VPN Verbindungsaufbau von Linux zu Router nicht möglich
Hat jemand von euch damit Erfahrungen?
Hätte jemand zeit und könnte evtl. meiner Situation entsprechend mit mir eine Konfig erstellen?
Gruß
AzubiLE
Content-ID: 152132
Url: https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html
Ausgedruckt am: 14.07.2025 um 15:07 Uhr
- Kommentarübersicht - Bitte anmelden
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-600443
[content:152132#600443]
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-600453
[content:152132#600453]
- Welches VPN Protokoll ?
- NAT kein NAT ?
Da gibts dann nur eine Lösung
Nimm nen OpenVPN Server...
OpenVPN Server installieren auf pfSense Firewall, Mikrotik. DD-WRT oder GL.inet Router
ne IPsec Firewall...
Cisco PIX Firewall IPsec VPN Tunnel auf pfsense Firewall
oder machs mit PPTP
VPNs mit DD-WRT, pFsense oder OPNsense auf Basis von PPTP
Einfache und erfolgreiche Lösungen die in 5 Minuten Setup Zeit sicher und auf Anhieb funktionieren gibts doch hier oder im Internet zuhauf !
Ein Linux Rechner supportet alle Welten !
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-600680
[content:152132#600680]
Gruß
AzubiLE
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-601107
[content:152132#601107]
Was ich jetzt irgendwie nicht verstehe:
Ich möchte PSK verwenden, keine Zertifikate, in den Beispielen wird immer von der Konfiguration der Clientsoftware geschrieben.
Ich verwende keine Clientsoftware. Auf dem VPN-Router soll in einer Policy nur der PSK eingegeben werden und der baut dann
die Verbindung zum Remote-VPN-Server auf. Genau dieser Server muss jetzt konfiguriert werden.
Hat da jemand entsprechend HowTo's zur Hand?
Gruß
AzubiLE
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-601128
[content:152132#601128]
Und auch OpenVPN lässt sich mit einer simplen PSK Konfig betreiben:
linux-technik.de/downloads/beta/preshared-key.pdf
Zertifikate sind also in allen Verfahren keineswegs zwingend !
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-601193
[content:152132#601193]
nur keine Panik, wir wollen uns ja jetzt mal nicht die Köpfe einschlagen.
Ja Zertifikate sind nicht zwingend, ich möchte ja auch mal keine verwenden.
Muss mal wohl genauer meine Situation beschreiben:
In meinem Fall wird Debian eingesetzt. Auf diesem ist openvpn, openssl und openswan installiert.
Ich habe auf der Seite: jacco2.dds.nl/networking/openswan-l2tp.html Punkt 10 durchgeführt,
Punkt 11 bezieht sich auf einen Client, in meinem Fall ist der Client der Netgear Router,
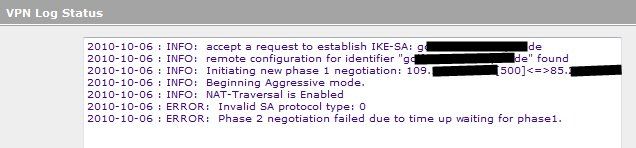
nun scheitere ich bei Punkt 12 bzw. der Router bringt mir beim Verbindungsversuch folgende Meldung:
2010-10-04 : INFO: accept a request to establish IKE-SA: 85.XX.XX.XX
2010-10-04 : INFO: Configuration found for 85.XX.XX.XX.
2010-10-04 : INFO: Initiating new phase 1 negotiation: 109.XX.XX.XX[500]<=>85.XX.XX.XX[500]
2010-10-04 : INFO: Beginning Aggressive mode.
2010-10-04 : INFO: NAT-Traversal is Enabled
2010-10-04 : ERROR: Invalid SA protocol type: 0
2010-10-04 : ERROR: Phase 2 negotiation failed due to time up waiting for phase1.
2010-10-04 : ERROR: Phase 1 negotiation failed due to time up for 85.XX.XX.XX[500].
Die Konfigurationsdateien sehen wie folgt aus:
ipsec.conf:
conn hotel
authby=secret
pfs=no
rekey=no
keyingtries=3
left=%defaultroute
leftprotoport=17/1701
- Allow incoming connections only from this IP address.
rightprotoport=17/%any
auto=add
ipsec.secrets:
- Preshared Key for clients connecting from any IP address:
Somit bitte ich etwas um Rücksicht auf meine Unwissenheit zu nehmen und ich wäre froh wenn der eine
andere mich auf den richtigen Weg bringen kann
Danke!
Gruß
AzubiLE
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-601248
[content:152132#601248]
Im Zweifel schmeiss den NetGear an die Wand und stell da was anständiges hin was acuh VPN (wirklich) kann.
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-601398
[content:152132#601398]
Das hilft ja schon mal etwas weiter. Den Netgear kann ich leider nicht an dei Wand werfen, da der extern steht.
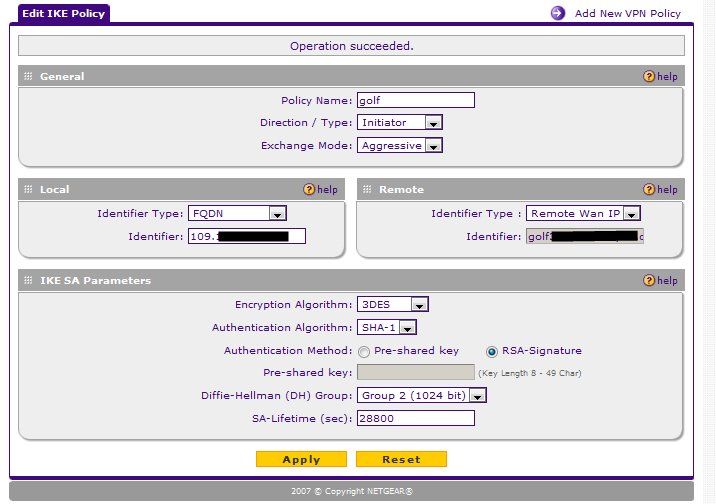
Was jetzt die Algorithmen angeht: auf dem Netgear ist eine IKE- und VPN-Policy eingerichtet die als encryption 3DES und als authentication SHA verwendet.
Wie im vorigen Post geschrieben habe ich Punkt 10 abgearbeitet und die Config-Files erstellt. Was muss ich jetzt tun, damit auf dem Server, auf dem der key in ipsec.secrets hintelegt ist mit 3DES verschlüsselt wird bzw. der Tunnel die Gegebenheiten aufweist, damit der Austausch stattfinden kann?
Gruß
AzubiLE
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-601774
[content:152132#601774]
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-601933
[content:152132#601933]
Ich habe auf dem Server anhand dieser Anleitung: linuxconfig.org/VPN_-_Virtual_Private_Network_and_OpenVPN
ab Punkt 10.3 die Konfigurationen abgearbeitet.
Hier die openvpn-server.conf die Anhand der Anleitung erstellt wordne ist:
#OpenVPN server configuration file example
local 85.XX.XX.XX
dev tun
server 192.168.0.0 255.255.255.0
ca ca-certificate.pem
cert vpn-server-certificate.pem
key privkey.pem
dh dh.pem
push "redirect-gateway"
comp-lzo
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
user openvpn
group openvpn
daemon
Auf dem Router wurden Policies angelegt und die entsprechenden Zertifikate hochgeladen.
Hier kann man die IKE-Policy sehen:
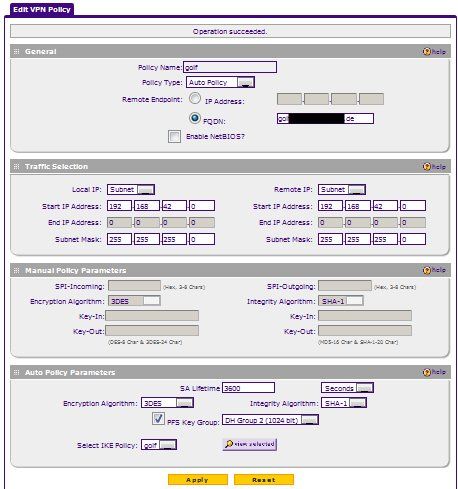
Hier kann man die VPN-Policy sehen:
Hier kann man die Zertifikate sehen:

Hier ist der Log-Auszug bei dem Verbindugsversuche mit Fehlermeldung:
So kann sich jemand erklären warum das Ganze nicht funktioniert? Was hab ich übersehen?
