con1|133> CHILD_SA closed
May 4 17:31:33 charon 35095 15[CHD] <con1|133> CHILD_SA con1{1627} state change: DELETING => DELETED
May 4 17:31:33 charon 35095 15[IKE] <con1|133> activating new tasks
May 4 17:31:33 charon 35095 15[IKE] <con1|133> nothing to initiate
May 4 17:31:38 charon 35095 08[IKE] <con1|133> queueing CHILD_DELETE task
May 4 17:31:38 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:31:38 charon 35095 08[IKE] <con1|133> activating CHILD_DELETE task
May 4 17:31:38 charon 35095 08[CHD] <con1|133> CHILD_SA con1{1627} state change: DELETED => DESTROYING
May 4 17:31:38 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:31:38 charon 35095 08[IKE] <con1|133> nothing to initiate
May 4 17:31:49 charon 35095 15[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:31:49 charon 35095 15[ENC] <con1|133> parsed INFORMATIONAL request 552 [ ]
May 4 17:31:49 charon 35095 15[ENC] <con1|133> generating INFORMATIONAL response 552 [ ]
May 4 17:31:49 charon 35095 15[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:32:07 charon 35095 15[IKE] <con1|133> sending DPD request
May 4 17:32:07 charon 35095 15[IKE] <con1|133> queueing IKE_DPD task
May 4 17:32:07 charon 35095 15[IKE] <con1|133> activating new tasks
May 4 17:32:07 charon 35095 15[IKE] <con1|133> activating IKE_DPD task
May 4 17:32:07 charon 35095 15[ENC] <con1|133> generating INFORMATIONAL request 350 [ ]
May 4 17:32:07 charon 35095 15[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:32:07 charon 35095 15[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:32:07 charon 35095 15[ENC] <con1|133> parsed INFORMATIONAL response 350 [ ]
May 4 17:32:07 charon 35095 15[IKE] <con1|133> activating new tasks
May 4 17:32:07 charon 35095 15[IKE] <con1|133> nothing to initiate
May 4 17:32:19 charon 35095 08[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:32:19 charon 35095 08[ENC] <con1|133> parsed INFORMATIONAL request 553 [ ]
May 4 17:32:19 charon 35095 08[ENC] <con1|133> generating INFORMATIONAL response 553 [ ]
May 4 17:32:19 charon 35095 08[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:32:29 charon 35095 08[IKE] <con1|133> sending DPD request
May 4 17:32:29 charon 35095 08[IKE] <con1|133> queueing IKE_DPD task
May 4 17:32:29 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:32:29 charon 35095 08[IKE] <con1|133> activating IKE_DPD task
May 4 17:32:29 charon 35095 08[ENC] <con1|133> generating INFORMATIONAL request 351 [ ]
May 4 17:32:29 charon 35095 08[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:32:29 charon 35095 08[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:32:29 charon 35095 08[ENC] <con1|133> parsed INFORMATIONAL response 351 [ ]
May 4 17:32:29 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:32:29 charon 35095 08[IKE] <con1|133> nothing to initiate
May 4 17:32:39 charon 35095 08[IKE] <con1|133> sending DPD request
May 4 17:32:39 charon 35095 08[IKE] <con1|133> queueing IKE_DPD task
May 4 17:32:39 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:32:39 charon 35095 08[IKE] <con1|133> activating IKE_DPD task
May 4 17:32:39 charon 35095 08[ENC] <con1|133> generating INFORMATIONAL request 352 [ ]
May 4 17:32:39 charon 35095 08[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:32:39 charon 35095 08[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:32:39 charon 35095 08[ENC] <con1|133> parsed INFORMATIONAL response 352 [ ]
May 4 17:32:39 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:32:39 charon 35095 08[IKE] <con1|133> nothing to initiate
May 4 17:32:49 charon 35095 08[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:32:49 charon 35095 08[ENC] <con1|133> parsed INFORMATIONAL request 554 [ ]
May 4 17:32:49 charon 35095 08[ENC] <con1|133> generating INFORMATIONAL response 554 [ ]
May 4 17:32:49 charon 35095 08[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:32:59 charon 35095 08[IKE] <con1|133> sending DPD request
May 4 17:32:59 charon 35095 08[IKE] <con1|133> queueing IKE_DPD task
May 4 17:32:59 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:32:59 charon 35095 08[IKE] <con1|133> activating IKE_DPD task
May 4 17:32:59 charon 35095 08[ENC] <con1|133> generating INFORMATIONAL request 353 [ ]
May 4 17:32:59 charon 35095 08[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:32:59 charon 35095 08[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:32:59 charon 35095 08[ENC] <con1|133> parsed INFORMATIONAL response 353 [ ]
May 4 17:32:59 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:32:59 charon 35095 08[IKE] <con1|133> nothing to initiate
May 4 17:33:09 charon 35095 08[IKE] <con1|133> sending DPD request
May 4 17:33:09 charon 35095 08[IKE] <con1|133> queueing IKE_DPD task
May 4 17:33:09 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:33:09 charon 35095 08[IKE] <con1|133> activating IKE_DPD task
May 4 17:33:09 charon 35095 08[ENC] <con1|133> generating INFORMATIONAL request 354 [ ]
May 4 17:33:09 charon 35095 08[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:33:09 charon 35095 08[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:33:09 charon 35095 08[ENC] <con1|133> parsed INFORMATIONAL response 354 [ ]
May 4 17:33:09 charon 35095 08[IKE] <con1|133> activating new tasks
May 4 17:33:09 charon 35095 08[IKE] <con1|133> nothing to initiate
May 4 17:33:19 charon 35095 14[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:33:19 charon 35095 14[ENC] <con1|133> parsed INFORMATIONAL request 555 [ ]
May 4 17:33:19 charon 35095 14[ENC] <con1|133> generating INFORMATIONAL response 555 [ ]
May 4 17:33:19 charon 35095 14[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:33:30 charon 35095 14[IKE] <con1|133> sending DPD request
May 4 17:33:30 charon 35095 14[IKE] <con1|133> queueing IKE_DPD task
May 4 17:33:30 charon 35095 14[IKE] <con1|133> activating new tasks
May 4 17:33:30 charon 35095 14[IKE] <con1|133> activating IKE_DPD task
May 4 17:33:30 charon 35095 14[ENC] <con1|133> generating INFORMATIONAL request 355 [ ]
May 4 17:33:30 charon 35095 14[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:33:30 charon 35095 14[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:33:30 charon 35095 14[ENC] <con1|133> parsed INFORMATIONAL response 355 [ ]
May 4 17:33:30 charon 35095 14[IKE] <con1|133> activating new tasks
May 4 17:33:30 charon 35095 14[IKE] <con1|133> nothing to initiate
May 4 17:33:49 charon 35095 14[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:33:49 charon 35095 14[ENC] <con1|133> parsed INFORMATIONAL request 556 [ ]
May 4 17:33:49 charon 35095 14[ENC] <con1|133> generating INFORMATIONAL response 556 [ ]
May 4 17:33:49 charon 35095 14[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:33:53 charon 35095 14[KNL] creating rekey job for CHILD_SA ESP/0xa379cb6d/zyxelip
May 4 17:33:53 charon 35095 09[IKE] <con1|133> queueing CHILD_REKEY task
May 4 17:33:53 charon 35095 09[IKE] <con1|133> activating new tasks
May 4 17:33:53 charon 35095 09[IKE] <con1|133> activating CHILD_REKEY task
May 4 17:33:53 charon 35095 09[CFG] <con1|133> proposing traffic selectors for us:
May 4 17:33:53 charon 35095 09[CFG] <con1|133> 192.168.0.0/24|/0
May 4 17:33:53 charon 35095 09[CFG] <con1|133> 192.168.3.0/24|/0
May 4 17:33:53 charon 35095 09[CFG] <con1|133> proposing traffic selectors for other:
May 4 17:33:53 charon 35095 09[CFG] <con1|133> 192.168.10.0/24|/0
May 4 17:33:53 charon 35095 09[CFG] <con1|133> 192.168.10.0/24|/0
May 4 17:33:53 charon 35095 09[CFG] <con1|133> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:33:53 charon 35095 09[IKE] <con1|133> establishing CHILD_SA con1{1638} reqid 2
May 4 17:33:53 charon 35095 09[CHD] <con1|133> CHILD_SA con1{1626} state change: INSTALLED => REKEYING
May 4 17:33:53 charon 35095 09[ENC] <con1|133> generating CREATE_CHILD_SA request 356 [ N(REKEY_SA) N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 4 17:33:53 charon 35095 09[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (512 bytes)
May 4 17:33:54 charon 35095 09[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (496 bytes)
May 4 17:33:54 charon 35095 09[ENC] <con1|133> parsed CREATE_CHILD_SA response 356 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 4 17:33:54 charon 35095 09[IKE] <con1|133> received ESP_TFC_PADDING_NOT_SUPPORTED notify
May 4 17:33:54 charon 35095 09[IKE] <con1|133> received NON_FIRST_FRAGMENTS_ALSO notify
May 4 17:33:54 charon 35095 09[IKE] <con1|133> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 4 17:33:54 charon 35095 09[CFG] <con1|133> selecting proposal:
May 4 17:33:54 charon 35095 09[CFG] <con1|133> proposal matches
May 4 17:33:54 charon 35095 09[CFG] <con1|133> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:33:54 charon 35095 09[CFG] <con1|133> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:33:54 charon 35095 09[CFG] <con1|133> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:33:54 charon 35095 09[CFG] <con1|133> selecting traffic selectors for us:
May 4 17:33:54 charon 35095 09[CFG] <con1|133> config: 192.168.0.0/24|/0, received: 192.168.0.0/24|/0 => match: 192.168.0.0/24|/0
May 4 17:33:54 charon 35095 09[CFG] <con1|133> config: 192.168.3.0/24|/0, received: 192.168.0.0/24|/0 => no match
May 4 17:33:54 charon 35095 09[CFG] <con1|133> selecting traffic selectors for other:
May 4 17:33:54 charon 35095 09[CFG] <con1|133> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 4 17:33:54 charon 35095 09[CFG] <con1|133> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 4 17:33:54 charon 35095 09[CHD] <con1|133> CHILD_SA con1{1638} state change: CREATED => INSTALLING
May 4 17:33:54 charon 35095 09[CHD] <con1|133> using AES_CBC for encryption
May 4 17:33:54 charon 35095 09[CHD] <con1|133> using HMAC_SHA2_256_128 for integrity
May 4 17:33:54 charon 35095 09[CHD] <con1|133> adding inbound ESP SA
May 4 17:33:54 charon 35095 09[CHD] <con1|133> SPI 0xceaa49f7, src zyxelip dst pfsenseip
May 4 17:33:54 charon 35095 09[CHD] <con1|133> registering outbound ESP SA
May 4 17:33:54 charon 35095 09[CHD] <con1|133> SPI 0xa587a00b, src pfsenseip dst zyxelip
May 4 17:33:54 charon 35095 09[IKE] <con1|133> inbound CHILD_SA con1{1638} established with SPIs ceaa49f7_i a587a00b_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:33:54 charon 35095 09[CHD] <con1|133> CHILD_SA con1{1638} state change: INSTALLING => INSTALLED
May 4 17:33:54 charon 35095 09[CHD] <con1|133> adding outbound ESP SA
May 4 17:33:54 charon 35095 09[CHD] <con1|133> SPI 0xa587a00b, src pfsenseip dst zyxelip
May 4 17:33:54 charon 35095 09[IKE] <con1|133> outbound CHILD_SA con1{1638} established with SPIs ceaa49f7_i a587a00b_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:33:54 charon 35095 09[CHD] <con1|133> CHILD_SA con1{1626} state change: REKEYING => REKEYED
May 4 17:33:54 charon 35095 09[IKE] <con1|133> reinitiating already active tasks
May 4 17:33:54 charon 35095 09[IKE] <con1|133> CHILD_REKEY task
May 4 17:33:54 charon 35095 09[IKE] <con1|133> closing CHILD_SA con1{1626} with SPIs ca21e420_i (0 bytes) a379cb6d_o (24236 bytes) and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:33:54 charon 35095 09[IKE] <con1|133> sending DELETE for ESP CHILD_SA with SPI ca21e420
May 4 17:33:54 charon 35095 09[CHD] <con1|133> CHILD_SA con1{1626} state change: REKEYED => DELETING
May 4 17:33:54 charon 35095 09[ENC] <con1|133> generating INFORMATIONAL request 357 [ D ]
May 4 17:33:54 charon 35095 09[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:33:54 charon 35095 09[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:33:54 charon 35095 09[ENC] <con1|133> parsed INFORMATIONAL response 357 [ ]
May 4 17:33:54 charon 35095 09[IKE] <con1|133> CHILD_SA closed
May 4 17:33:54 charon 35095 09[CHD] <con1|133> CHILD_SA con1{1626} state change: DELETING => DELETED
May 4 17:33:54 charon 35095 09[IKE] <con1|133> activating new tasks
May 4 17:33:54 charon 35095 09[IKE] <con1|133> nothing to initiate
May 4 17:33:55 charon 35095 09[KNL] creating rekey job for CHILD_SA ESP/0xca21e420/pfsenseip
May 4 17:33:55 charon 35095 06[IKE] <con1|133> queueing CHILD_REKEY task
May 4 17:33:55 charon 35095 06[IKE] <con1|133> activating new tasks
May 4 17:33:55 charon 35095 06[IKE] <con1|133> activating CHILD_REKEY task
May 4 17:33:55 charon 35095 06[IKE] <con1|133> activating new tasks
May 4 17:33:55 charon 35095 06[IKE] <con1|133> nothing to initiate
May 4 17:33:59 charon 35095 06[IKE] <con1|133> queueing CHILD_DELETE task
May 4 17:33:59 charon 35095 06[IKE] <con1|133> activating new tasks
May 4 17:33:59 charon 35095 06[IKE] <con1|133> activating CHILD_DELETE task
May 4 17:33:59 charon 35095 06[CHD] <con1|133> CHILD_SA con1{1626} state change: DELETED => DESTROYING
May 4 17:33:59 charon 35095 06[IKE] <con1|133> activating new tasks
May 4 17:33:59 charon 35095 06[IKE] <con1|133> nothing to initiate
May 4 17:34:05 charon 35095 09[IKE] <con1|133> sending DPD request
May 4 17:34:05 charon 35095 09[IKE] <con1|133> queueing IKE_DPD task
May 4 17:34:05 charon 35095 09[IKE] <con1|133> activating new tasks
May 4 17:34:05 charon 35095 09[IKE] <con1|133> activating IKE_DPD task
May 4 17:34:05 charon 35095 09[ENC] <con1|133> generating INFORMATIONAL request 358 [ ]
May 4 17:34:05 charon 35095 09[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:34:05 charon 35095 09[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:34:05 charon 35095 09[ENC] <con1|133> parsed INFORMATIONAL response 358 [ ]
May 4 17:34:05 charon 35095 09[IKE] <con1|133> activating new tasks
May 4 17:34:05 charon 35095 09[IKE] <con1|133> nothing to initiate
May 4 17:34:15 charon 35095 09[IKE] <con1|133> sending DPD request
May 4 17:34:15 charon 35095 09[IKE] <con1|133> queueing IKE_DPD task
May 4 17:34:15 charon 35095 09[IKE] <con1|133> activating new tasks
May 4 17:34:15 charon 35095 09[IKE] <con1|133> activating IKE_DPD task
May 4 17:34:15 charon 35095 09[ENC] <con1|133> generating INFORMATIONAL request 359 [ ]
May 4 17:34:15 charon 35095 09[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:34:15 charon 35095 09[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:34:15 charon 35095 09[ENC] <con1|133> parsed INFORMATIONAL response 359 [ ]
May 4 17:34:15 charon 35095 09[IKE] <con1|133> activating new tasks
May 4 17:34:15 charon 35095 09[IKE] <con1|133> nothing to initiate
May 4 17:34:19 charon 35095 09[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:34:19 charon 35095 09[ENC] <con1|133> parsed INFORMATIONAL request 557 [ ]
May 4 17:34:19 charon 35095 09[ENC] <con1|133> generating INFORMATIONAL response 557 [ ]
May 4 17:34:19 charon 35095 09[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:34:49 charon 35095 06[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:34:49 charon 35095 06[ENC] <con1|133> parsed INFORMATIONAL request 558 [ ]
May 4 17:34:49 charon 35095 06[ENC] <con1|133> generating INFORMATIONAL response 558 [ ]
May 4 17:34:49 charon 35095 06[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:34:57 charon 35095 06[KNL] creating rekey job for CHILD_SA ESP/0xd3b37afe/zyxelip
May 4 17:34:57 charon 35095 10[IKE] <con1|133> queueing CHILD_REKEY task
May 4 17:34:57 charon 35095 10[IKE] <con1|133> activating new tasks
May 4 17:34:57 charon 35095 10[IKE] <con1|133> activating CHILD_REKEY task
May 4 17:34:57 charon 35095 10[CFG] <con1|133> proposing traffic selectors for us:
May 4 17:34:57 charon 35095 10[CFG] <con1|133> 192.168.0.0/24|/0
May 4 17:34:57 charon 35095 10[CFG] <con1|133> 192.168.3.0/24|/0
May 4 17:34:57 charon 35095 10[CFG] <con1|133> proposing traffic selectors for other:
May 4 17:34:57 charon 35095 10[CFG] <con1|133> 192.168.10.0/24|/0
May 4 17:34:57 charon 35095 10[CFG] <con1|133> 192.168.10.0/24|/0
May 4 17:34:57 charon 35095 10[CFG] <con1|133> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:34:57 charon 35095 10[IKE] <con1|133> establishing CHILD_SA con1{1639} reqid 2
May 4 17:34:57 charon 35095 10[CHD] <con1|133> CHILD_SA con1{1629} state change: INSTALLED => REKEYING
May 4 17:34:57 charon 35095 10[ENC] <con1|133> generating CREATE_CHILD_SA request 360 [ N(REKEY_SA) N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 4 17:34:57 charon 35095 10[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (512 bytes)
May 4 17:34:59 charon 35095 10[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (496 bytes)
May 4 17:34:59 charon 35095 10[ENC] <con1|133> parsed CREATE_CHILD_SA response 360 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 4 17:34:59 charon 35095 10[IKE] <con1|133> received ESP_TFC_PADDING_NOT_SUPPORTED notify
May 4 17:34:59 charon 35095 10[IKE] <con1|133> received NON_FIRST_FRAGMENTS_ALSO notify
May 4 17:34:59 charon 35095 10[IKE] <con1|133> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 4 17:34:59 charon 35095 10[CFG] <con1|133> selecting proposal:
May 4 17:34:59 charon 35095 10[CFG] <con1|133> proposal matches
May 4 17:34:59 charon 35095 10[CFG] <con1|133> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:34:59 charon 35095 10[CFG] <con1|133> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:34:59 charon 35095 10[CFG] <con1|133> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:34:59 charon 35095 10[CFG] <con1|133> selecting traffic selectors for us:
May 4 17:34:59 charon 35095 10[CFG] <con1|133> config: 192.168.0.0/24|/0, received: 192.168.0.0/24|/0 => match: 192.168.0.0/24|/0
May 4 17:34:59 charon 35095 10[CFG] <con1|133> config: 192.168.3.0/24|/0, received: 192.168.0.0/24|/0 => no match
May 4 17:34:59 charon 35095 10[CFG] <con1|133> selecting traffic selectors for other:
May 4 17:34:59 charon 35095 10[CFG] <con1|133> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 4 17:34:59 charon 35095 10[CFG] <con1|133> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 4 17:34:59 charon 35095 10[CHD] <con1|133> CHILD_SA con1{1639} state change: CREATED => INSTALLING
May 4 17:34:59 charon 35095 10[CHD] <con1|133> using AES_CBC for encryption
