Install own SSL certificate on HP ScanJet Pro N4000 snw1 does not work
I have a brand new HP ScanJet Pro N4000 snw1, firmware 0.80.
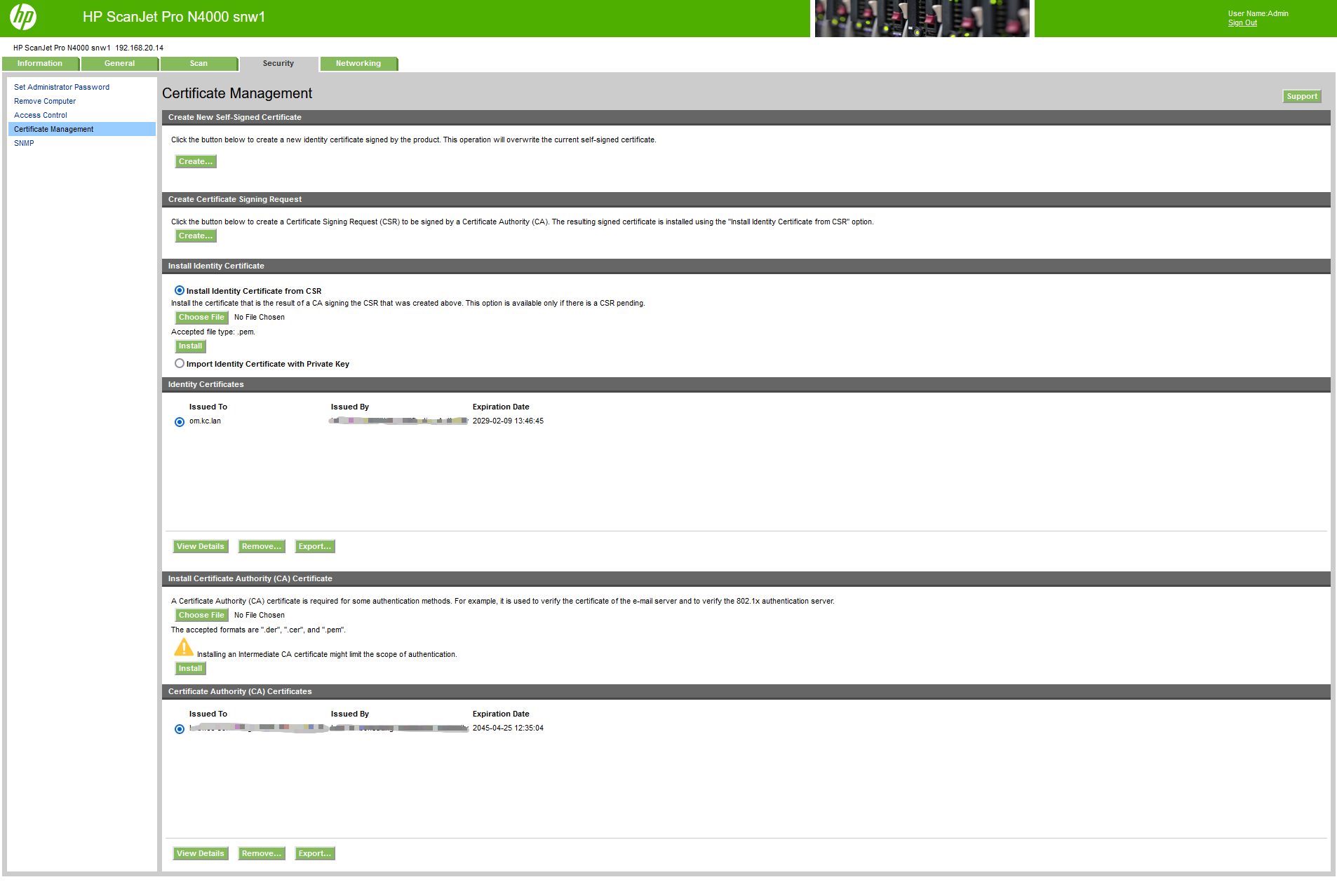
I would like to install a self created SSL certificate and I can't.
Variant 1: import p12 certificate, containing a private key works. I see a certificate on the certificate management site, but the certificate is not used for the website.
Variant 2: create the CSR on the scanner's website and create a cert from it. I can create a CSR, but if I try to import the certificate made from it, I always get the message "password incorrect". Though, there is no any password: after the creation of CSR you're just importing the cert without private key.
Does somebody have an idea, what is wrong?
I would like to install a self created SSL certificate and I can't.
Variant 1: import p12 certificate, containing a private key works. I see a certificate on the certificate management site, but the certificate is not used for the website.
Variant 2: create the CSR on the scanner's website and create a cert from it. I can create a CSR, but if I try to import the certificate made from it, I always get the message "password incorrect". Though, there is no any password: after the creation of CSR you're just importing the cert without private key.
Does somebody have an idea, what is wrong?
Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 53993779015
Url: https://administrator.de/en/install-own-ssl-certificate-on-hp-scanjet-pro-n4000-snw1-does-not-work-53993779015.html
Ausgedruckt am: 30.01.2025 um 08:01 Uhr
25 Kommentare
Neuester Kommentar
Cross post
Wich encryption standard has been used to create the PFX/P12 Container? Try to create the container by using the legacy DES format or convert it by using openssl.
Are you really sure that the certificate should be used by the scanners management page? I think this is only used for authentication to remote servers and server certificate validation.
Variant 1: import p12 certificate, containing a private key works. I see a certificate on the certificate management site, but the certificate is not used for the website.
Assign the cert to be used by the interface. Check the options on the management interface.Wich encryption standard has been used to create the PFX/P12 Container? Try to create the container by using the legacy DES format or convert it by using openssl.
Are you really sure that the certificate should be used by the scanners management page? I think this is only used for authentication to remote servers and server certificate validation.
No that is not what i mean, i mean the encryption scheme by the P12 container, if it as legacy or modern one with aes256 encryption!
but I don't think, it is an issue here: the cert was read by the website...
That it can read the container does not mean it's correctly decoded.I think, it was a modern one
Show us the output of ...openssl pkcs12 -in hp-scanner.p12 -info -nooutP12 zertifikat auf aktuelle Linux-Server kann auf IIS nicht importiert werden (Angeblich falsches Kennwort)
OK, then show us all your settings you have set (screenshots).
What does the HP support say?
What does the HP support say?
OK let's wait. Seams to be a bug then if it does not work when you reset the scanner to default settings.
Have you cleared your Browser cache? => use private mode as best practice
Did you really call the page by it's common name afterwards?
Have you cleared your Browser cache? => use private mode as best practice
Did you really call the page by it's common name afterwards?
Did your certs contain the necessary extensions for a webserver certificate? "keyAgreement, keyEncipherment, digitalSignature" and extendedKeyUsage "serverAuth".
Sorry, but wee need to pull everything out of your nose, because we can't see that much information from your post, but wait ... OK it's friday, so nothing unusual 💩
Sorry, but wee need to pull everything out of your nose, because we can't see that much information from your post, but wait ... OK it's friday, so nothing unusual 💩
Please post the complete settings of the cert. Is the common name also listet as SubjectAlternativeName ?
subjectAltName = DNS:demo.tld
You are missing the CN as SAN entry.
I suggest using a GUI Tool like this:
XCA
XCA
Zitat von @sashaak:
Update from HP support: it is not possible to install own cert for this device type.
As I suspected in first place ... Thanks for the update.Update from HP support: it is not possible to install own cert for this device type.