Grüße
AzubiLE
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-602277
[content:152132#602277]
NetGear spricht IPsec im ESP Mode !!
OpenVPN spricht SSL !!
Kann ein Chinese einen Russen verstehen ??
Kannst du als Deutscher Kisuaheli verstehen ??
Siehste !! Deshalb kann auch OpenVPN SSL kein IPsec verstehen !!
Falsche Baustelle, da 2 völlig verschiedene inkompatible VPN Verfahren !!! Vergiss das also, das wirst du auch durch noch so viele Screenshots nicht lösen können (sowieso schon mal gar nicht mit NetGear !!)
Fazit: OpenVPN muss mit OpenVPN sprechen, IPsec spricht mit IPsec, PPTP spricht mit PPTP usw. usw.
Es gibt wie bei humanoiden Sprachen auch unterschiedliche VPN "Sprachen" !!
Nun verstanden ???
Wenn es bei dir an solchen simplen VPN Basics schon scheitert solltest du ggf. mal jemanden fragen der weiss was er macht ?! Sorry....
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-602448
[content:152132#602448]
Muss dann wohl eine andere Lösung her.
Gruß
AzubiLE
- Internen Kommentar-Link kopieren
- Externen Kommentar-Link kopieren
- Zum Anfang der Kommentare
https://administrator.de/forum/vpn-verbindungsaufbau-von-linux-zu-router-nicht-moeglich-152132.html#comment-610540
[content:152132#610540]
Es gab mittlerweile ein paar Fortschritte was die Konfiguration und den Verbindugsaufbau angeht.
ipsec.conf:
version 2.0 # conforms to second version of ipsec.conf specification
config setup
interfaces=%defaultroute
klipsdebug=all
plutodebug=all
#plutoload=%search
uniqueids=yes
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/24,%v4:192.168.42.0/24,%v4:172.16.0.0/12
nhelpers=0
#include /etc/ipsec.d/examples/no_oe.conf
#Beginning config
conn %default
keyingtries=0
authby=secret
conn golf335
type=tunnel
left=85.XX.XX.216 #WAN ip address of local router
leftsubnet=192.168.42.0/24 #ip address of CC LAN subnet
leftnexthop=%defaultroute #ip address of local internet gateway
leftid=85.XX.XX.216 #WAN IP
right=95.XX.XX.201 #WAN ip address of remote netgear fvs318
rightnexthop=%defaultroute #ip address of remote internet gateway
rightsubnet=192.168.0.0/24 #ip address of netear LAN subnet
rightid=95.XX.XX.201 #WAN IP
auth=esp
ike=3des-sha1-modp1024 #ike policy settings
ikelifetime=28800s #ike lifetime
keylife=3600s #key life
pfs=no #pfs is off, could not get pfs working
keyexchange=ike #tell it to use ike(not AH)
authby=secret #tells it to use a PSK for authentication
auto=add
aggrmode=yes
esp=3des-sha1 #phase 2 encryption
include /etc/ipsec.d/examples/no_oe.conf
#End of config
ipsec.secrets:
- PSK "mysharedsecret"
Beim Verbindugsversuch erscheinen nun folgende Meldungen:
Seitens Router: - INFO: accept a request to establish IKE-SA: 85.XX.XX.216
: INFO: Configuration found for 85.XX.XX.216.
: INFO: Initiating new phase 1 negotiation: 95.XX.XX.201[500]<=>85.XX.XX.216[500]
: INFO: Beginning Aggressive mode.
: INFO: NAT-Traversal is Enabled
: INFO: Received unknown Vendor ID
: INFO: ISAKMP-SA established for 95.XX.XX.201[500]-85.XX.XX.216[500] with spi:e5ce8a2e2f00b321:a6b177033f22b9be
: INFO: Sending Informational Exchange: notify payload[INITIAL-CONTACT]
: ERROR: Ignore information because the message has no hash payload.
: ERROR: Ignore information because the message has no hash payload.
: INFO: Initiating new phase 2 negotiation: 95.XX.XX.201[500]<=>85.XX.XX.216
: ERROR: Ignore information because the message has no hash payload.
: NOTIFY: The packet is retransmitted by 85.XX.XX.216[500].
: ERROR: Ignore information because the message has no hash payload.
: ERROR: Ignore information because the message has no hash payload.
: ERROR: Ignore information because the message has no hash payload.
: NOTIFY: The packet is retransmitted by 85.XX.XX.216[500].
: ERROR: Ignore information because the message has no hash payload.
: ERROR: Giving up on 85.XX.XX.216 to set up IPsec-SA due to time up
Seitens Linux:
auth.log:
golf335 pluto[2172]: |
golf335 pluto[2172]: | *time to handle event
golf335 pluto[2172]: | handling event EVENT_PENDING_PHASE2
golf335 pluto[2172]: | event after this is EVENT_REINIT_SECRET in 200 seconds
golf335 pluto[2172]: | inserting event EVENT_PENDING_PHASE2, timeout in 120 seconds
golf335 pluto[2172]: | pending review: connection "golf335" was not up, skipped
golf335 pluto[2172]: | next event EVENT_PENDING_PHASE2 in 120 seconds
golf335 pluto[2172]: |
golf335 pluto[2172]: | *received 264 bytes from 95.XX.XX.201:500 on eth0 (port=500)
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 00 00 00 00 00 00 00 00
golf335 pluto[2172]: | 01 10 04 00 00 00 00 00 00 00 01 08 04 00 00 34
golf335 pluto[2172]: | 00 00 00 01 00 00 00 01 00 00 00 28 01 01 00 01
golf335 pluto[2172]: | 00 00 00 20 01 01 00 00 80 0b 00 01 80 0c 70 80
golf335 pluto[2172]: | 80 01 00 05 80 03 00 01 80 02 00 02 80 04 00 02
golf335 pluto[2172]: | 0a 00 00 84 79 77 9c 7d 70 54 5b 4e 53 bb 23 c1
golf335 pluto[2172]: | 87 d0 77 90 8d 57 85 dd 00 d0 a8 2a e9 56 7c d6
golf335 pluto[2172]: | 8e 1f c9 1d 81 ca ee 75 97 30 07 ae 0c 73 9d 4d
golf335 pluto[2172]: | 45 1b ca e9 a9 38 c9 3f d5 12 44 79 a6 c1 e4 05
golf335 pluto[2172]: | d3 01 8c a3 98 88 f9 7d f0 0c a2 ea 4c e1 b4 d8
golf335 pluto[2172]: | 4c ac cb d6 67 7b c6 24 06 23 a1 9c 11 99 b7 55
golf335 pluto[2172]: | 01 cf ab ac 39 02 92 4c d3 d2 5a 10 dd 6b b1 ff
golf335 pluto[2172]: | b0 ac 1e 56 bb 66 40 c6 b2 54 ce d7 cb d6 ea bf
golf335 pluto[2172]: | 38 8d bd 69 05 00 00 14 d2 86 bd 92 11 c9 27 40
golf335 pluto[2172]: | f0 60 83 db 72 60 9c 2c 0d 00 00 0c 01 11 01 f4
golf335 pluto[2172]: | 5f d0 2a c9 00 00 00 14 81 0f a5 65 f8 ab 14 36
golf335 pluto[2172]: | 91 05 d7 06 fb d5 72 79
golf335 pluto[2172]: | parse ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | 00 00 00 00 00 00 00 00
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_SA
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_AGGR
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 00 00 00 00
golf335 pluto[2172]: | length: 264
golf335 pluto[2172]: | processing packet with exchange type=ISAKMP_XCHG_AGGR (4)
golf335 pluto[2172]: | np=1 and sd=0x4a2cb0
golf335 pluto[2172]: | *parse ISAKMP Security Association Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_KE
golf335 pluto[2172]: | length: 52
golf335 pluto[2172]: | DOI: ISAKMP_DOI_IPSEC
golf335 pluto[2172]: | np=4 and sd=0x4a2d90
golf335 pluto[2172]: | *parse ISAKMP Key Exchange Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONCE
golf335 pluto[2172]: | length: 132
golf335 pluto[2172]: | np=10 and sd=0x4a2e70
golf335 pluto[2172]: | *parse ISAKMP Nonce Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_ID