May 4 17:34:59 charon 35095 10[CHD] <con1|133> using HMAC_SHA2_256_128 for integrity
May 4 17:34:59 charon 35095 10[CHD] <con1|133> adding inbound ESP SA
May 4 17:34:59 charon 35095 10[CHD] <con1|133> SPI 0xc686d901, src zyxelip dst pfsenseip
May 4 17:34:59 charon 35095 10[CHD] <con1|133> registering outbound ESP SA
May 4 17:34:59 charon 35095 10[CHD] <con1|133> SPI 0x1e51ee95, src pfsenseip dst zyxelip
May 4 17:34:59 charon 35095 10[IKE] <con1|133> inbound CHILD_SA con1{1639} established with SPIs c686d901_i 1e51ee95_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:34:59 charon 35095 10[CHD] <con1|133> CHILD_SA con1{1639} state change: INSTALLING => INSTALLED
May 4 17:34:59 charon 35095 10[CHD] <con1|133> adding outbound ESP SA
May 4 17:34:59 charon 35095 10[CHD] <con1|133> SPI 0x1e51ee95, src pfsenseip dst zyxelip
May 4 17:34:59 charon 35095 10[IKE] <con1|133> outbound CHILD_SA con1{1639} established with SPIs c686d901_i 1e51ee95_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:34:59 charon 35095 10[CHD] <con1|133> CHILD_SA con1{1629} state change: REKEYING => REKEYED
May 4 17:34:59 charon 35095 10[IKE] <con1|133> reinitiating already active tasks
May 4 17:34:59 charon 35095 10[IKE] <con1|133> CHILD_REKEY task
May 4 17:34:59 charon 35095 10[IKE] <con1|133> closing CHILD_SA con1{1629} with SPIs c7c91884_i (0 bytes) d3b37afe_o (3172 bytes) and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:34:59 charon 35095 10[IKE] <con1|133> sending DELETE for ESP CHILD_SA with SPI c7c91884
May 4 17:34:59 charon 35095 10[CHD] <con1|133> CHILD_SA con1{1629} state change: REKEYED => DELETING
May 4 17:34:59 charon 35095 10[ENC] <con1|133> generating INFORMATIONAL request 361 [ D ]
May 4 17:34:59 charon 35095 10[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:34:59 charon 35095 10[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:34:59 charon 35095 10[ENC] <con1|133> parsed INFORMATIONAL response 361 [ ]
May 4 17:34:59 charon 35095 10[IKE] <con1|133> CHILD_SA closed
May 4 17:34:59 charon 35095 10[CHD] <con1|133> CHILD_SA con1{1629} state change: DELETING => DELETED
May 4 17:34:59 charon 35095 10[IKE] <con1|133> activating new tasks
May 4 17:34:59 charon 35095 10[IKE] <con1|133> nothing to initiate
May 4 17:35:04 charon 35095 06[IKE] <con1|133> queueing CHILD_DELETE task
May 4 17:35:04 charon 35095 06[IKE] <con1|133> activating new tasks
May 4 17:35:04 charon 35095 06[IKE] <con1|133> activating CHILD_DELETE task
May 4 17:35:04 charon 35095 06[CHD] <con1|133> CHILD_SA con1{1629} state change: DELETED => DESTROYING
May 4 17:35:04 charon 35095 06[IKE] <con1|133> activating new tasks
May 4 17:35:04 charon 35095 06[IKE] <con1|133> nothing to initiate
May 4 17:35:19 charon 35095 07[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:35:19 charon 35095 07[ENC] <con1|133> parsed INFORMATIONAL request 559 [ ]
May 4 17:35:19 charon 35095 07[ENC] <con1|133> generating INFORMATIONAL response 559 [ ]
May 4 17:35:19 charon 35095 07[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:35:28 charon 35095 07[IKE] <con1|133> sending DPD request
May 4 17:35:28 charon 35095 07[IKE] <con1|133> queueing IKE_DPD task
May 4 17:35:28 charon 35095 07[IKE] <con1|133> activating new tasks
May 4 17:35:28 charon 35095 07[IKE] <con1|133> activating IKE_DPD task
May 4 17:35:28 charon 35095 07[ENC] <con1|133> generating INFORMATIONAL request 362 [ ]
May 4 17:35:28 charon 35095 07[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:35:28 charon 35095 07[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:35:28 charon 35095 07[ENC] <con1|133> parsed INFORMATIONAL response 362 [ ]
May 4 17:35:28 charon 35095 07[IKE] <con1|133> activating new tasks
May 4 17:35:28 charon 35095 07[IKE] <con1|133> nothing to initiate
May 4 17:35:40 charon 35095 07[KNL] creating rekey job for CHILD_SA ESP/0xc4bad3f9/pfsenseip
May 4 17:35:40 charon 35095 06[IKE] <con1|133> queueing CHILD_REKEY task
May 4 17:35:40 charon 35095 06[IKE] <con1|133> activating new tasks
May 4 17:35:40 charon 35095 06[IKE] <con1|133> activating CHILD_REKEY task
May 4 17:35:40 charon 35095 06[CFG] <con1|133> proposing traffic selectors for us:
May 4 17:35:40 charon 35095 06[CFG] <con1|133> 192.168.0.0/24|/0
May 4 17:35:40 charon 35095 06[CFG] <con1|133> 192.168.3.0/24|/0
May 4 17:35:40 charon 35095 06[CFG] <con1|133> proposing traffic selectors for other:
May 4 17:35:40 charon 35095 06[CFG] <con1|133> 192.168.10.0/24|/0
May 4 17:35:40 charon 35095 06[CFG] <con1|133> 192.168.10.0/24|/0
May 4 17:35:40 charon 35095 06[CFG] <con1|133> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:35:40 charon 35095 06[IKE] <con1|133> establishing CHILD_SA con1{1640} reqid 2
May 4 17:35:40 charon 35095 06[CHD] <con1|133> CHILD_SA con1{1630} state change: INSTALLED => REKEYING
May 4 17:35:40 charon 35095 06[ENC] <con1|133> generating CREATE_CHILD_SA request 363 [ N(REKEY_SA) N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 4 17:35:40 charon 35095 06[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (512 bytes)
May 4 17:35:41 charon 35095 06[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (496 bytes)
May 4 17:35:41 charon 35095 06[ENC] <con1|133> parsed CREATE_CHILD_SA response 363 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 4 17:35:41 charon 35095 06[IKE] <con1|133> received ESP_TFC_PADDING_NOT_SUPPORTED notify
May 4 17:35:41 charon 35095 06[IKE] <con1|133> received NON_FIRST_FRAGMENTS_ALSO notify
May 4 17:35:41 charon 35095 06[IKE] <con1|133> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 4 17:35:41 charon 35095 06[CFG] <con1|133> selecting proposal:
May 4 17:35:41 charon 35095 06[CFG] <con1|133> proposal matches
May 4 17:35:41 charon 35095 06[CFG] <con1|133> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:35:41 charon 35095 06[CFG] <con1|133> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:35:41 charon 35095 06[CFG] <con1|133> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 4 17:35:41 charon 35095 06[CFG] <con1|133> selecting traffic selectors for us:
May 4 17:35:41 charon 35095 06[CFG] <con1|133> config: 192.168.0.0/24|/0, received: 192.168.0.0/24|/0 => match: 192.168.0.0/24|/0
May 4 17:35:41 charon 35095 06[CFG] <con1|133> config: 192.168.3.0/24|/0, received: 192.168.0.0/24|/0 => no match
May 4 17:35:41 charon 35095 06[CFG] <con1|133> selecting traffic selectors for other:
May 4 17:35:41 charon 35095 06[CFG] <con1|133> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 4 17:35:41 charon 35095 06[CFG] <con1|133> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 4 17:35:41 charon 35095 06[CHD] <con1|133> CHILD_SA con1{1640} state change: CREATED => INSTALLING
May 4 17:35:41 charon 35095 06[CHD] <con1|133> using AES_CBC for encryption
May 4 17:35:41 charon 35095 06[CHD] <con1|133> using HMAC_SHA2_256_128 for integrity
May 4 17:35:41 charon 35095 06[CHD] <con1|133> adding inbound ESP SA
May 4 17:35:41 charon 35095 06[CHD] <con1|133> SPI 0xcf90204b, src zyxelip dst pfsenseip
May 4 17:35:41 charon 35095 06[CHD] <con1|133> registering outbound ESP SA
May 4 17:35:41 charon 35095 06[CHD] <con1|133> SPI 0x538d661d, src pfsenseip dst zyxelip
May 4 17:35:41 charon 35095 06[IKE] <con1|133> inbound CHILD_SA con1{1640} established with SPIs cf90204b_i 538d661d_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:35:41 charon 35095 06[CHD] <con1|133> CHILD_SA con1{1640} state change: INSTALLING => INSTALLED
May 4 17:35:41 charon 35095 06[CHD] <con1|133> adding outbound ESP SA
May 4 17:35:41 charon 35095 06[CHD] <con1|133> SPI 0x538d661d, src pfsenseip dst zyxelip
May 4 17:35:41 charon 35095 06[IKE] <con1|133> outbound CHILD_SA con1{1640} established with SPIs cf90204b_i 538d661d_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:35:41 charon 35095 06[CHD] <con1|133> CHILD_SA con1{1630} state change: REKEYING => REKEYED
May 4 17:35:41 charon 35095 06[IKE] <con1|133> reinitiating already active tasks
May 4 17:35:41 charon 35095 06[IKE] <con1|133> CHILD_REKEY task
May 4 17:35:41 charon 35095 06[IKE] <con1|133> closing CHILD_SA con1{1630} with SPIs c4bad3f9_i (0 bytes) 23770feb_o (97108 bytes) and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 4 17:35:41 charon 35095 06[IKE] <con1|133> sending DELETE for ESP CHILD_SA with SPI c4bad3f9
May 4 17:35:41 charon 35095 06[CHD] <con1|133> CHILD_SA con1{1630} state change: REKEYED => DELETING
May 4 17:35:41 charon 35095 06[ENC] <con1|133> generating INFORMATIONAL request 364 [ D ]
May 4 17:35:41 charon 35095 06[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:35:41 charon 35095 07[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:35:41 charon 35095 07[ENC] <con1|133> parsed INFORMATIONAL response 364 [ ]
May 4 17:35:41 charon 35095 07[IKE] <con1|133> CHILD_SA closed
May 4 17:35:41 charon 35095 07[CHD] <con1|133> CHILD_SA con1{1630} state change: DELETING => DELETED
May 4 17:35:41 charon 35095 07[IKE] <con1|133> activating new tasks
May 4 17:35:41 charon 35095 07[IKE] <con1|133> nothing to initiate
May 4 17:35:46 charon 35095 16[IKE] <con1|133> queueing CHILD_DELETE task
May 4 17:35:46 charon 35095 16[IKE] <con1|133> activating new tasks
May 4 17:35:46 charon 35095 16[IKE] <con1|133> activating CHILD_DELETE task
May 4 17:35:46 charon 35095 16[CHD] <con1|133> CHILD_SA con1{1630} state change: DELETED => DESTROYING
May 4 17:35:46 charon 35095 16[IKE] <con1|133> activating new tasks
May 4 17:35:46 charon 35095 16[IKE] <con1|133> nothing to initiate
May 4 17:35:48 charon 35095 07[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:35:48 charon 35095 07[ENC] <con1|133> parsed INFORMATIONAL request 560 [ ]
May 4 17:35:48 charon 35095 07[ENC] <con1|133> generating INFORMATIONAL response 560 [ ]
May 4 17:35:48 charon 35095 07[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:35:58 charon 35095 07[IKE] <con1|133> sending DPD request
May 4 17:35:58 charon 35095 07[IKE] <con1|133> queueing IKE_DPD task
May 4 17:35:58 charon 35095 07[IKE] <con1|133> activating new tasks
May 4 17:35:58 charon 35095 07[IKE] <con1|133> activating IKE_DPD task
May 4 17:35:58 charon 35095 07[ENC] <con1|133> generating INFORMATIONAL request 365 [ ]
May 4 17:35:58 charon 35095 07[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:35:58 charon 35095 07[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:35:58 charon 35095 07[ENC] <con1|133> parsed INFORMATIONAL response 365 [ ]
May 4 17:35:58 charon 35095 07[IKE] <con1|133> activating new tasks
May 4 17:35:58 charon 35095 07[IKE] <con1|133> nothing to initiate
May 4 17:36:10 charon 35095 16[CFG] vici client 8494 connected
May 4 17:36:10 charon 35095 13[CFG] vici client 8494 registered for: list-sa
May 4 17:36:10 charon 35095 07[CFG] vici client 8494 requests: list-sas
May 4 17:36:10 charon 35095 07[CFG] vici client 8494 disconnected
May 4 17:36:18 charon 35095 05[IKE] <con1|133> sending DPD request
May 4 17:36:18 charon 35095 05[IKE] <con1|133> queueing IKE_DPD task
May 4 17:36:18 charon 35095 05[IKE] <con1|133> activating new tasks
May 4 17:36:18 charon 35095 05[IKE] <con1|133> activating IKE_DPD task
May 4 17:36:18 charon 35095 05[ENC] <con1|133> generating INFORMATIONAL request 366 [ ]
May 4 17:36:18 charon 35095 05[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:36:18 charon 35095 12[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:36:18 charon 35095 12[ENC] <con1|133> parsed INFORMATIONAL response 366 [ ]
May 4 17:36:18 charon 35095 12[IKE] <con1|133> activating new tasks
May 4 17:36:18 charon 35095 12[IKE] <con1|133> nothing to initiate
May 4 17:36:18 charon 35095 12[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:36:18 charon 35095 12[ENC] <con1|133> parsed INFORMATIONAL request 561 [ ]
May 4 17:36:18 charon 35095 12[ENC] <con1|133> generating INFORMATIONAL response 561 [ ]
May 4 17:36:18 charon 35095 12[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:36:30 charon 35095 12[IKE] <con1|133> sending DPD request
May 4 17:36:30 charon 35095 12[IKE] <con1|133> queueing IKE_DPD task
May 4 17:36:30 charon 35095 12[IKE] <con1|133> activating new tasks
May 4 17:36:30 charon 35095 12[IKE] <con1|133> activating IKE_DPD task
May 4 17:36:30 charon 35095 12[ENC] <con1|133> generating INFORMATIONAL request 367 [ ]
May 4 17:36:30 charon 35095 12[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:36:30 charon 35095 12[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:36:30 charon 35095 12[ENC] <con1|133> parsed INFORMATIONAL response 367 [ ]
May 4 17:36:30 charon 35095 12[IKE] <con1|133> activating new tasks
May 4 17:36:30 charon 35095 12[IKE] <con1|133> nothing to initiate
May 4 17:36:40 charon 35095 12[IKE] <con1|133> sending DPD request
May 4 17:36:40 charon 35095 12[IKE] <con1|133> queueing IKE_DPD task
May 4 17:36:40 charon 35095 12[IKE] <con1|133> activating new tasks
May 4 17:36:40 charon 35095 12[IKE] <con1|133> activating IKE_DPD task
May 4 17:36:40 charon 35095 12[ENC] <con1|133> generating INFORMATIONAL request 368 [ ]
May 4 17:36:40 charon 35095 12[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:36:40 charon 35095 12[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:36:40 charon 35095 12[ENC] <con1|133> parsed INFORMATIONAL response 368 [ ]
May 4 17:36:40 charon 35095 12[IKE] <con1|133> activating new tasks
May 4 17:36:40 charon 35095 12[IKE] <con1|133> nothing to initiate
May 4 17:36:49 charon 35095 12[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:36:49 charon 35095 12[ENC] <con1|133> parsed INFORMATIONAL request 562 [ ]
May 4 17:36:49 charon 35095 12[ENC] <con1|133> generating INFORMATIONAL response 562 [ ]
May 4 17:36:49 charon 35095 12[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:36:58 charon 35095 12[IKE] <con1|133> sending DPD request
May 4 17:36:58 charon 35095 12[IKE] <con1|133> queueing IKE_DPD task
May 4 17:36:58 charon 35095 12[IKE] <con1|133> activating new tasks
May 4 17:36:58 charon 35095 12[IKE] <con1|133> activating IKE_DPD task
May 4 17:36:58 charon 35095 12[ENC] <con1|133> generating INFORMATIONAL request 369 [ ]
May 4 17:36:58 charon 35095 12[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:36:58 charon 35095 12[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:36:58 charon 35095 12[ENC] <con1|133> parsed INFORMATIONAL response 369 [ ]
May 4 17:36:58 charon 35095 12[IKE] <con1|133> activating new tasks
May 4 17:36:58 charon 35095 12[IKE] <con1|133> nothing to initiate
May 4 17:37:08 charon 35095 12[IKE] <con1|133> sending DPD request
May 4 17:37:08 charon 35095 12[IKE] <con1|133> queueing IKE_DPD task
May 4 17:37:08 charon 35095 12[IKE] <con1|133> activating new tasks
May 4 17:37:08 charon 35095 12[IKE] <con1|133> activating IKE_DPD task
May 4 17:37:08 charon 35095 12[ENC] <con1|133> generating INFORMATIONAL request 370 [ ]
May 4 17:37:08 charon 35095 12[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:37:08 charon 35095 11[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:37:08 charon 35095 11[ENC] <con1|133> parsed INFORMATIONAL response 370 [ ]
May 4 17:37:08 charon 35095 11[IKE] <con1|133> activating new tasks
May 4 17:37:08 charon 35095 11[IKE] <con1|133> nothing to initiate
May 4 17:37:18 charon 35095 11[IKE] <con1|133> sending DPD request
May 4 17:37:18 charon 35095 11[IKE] <con1|133> queueing IKE_DPD task
May 4 17:37:18 charon 35095 11[IKE] <con1|133> activating new tasks
May 4 17:37:18 charon 35095 11[IKE] <con1|133> activating IKE_DPD task
May 4 17:37:18 charon 35095 11[ENC] <con1|133> generating INFORMATIONAL request 371 [ ]
May 4 17:37:18 charon 35095 11[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:37:18 charon 35095 11[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:37:18 charon 35095 11[ENC] <con1|133> parsed INFORMATIONAL response 371 [ ]
May 4 17:37:18 charon 35095 11[IKE] <con1|133> activating new tasks
May 4 17:37:18 charon 35095 11[IKE] <con1|133> nothing to initiate
May 4 17:37:19 charon 35095 11[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:37:19 charon 35095 11[ENC] <con1|133> parsed INFORMATIONAL request 563 [ ]
May 4 17:37:19 charon 35095 11[ENC] <con1|133> generating INFORMATIONAL response 563 [ ]
May 4 17:37:19 charon 35095 11[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:37:49 charon 35095 11[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:37:49 charon 35095 11[ENC] <con1|133> parsed INFORMATIONAL request 564 [ ]
May 4 17:37:49 charon 35095 11[ENC] <con1|133> generating INFORMATIONAL response 564 [ ]
May 4 17:37:49 charon 35095 11[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:38:19 charon 35095 11[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:38:19 charon 35095 11[ENC] <con1|133> parsed INFORMATIONAL request 565 [ ]
May 4 17:38:19 charon 35095 11[ENC] <con1|133> generating INFORMATIONAL response 565 [ ]
May 4 17:38:19 charon 35095 11[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:38:49 charon 35095 15[NET] <con1|133> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 4 17:38:49 charon 35095 15[ENC] <con1|133> parsed INFORMATIONAL request 566 [ ]
May 4 17:38:49 charon 35095 15[ENC] <con1|133> generating INFORMATIONAL response 566 [ ]
May 4 17:38:49 charon 35095 15[NET] <con1|133> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 4 17:38:58 charon 35095 08[CFG] vici client 8495 connected
May 4 17:38:58 charon 35095 15[CFG] vici client 8495 registered for: list-sa
May 4 17:38:58 charon 35095 15[CFG] vici client 8495 requests: list-sas
May 4 17:38:58 charon 35095 08[CFG] vici client 8495 disconnected- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7017223342
[content:7002498628#7017223342]
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7025220233
[content:7002498628#7025220233]
Was den Charon Daemon angeht stehen HIER noch ein paar Dokus zum Rekeying Verhalten. Möglich das es an der Zyxel Seite liegt die sich nicht korrekt verhält.
Ggf. macht es einmal Sinn das Rekeying einseitig zu deaktivieren und das verhalten zu checken.
Ist PFS aktiviert auf beiden Seiten?
Nur so viel:
Ein Vergleichs Setup von IKEv2 mit einem Cisco Router und aktuellem IOS-XE sowie einem Mikrotik IKEv2 Router und aktuellem RouterOS 7.8 verhät sich völlig unauffällig und fehlerlos mit einer pfSense Ver.2.6. Es liegt also definitiv nicht an der pfSense oder dem Charon Daemon welcher so oder so überall im Hintergrund werkelt wie auch auf deinem Zyxel.
Ohne dein genaues Setup auf beiden Seiten zu kennen wird es schwierig ins Detail zu gehen ohne in Gefahr zu geraten wild rumzuraten.
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7030972727
[content:7002498628#7030972727]
May 5 17:27:34 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:28:04 charon 35095 12[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:28:04 charon 35095 12[ENC] <con1|141> parsed INFORMATIONAL request 954 [ ]
May 5 17:28:04 charon 35095 12[ENC] <con1|141> generating INFORMATIONAL response 954 [ ]
May 5 17:28:04 charon 35095 12[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:28:34 charon 35095 12[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:28:34 charon 35095 12[ENC] <con1|141> parsed INFORMATIONAL request 955 [ ]
May 5 17:28:34 charon 35095 12[ENC] <con1|141> generating INFORMATIONAL response 955 [ ]
May 5 17:28:34 charon 35095 12[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:28:41 charon 35095 06[CFG] vici client 9604 connected
May 5 17:28:41 charon 35095 12[CFG] vici client 9604 registered for: list-sa
May 5 17:28:41 charon 35095 05[CFG] vici client 9604 requests: list-sas
May 5 17:28:41 charon 35095 05[CFG] vici client 9604 disconnected
May 5 17:29:04 charon 35095 13[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:29:04 charon 35095 13[ENC] <con1|141> parsed INFORMATIONAL request 956 [ ]
May 5 17:29:04 charon 35095 13[ENC] <con1|141> generating INFORMATIONAL response 956 [ ]
May 5 17:29:04 charon 35095 13[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:29:33 charon 35095 15[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:29:33 charon 35095 15[ENC] <con1|141> parsed INFORMATIONAL request 957 [ ]
May 5 17:29:33 charon 35095 15[ENC] <con1|141> generating INFORMATIONAL response 957 [ ]
May 5 17:29:33 charon 35095 15[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:30:03 charon 35095 15[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:30:03 charon 35095 15[ENC] <con1|141> parsed INFORMATIONAL request 958 [ ]
May 5 17:30:03 charon 35095 15[ENC] <con1|141> generating INFORMATIONAL response 958 [ ]
May 5 17:30:03 charon 35095 15[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:30:34 charon 35095 15[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:30:34 charon 35095 15[ENC] <con1|141> parsed INFORMATIONAL request 959 [ ]
May 5 17:30:34 charon 35095 15[ENC] <con1|141> generating INFORMATIONAL response 959 [ ]
May 5 17:30:34 charon 35095 15[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:31:04 charon 35095 14[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:31:04 charon 35095 14[ENC] <con1|141> parsed INFORMATIONAL request 960 [ ]
May 5 17:31:04 charon 35095 14[ENC] <con1|141> generating INFORMATIONAL response 960 [ ]
May 5 17:31:04 charon 35095 14[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:31:34 charon 35095 14[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:31:34 charon 35095 14[ENC] <con1|141> parsed INFORMATIONAL request 961 [ ]
May 5 17:31:34 charon 35095 14[ENC] <con1|141> generating INFORMATIONAL response 961 [ ]
May 5 17:31:34 charon 35095 14[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:32:04 charon 35095 14[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:32:04 charon 35095 14[ENC] <con1|141> parsed INFORMATIONAL request 962 [ ]
May 5 17:32:04 charon 35095 14[ENC] <con1|141> generating INFORMATIONAL response 962 [ ]
May 5 17:32:04 charon 35095 14[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:32:34 charon 35095 14[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:32:34 charon 35095 14[ENC] <con1|141> parsed INFORMATIONAL request 963 [ ]
May 5 17:32:34 charon 35095 14[ENC] <con1|141> generating INFORMATIONAL response 963 [ ]
May 5 17:32:34 charon 35095 14[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:33:03 charon 35095 11[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:33:03 charon 35095 11[ENC] <con1|141> parsed INFORMATIONAL request 964 [ ]
May 5 17:33:03 charon 35095 11[ENC] <con1|141> generating INFORMATIONAL response 964 [ ]
May 5 17:33:03 charon 35095 11[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:33:34 charon 35095 11[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:33:34 charon 35095 11[ENC] <con1|141> parsed INFORMATIONAL request 965 [ ]
May 5 17:33:34 charon 35095 11[ENC] <con1|141> generating INFORMATIONAL response 965 [ ]
May 5 17:33:34 charon 35095 11[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:33:42 charon 35095 10[CFG] vici client 9605 connected
May 5 17:33:42 charon 35095 09[CFG] vici client 9605 registered for: list-sa
May 5 17:33:42 charon 35095 11[CFG] vici client 9605 requests: list-sas
May 5 17:33:42 charon 35095 11[CFG] vici client 9605 disconnected
May 5 17:34:04 charon 35095 08[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:34:04 charon 35095 08[ENC] <con1|141> parsed INFORMATIONAL request 966 [ ]
May 5 17:34:04 charon 35095 08[ENC] <con1|141> generating INFORMATIONAL response 966 [ ]
May 5 17:34:04 charon 35095 08[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:34:33 charon 35095 08[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:34:33 charon 35095 08[ENC] <con1|141> parsed INFORMATIONAL request 967 [ ]
May 5 17:34:33 charon 35095 08[ENC] <con1|141> generating INFORMATIONAL response 967 [ ]
May 5 17:34:33 charon 35095 08[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:34:59 charon 35095 08[KNL] creating rekey job for CHILD_SA ESP/0x3a901054/zyxelip
May 5 17:34:59 charon 35095 07[IKE] <con1|141> queueing CHILD_REKEY task
May 5 17:34:59 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:34:59 charon 35095 07[IKE] <con1|141> activating CHILD_REKEY task
May 5 17:34:59 charon 35095 07[CFG] <con1|141> proposing traffic selectors for us:
May 5 17:34:59 charon 35095 07[CFG] <con1|141> 192.168.0.0/24|/0
May 5 17:34:59 charon 35095 07[CFG] <con1|141> 192.168.3.0/24|/0
May 5 17:34:59 charon 35095 07[CFG] <con1|141> proposing traffic selectors for other:
May 5 17:34:59 charon 35095 07[CFG] <con1|141> 192.168.10.0/24|/0
May 5 17:34:59 charon 35095 07[CFG] <con1|141> 192.168.10.0/24|/0
May 5 17:34:59 charon 35095 07[CFG] <con1|141> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:34:59 charon 35095 07[IKE] <con1|141> establishing CHILD_SA con1{1813} reqid 2
May 5 17:34:59 charon 35095 07[CHD] <con1|141> CHILD_SA con1{1806} state change: INSTALLED => REKEYING
May 5 17:34:59 charon 35095 07[ENC] <con1|141> generating CREATE_CHILD_SA request 495 [ N(REKEY_SA) N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 5 17:34:59 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:35:00 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:35:00 charon 35095 07[ENC] <con1|141> parsed CREATE_CHILD_SA response 495 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 5 17:35:00 charon 35095 07[IKE] <con1|141> received ESP_TFC_PADDING_NOT_SUPPORTED notify
May 5 17:35:00 charon 35095 07[IKE] <con1|141> received NON_FIRST_FRAGMENTS_ALSO notify
May 5 17:35:00 charon 35095 07[IKE] <con1|141> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 5 17:35:00 charon 35095 07[CFG] <con1|141> selecting proposal:
May 5 17:35:00 charon 35095 07[CFG] <con1|141> proposal matches
May 5 17:35:00 charon 35095 07[CFG] <con1|141> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:35:00 charon 35095 07[CFG] <con1|141> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:35:00 charon 35095 07[CFG] <con1|141> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:35:00 charon 35095 07[CFG] <con1|141> selecting traffic selectors for us:
May 5 17:35:00 charon 35095 07[CFG] <con1|141> config: 192.168.0.0/24|/0, received: 192.168.0.0/24|/0 => match: 192.168.0.0/24|/0
May 5 17:35:00 charon 35095 07[CFG] <con1|141> config: 192.168.3.0/24|/0, received: 192.168.0.0/24|/0 => no match
May 5 17:35:00 charon 35095 07[CFG] <con1|141> selecting traffic selectors for other:
May 5 17:35:00 charon 35095 07[CFG] <con1|141> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 5 17:35:00 charon 35095 07[CFG] <con1|141> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 5 17:35:00 charon 35095 07[CHD] <con1|141> CHILD_SA con1{1813} state change: CREATED => INSTALLING
May 5 17:35:00 charon 35095 07[CHD] <con1|141> using AES_CBC for encryption
May 5 17:35:00 charon 35095 07[CHD] <con1|141> using HMAC_SHA2_256_128 for integrity
May 5 17:35:00 charon 35095 07[CHD] <con1|141> adding inbound ESP SA
May 5 17:35:00 charon 35095 07[CHD] <con1|141> SPI 0xcec966f2, src zyxelip dst pfsenseip
May 5 17:35:00 charon 35095 07[CHD] <con1|141> registering outbound ESP SA
May 5 17:35:00 charon 35095 07[CHD] <con1|141> SPI 0x84c71b00, src pfsenseip dst zyxelip
May 5 17:35:00 charon 35095 07[IKE] <con1|141> inbound CHILD_SA con1{1813} established with SPIs cec966f2_i 84c71b00_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 5 17:35:00 charon 35095 07[CHD] <con1|141> CHILD_SA con1{1813} state change: INSTALLING => INSTALLED
May 5 17:35:00 charon 35095 07[CHD] <con1|141> adding outbound ESP SA
May 5 17:35:00 charon 35095 07[CHD] <con1|141> SPI 0x84c71b00, src pfsenseip dst zyxelip
May 5 17:35:00 charon 35095 07[IKE] <con1|141> outbound CHILD_SA con1{1813} established with SPIs cec966f2_i 84c71b00_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 5 17:35:00 charon 35095 07[CHD] <con1|141> CHILD_SA con1{1806} state change: REKEYING => REKEYED
May 5 17:35:00 charon 35095 07[IKE] <con1|141> reinitiating already active tasks
May 5 17:35:00 charon 35095 07[IKE] <con1|141> CHILD_REKEY task
May 5 17:35:00 charon 35095 07[IKE] <con1|141> closing CHILD_SA con1{1806} with SPIs c92d2cad_i (172200 bytes) 3a901054_o (41240 bytes) and TS 192.168.3.0/24|/0 === 192.168.10.0/24|/0
May 5 17:35:00 charon 35095 07[IKE] <con1|141> sending DELETE for ESP CHILD_SA with SPI c92d2cad
May 5 17:35:00 charon 35095 07[CHD] <con1|141> CHILD_SA con1{1806} state change: REKEYED => DELETING
May 5 17:35:00 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL request 496 [ D ]
May 5 17:35:00 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:35:00 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:35:00 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL response 496 [ ]
May 5 17:35:00 charon 35095 07[IKE] <con1|141> CHILD_SA closed
May 5 17:35:00 charon 35095 07[CHD] <con1|141> CHILD_SA con1{1806} state change: DELETING => DELETED
May 5 17:35:00 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:35:00 charon 35095 07[IKE] <con1|141> nothing to initiate
May 5 17:35:03 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:35:03 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL request 968 [ ]
May 5 17:35:03 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL response 968 [ ]
May 5 17:35:03 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:35:05 charon 35095 07[IKE] <con1|141> queueing CHILD_DELETE task
May 5 17:35:05 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:35:05 charon 35095 07[IKE] <con1|141> activating CHILD_DELETE task
May 5 17:35:05 charon 35095 07[CHD] <con1|141> CHILD_SA con1{1806} state change: DELETED => DESTROYING
May 5 17:35:05 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:35:05 charon 35095 07[IKE] <con1|141> nothing to initiate
May 5 17:35:17 charon 35095 12[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:35:17 charon 35095 12[ENC] <con1|141> parsed CREATE_CHILD_SA request 969 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 5 17:35:17 charon 35095 12[IKE] <con1|141> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 5 17:35:17 charon 35095 12[CFG] <con1|141> looking for a child config for 192.168.3.0/24|/0 === 192.168.10.0/24|/0
May 5 17:35:17 charon 35095 12[CFG] <con1|141> proposing traffic selectors for us:
May 5 17:35:17 charon 35095 12[CFG] <con1|141> 192.168.0.0/24|/0
May 5 17:35:17 charon 35095 12[CFG] <con1|141> 192.168.3.0/24|/0
May 5 17:35:17 charon 35095 12[CFG] <con1|141> proposing traffic selectors for other:
May 5 17:35:17 charon 35095 12[CFG] <con1|141> 192.168.10.0/24|/0
May 5 17:35:17 charon 35095 12[CFG] <con1|141> 192.168.10.0/24|/0
May 5 17:35:17 charon 35095 12[CFG] <con1|141> candidate "con1" with prio 5+5
May 5 17:35:17 charon 35095 12[CFG] <con1|141> found matching child config "con1" with prio 10
May 5 17:35:17 charon 35095 12[CFG] <con1|141> selecting proposal:
May 5 17:35:17 charon 35095 12[CFG] <con1|141> proposal matches
May 5 17:35:17 charon 35095 12[CFG] <con1|141> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:35:17 charon 35095 12[CFG] <con1|141> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:35:17 charon 35095 12[CFG] <con1|141> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:35:17 charon 35095 12[CFG] <con1|141> selecting traffic selectors for us:
May 5 17:35:17 charon 35095 12[CFG] <con1|141> config: 192.168.0.0/24|/0, received: 192.168.3.0/24|/0 => no match
May 5 17:35:17 charon 35095 12[CFG] <con1|141> config: 192.168.3.0/24|/0, received: 192.168.3.0/24|/0 => match: 192.168.3.0/24|/0
May 5 17:35:17 charon 35095 12[CFG] <con1|141> selecting traffic selectors for other:
May 5 17:35:17 charon 35095 12[CFG] <con1|141> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 5 17:35:17 charon 35095 12[CFG] <con1|141> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 5 17:35:17 charon 35095 12[CHD] <con1|141> CHILD_SA con1{1814} state change: CREATED => INSTALLING
May 5 17:35:17 charon 35095 12[CHD] <con1|141> using AES_CBC for encryption
May 5 17:35:17 charon 35095 12[CHD] <con1|141> using HMAC_SHA2_256_128 for integrity
May 5 17:35:17 charon 35095 12[CHD] <con1|141> adding inbound ESP SA
May 5 17:35:17 charon 35095 12[CHD] <con1|141> SPI 0xc0a46492, src zyxelip dst pfsenseip
May 5 17:35:17 charon 35095 12[CHD] <con1|141> adding outbound ESP SA
May 5 17:35:17 charon 35095 12[CHD] <con1|141> SPI 0x6bea62d9, src pfsenseip dst zyxelip
May 5 17:35:17 charon 35095 12[IKE] <con1|141> CHILD_SA con1{1814} established with SPIs c0a46492_i 6bea62d9_o and TS 192.168.3.0/24|/0 === 192.168.10.0/24|/0
May 5 17:35:17 charon 35095 12[CHD] <con1|141> CHILD_SA con1{1814} state change: INSTALLING => INSTALLED
May 5 17:35:17 charon 35095 12[ENC] <con1|141> generating CREATE_CHILD_SA response 969 [ N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 5 17:35:17 charon 35095 12[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (480 bytes)
May 5 17:35:32 charon 35095 07[IKE] <con1|141> sending DPD request
May 5 17:35:32 charon 35095 07[IKE] <con1|141> queueing IKE_DPD task
May 5 17:35:32 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:35:32 charon 35095 07[IKE] <con1|141> activating IKE_DPD task
May 5 17:35:32 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL request 497 [ ]
May 5 17:35:32 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:35:32 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:35:32 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL response 497 [ ]
May 5 17:35:32 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:35:32 charon 35095 07[IKE] <con1|141> nothing to initiate
May 5 17:35:33 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:35:33 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL request 970 [ ]
May 5 17:35:33 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL response 970 [ ]
May 5 17:35:33 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:35:44 charon 35095 07[IKE] <con1|141> sending DPD request
May 5 17:35:44 charon 35095 07[IKE] <con1|141> queueing IKE_DPD task
May 5 17:35:44 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:35:44 charon 35095 07[IKE] <con1|141> activating IKE_DPD task
May 5 17:35:44 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL request 498 [ ]
May 5 17:35:44 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:35:44 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:35:44 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL response 498 [ ]
May 5 17:35:54 charon 35095 07[IKE] <con1|141> activating IKE_DPD task
May 5 17:35:54 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL request 499 [ ]
May 5 17:35:54 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:35:54 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:35:54 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL response 499 [ ]
May 5 17:35:54 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:35:54 charon 35095 07[IKE] <con1|141> nothing to initiate
May 5 17:36:03 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:36:03 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL request 971 [ ]
May 5 17:36:03 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL response 971 [ ]
May 5 17:36:03 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:36:16 charon 35095 05[IKE] <con1|141> sending DPD request
May 5 17:36:16 charon 35095 05[IKE] <con1|141> queueing IKE_DPD task
May 5 17:36:16 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:36:16 charon 35095 05[IKE] <con1|141> activating IKE_DPD task
May 5 17:36:16 charon 35095 05[ENC] <con1|141> generating INFORMATIONAL request 500 [ ]
May 5 17:36:16 charon 35095 05[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:36:16 charon 35095 05[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:36:16 charon 35095 05[ENC] <con1|141> parsed INFORMATIONAL response 500 [ ]
May 5 17:36:16 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:36:16 charon 35095 05[IKE] <con1|141> nothing to initiate
May 5 17:36:30 charon 35095 05[IKE] <con1|141> sending DPD request
May 5 17:36:30 charon 35095 05[IKE] <con1|141> queueing IKE_DPD task
May 5 17:36:30 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:36:30 charon 35095 05[IKE] <con1|141> activating IKE_DPD task
May 5 17:36:30 charon 35095 05[ENC] <con1|141> generating INFORMATIONAL request 501 [ ]
May 5 17:36:30 charon 35095 05[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:36:30 charon 35095 05[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:36:30 charon 35095 05[ENC] <con1|141> parsed INFORMATIONAL response 501 [ ]
May 5 17:36:30 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:36:30 charon 35095 05[IKE] <con1|141> nothing to initiate
May 5 17:36:34 charon 35095 05[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:36:34 charon 35095 05[ENC] <con1|141> parsed INFORMATIONAL request 972 [ ]
May 5 17:36:34 charon 35095 05[ENC] <con1|141> generating INFORMATIONAL response 972 [ ]
May 5 17:36:34 charon 35095 05[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:36:44 charon 35095 05[IKE] <con1|141> sending DPD request
May 5 17:36:44 charon 35095 05[IKE] <con1|141> queueing IKE_DPD task
May 5 17:36:44 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:36:44 charon 35095 05[IKE] <con1|141> activating IKE_DPD task
May 5 17:36:44 charon 35095 05[ENC] <con1|141> generating INFORMATIONAL request 502 [ ]
May 5 17:36:44 charon 35095 05[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:36:44 charon 35095 05[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:36:44 charon 35095 05[ENC] <con1|141> parsed INFORMATIONAL response 502 [ ]
May 5 17:36:44 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:36:44 charon 35095 05[IKE] <con1|141> nothing to initiate
May 5 17:36:54 charon 35095 05[IKE] <con1|141> sending DPD request
May 5 17:36:54 charon 35095 05[IKE] <con1|141> queueing IKE_DPD task
May 5 17:36:54 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:36:54 charon 35095 05[IKE] <con1|141> activating IKE_DPD task
May 5 17:36:54 charon 35095 05[ENC] <con1|141> generating INFORMATIONAL request 503 [ ]
May 5 17:36:54 charon 35095 05[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:36:54 charon 35095 05[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:36:54 charon 35095 05[ENC] <con1|141> parsed INFORMATIONAL response 503 [ ]
May 5 17:36:54 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:36:54 charon 35095 05[IKE] <con1|141> nothing to initiate
May 5 17:37:03 charon 35095 06[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:37:03 charon 35095 06[ENC] <con1|141> parsed INFORMATIONAL request 973 [ ]
May 5 17:37:03 charon 35095 06[ENC] <con1|141> generating INFORMATIONAL response 973 [ ]
May 5 17:37:03 charon 35095 06[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:37:13 charon 35095 06[IKE] <con1|141> sending DPD request
May 5 17:37:13 charon 35095 06[IKE] <con1|141> queueing IKE_DPD task
May 5 17:37:13 charon 35095 06[IKE] <con1|141> activating new tasks