golf335 pluto[2172]: | length: 20
golf335 pluto[2172]: | np=5 and sd=(nil)
golf335 pluto[2172]: | *parse ISAKMP Identification Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_VID
golf335 pluto[2172]: | length: 12
golf335 pluto[2172]: | ID type: ID_IPV4_ADDR
golf335 pluto[2172]: | DOI specific A: 17
golf335 pluto[2172]: | DOI specific B: 500
golf335 pluto[2172]: | np=13 and sd=0x4a2ed0
golf335 pluto[2172]: | *parse ISAKMP Vendor ID Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | length: 20
golf335 pluto[2172]: packet from 95.XX.XX.201:500: ignoring unknown Vendor ID payload [810fa565f8ab14369105d706fbd57279]
golf335 pluto[2172]: | find_host_connection called from aggr_inI1_outR1_common
golf335 pluto[2172]: | find_host_pair: comparing to 85.XX.XX.216:500 95.XX.XX.201:500
golf335 pluto[2172]: | find_host_pair_conn (find_host_connection2): 85.XX.XX.216:500 95.XX.XX.201:500 -> hp:golf335
golf335 pluto[2172]: | creating state object #3 at 0xf18d40
golf335 pluto[2172]: "golf335" #3: Aggressive mode peer ID is ID_IPV4_ADDR: '95.XX.XX.201'
golf335 pluto[2172]: | refine_connection: starting with golf335
golf335 pluto[2172]: | trusted_ca called with a=(empty) b=(empty)
golf335 pluto[2172]: | refine_connection: happy with starting point: golf335
golf335 pluto[2172]: | offered CA: '%none'
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | inserting event EVENT_SO_DISCARD, timeout in 0 seconds for #3
golf335 pluto[2172]: "golf335" #3: responding to Aggressive Mode, state #3, connection "golf335" from 95.XX.XX.201
golf335 pluto[2172]: | parse IPsec DOI SIT:
golf335 pluto[2172]: | IPsec DOI SIT: SIT_IDENTITY_ONLY
golf335 pluto[2172]: | parse ISAKMP Proposal Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | length: 40
golf335 pluto[2172]: | proposal number: 1
golf335 pluto[2172]: | protocol ID: PROTO_ISAKMP
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | number of transforms: 1
golf335 pluto[2172]: | *parse ISAKMP Transform Payload (ISAKMP):
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | length: 32
golf335 pluto[2172]: | transform number: 1
golf335 pluto[2172]: | transform ID: KEY_IKE
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_LIFE_TYPE
golf335 pluto[2172]: | length/value: 1
golf335 pluto[2172]: | [1 is OAKLEY_LIFE_SECONDS]
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_LIFE_DURATION
golf335 pluto[2172]: | length/value: 28800
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_ENCRYPTION_ALGORITHM
golf335 pluto[2172]: | length/value: 5
golf335 pluto[2172]: | [5 is OAKLEY_3DES_CBC]
golf335 pluto[2172]: | ike_alg_enc_ok(ealg=5,key_len=0): blocksize=8, keyminlen=192, keydeflen=192, keymaxlen=192, ret=1
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_AUTHENTICATION_METHOD
golf335 pluto[2172]: | length/value: 1
golf335 pluto[2172]: | [1 is OAKLEY_PRESHARED_KEY]
golf335 pluto[2172]: | started looking for secret for 85.XX.XX.216->95.XX.XX.201 of kind PPK_PSK
golf335 pluto[2172]: | actually looking for secret for 85.XX.XX.216->95.XX.XX.201 of kind PPK_PSK
golf335 pluto[2172]: | best_match 0>1 best=0xf17340 (line=15)
golf335 pluto[2172]: | concluding with best_match=1 best=0xf17340 (lineno=15)
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_HASH_ALGORITHM
golf335 pluto[2172]: | length/value: 2
golf335 pluto[2172]: | [2 is OAKLEY_SHA1]
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_GROUP_DESCRIPTION
golf335 pluto[2172]: | length/value: 2
golf335 pluto[2172]: | [2 is OAKLEY_GROUP_MODP1024]
golf335 pluto[2172]: | Oakley Transform 1 accepted
golf335 pluto[2172]: | DH public value received:
golf335 pluto[2172]: | 79 77 9c 7d 70 54 5b 4e 53 bb 23 c1 87 d0 77 90
golf335 pluto[2172]: | 8d 57 85 dd 00 d0 a8 2a e9 56 7c d6 8e 1f c9 1d
golf335 pluto[2172]: | 81 ca ee 75 97 30 07 ae 0c 73 9d 4d 45 1b ca e9
golf335 pluto[2172]: | a9 38 c9 3f d5 12 44 79 a6 c1 e4 05 d3 01 8c a3
golf335 pluto[2172]: | 98 88 f9 7d f0 0c a2 ea 4c e1 b4 d8 4c ac cb d6
golf335 pluto[2172]: | 67 7b c6 24 06 23 a1 9c 11 99 b7 55 01 cf ab ac
golf335 pluto[2172]: | 39 02 92 4c d3 d2 5a 10 dd 6b b1 ff b0 ac 1e 56
golf335 pluto[2172]: | bb 66 40 c6 b2 54 ce d7 cb d6 ea bf 38 8d bd 69
golf335 pluto[2172]: | helper -1 doing build_kenonce op id: 0
golf335 pluto[2172]: | Local DH secret:
golf335 pluto[2172]: | bd 9d fd 35 f9 41 a9 68 5f 43 8a 05 c7 61 b4 c4
golf335 pluto[2172]: | 0f cf eb 57 d7 19 b2 4f 01 92 2a 4f a6 09 89 0c
golf335 pluto[2172]: | Public DH value sent:
golf335 pluto[2172]: | 47 af 54 0d 82 38 a5 34 d5 15 f2 17 b9 55 ca ed
golf335 pluto[2172]: | 85 00 c5 eb 92 2d 9e 19 b1 5f e9 a5 83 9c b6 5c
golf335 pluto[2172]: | 33 d1 d6 18 4d 75 aa 3e 46 09 5e 48 31 2b da c0
golf335 pluto[2172]: | 44 44 9b 4c 9f 8f 95 87 62 30 2b 74 e8 34 88 5c
golf335 pluto[2172]: | aa 3b 55 b9 16 0d f6 54 76 cd 33 a0 b4 da 2b 23
golf335 pluto[2172]: | 04 f4 ce d3 a7 de 27 12 1c b6 94 27 00 8a 51 d9
golf335 pluto[2172]: | 19 e8 79 8b 18 b5 be 99 0c f1 b7 e8 74 e0 5f ff
golf335 pluto[2172]: | 0a 96 99 53 19 6c a3 26 a3 f2 34 c0 b6 de 6f 47
golf335 pluto[2172]: | Generated nonce:
golf335 pluto[2172]: | 38 4d d8 c8 13 83 4d b8 96 24 24 12 a8 36 d7 3f
golf335 pluto[2172]: | aggr inI1_outR1: calculated ke+nonce, sending R1
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: | emit ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_SA
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_AGGR
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 00 00 00 00
golf335 pluto[2172]: | *emit ISAKMP Security Association Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_KE
golf335 pluto[2172]: | DOI: ISAKMP_DOI_IPSEC
golf335 pluto[2172]: | parse IPsec DOI SIT:
golf335 pluto[2172]: | IPsec DOI SIT: SIT_IDENTITY_ONLY
golf335 pluto[2172]: | parse ISAKMP Proposal Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | length: 40
golf335 pluto[2172]: | proposal number: 1
golf335 pluto[2172]: | protocol ID: PROTO_ISAKMP
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | number of transforms: 1
golf335 pluto[2172]: | *parse ISAKMP Transform Payload (ISAKMP):
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | length: 32
golf335 pluto[2172]: | transform number: 1
golf335 pluto[2172]: | transform ID: KEY_IKE
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_LIFE_TYPE
golf335 pluto[2172]: | length/value: 1
golf335 pluto[2172]: | [1 is OAKLEY_LIFE_SECONDS]
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_LIFE_DURATION
golf335 pluto[2172]: | length/value: 28800
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_ENCRYPTION_ALGORITHM