May 5 17:37:13 charon 35095 06[IKE] <con1|141> activating IKE_DPD task
May 5 17:37:13 charon 35095 06[ENC] <con1|141> generating INFORMATIONAL request 504 [ ]
May 5 17:37:13 charon 35095 06[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:37:13 charon 35095 06[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:37:13 charon 35095 06[ENC] <con1|141> parsed INFORMATIONAL response 504 [ ]
May 5 17:37:13 charon 35095 06[IKE] <con1|141> activating new tasks
May 5 17:37:13 charon 35095 06[IKE] <con1|141> nothing to initiate
May 5 17:37:34 charon 35095 06[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:37:34 charon 35095 06[ENC] <con1|141> parsed INFORMATIONAL request 974 [ ]
May 5 17:37:34 charon 35095 06[ENC] <con1|141> generating INFORMATIONAL response 974 [ ]
May 5 17:37:34 charon 35095 06[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:38:03 charon 35095 06[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:38:03 charon 35095 06[ENC] <con1|141> parsed INFORMATIONAL request 975 [ ]
May 5 17:38:03 charon 35095 06[ENC] <con1|141> generating INFORMATIONAL response 975 [ ]
May 5 17:38:03 charon 35095 06[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:38:34 charon 35095 13[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:38:34 charon 35095 13[ENC] <con1|141> parsed INFORMATIONAL request 976 [ ]
May 5 17:38:34 charon 35095 13[ENC] <con1|141> generating INFORMATIONAL response 976 [ ]
May 5 17:38:34 charon 35095 13[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:38:42 charon 35095 15[CFG] vici client 9606 connected
May 5 17:38:42 charon 35095 13[CFG] vici client 9606 registered for: list-sa
May 5 17:38:42 charon 35095 13[CFG] vici client 9606 requests: list-sas
May 5 17:38:42 charon 35095 14[CFG] vici client 9606 disconnected
May 5 17:39:04 charon 35095 10[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:39:04 charon 35095 10[ENC] <con1|141> parsed INFORMATIONAL request 977 [ ]
May 5 17:39:04 charon 35095 10[ENC] <con1|141> generating INFORMATIONAL response 977 [ ]
May 5 17:39:04 charon 35095 10[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:39:34 charon 35095 10[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:39:34 charon 35095 10[ENC] <con1|141> parsed INFORMATIONAL request 978 [ ]
May 5 17:39:34 charon 35095 10[ENC] <con1|141> generating INFORMATIONAL response 978 [ ]
May 5 17:39:34 charon 35095 10[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:40:03 charon 35095 10[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:40:03 charon 35095 10[ENC] <con1|141> parsed INFORMATIONAL request 979 [ ]
May 5 17:40:03 charon 35095 10[ENC] <con1|141> generating INFORMATIONAL response 979 [ ]
May 5 17:40:03 charon 35095 10[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:40:33 charon 35095 11[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:40:33 charon 35095 11[ENC] <con1|141> parsed INFORMATIONAL request 980 [ ]
May 5 17:40:33 charon 35095 11[ENC] <con1|141> generating INFORMATIONAL response 980 [ ]
May 5 17:40:33 charon 35095 11[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:41:03 charon 35095 11[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:41:03 charon 35095 11[ENC] <con1|141> parsed INFORMATIONAL request 981 [ ]
May 5 17:41:03 charon 35095 11[ENC] <con1|141> generating INFORMATIONAL response 981 [ ]
May 5 17:41:03 charon 35095 11[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:41:33 charon 35095 11[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:41:33 charon 35095 11[ENC] <con1|141> parsed INFORMATIONAL request 982 [ ]
May 5 17:41:33 charon 35095 11[ENC] <con1|141> generating INFORMATIONAL response 982 [ ]
May 5 17:41:33 charon 35095 11[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:42:03 charon 35095 11[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:42:03 charon 35095 11[ENC] <con1|141> parsed INFORMATIONAL request 983 [ ]
May 5 17:42:03 charon 35095 11[ENC] <con1|141> generating INFORMATIONAL response 983 [ ]
May 5 17:42:03 charon 35095 11[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:42:33 charon 35095 09[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:42:33 charon 35095 09[ENC] <con1|141> parsed INFORMATIONAL request 984 [ ]
May 5 17:42:33 charon 35095 09[ENC] <con1|141> generating INFORMATIONAL response 984 [ ]
May 5 17:42:33 charon 35095 09[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:43:04 charon 35095 09[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:43:04 charon 35095 09[ENC] <con1|141> parsed INFORMATIONAL request 985 [ ]
May 5 17:43:04 charon 35095 09[ENC] <con1|141> generating INFORMATIONAL response 985 [ ]
May 5 17:43:04 charon 35095 09[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:43:33 charon 35095 09[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:43:33 charon 35095 09[ENC] <con1|141> parsed INFORMATIONAL request 986 [ ]
May 5 17:43:33 charon 35095 09[ENC] <con1|141> generating INFORMATIONAL response 986 [ ]
May 5 17:43:33 charon 35095 09[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:43:43 charon 35095 16[CFG] vici client 9607 connected
May 5 17:43:43 charon 35095 08[CFG] vici client 9607 registered for: list-sa
May 5 17:43:43 charon 35095 09[CFG] vici client 9607 requests: list-sas
May 5 17:43:43 charon 35095 09[CFG] vici client 9607 disconnected
May 5 17:44:03 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:44:03 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL request 987 [ ]
May 5 17:44:03 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL response 987 [ ]
May 5 17:44:03 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:44:34 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:44:34 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL request 988 [ ]
May 5 17:44:34 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL response 988 [ ]
May 5 17:44:34 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:44:47 charon 35095 07[KNL] creating rekey job for CHILD_SA ESP/0xca744e29/pfsenseip
May 5 17:44:47 charon 35095 05[IKE] <con1|141> queueing CHILD_REKEY task
May 5 17:44:47 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:44:47 charon 35095 05[IKE] <con1|141> activating CHILD_REKEY task
May 5 17:44:47 charon 35095 05[CFG] <con1|141> proposing traffic selectors for us:
May 5 17:44:47 charon 35095 05[CFG] <con1|141> 192.168.0.0/24|/0
May 5 17:44:47 charon 35095 05[CFG] <con1|141> 192.168.3.0/24|/0
May 5 17:44:47 charon 35095 05[CFG] <con1|141> proposing traffic selectors for other:
May 5 17:44:47 charon 35095 05[CFG] <con1|141> 192.168.10.0/24|/0
May 5 17:44:47 charon 35095 05[CFG] <con1|141> 192.168.10.0/24|/0
May 5 17:44:47 charon 35095 05[CFG] <con1|141> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:44:47 charon 35095 05[IKE] <con1|141> establishing CHILD_SA con1{1815} reqid 2
May 5 17:44:47 charon 35095 05[CHD] <con1|141> CHILD_SA con1{1807} state change: INSTALLED => REKEYING
May 5 17:44:47 charon 35095 05[ENC] <con1|141> generating CREATE_CHILD_SA request 505 [ N(REKEY_SA) N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 5 17:44:47 charon 35095 05[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (512 bytes)
May 5 17:44:48 charon 35095 05[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (496 bytes)
May 5 17:44:48 charon 35095 05[ENC] <con1|141> parsed CREATE_CHILD_SA response 505 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 5 17:44:48 charon 35095 05[IKE] <con1|141> received ESP_TFC_PADDING_NOT_SUPPORTED notify
May 5 17:44:48 charon 35095 05[IKE] <con1|141> received NON_FIRST_FRAGMENTS_ALSO notify
May 5 17:44:49 charon 35095 05[IKE] <con1|141> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 5 17:44:49 charon 35095 05[CFG] <con1|141> selecting proposal:
May 5 17:44:49 charon 35095 05[CFG] <con1|141> proposal matches
May 5 17:44:49 charon 35095 05[CFG] <con1|141> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:44:49 charon 35095 05[CFG] <con1|141> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:44:49 charon 35095 05[CFG] <con1|141> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:44:49 charon 35095 05[CFG] <con1|141> selecting traffic selectors for us:
May 5 17:44:49 charon 35095 05[CFG] <con1|141> config: 192.168.0.0/24|/0, received: 192.168.0.0/24|/0 => match: 192.168.0.0/24|/0
May 5 17:44:49 charon 35095 05[CFG] <con1|141> config: 192.168.3.0/24|/0, received: 192.168.0.0/24|/0 => no match
May 5 17:44:49 charon 35095 05[CFG] <con1|141> selecting traffic selectors for other:
May 5 17:44:49 charon 35095 05[CFG] <con1|141> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 5 17:44:49 charon 35095 05[CFG] <con1|141> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 5 17:44:49 charon 35095 05[CHD] <con1|141> CHILD_SA con1{1815} state change: CREATED => INSTALLING
May 5 17:44:49 charon 35095 05[CHD] <con1|141> using AES_CBC for encryption
May 5 17:44:49 charon 35095 05[CHD] <con1|141> using HMAC_SHA2_256_128 for integrity
May 5 17:44:49 charon 35095 05[CHD] <con1|141> adding inbound ESP SA
May 5 17:44:49 charon 35095 05[CHD] <con1|141> SPI 0xcd73cbea, src zyxelip dst pfsenseip
May 5 17:44:49 charon 35095 05[CHD] <con1|141> registering outbound ESP SA
May 5 17:44:49 charon 35095 05[CHD] <con1|141> SPI 0x2929b77e, src pfsenseip dst zyxelip
May 5 17:44:49 charon 35095 05[IKE] <con1|141> inbound CHILD_SA con1{1815} established with SPIs cd73cbea_i 2929b77e_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 5 17:44:49 charon 35095 05[CHD] <con1|141> CHILD_SA con1{1815} state change: INSTALLING => INSTALLED
May 5 17:44:49 charon 35095 05[CHD] <con1|141> adding outbound ESP SA
May 5 17:44:49 charon 35095 05[CHD] <con1|141> SPI 0x2929b77e, src pfsenseip dst zyxelip
May 5 17:44:49 charon 35095 05[IKE] <con1|141> outbound CHILD_SA con1{1815} established with SPIs cd73cbea_i 2929b77e_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 5 17:44:49 charon 35095 05[CHD] <con1|141> CHILD_SA con1{1807} state change: REKEYING => REKEYED
May 5 17:44:49 charon 35095 05[IKE] <con1|141> reinitiating already active tasks
May 5 17:44:49 charon 35095 05[IKE] <con1|141> CHILD_REKEY task
May 5 17:44:49 charon 35095 05[IKE] <con1|141> closing CHILD_SA con1{1807} with SPIs ca744e29_i (3360 bytes) b03d242e_o (29984 bytes) and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 5 17:44:49 charon 35095 05[IKE] <con1|141> sending DELETE for ESP CHILD_SA with SPI ca744e29
May 5 17:44:49 charon 35095 05[CHD] <con1|141> CHILD_SA con1{1807} state change: REKEYED => DELETING
May 5 17:44:49 charon 35095 05[ENC] <con1|141> generating INFORMATIONAL request 506 [ D ]
May 5 17:44:49 charon 35095 05[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:44:49 charon 35095 05[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:44:49 charon 35095 05[ENC] <con1|141> parsed INFORMATIONAL response 506 [ ]
May 5 17:44:49 charon 35095 05[IKE] <con1|141> CHILD_SA closed
May 5 17:44:49 charon 35095 05[CHD] <con1|141> CHILD_SA con1{1807} state change: DELETING => DELETED
May 5 17:44:49 charon 35095 05[IKE] <con1|141> activating new tasks
May 5 17:44:49 charon 35095 05[IKE] <con1|141> nothing to initiate
May 5 17:44:54 charon 35095 07[IKE] <con1|141> queueing CHILD_DELETE task
May 5 17:44:54 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:44:54 charon 35095 07[IKE] <con1|141> activating CHILD_DELETE task
May 5 17:44:54 charon 35095 07[CHD] <con1|141> CHILD_SA con1{1807} state change: DELETED => DESTROYING
May 5 17:44:54 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:44:54 charon 35095 07[IKE] <con1|141> nothing to initiate
May 5 17:45:04 charon 35095 06[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:45:04 charon 35095 06[ENC] <con1|141> parsed INFORMATIONAL request 989 [ ]
May 5 17:45:04 charon 35095 06[ENC] <con1|141> generating INFORMATIONAL response 989 [ ]
May 5 17:45:04 charon 35095 06[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:45:18 charon 35095 06[IKE] <con1|141> sending DPD request
May 5 17:45:18 charon 35095 06[IKE] <con1|141> queueing IKE_DPD task
May 5 17:45:18 charon 35095 06[IKE] <con1|141> activating new tasks
May 5 17:45:18 charon 35095 06[IKE] <con1|141> activating IKE_DPD task
May 5 17:45:18 charon 35095 06[ENC] <con1|141> generating INFORMATIONAL request 507 [ ]
May 5 17:45:18 charon 35095 06[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:45:18 charon 35095 06[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:45:18 charon 35095 06[ENC] <con1|141> parsed INFORMATIONAL response 507 [ ]
May 5 17:45:18 charon 35095 06[IKE] <con1|141> activating new tasks
May 5 17:45:18 charon 35095 06[IKE] <con1|141> nothing to initiate
May 5 17:45:33 charon 35095 06[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:45:33 charon 35095 06[ENC] <con1|141> parsed INFORMATIONAL request 990 [ ]
May 5 17:45:33 charon 35095 06[ENC] <con1|141> generating INFORMATIONAL response 990 [ ]
May 5 17:45:33 charon 35095 06[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:45:43 charon 35095 06[IKE] <con1|141> sending DPD request
May 5 17:45:43 charon 35095 06[IKE] <con1|141> queueing IKE_DPD task
May 5 17:45:43 charon 35095 06[IKE] <con1|141> activating new tasks
May 5 17:45:43 charon 35095 06[IKE] <con1|141> activating IKE_DPD task
May 5 17:45:43 charon 35095 06[ENC] <con1|141> generating INFORMATIONAL request 508 [ ]
May 5 17:45:43 charon 35095 06[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:45:43 charon 35095 06[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:45:43 charon 35095 06[ENC] <con1|141> parsed INFORMATIONAL response 508 [ ]
May 5 17:45:43 charon 35095 06[IKE] <con1|141> activating new tasks
May 5 17:45:43 charon 35095 06[IKE] <con1|141> nothing to initiate
May 5 17:46:03 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:46:03 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL request 991 [ ]
May 5 17:46:03 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL response 991 [ ]
May 5 17:46:03 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:46:33 charon 35095 07[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:46:33 charon 35095 07[ENC] <con1|141> parsed INFORMATIONAL request 992 [ ]
May 5 17:46:33 charon 35095 07[ENC] <con1|141> generating INFORMATIONAL response 992 [ ]
May 5 17:46:33 charon 35095 07[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 5 17:46:41 charon 35095 07[KNL] creating rekey job for CHILD_SA ESP/0xc1418538/pfsenseip
May 5 17:46:41 charon 35095 13[IKE] <con1|141> queueing CHILD_REKEY task
May 5 17:46:41 charon 35095 13[IKE] <con1|141> activating new tasks
May 5 17:46:41 charon 35095 13[IKE] <con1|141> activating CHILD_REKEY task
May 5 17:46:41 charon 35095 13[CFG] <con1|141> proposing traffic selectors for us:
May 5 17:46:41 charon 35095 13[CFG] <con1|141> 192.168.0.0/24|/0
May 5 17:46:41 charon 35095 13[CFG] <con1|141> 192.168.3.0/24|/0
May 5 17:46:41 charon 35095 13[CFG] <con1|141> proposing traffic selectors for other:
May 5 17:46:41 charon 35095 13[CFG] <con1|141> 192.168.10.0/24|/0
May 5 17:46:41 charon 35095 13[CFG] <con1|141> 192.168.10.0/24|/0
May 5 17:46:41 charon 35095 13[CFG] <con1|141> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:46:41 charon 35095 13[IKE] <con1|141> establishing CHILD_SA con1{1816} reqid 2
May 5 17:46:41 charon 35095 13[CHD] <con1|141> CHILD_SA con1{1808} state change: INSTALLED => REKEYING
May 5 17:46:41 charon 35095 13[ENC] <con1|141> generating CREATE_CHILD_SA request 509 [ N(REKEY_SA) N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 5 17:46:41 charon 35095 13[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978] (512 bytes)
May 5 17:46:42 charon 35095 13[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (496 bytes)
May 5 17:46:42 charon 35095 13[ENC] <con1|141> parsed CREATE_CHILD_SA response 509 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 5 17:46:42 charon 35095 13[IKE] <con1|141> received ESP_TFC_PADDING_NOT_SUPPORTED notify
May 5 17:46:42 charon 35095 13[IKE] <con1|141> received NON_FIRST_FRAGMENTS_ALSO notify
May 5 17:46:42 charon 35095 13[IKE] <con1|141> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 5 17:46:42 charon 35095 13[CFG] <con1|141> selecting proposal:
May 5 17:46:42 charon 35095 13[CFG] <con1|141> proposal matches
May 5 17:46:42 charon 35095 13[CFG] <con1|141> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:46:42 charon 35095 13[CFG] <con1|141> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:46:42 charon 35095 13[CFG] <con1|141> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 5 17:46:42 charon 35095 13[CFG] <con1|141> selecting traffic selectors for us:
May 5 17:46:42 charon 35095 13[CFG] <con1|141> config: 192.168.0.0/24|/0, received: 192.168.0.0/24|/0 => match: 192.168.0.0/24|/0
May 5 17:46:42 charon 35095 13[CFG] <con1|141> config: 192.168.3.0/24|/0, received: 192.168.0.0/24|/0 => no match
May 5 17:46:42 charon 35095 13[CFG] <con1|141> selecting traffic selectors for other:
May 5 17:46:42 charon 35095 13[CFG] <con1|141> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 5 17:46:42 charon 35095 13[CFG] <con1|141> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 5 17:46:42 charon 35095 13[CHD] <con1|141> CHILD_SA con1{1816} state change: CREATED => INSTALLING
May 5 17:46:42 charon 35095 13[CHD] <con1|141> using AES_CBC for encryption
May 5 17:46:42 charon 35095 13[CHD] <con1|141> using HMAC_SHA2_256_128 for integrity
May 5 17:46:42 charon 35095 13[CHD] <con1|141> adding inbound ESP SA
May 5 17:46:42 charon 35095 13[CHD] <con1|141> SPI 0xc6eb7624, src zyxelip dst pfsenseip
May 5 17:46:42 charon 35095 13[CHD] <con1|141> registering outbound ESP SA
May 5 17:46:42 charon 35095 13[CHD] <con1|141> SPI 0x40b18b38, src pfsenseip dst zyxelip
May 5 17:46:42 charon 35095 13[IKE] <con1|141> inbound CHILD_SA con1{1816} established with SPIs c6eb7624_i 40b18b38_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 5 17:46:42 charon 35095 13[CHD] <con1|141> CHILD_SA con1{1816} state change: INSTALLING => INSTALLED
May 5 17:46:42 charon 35095 13[CHD] <con1|141> adding outbound ESP SA
May 5 17:46:42 charon 35095 13[CHD] <con1|141> SPI 0x40b18b38, src pfsenseip dst zyxelip
May 5 17:46:42 charon 35095 13[IKE] <con1|141> outbound CHILD_SA con1{1816} established with SPIs c6eb7624_i 40b18b38_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 5 17:46:42 charon 35095 13[CHD] <con1|141> CHILD_SA con1{1808} state change: REKEYING => REKEYED
May 5 17:46:42 charon 35095 13[IKE] <con1|141> reinitiating already active tasks
May 5 17:46:42 charon 35095 13[IKE] <con1|141> CHILD_REKEY task
May 5 17:46:42 charon 35095 13[IKE] <con1|141> closing CHILD_SA con1{1808} with SPIs c1418538_i (0 bytes) 9a9b6936_o (27736 bytes) and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 5 17:46:42 charon 35095 13[IKE] <con1|141> sending DELETE for ESP CHILD_SA with SPI c1418538
May 5 17:46:42 charon 35095 13[CHD] <con1|141> CHILD_SA con1{1808} state change: REKEYED => DELETING
May 5 17:46:42 charon 35095 13[ENC] <con1|141> generating INFORMATIONAL request 510 [ D ]
May 5 17:46:42 charon 35095 13[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:46:42 charon 35095 13[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 5 17:46:42 charon 35095 13[ENC] <con1|141> parsed INFORMATIONAL response 510 [ ]
May 5 17:46:42 charon 35095 13[IKE] <con1|141> CHILD_SA closed
May 5 17:46:42 charon 35095 13[CHD] <con1|141> CHILD_SA con1{1808} state change: DELETING => DELETED
May 5 17:46:42 charon 35095 13[IKE] <con1|141> activating new tasks
May 5 17:46:42 charon 35095 13[IKE] <con1|141> nothing to initiate
May 5 17:46:47 charon 35095 07[IKE] <con1|141> queueing CHILD_DELETE task
May 5 17:46:47 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:46:47 charon 35095 07[IKE] <con1|141> activating CHILD_DELETE task
May 5 17:46:47 charon 35095 07[CHD] <con1|141> CHILD_SA con1{1808} state change: DELETED => DESTROYING
May 5 17:46:47 charon 35095 07[IKE] <con1|141> activating new tasks
May 5 17:46:47 charon 35095 07[IKE] <con1|141> nothing to initiate
May 5 17:47:03 charon 35095 14[NET] <con1|141> received packet: from zyxelip[18978] to pfsenseip[4500]
May 5 17:47:03 charon 35095 14[ENC] <con1|141> parsed INFORMATIONAL request 993 [ ]
May 5 17:47:03 charon 35095 14[ENC] <con1|141> generating INFORMATIONAL response 993 [ ]
May 5 17:47:03 charon 35095 14[NET] <con1|141> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 5 17:47:23 charon 35095 07[CFG] vici client 9608 connected
May 5 17:47:23 charon 35095 14[CFG] vici client 9608 registered for: list-sa
May 5 17:47:23 charon 35095 14[CFG] vici client 9608 requests: list-sas
May 5 17:47:23 charon 35095 14[CFG] vici client 9608 disconnected- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7031864024
[content:7002498628#7031864024]
Bedenke das eine VTI Tunnel Konfig Option immer beidseitig bestehen muss sprich der Zyxel muss das dann auch supporten ansonsten scheitert so ein VPN.