golf335 pluto[2172]: | length/value: 5
golf335 pluto[2172]: | [5 is OAKLEY_3DES_CBC]
golf335 pluto[2172]: | ike_alg_enc_ok(ealg=5,key_len=0): blocksize=8, keyminlen=192, keydeflen=192, keymaxlen=192, ret=1
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_AUTHENTICATION_METHOD
golf335 pluto[2172]: | length/value: 1
golf335 pluto[2172]: | [1 is OAKLEY_PRESHARED_KEY]
golf335 pluto[2172]: | started looking for secret for 85.XX.XX.216->95.XX.XX.201 of kind PPK_PSK
golf335 pluto[2172]: | actually looking for secret for 85.XX.XX.216->95.XX.XX.201 of kind PPK_PSK
golf335 pluto[2172]: | best_match 0>1 best=0xf17340 (line=15)
golf335 pluto[2172]: | concluding with best_match=1 best=0xf17340 (lineno=15)
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_HASH_ALGORITHM
golf335 pluto[2172]: | length/value: 2
golf335 pluto[2172]: | [2 is OAKLEY_SHA1]
golf335 pluto[2172]: | parse ISAKMP Oakley attribute:
golf335 pluto[2172]: | af+type: OAKLEY_GROUP_DESCRIPTION
golf335 pluto[2172]: | length/value: 2
golf335 pluto[2172]: | [2 is OAKLEY_GROUP_MODP1024]
golf335 pluto[2172]: | Oakley Transform 1 accepted
golf335 pluto[2172]: | emit IPsec DOI SIT:
golf335 pluto[2172]: | IPsec DOI SIT: SIT_IDENTITY_ONLY
golf335 pluto[2172]: | emit ISAKMP Proposal Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | proposal number: 1
golf335 pluto[2172]: | protocol ID: PROTO_ISAKMP
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | number of transforms: 1
golf335 pluto[2172]: | *emit ISAKMP Transform Payload (ISAKMP):
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | transform number: 1
golf335 pluto[2172]: | transform ID: KEY_IKE
golf335 pluto[2172]: | emitting 24 raw bytes of attributes into ISAKMP Transform Payload (ISAKMP)
golf335 pluto[2172]: | attributes 80 0b 00 01 80 0c 70 80 80 01 00 05 80 03 00 01
golf335 pluto[2172]: | 80 02 00 02 80 04 00 02
golf335 pluto[2172]: | emitting length of ISAKMP Transform Payload (ISAKMP): 32
golf335 pluto[2172]: | emitting length of ISAKMP Proposal Payload: 40
golf335 pluto[2172]: | emitting length of ISAKMP Security Association Payload: 52
golf335 pluto[2172]: | *emit ISAKMP Key Exchange Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONCE
golf335 pluto[2172]: | emitting 128 raw bytes of keyex value into ISAKMP Key Exchange Payload
golf335 pluto[2172]: | keyex value 47 af 54 0d 82 38 a5 34 d5 15 f2 17 b9 55 ca ed
golf335 pluto[2172]: | 85 00 c5 eb 92 2d 9e 19 b1 5f e9 a5 83 9c b6 5c
golf335 pluto[2172]: | 33 d1 d6 18 4d 75 aa 3e 46 09 5e 48 31 2b da c0
golf335 pluto[2172]: | 44 44 9b 4c 9f 8f 95 87 62 30 2b 74 e8 34 88 5c
golf335 pluto[2172]: | aa 3b 55 b9 16 0d f6 54 76 cd 33 a0 b4 da 2b 23
golf335 pluto[2172]: | 04 f4 ce d3 a7 de 27 12 1c b6 94 27 00 8a 51 d9
golf335 pluto[2172]: | 19 e8 79 8b 18 b5 be 99 0c f1 b7 e8 74 e0 5f ff
golf335 pluto[2172]: | 0a 96 99 53 19 6c a3 26 a3 f2 34 c0 b6 de 6f 47
golf335 pluto[2172]: | emitting length of ISAKMP Key Exchange Payload: 132
golf335 pluto[2172]: | *emit ISAKMP Nonce Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_ID
golf335 pluto[2172]: | emitting 16 raw bytes of Nr into ISAKMP Nonce Payload
golf335 pluto[2172]: | Nr 38 4d d8 c8 13 83 4d b8 96 24 24 12 a8 36 d7 3f
golf335 pluto[2172]: | emitting length of ISAKMP Nonce Payload: 20
golf335 pluto[2172]: | *emit ISAKMP Identification Payload (IPsec DOI):
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_HASH
golf335 pluto[2172]: | ID type: ID_IPV4_ADDR
golf335 pluto[2172]: | Protocol ID: 0
golf335 pluto[2172]: | port: 0
golf335 pluto[2172]: | emitting 4 raw bytes of my identity into ISAKMP Identification Payload (IPsec DOI)
golf335 pluto[2172]: | my identity 55 19 8f d8
golf335 pluto[2172]: | emitting length of ISAKMP Identification Payload (IPsec DOI): 12
golf335 pluto[2172]: | started looking for secret for 85.XX.XX.216->95.XX.XX.201 of kind PPK_PSK
golf335 pluto[2172]: | actually looking for secret for 85.XX.XX.216->95.XX.XX.201 of kind PPK_PSK
golf335 pluto[2172]: | best_match 0>1 best=0xf17340 (line=15)
golf335 pluto[2172]: | concluding with best_match=1 best=0xf17340 (lineno=15)
golf335 pluto[2172]: | calc_dh_shared(): time elapsed (OAKLEY_GROUP_MODP1024): 524 usec
golf335 pluto[2172]: | DH shared secret:
golf335 pluto[2172]: | 45 f7 2c a7 38 81 82 b9 fd 80 af b8 23 ee e3 96
golf335 pluto[2172]: | 16 39 79 87 60 39 7b 4c 31 4d 15 89 d4 2c 3e 43
golf335 pluto[2172]: | 21 25 d5 b1 c2 52 9d 65 5f 92 bc f0 05 b3 51 f4
golf335 pluto[2172]: | 34 a7 0e d8 17 f8 35 c9 cc 5c e3 45 54 46 3f 95
golf335 pluto[2172]: | 6a 8d 94 16 4c 7f 12 43 8d 55 5b 6d bb 25 92 be
golf335 pluto[2172]: | 9a bd ce 72 1a f7 a4 eb 6a a0 70 80 f4 6c b2 81
golf335 pluto[2172]: | 6a 35 35 fb c5 a8 c2 13 6e a5 42 6b 85 a1 7a 40
golf335 pluto[2172]: | 23 b1 b8 26 2c e9 0f fd 2d 3f 96 11 d1 44 52 04
golf335 pluto[2172]: | Skey inputs (PSK+NI+NR)
golf335 pluto[2172]: | ni: d2 86 bd 92 11 c9 27 40 f0 60 83 db 72 60 9c 2c
golf335 pluto[2172]: | nr: 38 4d d8 c8 13 83 4d b8 96 24 24 12 a8 36 d7 3f
golf335 pluto[2172]: | keyid: 1f 5a ea 7f 3a fa a9 d7 88 e1 74 0d 41 af a6 9c
golf335 pluto[2172]: | 90 5d 57 09
golf335 pluto[2172]: | DH_i: 79 77 9c 7d 70 54 5b 4e 53 bb 23 c1 87 d0 77 90
golf335 pluto[2172]: | 8d 57 85 dd 00 d0 a8 2a e9 56 7c d6 8e 1f c9 1d
golf335 pluto[2172]: | 81 ca ee 75 97 30 07 ae 0c 73 9d 4d 45 1b ca e9
golf335 pluto[2172]: | a9 38 c9 3f d5 12 44 79 a6 c1 e4 05 d3 01 8c a3
golf335 pluto[2172]: | 98 88 f9 7d f0 0c a2 ea 4c e1 b4 d8 4c ac cb d6
golf335 pluto[2172]: | 67 7b c6 24 06 23 a1 9c 11 99 b7 55 01 cf ab ac
golf335 pluto[2172]: | 39 02 92 4c d3 d2 5a 10 dd 6b b1 ff b0 ac 1e 56
golf335 pluto[2172]: | bb 66 40 c6 b2 54 ce d7 cb d6 ea bf 38 8d bd 69
golf335 pluto[2172]: | DH_r: 47 af 54 0d 82 38 a5 34 d5 15 f2 17 b9 55 ca ed
golf335 pluto[2172]: | 85 00 c5 eb 92 2d 9e 19 b1 5f e9 a5 83 9c b6 5c
golf335 pluto[2172]: | 33 d1 d6 18 4d 75 aa 3e 46 09 5e 48 31 2b da c0
golf335 pluto[2172]: | 44 44 9b 4c 9f 8f 95 87 62 30 2b 74 e8 34 88 5c
golf335 pluto[2172]: | aa 3b 55 b9 16 0d f6 54 76 cd 33 a0 b4 da 2b 23
golf335 pluto[2172]: | 04 f4 ce d3 a7 de 27 12 1c b6 94 27 00 8a 51 d9
golf335 pluto[2172]: | 19 e8 79 8b 18 b5 be 99 0c f1 b7 e8 74 e0 5f ff
golf335 pluto[2172]: | 0a 96 99 53 19 6c a3 26 a3 f2 34 c0 b6 de 6f 47
golf335 pluto[2172]: | Skeyid: 1f 5a ea 7f 3a fa a9 d7 88 e1 74 0d 41 af a6 9c
golf335 pluto[2172]: | 90 5d 57 09
golf335 pluto[2172]: | Skeyid_d: c1 5f bf a8 d9 50 7a 64 72 e3 81 ff 9c f7 ed cc
golf335 pluto[2172]: | d5 ec 48 57
golf335 pluto[2172]: | Skeyid_a: 92 ac 3c e3 d6 05 f0 f0 c6 c3 63 4d 55 fe d8 a0