Du siehst selber...solange wir deine genaue Konfig nicht kennen drehen wir uns weiter im Kreis und raten fröhlich weiter.
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7032329590
[content:7002498628#7032329590]
An den anderen Einstellungen (Reiter Advanced auf der Pfsense) habe ich alles so gelassen wie es war.
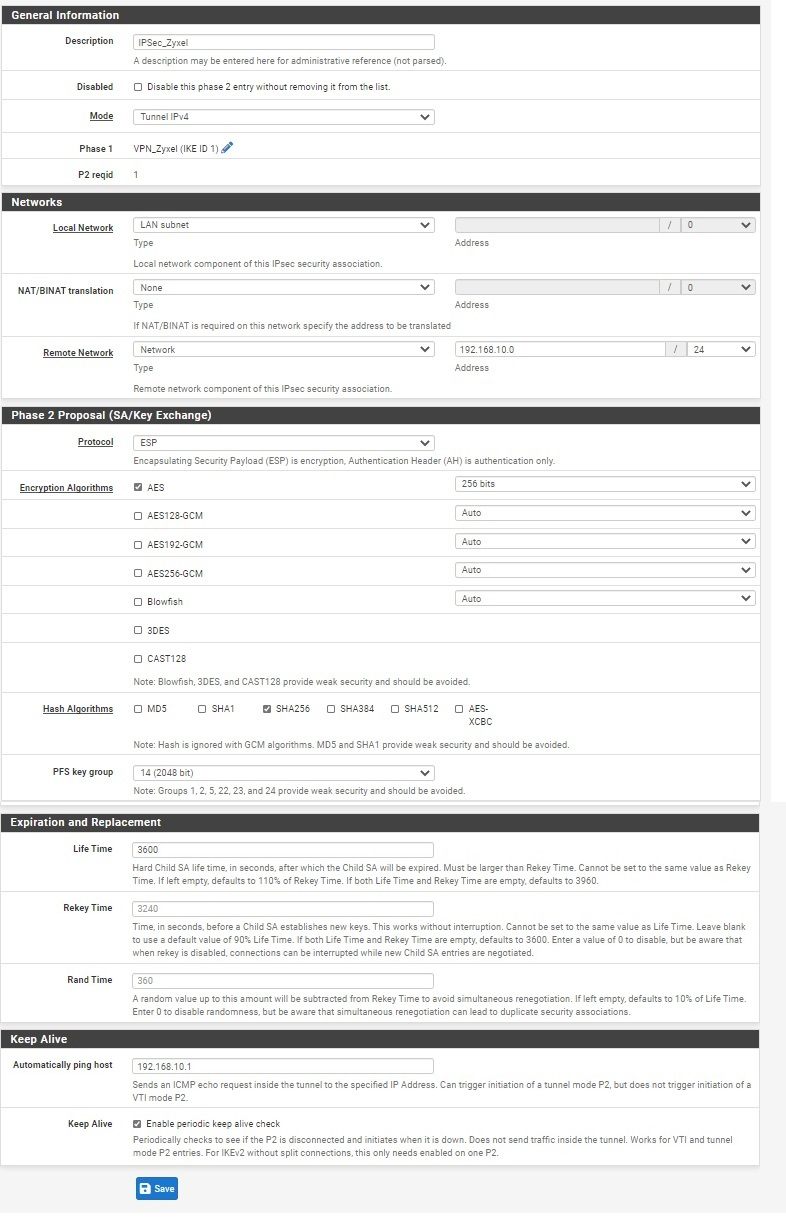
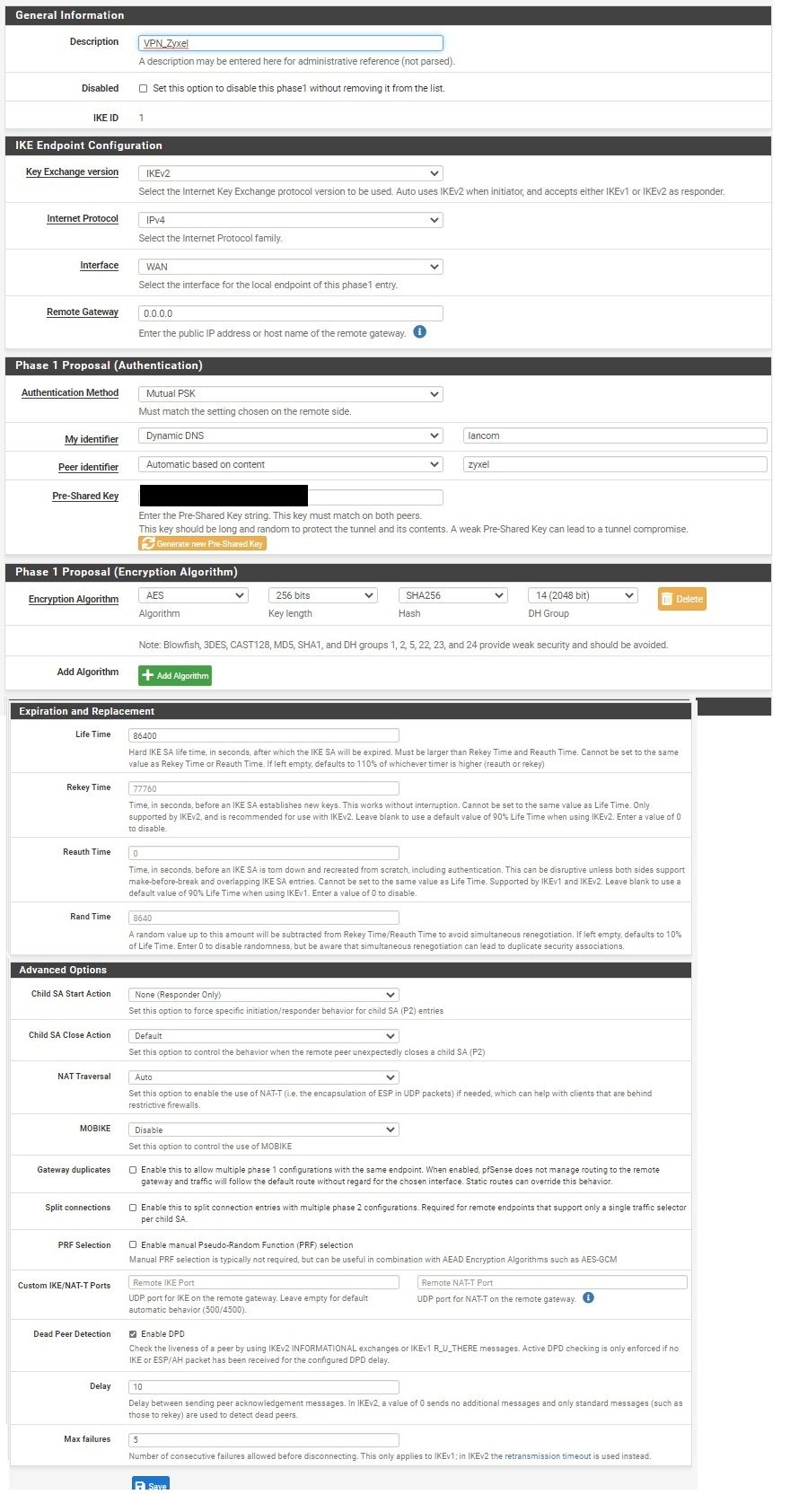
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7032334037
[content:7002498628#7032334037]
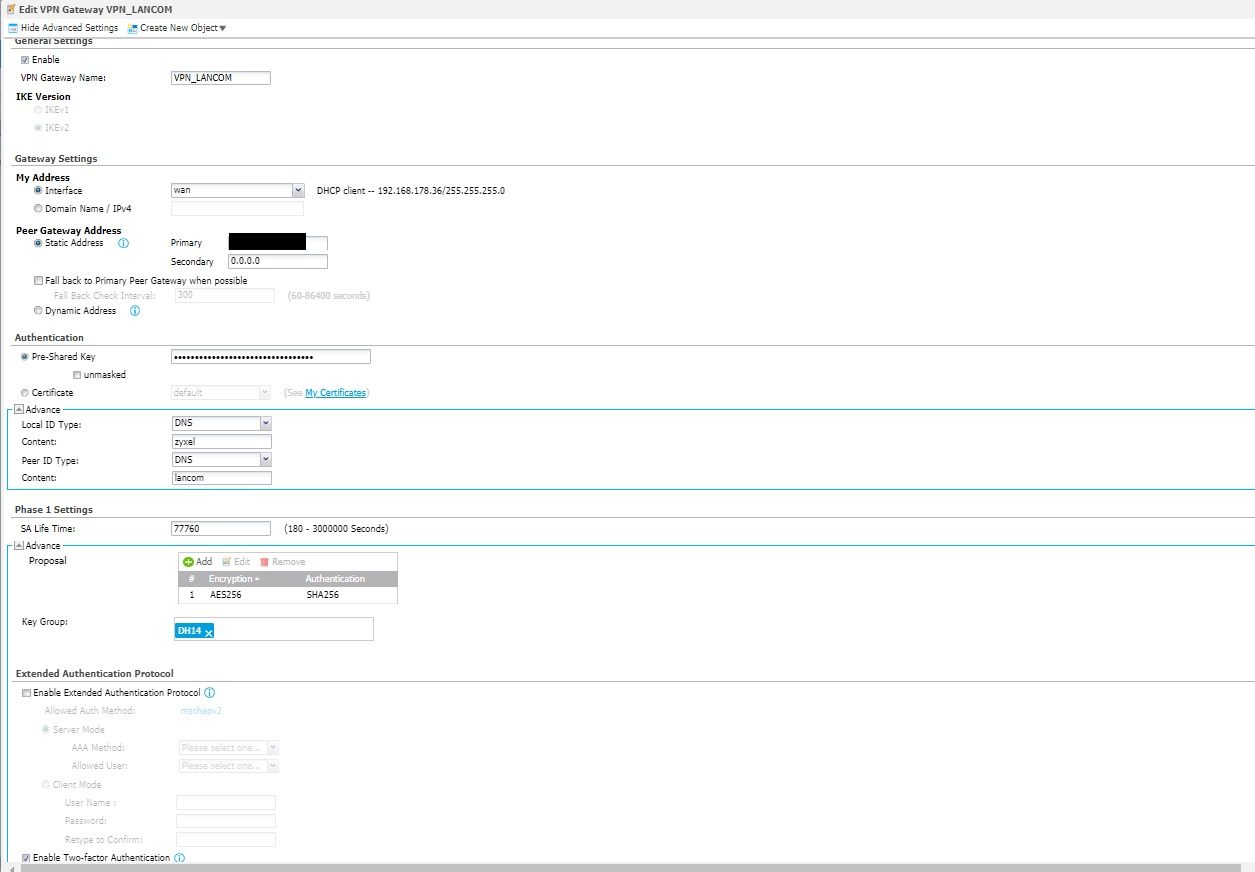
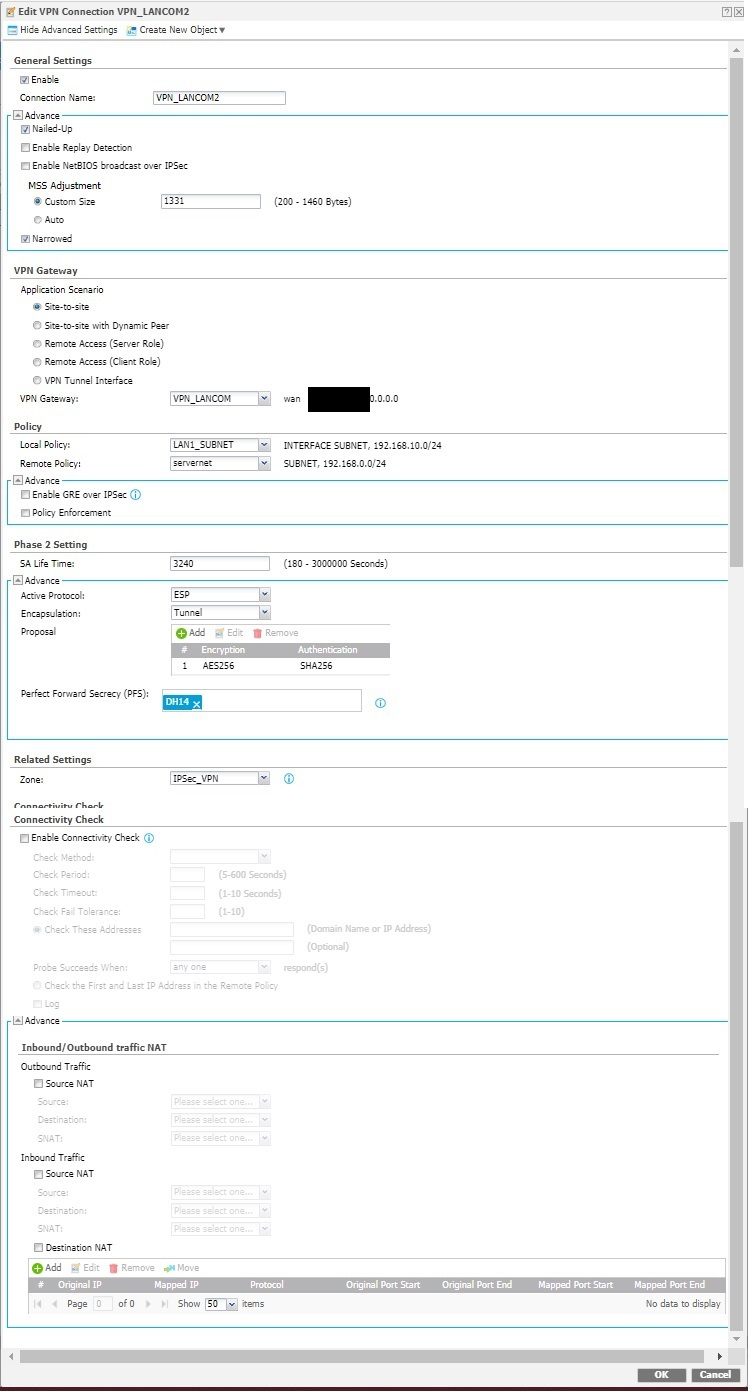
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7041879885
[content:7002498628#7041879885]
- Die Phase 1 SA Lifetime sollte auf beiden Seiten identisch sein! Die "86400" der pfSense ist ein gängiger Wert (24 Stunden) und der sollte am Zyxel identisch sein! Leider fehlt das komplette Phase 2 Setup der pfSense so das man hier nicht überprüfen kann ob du dort auch ggf. ein Lifetime oder Parameter Mismatch zur Zyxel Phase 2 hast.
- Gravierend ist aber das die Peer Identity unüberlicherweise auf "DNS" steht. Das ist in einem Setup mit dynamischen Initiator Adressen wie bei dir mit dem Zyxel (pfSense hat 0.0.0.0 als Peer) kontraproduktiv. Normalerweise nimmt man hier 2 statische Namen wie du das vermutlich auch vorhattest mit "lancom" und "zyxel". Dann darf die Identity aber niemals auf "DNS" stehen sondern immer auf "Distinguished name" oder mit "User distinguished name" wie du es z.B. HIER und auch an einem IKEv2 Beispiel HIER mit Mikrotik o. Cisco sehen kannst. Wurde oben schon einmal gepostet und hast du vermutlich nicht gelesen.
Das solltest du also dringenst anpassen, denn sehr wahrscheinlich wird das dein Problem lösen.
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7044338340
[content:7002498628#7044338340]
2 Dinge die auffallen und falsch sind
- Die Phase 1 SA Lifetime sollte auf beiden Seiten identisch sein! Die "86400" der pfSense ist ein gängiger Wert (24 Stunden) und der sollte am Zyxel identisch sein! Leider fehlt das komplette Phase 2 Setup der pfSense so das man hier nicht überprüfen kann ob du dort auch ggf. ein Lifetime oder Parameter Mismatch zur Zyxel Phase 2 hast.
Das mit der Phase 2 Lifetime mismatch habe ich extra gemacht, nachdem ich diese Dokumentation gelesen hatte
Netgate Dokumentation
Hatte damit aber auch leider keinen Erfolg
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7044694720
[content:7002498628#7044694720]
docs.strongswan.org/docs/5.9/config/rekeying.html
Ggf. lässt du mal die DH Gruppe in der Negotiation weg oder deaktivierst PFS. Das musst du mal testen sofern die Anpassung der Identity keine Änderung bringt.
Hast du das Verhalten ggf. einmal mit IKEv1 getestet ob es dort auch auftritt? Hatte der Lancom auch mit IKEv2 gearbeitet?
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7044853712
[content:7002498628#7044853712]
Hilfreich ist auch was zum Charon Daemon dazu steht:
docs.strongswan.org/docs/5.9/config/rekeying.html
Ggf. lässt du mal die DH Gruppe in der Negotiation weg oder deaktivierst PFS. Das musst du mal testen sofern die Anpassung der Identity keine Änderung bringt.
Hast du das Verhalten ggf. einmal mit IKEv1 getestet ob es dort auch auftritt? Hatte der Lancom auch mit IKEv2 gearbeitet?
Gerade eben einmal nachgeschaut, Zyxel bietet als Identifier nur IPv4, DNS und Email an.
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7046033470
[content:7002498628#7046033470]
Ich konnte jetzt mal mal einen Zeitpunkt abfangen, wo es zu einer Duplikation der child SA kam:
Das Rekey für das 192.168.3.0/24 Child-SA stand an, dabei kam es kurzzeitig zu einem Verbindungsabbruch für Phase 2 beider Subnetze, am Ende entstand eine Duplikation der Child SA für die 192.168.2.0/24 Verbindung, aber nach wie vor nur ein einziges für das 192.168.3.0/24 SA.
May 6 19:14:21 charon 35095 15[CFG] vici client 11083 requests: list-sas
May 6 19:14:21 charon 35095 15[CFG] vici client 11083 disconnected
May 6 19:14:26 charon 35095 07[CFG] vici client 11084 connected
May 6 19:14:36 charon 35095 12[CFG] vici client 11086 connected
May 6 19:14:36 charon 35095 08[CFG] vici client 11086 registered for: list-sa
May 6 19:14:36 charon 35095 08[CFG] vici client 11086 requests: list-sas
May 6 19:14:36 charon 35095 08[CFG] vici client 11086 disconnected
May 6 19:14:41 charon 35095 10[CFG] vici client 11087 connected
May 6 19:14:41 charon 35095 09[CFG] vici client 11087 registered for: list-sa
May 6 19:14:41 charon 35095 09[CFG] vici client 11087 requests: list-sas
May 6 19:14:41 charon 35095 09[CFG] vici client 11087 disconnected
May 6 19:14:46 charon 35095 06[CFG] vici client 11088 connected
May 6 19:14:46 charon 35095 16[CFG] vici client 11088 registered for: list-sa
May 6 19:14:46 charon 35095 16[CFG] vici client 11088 requests: list-sas
May 6 19:14:46 charon 35095 15[CFG] vici client 11088 disconnected
May 6 19:14:48 charon 35095 11[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:14:48 charon 35095 11[ENC] <con1|226> parsed INFORMATIONAL request 205 [ ]
May 6 19:14:48 charon 35095 11[ENC] <con1|226> generating INFORMATIONAL response 205 [ ]
May 6 19:14:48 charon 35095 11[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:15:08 charon 35095 07[CFG] vici client 11089 connected
May 6 19:15:08 charon 35095 13[CFG] vici client 11089 registered for: list-sa
May 6 19:15:08 charon 35095 13[CFG] vici client 11089 requests: list-sas
May 6 19:15:08 charon 35095 14[CFG] vici client 11089 disconnected
May 6 19:15:13 charon 35095 05[CFG] vici client 11090 connected
May 6 19:15:13 charon 35095 07[CFG] vici client 11090 registered for: list-sa
May 6 19:15:13 charon 35095 07[CFG] vici client 11090 requests: list-sas
May 6 19:15:13 charon 35095 12[CFG] vici client 11090 disconnected
May 6 19:15:18 charon 35095 05[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:15:18 charon 35095 05[ENC] <con1|226> parsed INFORMATIONAL request 206 [ ]
May 6 19:15:18 charon 35095 05[ENC] <con1|226> generating INFORMATIONAL response 206 [ ]
May 6 19:15:18 charon 35095 05[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:15:19 charon 35095 05[CFG] vici client 11091 connected
May 6 19:15:19 charon 35095 10[CFG] vici client 11091 registered for: list-sa
May 6 19:15:19 charon 35095 10[CFG] vici client 11091 requests: list-sas
May 6 19:15:19 charon 35095 10[CFG] vici client 11091 disconnected
May 6 19:15:24 charon 35095 09[CFG] vici client 11092 connected
May 6 19:15:24 charon 35095 05[CFG] vici client 11092 registered for: list-sa
May 6 19:15:29 charon 35095 06[CFG] vici client 11093 disconnected
May 6 19:15:34 charon 35095 11[CFG] vici client 11094 connected
May 6 19:15:34 charon 35095 16[CFG] vici client 11094 registered for: list-sa
May 6 19:15:34 charon 35095 13[CFG] vici client 11094 requests: list-sas
May 6 19:15:34 charon 35095 11[CFG] vici client 11094 disconnected
May 6 19:15:36 charon 35095 13[KNL] creating rekey job for CHILD_SA ESP/0xc338a5d9/pfsenseip
May 6 19:15:36 charon 35095 14[IKE] <con1|226> queueing CHILD_REKEY task
May 6 19:15:36 charon 35095 14[IKE] <con1|226> activating new tasks
May 6 19:15:36 charon 35095 14[IKE] <con1|226> activating CHILD_REKEY task
May 6 19:15:36 charon 35095 14[CFG] <con1|226> proposing traffic selectors for us:
May 6 19:15:36 charon 35095 14[CFG] <con1|226> 192.168.0.0/24|/0
May 6 19:15:36 charon 35095 14[CFG] <con1|226> 192.168.3.0/24|/0
May 6 19:15:36 charon 35095 14[CFG] <con1|226> proposing traffic selectors for other:
May 6 19:15:36 charon 35095 14[CFG] <con1|226> 192.168.10.0/24|/0
May 6 19:15:36 charon 35095 14[CFG] <con1|226> 192.168.10.0/24|/0
May 6 19:15:36 charon 35095 14[CFG] <con1|226> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:15:36 charon 35095 14[IKE] <con1|226> establishing CHILD_SA con1{2164} reqid 3
May 6 19:15:37 charon 35095 14[CHD] <con1|226> CHILD_SA con1{2161} state change: INSTALLED => REKEYING
May 6 19:15:37 charon 35095 14[ENC] <con1|226> generating CREATE_CHILD_SA request 7 [ N(REKEY_SA) N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 6 19:15:37 charon 35095 14[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (512 bytes)
May 6 19:15:38 charon 35095 14[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (496 bytes)
May 6 19:15:38 charon 35095 14[ENC] <con1|226> parsed CREATE_CHILD_SA response 7 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 6 19:15:38 charon 35095 14[IKE] <con1|226> received ESP_TFC_PADDING_NOT_SUPPORTED notify
May 6 19:15:38 charon 35095 14[IKE] <con1|226> received NON_FIRST_FRAGMENTS_ALSO notify
May 6 19:15:38 charon 35095 14[IKE] <con1|226> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 6 19:15:38 charon 35095 14[CFG] <con1|226> selecting proposal:
May 6 19:15:38 charon 35095 14[CFG] <con1|226> proposal matches
May 6 19:15:38 charon 35095 14[CFG] <con1|226> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:15:38 charon 35095 14[CFG] <con1|226> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:15:38 charon 35095 14[CFG] <con1|226> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:15:38 charon 35095 14[CFG] <con1|226> selecting traffic selectors for us:
May 6 19:15:38 charon 35095 14[CFG] <con1|226> config: 192.168.0.0/24|/0, received: 192.168.0.0/24|/0 => match: 192.168.0.0/24|/0
May 6 19:15:38 charon 35095 14[CFG] <con1|226> config: 192.168.3.0/24|/0, received: 192.168.0.0/24|/0 => no match
May 6 19:15:38 charon 35095 14[CFG] <con1|226> selecting traffic selectors for other:
May 6 19:15:38 charon 35095 14[CFG] <con1|226> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 6 19:15:38 charon 35095 14[CFG] <con1|226> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 6 19:15:38 charon 35095 14[CHD] <con1|226> CHILD_SA con1{2164} state change: CREATED => INSTALLING
May 6 19:15:38 charon 35095 14[CHD] <con1|226> using AES_CBC for encryption
May 6 19:15:38 charon 35095 14[CHD] <con1|226> using HMAC_SHA2_256_128 for integrity
May 6 19:15:38 charon 35095 14[CHD] <con1|226> adding inbound ESP SA
May 6 19:15:38 charon 35095 14[CHD] <con1|226> SPI 0xcde63d99, src zyxelip dst pfsenseip
May 6 19:15:38 charon 35095 14[CHD] <con1|226> registering outbound ESP SA
May 6 19:15:38 charon 35095 14[CHD] <con1|226> SPI 0x908230ee, src pfsenseip dst zyxelip
May 6 19:15:38 charon 35095 14[IKE] <con1|226> inbound CHILD_SA con1{2164} established with SPIs cde63d99_i 908230ee_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 6 19:15:38 charon 35095 14[CHD] <con1|226> CHILD_SA con1{2164} state change: INSTALLING => INSTALLED
May 6 19:15:38 charon 35095 14[CHD] <con1|226> adding outbound ESP SA
May 6 19:15:38 charon 35095 14[CHD] <con1|226> SPI 0x908230ee, src pfsenseip dst zyxelip
May 6 19:15:38 charon 35095 14[IKE] <con1|226> outbound CHILD_SA con1{2164} established with SPIs cde63d99_i 908230ee_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 6 19:15:38 charon 35095 14[CHD] <con1|226> CHILD_SA con1{2161} state change: REKEYING => REKEYED
May 6 19:15:38 charon 35095 14[IKE] <con1|226> reinitiating already active tasks
May 6 19:15:38 charon 35095 14[IKE] <con1|226> CHILD_REKEY task
May 6 19:15:38 charon 35095 14[IKE] <con1|226> closing CHILD_SA con1{2161} with SPIs c338a5d9_i (195370 bytes) 3ca8df18_o (30668 bytes) and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 6 19:15:38 charon 35095 14[IKE] <con1|226> sending DELETE for ESP CHILD_SA with SPI c338a5d9
May 6 19:15:38 charon 35095 14[CHD] <con1|226> CHILD_SA con1{2161} state change: REKEYED => DELETING
May 6 19:15:38 charon 35095 14[ENC] <con1|226> generating INFORMATIONAL request 8 [ D ]
May 6 19:15:38 charon 35095 14[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:15:38 charon 35095 07[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:15:38 charon 35095 07[ENC] <con1|226> parsed INFORMATIONAL response 8 [ ]
May 6 19:15:38 charon 35095 07[IKE] <con1|226> CHILD_SA closed
May 6 19:15:38 charon 35095 07[CHD] <con1|226> CHILD_SA con1{2161} state change: DELETING => DELETED
May 6 19:15:38 charon 35095 07[IKE] <con1|226> activating new tasks
May 6 19:15:38 charon 35095 07[IKE] <con1|226> nothing to initiate
May 6 19:15:39 charon 35095 14[CFG] vici client 11095 connected
May 6 19:15:39 charon 35095 07[CFG] vici client 11095 registered for: list-sa
May 6 19:15:39 charon 35095 07[CFG] vici client 11095 requests: list-sas
May 6 19:15:39 charon 35095 07[CFG] vici client 11095 disconnected
May 6 19:15:43 charon 35095 12[IKE] <con1|226> queueing CHILD_DELETE task
May 6 19:15:43 charon 35095 12[IKE] <con1|226> activating new tasks
May 6 19:15:43 charon 35095 12[IKE] <con1|226> activating CHILD_DELETE task
May 6 19:15:43 charon 35095 12[CHD] <con1|226> CHILD_SA con1{2161} state change: DELETED => DESTROYING
May 6 19:15:43 charon 35095 12[IKE] <con1|226> activating new tasks
May 6 19:15:43 charon 35095 12[IKE] <con1|226> nothing to initiate
May 6 19:15:49 charon 35095 08[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:15:49 charon 35095 08[ENC] <con1|226> parsed INFORMATIONAL request 207 [ ]
May 6 19:15:49 charon 35095 08[ENC] <con1|226> generating INFORMATIONAL response 207 [ ]
May 6 19:15:49 charon 35095 08[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:15:59 charon 35095 10[CFG] vici client 11096 connected
May 6 19:15:59 charon 35095 12[CFG] vici client 11096 registered for: list-sa
May 6 19:16:04 charon 35095 16[CFG] vici client 11098 registered for: list-sa
May 6 19:16:04 charon 35095 06[CFG] vici client 11098 requests: list-sas
May 6 19:16:04 charon 35095 06[CFG] vici client 11098 disconnected
May 6 19:16:09 charon 35095 11[CFG] vici client 11099 connected
May 6 19:16:09 charon 35095 13[CFG] vici client 11099 registered for: list-sa
May 6 19:16:09 charon 35095 11[CFG] vici client 11099 requests: list-sas
May 6 19:16:09 charon 35095 11[CFG] vici client 11099 disconnected
May 6 19:16:14 charon 35095 07[CFG] vici client 11100 connected
May 6 19:16:14 charon 35095 14[CFG] vici client 11100 registered for: list-sa
May 6 19:16:14 charon 35095 14[CFG] vici client 11100 requests: list-sas
May 6 19:16:14 charon 35095 14[CFG] vici client 11100 disconnected
May 6 19:16:19 charon 35095 08[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:16:19 charon 35095 08[ENC] <con1|226> parsed INFORMATIONAL request 208 [ ]
May 6 19:16:19 charon 35095 08[ENC] <con1|226> generating INFORMATIONAL response 208 [ ]
May 6 19:16:19 charon 35095 08[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:16:20 charon 35095 08[CFG] vici client 11101 connected
May 6 19:16:20 charon 35095 10[CFG] vici client 11101 registered for: list-sa
May 6 19:16:20 charon 35095 10[CFG] vici client 11101 requests: list-sas
May 6 19:16:20 charon 35095 10[CFG] vici client 11101 disconnected
May 6 19:16:25 charon 35095 09[CFG] vici client 11102 connected
May 6 19:16:25 charon 35095 08[CFG] vici client 11102 registered for: list-sa
May 6 19:16:25 charon 35095 08[CFG] vici client 11102 requests: list-sas
May 6 19:16:25 charon 35095 08[CFG] vici client 11102 disconnected
May 6 19:16:25 charon 35095 05[CFG] vici client 11103 connected
May 6 19:16:25 charon 35095 09[CFG] vici client 11103 registered for: list-sa
May 6 19:16:25 charon 35095 15[CFG] vici client 11103 requests: list-sas
May 6 19:16:25 charon 35095 09[CFG] vici client 11103 disconnected
May 6 19:16:30 charon 35095 11[CFG] vici client 11104 connected
May 6 19:16:30 charon 35095 16[CFG] vici client 11104 registered for: list-sa
May 6 19:16:30 charon 35095 16[CFG] vici client 11104 requests: list-sas
May 6 19:16:30 charon 35095 16[CFG] vici client 11104 disconnected
May 6 19:16:35 charon 35095 14[CFG] vici client 11105 connected
May 6 19:16:35 charon 35095 13[CFG] vici client 11105 registered for: list-sa
May 6 19:16:35 charon 35095 13[CFG] vici client 11105 requests: list-sas
May 6 19:16:35 charon 35095 13[CFG] vici client 11105 disconnected
May 6 19:16:37 charon 35095 10[CFG] vici client 11106 connected
May 6 19:16:37 charon 35095 07[CFG] vici client 11106 registered for: list-sa
May 6 19:16:37 charon 35095 12[CFG] vici client 11106 requests: list-sas
May 6 19:16:37 charon 35095 12[CFG] vici client 11106 disconnected
May 6 19:16:42 charon 35095 05[CFG] vici client 11107 connected
May 6 19:16:42 charon 35095 08[CFG] vici client 11107 registered for: list-sa
May 6 19:16:42 charon 35095 08[CFG] vici client 11107 requests: list-sas
May 6 19:16:42 charon 35095 08[CFG] vici client 11107 disconnected
May 6 19:16:48 charon 35095 15[CFG] vici client 11108 connected
May 6 19:16:48 charon 35095 09[CFG] vici client 11108 registered for: list-sa
May 6 19:16:48 charon 35095 09[CFG] vici client 11108 requests: list-sas
May 6 19:16:48 charon 35095 09[CFG] vici client 11108 disconnected
May 6 19:16:49 charon 35095 06[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:16:49 charon 35095 06[ENC] <con1|226> parsed INFORMATIONAL request 209 [ ]
May 6 19:16:49 charon 35095 06[ENC] <con1|226> generating INFORMATIONAL response 209 [ ]
May 6 19:16:49 charon 35095 06[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:16:53 charon 35095 11[CFG] vici client 11109 connected
May 6 19:16:53 charon 35095 06[CFG] vici client 11109 registered for: list-sa
May 6 19:16:53 charon 35095 06[CFG] vici client 11109 requests: list-sas
May 6 19:17:09 charon 35095 05[CFG] vici client 11113 connected
May 6 19:17:09 charon 35095 09[CFG] vici client 11113 registered for: list-sa
May 6 19:17:09 charon 35095 08[CFG] vici client 11113 requests: list-sas
May 6 19:17:09 charon 35095 08[CFG] vici client 11113 disconnected
May 6 19:17:14 charon 35095 09[CFG] vici client 11114 connected
May 6 19:17:14 charon 35095 06[CFG] vici client 11114 registered for: list-sa
May 6 19:17:14 charon 35095 06[CFG] vici client 11114 requests: list-sas
May 6 19:17:14 charon 35095 06[CFG] vici client 11114 disconnected
May 6 19:17:19 charon 35095 15[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:17:19 charon 35095 15[ENC] <con1|226> parsed INFORMATIONAL request 210 [ ]
May 6 19:17:19 charon 35095 15[ENC] <con1|226> generating INFORMATIONAL response 210 [ ]
May 6 19:17:19 charon 35095 15[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:17:19 charon 35095 16[CFG] vici client 11115 connected
May 6 19:17:24 charon 35095 14[CFG] vici client 11116 disconnected
May 6 19:17:29 charon 35095 10[CFG] vici client 11117 connected
May 6 19:17:29 charon 35095 13[CFG] vici client 11117 registered for: list-sa
May 6 19:17:29 charon 35095 13[CFG] vici client 11117 requests: list-sas
May 6 19:17:29 charon 35095 13[CFG] vici client 11117 disconnected
May 6 19:17:35 charon 35095 05[CFG] vici client 11118 connected
May 6 19:17:35 charon 35095 12[CFG] vici client 11118 registered for: list-sa
May 6 19:17:35 charon 35095 12[CFG] vici client 11118 requests: list-sas
May 6 19:17:35 charon 35095 12[CFG] vici client 11118 disconnected
May 6 19:17:40 charon 35095 09[CFG] vici client 11119 connected
May 6 19:17:40 charon 35095 08[CFG] vici client 11119 registered for: list-sa
May 6 19:17:40 charon 35095 08[CFG] vici client 11119 requests: list-sas
May 6 19:17:40 charon 35095 08[CFG] vici client 11119 disconnected
May 6 19:17:41 charon 35095 15[CFG] vici client 11120 connected
May 6 19:17:41 charon 35095 06[CFG] vici client 11120 registered for: list-sa
May 6 19:17:41 charon 35095 11[CFG] vici client 11120 requests: list-sas
May 6 19:17:41 charon 35095 06[CFG] vici client 11120 disconnected
May 6 19:17:47 charon 35095 16[CFG] vici client 11121 connected
May 6 19:17:47 charon 35095 11[CFG] vici client 11121 registered for: list-sa
May 6 19:17:47 charon 35095 11[CFG] vici client 11121 requests: list-sas