golf335 pluto[2172]: | 44 c2 f0 64
golf335 pluto[2172]: | Skeyid_e: 8c 06 7f f0 85 f9 e6 c0 55 65 dc 88 31 45 90 7d
golf335 pluto[2172]: | 84 a7 fe f5
golf335 pluto[2172]: | enc key: a5 9e f6 df 65 70 07 54 90 c6 99 d4 e1 31 6c 18
golf335 pluto[2172]: | 59 d3 02 bc 0d a5 09 6d
golf335 pluto[2172]: | IV: a6 97 56 7d 5d a6 1e a1 8c 9c b0 60 04 ad d2 98
golf335 pluto[2172]: | a8 68 31 f0
golf335 pluto[2172]: | hashing 48 bytes of SA
golf335 pluto[2172]: | *emit ISAKMP Hash Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_VID
golf335 pluto[2172]: | emitting 20 raw bytes of HASH_R into ISAKMP Hash Payload
golf335 pluto[2172]: | HASH_R 03 ef aa 94 10 f5 04 ba b7 61 8c 4f 23 28 25 2b
golf335 pluto[2172]: | b0 ad fe 40
golf335 pluto[2172]: | emitting length of ISAKMP Hash Payload: 24
golf335 pluto[2172]: | *emit ISAKMP Vendor ID Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | emitting 16 raw bytes of DPP Vendor ID into ISAKMP Vendor ID Payload
golf335 pluto[2172]: | DPP Vendor ID af ca d7 13 68 a1 f1 c9 6b 86 96 fc 77 57 01 00
golf335 pluto[2172]: | emitting length of ISAKMP Vendor ID Payload: 20
golf335 pluto[2172]: | emitting length of ISAKMP Message: 288
golf335 pluto[2172]: | complete state transition with STF_OK
golf335 pluto[2172]: "golf335" #3: transition from state STATE_AGGR_R0 to state STATE_AGGR_R1
golf335 pluto[2172]: | sending reply packet to 95.XX.XX.201:500 (from port=500)
golf335 pluto[2172]: | sending 288 bytes for STATE_AGGR_R0 through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 01 10 04 00 00 00 00 00 00 00 01 20 04 00 00 34
golf335 pluto[2172]: | 00 00 00 01 00 00 00 01 00 00 00 28 01 01 00 01
golf335 pluto[2172]: | 00 00 00 20 01 01 00 00 80 0b 00 01 80 0c 70 80
golf335 pluto[2172]: | 80 01 00 05 80 03 00 01 80 02 00 02 80 04 00 02
golf335 pluto[2172]: | 0a 00 00 84 47 af 54 0d 82 38 a5 34 d5 15 f2 17
golf335 pluto[2172]: | b9 55 ca ed 85 00 c5 eb 92 2d 9e 19 b1 5f e9 a5
golf335 pluto[2172]: | 83 9c b6 5c 33 d1 d6 18 4d 75 aa 3e 46 09 5e 48
golf335 pluto[2172]: | 31 2b da c0 44 44 9b 4c 9f 8f 95 87 62 30 2b 74
golf335 pluto[2172]: | e8 34 88 5c aa 3b 55 b9 16 0d f6 54 76 cd 33 a0
golf335 pluto[2172]: | b4 da 2b 23 04 f4 ce d3 a7 de 27 12 1c b6 94 27
golf335 pluto[2172]: | 00 8a 51 d9 19 e8 79 8b 18 b5 be 99 0c f1 b7 e8
golf335 pluto[2172]: | 74 e0 5f ff 0a 96 99 53 19 6c a3 26 a3 f2 34 c0
golf335 pluto[2172]: | b6 de 6f 47 05 00 00 14 38 4d d8 c8 13 83 4d b8
golf335 pluto[2172]: | 96 24 24 12 a8 36 d7 3f 08 00 00 0c 01 00 00 00
golf335 pluto[2172]: | 55 19 8f d8 0d 00 00 18 03 ef aa 94 10 f5 04 ba
golf335 pluto[2172]: | b7 61 8c 4f 23 28 25 2b b0 ad fe 40 00 00 00 14
golf335 pluto[2172]: | af ca d7 13 68 a1 f1 c9 6b 86 96 fc 77 57 01 00
golf335 pluto[2172]: | inserting event EVENT_RETRANSMIT, timeout in 10 seconds for #3
golf335 pluto[2172]: "golf335" #3: STATE_AGGR_R1: sent AR1, expecting AI2
golf335 pluto[2172]: | modecfg pull: noquirk policy:push not-client
golf335 pluto[2172]: | phase 1 is done, looking for phase 1 to unpend
golf335 pluto[2172]: | complete state transition with STF_INLINE
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 10 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *received 52 bytes from 95.XX.XX.201:500 on eth0 (port=500)
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 08 10 04 00 00 00 00 00 00 00 00 34 00 00 00 18
golf335 pluto[2172]: | b4 2a 80 82 d4 a5 01 57 de b6 84 0f 88 57 02 21
golf335 pluto[2172]: | f6 cc f6 be
golf335 pluto[2172]: | parse ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_HASH
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_AGGR
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 00 00 00 00
golf335 pluto[2172]: | length: 52
golf335 pluto[2172]: | processing packet with exchange type=ISAKMP_XCHG_AGGR (4)
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid 00000000 vs 00000000
golf335 pluto[2172]: | state object #3 found, in STATE_AGGR_R1
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: "golf335" #3: packet rejected: should have been encrypted
golf335 pluto[2172]: "golf335" #3: sending notification INVALID_FLAGS to 95.XX.XX.201:500
golf335 pluto[2172]: | emit ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_N
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_INFO
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 03 ab 30 1e
golf335 pluto[2172]: | *emit ISAKMP Notification Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | DOI: ISAKMP_DOI_IPSEC
golf335 pluto[2172]: | protocol ID: 1
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | Notify Message Type: INVALID_FLAGS
golf335 pluto[2172]: | emitting length of ISAKMP Notification Payload: 12
golf335 pluto[2172]: | emitting length of ISAKMP Message: 40
golf335 pluto[2172]: | sending 40 bytes for notification packet through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 0b 10 05 00 03 ab 30 1e 00 00 00 28 00 00 00 0c
golf335 pluto[2172]: | 00 00 00 01 01 00 00 08
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 10 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *received 84 bytes from 95.XX.XX.201:500 on eth0 (port=500)
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 08 10 05 01 c2 0a fc c1 00 00 00 54 ea 53 48 4d
golf335 pluto[2172]: | 28 3b 14 f1 ec 17 1e 22 da a0 92 00 32 50 86 78
golf335 pluto[2172]: | d5 75 95 e7 c2 7e 9d df d1 3a 8a e2 2d 34 40 de
golf335 pluto[2172]: | 64 a6 e3 81 af d3 b0 c8 55 ab ee 53 2c 97 59 46
golf335 pluto[2172]: | e3 82 49 f6
golf335 pluto[2172]: | parse ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_HASH
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_INFO
golf335 pluto[2172]: | flags: ISAKMP_FLAG_ENCRYPTION
golf335 pluto[2172]: | message ID: c2 0a fc c1
golf335 pluto[2172]: | length: 84
golf335 pluto[2172]: | processing packet with exchange type=ISAKMP_XCHG_INFO (5)
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid 00000000 vs 00000000/00000000
golf335 pluto[2172]: | p15 state object #3 found, in STATE_AGGR_R1
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: | last Phase 1 IV:
golf335 pluto[2172]: | current Phase 1 IV: a6 97 56 7d 5d a6 1e a1 8c 9c b0 60 04 ad d2 98
golf335 pluto[2172]: | a8 68 31 f0
golf335 pluto[2172]: | computed Phase 2 IV:
golf335 pluto[2172]: | 0a 68 40 48 88 f3 a4 a1 2b 13 7d 0b fb ff b0 37
golf335 pluto[2172]: | c5 1d 55 a7
golf335 pluto[2172]: | received encrypted packet from 95.XX.XX.201:500
golf335 pluto[2172]: | decrypting 56 bytes using algorithm OAKLEY_3DES_CBC
golf335 pluto[2172]: | decrypted:
golf335 pluto[2172]: | cd 34 3c 82 b3 e1 64 2b 26 bd f8 67 90 23 fe b2