May 6 19:17:47 charon 35095 11[CFG] vici client 11121 disconnected
May 6 19:17:49 charon 35095 14[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:17:49 charon 35095 14[ENC] <con1|226> parsed INFORMATIONAL request 211 [ ]
May 6 19:17:49 charon 35095 14[ENC] <con1|226> generating INFORMATIONAL response 211 [ ]
May 6 19:17:49 charon 35095 14[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:17:52 charon 35095 07[CFG] vici client 11122 connected
May 6 19:17:52 charon 35095 13[CFG] vici client 11122 registered for: list-sa
May 6 19:17:52 charon 35095 14[CFG] vici client 11122 requests: list-sas
May 6 19:17:52 charon 35095 14[CFG] vici client 11122 disconnected
May 6 19:17:58 charon 35095 10[CFG] vici client 11123 connected
May 6 19:17:58 charon 35095 12[CFG] vici client 11123 registered for: list-sa
May 6 19:18:08 charon 35095 09[CFG] vici client 11125 registered for: list-sa
May 6 19:18:16 charon 35095 14[CFG] vici client 11127 connected
May 6 19:18:16 charon 35095 07[CFG] vici client 11127 registered for: list-sa
May 6 19:18:16 charon 35095 07[CFG] vici client 11127 requests: list-sas
May 6 19:18:16 charon 35095 07[CFG] vici client 11127 disconnected
May 6 19:18:19 charon 35095 13[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:18:19 charon 35095 13[ENC] <con1|226> parsed INFORMATIONAL request 212 [ ]
May 6 19:18:19 charon 35095 13[ENC] <con1|226> generating INFORMATIONAL response 212 [ ]
May 6 19:18:19 charon 35095 13[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:18:19 charon 35095 10[CFG] vici client 11128 connected
May 6 19:18:19 charon 35095 13[CFG] vici client 11128 registered for: list-sa
May 6 19:18:19 charon 35095 13[CFG] vici client 11128 requests: list-sas
May 6 19:18:19 charon 35095 13[CFG] vici client 11128 disconnected
May 6 19:18:24 charon 35095 05[CFG] vici client 11129 connected
May 6 19:18:24 charon 35095 08[CFG] vici client 11129 registered for: list-sa
May 6 19:18:34 charon 35095 16[CFG] vici client 11131 registered for: list-sa
May 6 19:18:34 charon 35095 11[CFG] vici client 11131 requests: list-sas
May 6 19:18:34 charon 35095 11[CFG] vici client 11131 disconnected
May 6 19:18:40 charon 35095 14[CFG] vici client 11132 connected
May 6 19:18:40 charon 35095 06[CFG] vici client 11132 registered for: list-sa
May 6 19:18:40 charon 35095 07[CFG] vici client 11132 requests: list-sas
May 6 19:18:40 charon 35095 07[CFG] vici client 11132 disconnected
May 6 19:18:42 charon 35095 13[CFG] vici client 11133 connected
May 6 19:18:42 charon 35095 10[CFG] vici client 11133 registered for: list-sa
May 6 19:18:42 charon 35095 10[CFG] vici client 11133 requests: list-sas
May 6 19:18:42 charon 35095 12[CFG] vici client 11133 disconnected
May 6 19:18:47 charon 35095 05[CFG] vici client 11134 connected
May 6 19:18:47 charon 35095 08[CFG] vici client 11134 registered for: list-sa
May 6 19:18:47 charon 35095 13[CFG] vici client 11134 requests: list-sas
May 6 19:18:47 charon 35095 13[CFG] vici client 11134 disconnected
May 6 19:18:49 charon 35095 15[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:18:49 charon 35095 15[ENC] <con1|226> parsed INFORMATIONAL request 213 [ ]
May 6 19:18:49 charon 35095 15[ENC] <con1|226> generating INFORMATIONAL response 213 [ ]
May 6 19:18:49 charon 35095 15[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:18:49 charon 35095 09[CFG] vici client 11135 connected
May 6 19:18:49 charon 35095 15[CFG] vici client 11135 registered for: list-sa
May 6 19:18:49 charon 35095 16[CFG] vici client 11135 requests: list-sas
May 6 19:18:49 charon 35095 15[CFG] vici client 11135 disconnected
May 6 19:18:53 charon 35095 16[KNL] creating rekey job for CHILD_SA ESP/0xcc4d2a04/pfsenseip
May 6 19:18:53 charon 35095 11[IKE] <con1|226> queueing CHILD_REKEY task
May 6 19:18:53 charon 35095 11[IKE] <con1|226> activating new tasks
May 6 19:18:53 charon 35095 11[IKE] <con1|226> activating CHILD_REKEY task
May 6 19:18:53 charon 35095 11[CFG] <con1|226> proposing traffic selectors for us:
May 6 19:18:53 charon 35095 11[CFG] <con1|226> 192.168.0.0/24|/0
May 6 19:18:53 charon 35095 11[CFG] <con1|226> 192.168.3.0/24|/0
May 6 19:18:53 charon 35095 11[CFG] <con1|226> proposing traffic selectors for other:
May 6 19:18:53 charon 35095 11[CFG] <con1|226> 192.168.10.0/24|/0
May 6 19:18:53 charon 35095 11[CFG] <con1|226> 192.168.10.0/24|/0
May 6 19:18:53 charon 35095 11[CFG] <con1|226> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:18:53 charon 35095 11[IKE] <con1|226> establishing CHILD_SA con1{2165} reqid 3
May 6 19:18:54 charon 35095 11[CHD] <con1|226> CHILD_SA con1{2162} state change: INSTALLED => REKEYING
May 6 19:18:54 charon 35095 11[ENC] <con1|226> generating CREATE_CHILD_SA request 9 [ N(REKEY_SA) N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 6 19:18:54 charon 35095 11[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (512 bytes)
May 6 19:18:54 charon 35095 06[CFG] vici client 11136 connected
May 6 19:18:54 charon 35095 16[CFG] vici client 11136 registered for: list-sa
May 6 19:18:54 charon 35095 16[CFG] vici client 11136 requests: list-sas
May 6 19:18:54 charon 35095 16[CFG] vici client 11136 disconnected
May 6 19:18:55 charon 35095 07[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (496 bytes)
May 6 19:18:55 charon 35095 07[ENC] <con1|226> parsed CREATE_CHILD_SA response 9 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 6 19:18:55 charon 35095 07[IKE] <con1|226> received ESP_TFC_PADDING_NOT_SUPPORTED notify
May 6 19:18:55 charon 35095 07[IKE] <con1|226> received NON_FIRST_FRAGMENTS_ALSO notify
May 6 19:18:55 charon 35095 07[IKE] <con1|226> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 6 19:18:55 charon 35095 07[CFG] <con1|226> selecting proposal:
May 6 19:18:55 charon 35095 07[CFG] <con1|226> proposal matches
May 6 19:18:55 charon 35095 07[CFG] <con1|226> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:18:55 charon 35095 07[CFG] <con1|226> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:18:55 charon 35095 07[CFG] <con1|226> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:18:55 charon 35095 07[CFG] <con1|226> selecting traffic selectors for us:
May 6 19:18:55 charon 35095 07[CFG] <con1|226> config: 192.168.0.0/24|/0, received: 192.168.0.0/24|/0 => match: 192.168.0.0/24|/0
May 6 19:18:55 charon 35095 07[CFG] <con1|226> config: 192.168.3.0/24|/0, received: 192.168.0.0/24|/0 => no match
May 6 19:18:55 charon 35095 07[CFG] <con1|226> selecting traffic selectors for other:
May 6 19:18:55 charon 35095 07[CFG] <con1|226> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 6 19:18:55 charon 35095 07[CFG] <con1|226> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 6 19:18:55 charon 35095 07[CHD] <con1|226> CHILD_SA con1{2165} state change: CREATED => INSTALLING
May 6 19:18:55 charon 35095 07[CHD] <con1|226> using AES_CBC for encryption
May 6 19:18:55 charon 35095 07[CHD] <con1|226> using HMAC_SHA2_256_128 for integrity
May 6 19:18:55 charon 35095 07[CHD] <con1|226> adding inbound ESP SA
May 6 19:18:55 charon 35095 07[CHD] <con1|226> SPI 0xc331f699, src zyxelip dst pfsenseip
May 6 19:18:55 charon 35095 07[CHD] <con1|226> registering outbound ESP SA
May 6 19:18:55 charon 35095 07[CHD] <con1|226> SPI 0x214b00d4, src pfsenseip dst zyxelip
May 6 19:18:55 charon 35095 07[IKE] <con1|226> inbound CHILD_SA con1{2165} established with SPIs c331f699_i 214b00d4_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 6 19:18:55 charon 35095 07[CHD] <con1|226> CHILD_SA con1{2165} state change: INSTALLING => INSTALLED
May 6 19:18:55 charon 35095 07[CHD] <con1|226> adding outbound ESP SA
May 6 19:18:55 charon 35095 07[CHD] <con1|226> SPI 0x214b00d4, src pfsenseip dst zyxelip
May 6 19:18:55 charon 35095 07[IKE] <con1|226> outbound CHILD_SA con1{2165} established with SPIs c331f699_i 214b00d4_o and TS 192.168.0.0/24|/0 === 192.168.10.0/24|/0
May 6 19:18:55 charon 35095 07[CHD] <con1|226> CHILD_SA con1{2162} state change: REKEYING => REKEYED
May 6 19:18:55 charon 35095 07[IKE] <con1|226> reinitiating already active tasks
May 6 19:18:55 charon 35095 07[IKE] <con1|226> CHILD_REKEY task
May 6 19:18:55 charon 35095 07[IKE] <con1|226> closing CHILD_SA con1{2162} with SPIs cc4d2a04_i (182681 bytes) 69f75052_o (1678276 bytes) and TS 192.168.3.0/24|/0 === 192.168.10.0/24|/0
May 6 19:18:55 charon 35095 07[IKE] <con1|226> sending DELETE for ESP CHILD_SA with SPI cc4d2a04
May 6 19:18:55 charon 35095 07[CHD] <con1|226> CHILD_SA con1{2162} state change: REKEYED => DELETING
May 6 19:18:55 charon 35095 07[ENC] <con1|226> generating INFORMATIONAL request 10 [ D ]
May 6 19:18:55 charon 35095 07[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:18:55 charon 35095 07[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:18:55 charon 35095 07[ENC] <con1|226> parsed INFORMATIONAL response 10 [ ]
May 6 19:18:55 charon 35095 07[IKE] <con1|226> CHILD_SA closed
May 6 19:18:55 charon 35095 07[CHD] <con1|226> CHILD_SA con1{2162} state change: DELETING => DELETED
May 6 19:18:55 charon 35095 07[IKE] <con1|226> activating new tasks
May 6 19:18:55 charon 35095 07[IKE] <con1|226> nothing to initiate
May 6 19:18:59 charon 35095 10[CFG] vici client 11137 connected
May 6 19:18:59 charon 35095 14[CFG] vici client 11137 registered for: list-sa
May 6 19:18:59 charon 35095 12[CFG] vici client 11137 requests: list-sas
May 6 19:18:59 charon 35095 14[CFG] vici client 11137 disconnected
May 6 19:19:00 charon 35095 12[IKE] <con1|226> queueing CHILD_DELETE task
May 6 19:19:00 charon 35095 12[IKE] <con1|226> activating new tasks
May 6 19:19:00 charon 35095 12[IKE] <con1|226> activating CHILD_DELETE task
May 6 19:19:00 charon 35095 12[CHD] <con1|226> CHILD_SA con1{2162} state change: DELETED => DESTROYING
May 6 19:19:00 charon 35095 12[IKE] <con1|226> activating new tasks
May 6 19:19:00 charon 35095 12[IKE] <con1|226> nothing to initiate
May 6 19:19:13 charon 35095 12[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (496 bytes)
May 6 19:19:13 charon 35095 12[ENC] <con1|226> parsed CREATE_CHILD_SA request 214 [ SA No KE TSi TSr N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) ]
May 6 19:19:13 charon 35095 12[IKE] <con1|226> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
May 6 19:19:13 charon 35095 12[CFG] <con1|226> looking for a child config for 192.168.3.0/24|/0 === 192.168.10.0/24|/0
May 6 19:19:13 charon 35095 12[CFG] <con1|226> proposing traffic selectors for us:
May 6 19:19:13 charon 35095 12[CFG] <con1|226> 192.168.0.0/24|/0
May 6 19:19:13 charon 35095 12[CFG] <con1|226> 192.168.3.0/24|/0
May 6 19:19:13 charon 35095 12[CFG] <con1|226> proposing traffic selectors for other:
May 6 19:19:13 charon 35095 12[CFG] <con1|226> 192.168.10.0/24|/0
May 6 19:19:13 charon 35095 12[CFG] <con1|226> 192.168.10.0/24|/0
May 6 19:19:13 charon 35095 12[CFG] <con1|226> candidate "con1" with prio 5+5
May 6 19:19:13 charon 35095 12[CFG] <con1|226> found matching child config "con1" with prio 10
May 6 19:19:13 charon 35095 12[CFG] <con1|226> selecting proposal:
May 6 19:19:13 charon 35095 12[CFG] <con1|226> proposal matches
May 6 19:19:13 charon 35095 12[CFG] <con1|226> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:19:13 charon 35095 12[CFG] <con1|226> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:19:13 charon 35095 12[CFG] <con1|226> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
May 6 19:19:13 charon 35095 12[CFG] <con1|226> selecting traffic selectors for us:
May 6 19:19:13 charon 35095 12[CFG] <con1|226> config: 192.168.0.0/24|/0, received: 192.168.3.0/24|/0 => no match
May 6 19:19:13 charon 35095 12[CFG] <con1|226> config: 192.168.3.0/24|/0, received: 192.168.3.0/24|/0 => match: 192.168.3.0/24|/0
May 6 19:19:13 charon 35095 12[CFG] <con1|226> selecting traffic selectors for other:
May 6 19:19:13 charon 35095 12[CFG] <con1|226> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 6 19:19:13 charon 35095 12[CFG] <con1|226> config: 192.168.10.0/24|/0, received: 192.168.10.0/24|/0 => match: 192.168.10.0/24|/0
May 6 19:19:13 charon 35095 12[CHD] <con1|226> CHILD_SA con1{2166} state change: CREATED => INSTALLING
May 6 19:19:13 charon 35095 12[CHD] <con1|226> using AES_CBC for encryption
May 6 19:19:13 charon 35095 12[CHD] <con1|226> using HMAC_SHA2_256_128 for integrity
May 6 19:19:13 charon 35095 12[CHD] <con1|226> adding inbound ESP SA
May 6 19:19:13 charon 35095 12[CHD] <con1|226> SPI 0xcd368482, src zyxelip dst pfsenseip
May 6 19:19:13 charon 35095 12[CHD] <con1|226> adding outbound ESP SA
May 6 19:19:13 charon 35095 12[CHD] <con1|226> SPI 0x9fb5373a, src pfsenseip dst zyxelip
May 6 19:19:13 charon 35095 12[IKE] <con1|226> CHILD_SA con1{2166} established with SPIs cd368482_i 9fb5373a_o and TS 192.168.3.0/24|/0 === 192.168.10.0/24|/0
May 6 19:19:13 charon 35095 12[CHD] <con1|226> CHILD_SA con1{2166} state change: INSTALLING => INSTALLED
May 6 19:19:13 charon 35095 12[ENC] <con1|226> generating CREATE_CHILD_SA response 214 [ N(ESP_TFC_PAD_N) SA No KE TSi TSr ]
May 6 19:19:13 charon 35095 12[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (480 bytes)
May 6 19:19:16 charon 35095 13[CFG] vici client 11138 connected
May 6 19:19:16 charon 35095 08[CFG] vici client 11138 registered for: list-sa
May 6 19:19:16 charon 35095 12[CFG] vici client 11138 requests: list-sas
May 6 19:19:16 charon 35095 12[CFG] vici client 11138 disconnected
May 6 19:19:16 charon 35095 15[CFG] vici client 11139 connected
May 6 19:19:16 charon 35095 09[CFG] vici client 11139 registered for: list-sa
May 6 19:19:16 charon 35095 09[CFG] vici client 11139 requests: list-sas
May 6 19:19:16 charon 35095 09[CFG] vici client 11139 disconnected
May 6 19:19:19 charon 35095 11[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:19:19 charon 35095 11[ENC] <con1|226> parsed INFORMATIONAL request 215 [ ]
May 6 19:19:19 charon 35095 11[ENC] <con1|226> generating INFORMATIONAL response 215 [ ]
May 6 19:19:19 charon 35095 11[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978] (80 bytes)
May 6 19:19:21 charon 35095 06[CFG] vici client 11140 connected
May 6 19:19:21 charon 35095 11[CFG] vici client 11140 registered for: list-sa
May 6 19:19:21 charon 35095 11[CFG] vici client 11140 requests: list-sas
May 6 19:19:37 charon 35095 10[CFG] vici client 11143 registered for: list-sa
May 6 19:19:42 charon 35095 09[CFG] vici client 11144 disconnected
May 6 19:19:47 charon 35095 15[CFG] vici client 11145 connected
May 6 19:19:47 charon 35095 08[CFG] vici client 11145 registered for: list-sa
May 6 19:19:47 charon 35095 08[CFG] vici client 11145 requests: list-sas
May 6 19:19:47 charon 35095 06[CFG] vici client 11145 disconnected
May 6 19:19:49 charon 35095 15[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500] (80 bytes)
May 6 19:19:49 charon 35095 15[ENC] <con1|226> parsed INFORMATIONAL request 216 [ ]
May 6 19:19:49 charon 35095 15[ENC] <con1|226> generating INFORMATIONAL response 216 [ ]
May 6 19:19:49 charon 35095 15[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 6 19:19:52 charon 35095 11[CFG] vici client 11146 connected
May 6 19:19:52 charon 35095 15[CFG] vici client 11146 registered for: list-sa
May 6 19:19:52 charon 35095 15[CFG] vici client 11146 requests: list-sas
May 6 19:19:52 charon 35095 15[CFG] vici client 11146 disconnected
May 6 19:19:57 charon 35095 16[CFG] vici client 11147 connected
May 6 19:19:57 charon 35095 07[CFG] vici client 11147 registered for: list-sa
May 6 19:19:57 charon 35095 07[CFG] vici client 11147 requests: list-sas
May 6 19:19:57 charon 35095 07[CFG] vici client 11147 disconnected
May 6 19:20:00 newsyslog 19505 logfile turned over due to size>500K
May 6 19:20:00 newsyslog 19505 logfile turned over due to size>500K
May 6 19:20:02 charon 35095 05[CFG] vici client 11148 connected
May 6 19:20:02 charon 35095 14[CFG] vici client 11148 registered for: list-sa
May 6 19:20:02 charon 35095 13[CFG] vici client 11148 requests: list-sas
May 6 19:20:02 charon 35095 14[CFG] vici client 11148 disconnected
May 6 19:20:08 charon 35095 12[CFG] vici client 11149 connected
May 6 19:20:08 charon 35095 13[CFG] vici client 11149 registered for: list-sa
May 6 19:20:08 charon 35095 10[CFG] vici client 11149 requests: list-sas
May 6 19:20:08 charon 35095 13[CFG] vici client 11149 disconnected
May 6 19:20:13 charon 35095 09[CFG] vici client 11150 connected
May 6 19:20:13 charon 35095 10[CFG] vici client 11150 registered for: list-sa
May 6 19:20:13 charon 35095 08[CFG] vici client 11150 requests: list-sas
May 6 19:20:13 charon 35095 09[CFG] vici client 11150 disconnected
May 6 19:20:14 charon 35095 06[CFG] vici client 11151 connected
May 6 19:20:14 charon 35095 11[CFG] vici client 11151 registered for: list-sa
May 6 19:20:14 charon 35095 06[CFG] vici client 11151 requests: list-sas
May 6 19:20:14 charon 35095 06[CFG] vici client 11151 disconnected
May 6 19:20:19 charon 35095 15[NET] <con1|226> received packet: from zyxelip[18978] to pfsenseip[4500]
May 6 19:20:19 charon 35095 15[ENC] <con1|226> parsed INFORMATIONAL request 217 [ ]
May 6 19:20:19 charon 35095 15[ENC] <con1|226> generating INFORMATIONAL response 217 [ ]
May 6 19:20:19 charon 35095 15[NET] <con1|226> sending packet: from pfsenseip[4500] to zyxelip[18978]
May 6 19:20:19 charon 35095 16[CFG] vici client 11152 connected
May 6 19:20:19 charon 35095 15[CFG] vici client 11152 registered for: list-sa
May 6 19:20:19 charon 35095 15[CFG] vici client 11152 requests: list-sas
May 6 19:20:19 charon 35095 07[CFG] vici client 11152 disconnected
May 6 19:20:33 charon 35095 10[CFG] vici client 11155 disconnected- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7046203805
[content:7002498628#7046203805]
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7046402376
[content:7002498628#7046402376]
Bedenklich ist der Fehler "config: 192.168.0.0/24|/0, received: 192.168.3.0/24|/0 => no match" was dafür spricht das es de facto irgendwo im Phase 2 Setup einen Fehler gibt! Das dürfte so nicht passieren!!