golf335 pluto[2172]: | ed 0b e8 2d 18 5b 5f 2d 00 00 00 1c 00 00 00 01
golf335 pluto[2172]: | 01 10 60 02 e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03
golf335 pluto[2172]: | 3f 22 b9 be 1a da 4a 03
golf335 pluto[2172]: | next IV: 2c 97 59 46 e3 82 49 f6
golf335 pluto[2172]: | np=8 and sd=0x4a2e30
golf335 pluto[2172]: "golf335" #3: next payload type of ISAKMP Hash Payload has an unknown value: 205
golf335 pluto[2172]: "golf335" #3: malformed payload in packet
golf335 pluto[2172]: | payload malformed after IV
golf335 pluto[2172]: | a6 97 56 7d 5d a6 1e a1 8c 9c b0 60 04 ad d2 98
golf335 pluto[2172]: | a8 68 31 f0
golf335 pluto[2172]: "golf335" #3: sending notification PAYLOAD_MALFORMED to 95.XX.XX.201:500
golf335 pluto[2172]: | emit ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_N
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_INFO
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 6d c1 31 e5
golf335 pluto[2172]: | *emit ISAKMP Notification Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | DOI: ISAKMP_DOI_IPSEC
golf335 pluto[2172]: | protocol ID: 1
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | Notify Message Type: PAYLOAD_MALFORMED
golf335 pluto[2172]: | emitting length of ISAKMP Notification Payload: 12
golf335 pluto[2172]: | emitting length of ISAKMP Message: 40
golf335 pluto[2172]: | sending 40 bytes for notification packet through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 0b 10 05 00 6d c1 31 e5 00 00 00 28 00 00 00 0c
golf335 pluto[2172]: | 00 00 00 01 01 00 00 10
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 10 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *received 156 bytes from 95.XX.XX.201:500 on eth0 (port=500)
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 08 10 20 01 e0 89 f5 b7 00 00 00 9c 79 fd 77 5f
golf335 pluto[2172]: | 72 f7 74 b1 62 56 bd 7b 69 39 5a f3 98 64 d8 78
golf335 pluto[2172]: | cc fd a9 0b 36 a6 7e 02 4b 74 8a 4d 52 f3 c9 7d
golf335 pluto[2172]: | 98 c1 a9 67 06 4f 96 4b 8b b8 24 6c 9f 00 69 98
golf335 pluto[2172]: | 57 de 6f 9e b6 08 c6 76 cd 55 a4 cf a4 e9 c7 b1
golf335 pluto[2172]: | 27 b0 10 9b 15 88 f8 ec 8b e2 f9 c6 a3 4d 18 4c
golf335 pluto[2172]: | 2b 14 63 55 b9 69 aa 47 6d cd b6 10 96 c1 6e 0f
golf335 pluto[2172]: | 6e 55 37 9a b9 df 71 64 d6 69 0e a2 a0 9a 05 05
golf335 pluto[2172]: | 6a 91 45 32 2b 95 70 bf 3b c0 28 86
golf335 pluto[2172]: | parse ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_HASH
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_QUICK
golf335 pluto[2172]: | flags: ISAKMP_FLAG_ENCRYPTION
golf335 pluto[2172]: | message ID: e0 89 f5 b7
golf335 pluto[2172]: | length: 156
golf335 pluto[2172]: | processing packet with exchange type=ISAKMP_XCHG_QUICK (32)
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid e089f5b7 vs 00000000
golf335 pluto[2172]: | state object not found
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid 00000000 vs 00000000
golf335 pluto[2172]: | state object #3 found, in STATE_AGGR_R1
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: "golf335" #3: Quick Mode message is unacceptable because it is for an incomplete ISAKMP SA
golf335 pluto[2172]: | payload malformed after IV
golf335 pluto[2172]: | a6 97 56 7d 5d a6 1e a1 8c 9c b0 60 04 ad d2 98
golf335 pluto[2172]: | a8 68 31 f0
golf335 pluto[2172]: "golf335" #3: sending notification PAYLOAD_MALFORMED to 95.XX.XX.201:500
golf335 pluto[2172]: | emit ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_N
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_INFO
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: d5 10 15 58
golf335 pluto[2172]: | *emit ISAKMP Notification Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | DOI: ISAKMP_DOI_IPSEC
golf335 pluto[2172]: | protocol ID: 1
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | Notify Message Type: PAYLOAD_MALFORMED
golf335 pluto[2172]: | emitting length of ISAKMP Notification Payload: 12
golf335 pluto[2172]: | emitting length of ISAKMP Message: 40
golf335 pluto[2172]: | sending 40 bytes for notification packet through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 0b 10 05 00 d5 10 15 58 00 00 00 28 00 00 00 0c
golf335 pluto[2172]: | 00 00 00 01 01 00 00 10
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 9 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *time to handle event
golf335 pluto[2172]: | handling event EVENT_RETRANSMIT
golf335 pluto[2172]: | event after this is EVENT_PENDING_PHASE2 in 97 seconds
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: | handling event EVENT_RETRANSMIT for 95.XX.XX.201 "golf335" #3
golf335 pluto[2172]: | sending 288 bytes for EVENT_RETRANSMIT through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 01 10 04 00 00 00 00 00 00 00 01 20 04 00 00 34
golf335 pluto[2172]: | 00 00 00 01 00 00 00 01 00 00 00 28 01 01 00 01
golf335 pluto[2172]: | 00 00 00 20 01 01 00 00 80 0b 00 01 80 0c 70 80
golf335 pluto[2172]: | 80 01 00 05 80 03 00 01 80 02 00 02 80 04 00 02
golf335 pluto[2172]: | 0a 00 00 84 47 af 54 0d 82 38 a5 34 d5 15 f2 17
golf335 pluto[2172]: | b9 55 ca ed 85 00 c5 eb 92 2d 9e 19 b1 5f e9 a5
golf335 pluto[2172]: | 83 9c b6 5c 33 d1 d6 18 4d 75 aa 3e 46 09 5e 48
golf335 pluto[2172]: | 31 2b da c0 44 44 9b 4c 9f 8f 95 87 62 30 2b 74
golf335 pluto[2172]: | e8 34 88 5c aa 3b 55 b9 16 0d f6 54 76 cd 33 a0
golf335 pluto[2172]: | b4 da 2b 23 04 f4 ce d3 a7 de 27 12 1c b6 94 27
golf335 pluto[2172]: | 00 8a 51 d9 19 e8 79 8b 18 b5 be 99 0c f1 b7 e8
golf335 pluto[2172]: | 74 e0 5f ff 0a 96 99 53 19 6c a3 26 a3 f2 34 c0
golf335 pluto[2172]: | b6 de 6f 47 05 00 00 14 38 4d d8 c8 13 83 4d b8
golf335 pluto[2172]: | 96 24 24 12 a8 36 d7 3f 08 00 00 0c 01 00 00 00
golf335 pluto[2172]: | 55 19 8f d8 0d 00 00 18 03 ef aa 94 10 f5 04 ba
golf335 pluto[2172]: | b7 61 8c 4f 23 28 25 2b b0 ad fe 40 00 00 00 14
golf335 pluto[2172]: | af ca d7 13 68 a1 f1 c9 6b 86 96 fc 77 57 01 00
golf335 pluto[2172]: | inserting event EVENT_RETRANSMIT, timeout in 20 seconds for #3
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 20 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *received 52 bytes from 95.XX.XX.201:500 on eth0 (port=500)
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 08 10 04 00 00 00 00 00 00 00 00 34 00 00 00 18
golf335 pluto[2172]: | b4 2a 80 82 d4 a5 01 57 de b6 84 0f 88 57 02 21
golf335 pluto[2172]: | f6 cc f6 be
golf335 pluto[2172]: | parse ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_HASH
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_AGGR
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 00 00 00 00
golf335 pluto[2172]: | length: 52
golf335 pluto[2172]: | processing packet with exchange type=ISAKMP_XCHG_AGGR (4)
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid 00000000 vs 00000000
golf335 pluto[2172]: | state object #3 found, in STATE_AGGR_R1
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: "golf335" #3: packet rejected: should have been encrypted
golf335 pluto[2172]: "golf335" #3: sending notification INVALID_FLAGS to 95.XX.XX.201:500
golf335 pluto[2172]: | emit ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_N
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_INFO
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 3a 0e 22 20
golf335 pluto[2172]: | *emit ISAKMP Notification Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | DOI: ISAKMP_DOI_IPSEC
golf335 pluto[2172]: | protocol ID: 1
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | Notify Message Type: INVALID_FLAGS
golf335 pluto[2172]: | emitting length of ISAKMP Notification Payload: 12
golf335 pluto[2172]: | emitting length of ISAKMP Message: 40
golf335 pluto[2172]: | sending 40 bytes for notification packet through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 0b 10 05 00 3a 0e 22 20 00 00 00 28 00 00 00 0c
golf335 pluto[2172]: | 00 00 00 01 01 00 00 08
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 20 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *received 156 bytes from 95.XX.XX.201:500 on eth0 (port=500)
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 08 10 20 01 e0 89 f5 b7 00 00 00 9c 79 fd 77 5f
golf335 pluto[2172]: | 72 f7 74 b1 62 56 bd 7b 69 39 5a f3 98 64 d8 78
golf335 pluto[2172]: | cc fd a9 0b 36 a6 7e 02 4b 74 8a 4d 52 f3 c9 7d
golf335 pluto[2172]: | 98 c1 a9 67 06 4f 96 4b 8b b8 24 6c 9f 00 69 98
golf335 pluto[2172]: | 57 de 6f 9e b6 08 c6 76 cd 55 a4 cf a4 e9 c7 b1
golf335 pluto[2172]: | 27 b0 10 9b 15 88 f8 ec 8b e2 f9 c6 a3 4d 18 4c
golf335 pluto[2172]: | 2b 14 63 55 b9 69 aa 47 6d cd b6 10 96 c1 6e 0f
golf335 pluto[2172]: | 6e 55 37 9a b9 df 71 64 d6 69 0e a2 a0 9a 05 05
golf335 pluto[2172]: | 6a 91 45 32 2b 95 70 bf 3b c0 28 86
golf335 pluto[2172]: | parse ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_HASH
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_QUICK
golf335 pluto[2172]: | flags: ISAKMP_FLAG_ENCRYPTION
golf335 pluto[2172]: | message ID: e0 89 f5 b7
golf335 pluto[2172]: | length: 156
golf335 pluto[2172]: | processing packet with exchange type=ISAKMP_XCHG_QUICK (32)
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid e089f5b7 vs 00000000
golf335 pluto[2172]: | state object not found
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid 00000000 vs 00000000
golf335 pluto[2172]: | state object #3 found, in STATE_AGGR_R1
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: "golf335" #3: Quick Mode message is unacceptable because it is for an incomplete ISAKMP SA
golf335 pluto[2172]: | payload malformed after IV
golf335 pluto[2172]: | a6 97 56 7d 5d a6 1e a1 8c 9c b0 60 04 ad d2 98
golf335 pluto[2172]: | a8 68 31 f0
golf335 pluto[2172]: "golf335" #3: sending notification PAYLOAD_MALFORMED to 95.XX.XX.201:500
golf335 pluto[2172]: | emit ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_N
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_INFO
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: b0 0a 8d 5b
golf335 pluto[2172]: | *emit ISAKMP Notification Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | DOI: ISAKMP_DOI_IPSEC
golf335 pluto[2172]: | protocol ID: 1
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | Notify Message Type: PAYLOAD_MALFORMED
golf335 pluto[2172]: | emitting length of ISAKMP Notification Payload: 12
golf335 pluto[2172]: | emitting length of ISAKMP Message: 40
golf335 pluto[2172]: | sending 40 bytes for notification packet through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 0b 10 05 00 b0 0a 8d 5b 00 00 00 28 00 00 00 0c
golf335 pluto[2172]: | 00 00 00 01 01 00 00 10
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 19 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *received 156 bytes from 95.XX.XX.201:500 on eth0 (port=500)
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 08 10 20 01 e0 89 f5 b7 00 00 00 9c 79 fd 77 5f
golf335 pluto[2172]: | 72 f7 74 b1 62 56 bd 7b 69 39 5a f3 98 64 d8 78
golf335 pluto[2172]: | cc fd a9 0b 36 a6 7e 02 4b 74 8a 4d 52 f3 c9 7d
golf335 pluto[2172]: | 98 c1 a9 67 06 4f 96 4b 8b b8 24 6c 9f 00 69 98
golf335 pluto[2172]: | 57 de 6f 9e b6 08 c6 76 cd 55 a4 cf a4 e9 c7 b1
golf335 pluto[2172]: | 27 b0 10 9b 15 88 f8 ec 8b e2 f9 c6 a3 4d 18 4c
golf335 pluto[2172]: | 2b 14 63 55 b9 69 aa 47 6d cd b6 10 96 c1 6e 0f
golf335 pluto[2172]: | 6e 55 37 9a b9 df 71 64 d6 69 0e a2 a0 9a 05 05
golf335 pluto[2172]: | 6a 91 45 32 2b 95 70 bf 3b c0 28 86
golf335 pluto[2172]: | parse ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_HASH
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_QUICK
golf335 pluto[2172]: | flags: ISAKMP_FLAG_ENCRYPTION
golf335 pluto[2172]: | message ID: e0 89 f5 b7
golf335 pluto[2172]: | length: 156
golf335 pluto[2172]: | processing packet with exchange type=ISAKMP_XCHG_QUICK (32)
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid e089f5b7 vs 00000000
golf335 pluto[2172]: | state object not found
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid 00000000 vs 00000000
golf335 pluto[2172]: | state object #3 found, in STATE_AGGR_R1
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: "golf335" #3: Quick Mode message is unacceptable because it is for an incomplete ISAKMP SA
golf335 pluto[2172]: | payload malformed after IV
golf335 pluto[2172]: | a6 97 56 7d 5d a6 1e a1 8c 9c b0 60 04 ad d2 98
golf335 pluto[2172]: | a8 68 31 f0
golf335 pluto[2172]: "golf335" #3: sending notification PAYLOAD_MALFORMED to 95.XX.XX.201:500
golf335 pluto[2172]: | emit ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_N
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_INFO
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 2e 5f d9 e8
golf335 pluto[2172]: | *emit ISAKMP Notification Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | DOI: ISAKMP_DOI_IPSEC
golf335 pluto[2172]: | protocol ID: 1
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | Notify Message Type: PAYLOAD_MALFORMED
golf335 pluto[2172]: | emitting length of ISAKMP Notification Payload: 12
golf335 pluto[2172]: | emitting length of ISAKMP Message: 40
golf335 pluto[2172]: | sending 40 bytes for notification packet through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 0b 10 05 00 2e 5f d9 e8 00 00 00 28 00 00 00 0c