Der Zyxel geht also davon aus das sein lokales LAN 192.168.10.0/24 ist und das remote lokale LAN an der pfSense 192.168.0.0/24
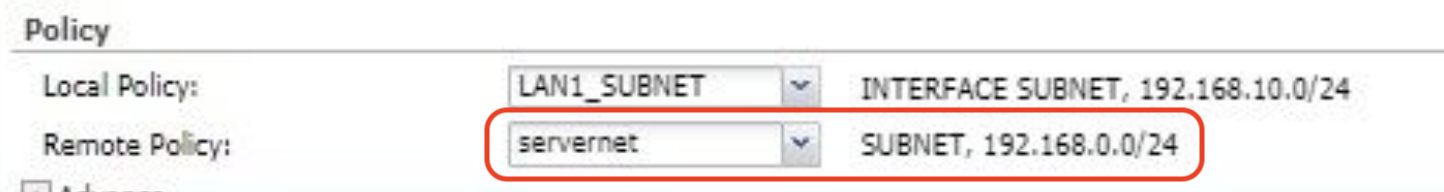
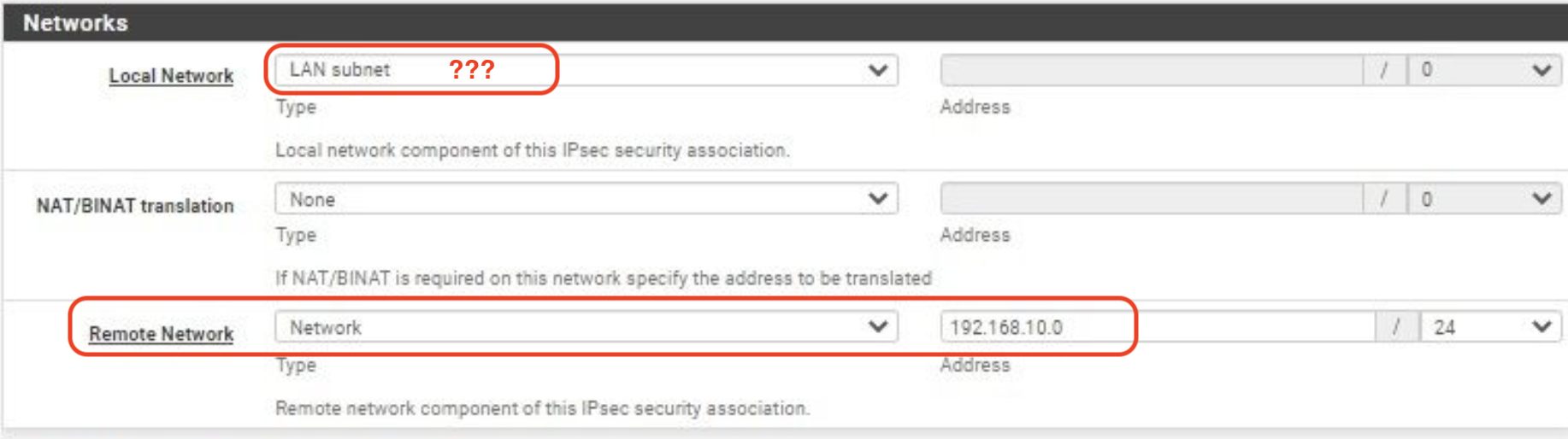
Wenn es wirklich .0.0/24 und .10.0/24 sein sollte fragt sich WOHER der eingehende Request für das remote .3.0er Netz herkommt?? Da ist also irgendwas faul!
Kann es sein das da ggf. noch irgendwelche "Konfig" Leichen vorhanden sind?!
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7046829021
[content:7002498628#7046829021]
Die Kardinalsfrage ist: WIE lautet das lokale LAN der pfSense und des Zyxel wirklich?? Lauten diese wirklich .0.0/24 und .10.0/24 und sind die auch wirklich an den LAN Schnittstellen so eingestellt bzw. korrespondieren die wirklichen LAN IP Netze mit den beidseitigen P2 Settings ??
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7053857811
[content:7002498628#7053857811]
OK, ist auch gut möglich das das nur eine informational Message ist das die pfSense den .3.0er SA lokal kennt aber dafür kein remoten P2 Request kommt.
Beide Tunnelendpunkte mal rebootet hast du?
Ich teste das nochmal an einem Mikrotik Router.
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7055917516
[content:7002498628#7055917516]
Die P2 auf der pfSense wurde hier im "Auto" Mode belassen, da der Mikrotik als Initiator dies ja fest vorgibt und der passive Responder (pfSense) sich dem immer anpassen sollte!
Local LAN pfSense = 192.168.1.0/24
Local LAN Mikrotik = 172.25.26.0/28
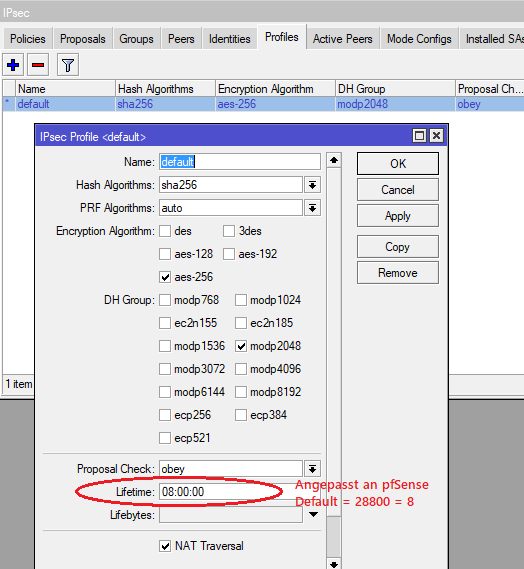
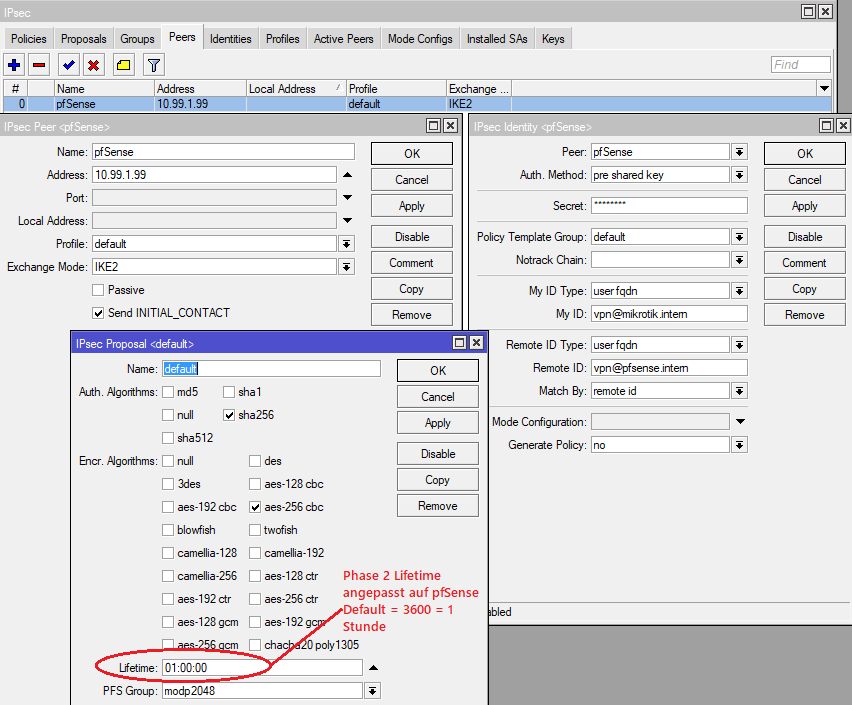
Fazit: Works as designed!! 👍 😉
Ggf. passt du dein Setup nochmal auf den Auto Mode an in der P2 der pfSense und ebenso die P1 und P2 Lifetimes des Clients (Zyxel) auf die Defaults der pfSense.
Ein Cisco IOS und IOS-XE Setup zeigt wie oben schon gesagt ein völlig identisches und damit korrektes Verhalten. Cisco nutzt die gleichen Lifetimes wie die pfSense im Default.
Dein o.a. Verhalten lässt sich zumindestens mit Standard konform arbeitenden IKEv2 Initiators leider nicht reproduzieren. Die Macke muss dann irgendwie vom Zyxel kommen.
Ob ein komplettes Neusetup ggf. das Problem löst müsstest du probieren sollte der Auto Mode und die Lifetime Anpassung nicht greifen.
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7086421985
[content:7002498628#7086421985]
Bei mir läuft mit einer Phase 2 ebenfalls alles stabil.
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7091538282
[content:7002498628#7091538282]
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7099460636
[content:7002498628#7099460636]
Ich habe nun deine Einstellung übernommen und wieder 2x Phase 2 Verbindungen eingerichtet. Es treten direkt wieder multiple SA childs auf.
Mit 1x Phase 2 Verbindung lief es über Tage stabil.
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7109263223
[content:7002498628#7109263223]
Wie könnte ich denn auf einfachstem Weg multiple Phase 2 Einträge umgehen? Auf pfSense 192.168.0.0/22 als lokales Subnetz um alle Subnetze 192.168.0.0/24-192.168.3.0/24 zu subsumieren, oder könnte ich das alternativ mit Routing erreichen?
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7138056683
[content:7002498628#7138056683]
Am Setup der pfSense wurde nur die Maske der lokalen Mikrotik LANs auf /27 vergrößert und die zweite P2 hinzugefügt. pfSense bleibt Responder der alle eingehenden IPsec Sessions annimmt.
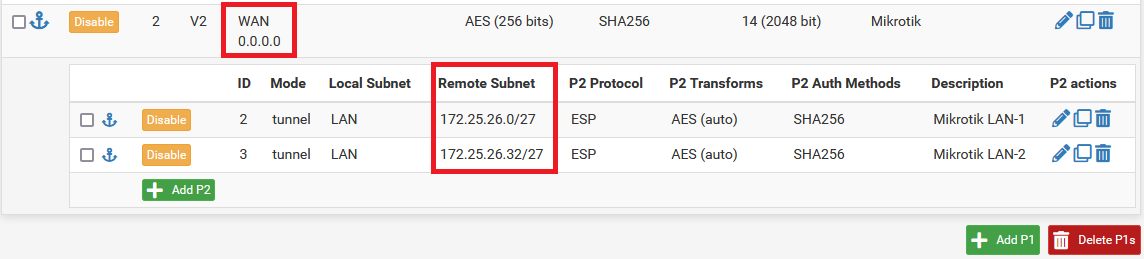
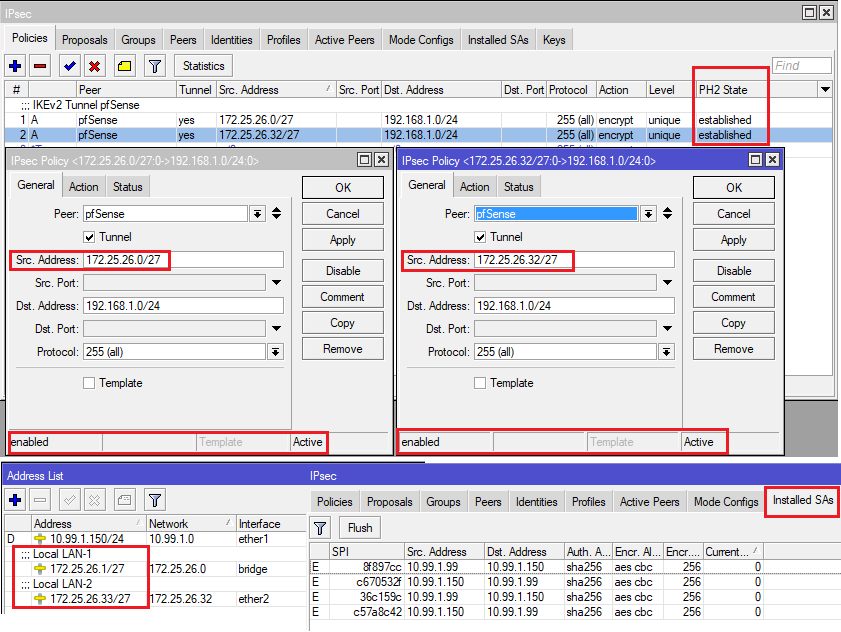
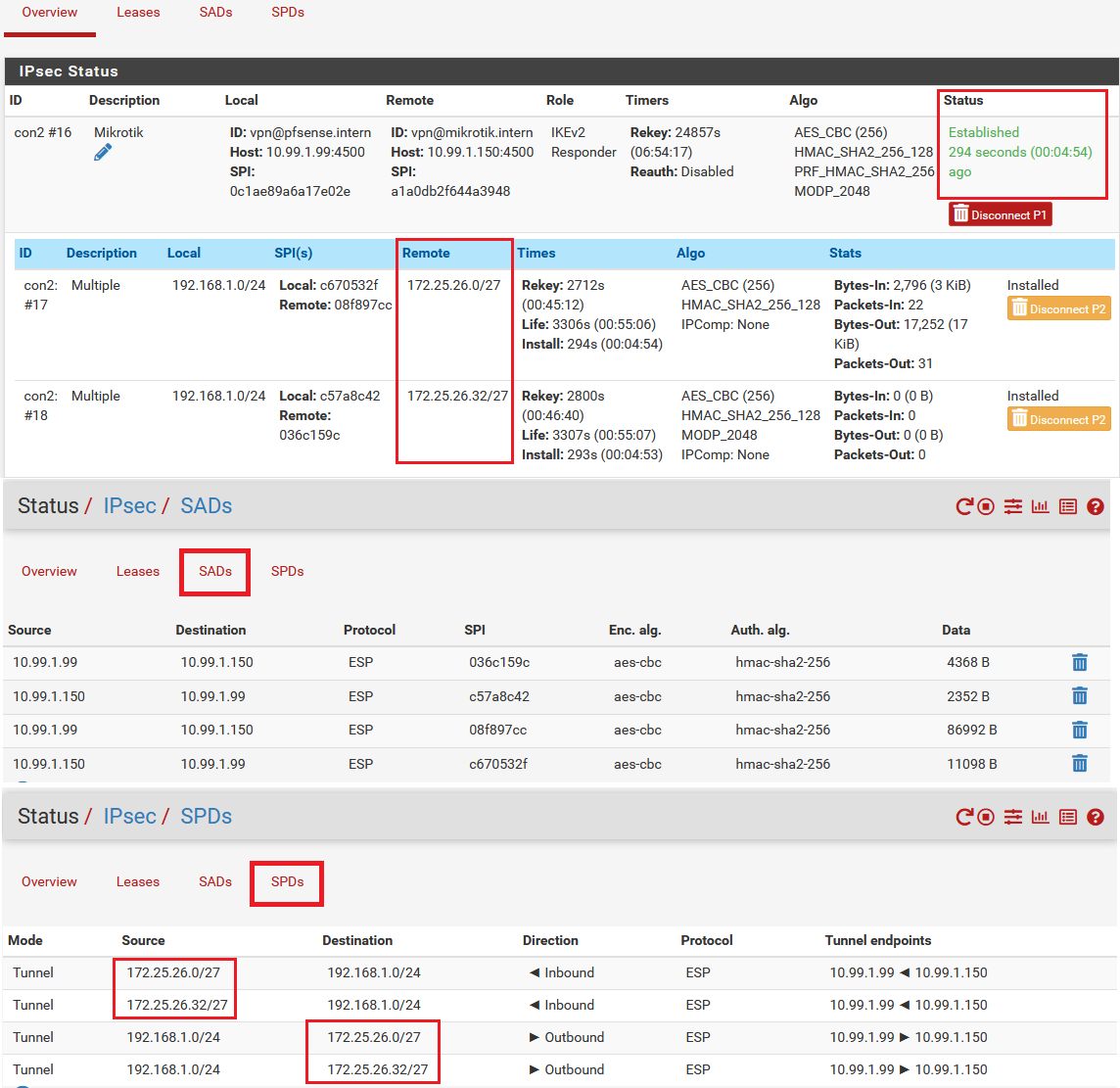
Du kannst selber sehen das sauber alle SAs und SPDs angezeigt werden auf beiden Seiten des Tunnels wie es sein soll.
Again: Works as designed!! 👍 😉
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7148684294
[content:7002498628#7148684294]
Da ich beide Netze einfach subsumieren konnte und auf eine Phase 2 Verbindung reduzieren konnte, läuft jetzt alles stabil.
Falls sonst noch jemand erfoglreich IPSec IKEv2 mit 2x Phase 2 Verbindung in der Kombination Zyxel <-> pfSense nutzt, einfach mal reinschreiben. Vielleicht habe ich ja doch etwas übersehen.
@aqui Danke für deine Hilfe
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/pfsense-vpn-site-to-site-multiple-phase-2-child-sa-eintraege-7002498628.html#comment-7148851230
[content:7002498628#7148851230]
Alles richtig gemacht! 👍