golf335 pluto[2172]: | 00 00 00 01 01 00 00 10
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 9 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *time to handle event
golf335 pluto[2172]: | handling event EVENT_RETRANSMIT
golf335 pluto[2172]: | event after this is EVENT_PENDING_PHASE2 in 77 seconds
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: | handling event EVENT_RETRANSMIT for 95.XX.XX.201 "golf335" #3
golf335 pluto[2172]: | sending 288 bytes for EVENT_RETRANSMIT through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 01 10 04 00 00 00 00 00 00 00 01 20 04 00 00 34
golf335 pluto[2172]: | 00 00 00 01 00 00 00 01 00 00 00 28 01 01 00 01
golf335 pluto[2172]: | 00 00 00 20 01 01 00 00 80 0b 00 01 80 0c 70 80
golf335 pluto[2172]: | 80 01 00 05 80 03 00 01 80 02 00 02 80 04 00 02
golf335 pluto[2172]: | 0a 00 00 84 47 af 54 0d 82 38 a5 34 d5 15 f2 17
golf335 pluto[2172]: | b9 55 ca ed 85 00 c5 eb 92 2d 9e 19 b1 5f e9 a5
golf335 pluto[2172]: | 83 9c b6 5c 33 d1 d6 18 4d 75 aa 3e 46 09 5e 48
golf335 pluto[2172]: | 31 2b da c0 44 44 9b 4c 9f 8f 95 87 62 30 2b 74
golf335 pluto[2172]: | e8 34 88 5c aa 3b 55 b9 16 0d f6 54 76 cd 33 a0
golf335 pluto[2172]: | b4 da 2b 23 04 f4 ce d3 a7 de 27 12 1c b6 94 27
golf335 pluto[2172]: | 00 8a 51 d9 19 e8 79 8b 18 b5 be 99 0c f1 b7 e8
golf335 pluto[2172]: | 74 e0 5f ff 0a 96 99 53 19 6c a3 26 a3 f2 34 c0
golf335 pluto[2172]: | b6 de 6f 47 05 00 00 14 38 4d d8 c8 13 83 4d b8
golf335 pluto[2172]: | 96 24 24 12 a8 36 d7 3f 08 00 00 0c 01 00 00 00
golf335 pluto[2172]: | 55 19 8f d8 0d 00 00 18 03 ef aa 94 10 f5 04 ba
golf335 pluto[2172]: | b7 61 8c 4f 23 28 25 2b b0 ad fe 40 00 00 00 14
golf335 pluto[2172]: | af ca d7 13 68 a1 f1 c9 6b 86 96 fc 77 57 01 00
golf335 pluto[2172]: | inserting event EVENT_RETRANSMIT, timeout in 40 seconds for #3
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 40 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *received 52 bytes from 95.XX.XX.201:500 on eth0 (port=500)
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 08 10 04 00 00 00 00 00 00 00 00 34 00 00 00 18
golf335 pluto[2172]: | b4 2a 80 82 d4 a5 01 57 de b6 84 0f 88 57 02 21
golf335 pluto[2172]: | f6 cc f6 be
golf335 pluto[2172]: | parse ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_HASH
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_AGGR
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 00 00 00 00
golf335 pluto[2172]: | length: 52
golf335 pluto[2172]: | processing packet with exchange type=ISAKMP_XCHG_AGGR (4)
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | peer and cookies match on #3, provided msgid 00000000 vs 00000000
golf335 pluto[2172]: | state object #3 found, in STATE_AGGR_R1
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: "golf335" #3: packet rejected: should have been encrypted
golf335 pluto[2172]: "golf335" #3: sending notification INVALID_FLAGS to 95.XX.XX.201:500
golf335 pluto[2172]: | emit ISAKMP Message:
golf335 pluto[2172]: | initiator cookie:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | responder cookie:
golf335 pluto[2172]: | a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_N
golf335 pluto[2172]: | ISAKMP version: ISAKMP Version 1.0
golf335 pluto[2172]: | exchange type: ISAKMP_XCHG_INFO
golf335 pluto[2172]: | flags: none
golf335 pluto[2172]: | message ID: 03 23 4e 6f
golf335 pluto[2172]: | *emit ISAKMP Notification Payload:
golf335 pluto[2172]: | next payload type: ISAKMP_NEXT_NONE
golf335 pluto[2172]: | DOI: ISAKMP_DOI_IPSEC
golf335 pluto[2172]: | protocol ID: 1
golf335 pluto[2172]: | SPI size: 0
golf335 pluto[2172]: | Notify Message Type: INVALID_FLAGS
golf335 pluto[2172]: | emitting length of ISAKMP Notification Payload: 12
golf335 pluto[2172]: | emitting length of ISAKMP Message: 40
golf335 pluto[2172]: | sending 40 bytes for notification packet through eth0:500 to 95.XX.XX.201:500:
golf335 pluto[2172]: | e5 ce 8a 2e 2f 00 b3 21 a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | 0b 10 05 00 03 23 4e 6f 00 00 00 28 00 00 00 0c
golf335 pluto[2172]: | 00 00 00 01 01 00 00 08
golf335 pluto[2172]: | next event EVENT_RETRANSMIT in 40 seconds for #3
golf335 pluto[2172]: |
golf335 pluto[2172]: | *time to handle event
golf335 pluto[2172]: | handling event EVENT_RETRANSMIT
golf335 pluto[2172]: | event after this is EVENT_PENDING_PHASE2 in 37 seconds
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: | handling event EVENT_RETRANSMIT for 95.XX.XX.201 "golf335" #3
golf335 pluto[2172]: "golf335" #3: max number of retransmissions (2) reached STATE_AGGR_R1
golf335 pluto[2172]: | deleting state #3
golf335 pluto[2172]: | processing connection golf335
golf335 pluto[2172]: | ICOOKIE: e5 ce 8a 2e 2f 00 b3 21
golf335 pluto[2172]: | RCOOKIE: a6 b1 77 03 3f 22 b9 be
golf335 pluto[2172]: | peer: 5f d0 2a c9
golf335 pluto[2172]: | state hash entry 25
golf335 pluto[2172]: | next event EVENT_PENDING_PHASE2 in 37 seconds
golf335 pluto[2172]: |
golf335 pluto[2172]: | *time to handle event
golf335 pluto[2172]: | handling event EVENT_PENDING_PHASE2
golf335 pluto[2172]: | event after this is EVENT_REINIT_SECRET in 80 seconds
golf335 pluto[2172]: | inserting event EVENT_PENDING_PHASE2, timeout in 120 seconds
golf335 pluto[2172]: | pending review: connection "golf335" was not up, skipped
golf335 pluto[2172]: | next event EVENT_REINIT_SECRET in 80 seconds
golf335 pluto[2172]: |
golf335 pluto[2172]: | *time to handle event
golf335 pluto[2172]: | handling event EVENT_REINIT_SECRET
golf335 pluto[2172]: | event after this is EVENT_PENDING_PHASE2 in 40 seconds
golf335 pluto[2172]: | event EVENT_REINIT_SECRET handled
golf335 pluto[2172]: | inserting event EVENT_REINIT_SECRET, timeout in 3600 seconds
golf335 pluto[2172]: | next event EVENT_PENDING_PHASE2 in 40 seconds
golf335 CRON[12318]: pam_unix(cron:session): session opened for user root by (uid=0)
golf335 poplock DB cleanup[12319]: started
golf335 poplock DB cleanup[12319]: completed
golf335 CRON[12318]: pam_unix(cron:session): session closed for user root
golf335 pluto[2172]: |
golf335 pluto[2172]: | *time to handle event
golf335 pluto[2172]: | handling event EVENT_PENDING_PHASE2
golf335 pluto[2172]: | event after this is EVENT_REINIT_SECRET in 3560 seconds
golf335 pluto[2172]: | inserting event EVENT_PENDING_PHASE2, timeout in 120 seconds
golf335 pluto[2172]: | pending review: connection "golf335" was not up, skipped
golf335 pluto[2172]: | next event EVENT_PENDING_PHASE2 in 120 seconds
VIelleicht kommt jemand noch drauf, an was es jetzt noch fehlt?
Gruß
AzubiLE