Cisco IPsec VPN with Mikrotik or FritzBox

Table of contents
The following tutorial is a quick overview how a site-to-site VPN access using the IPsec protocol can be realized with a Cisco IOS or IOS-XE router and popular, mass production routers like Mikrotik and/or AVM FritzBox.
One characteristic feature used here for router protection is the Cisco onboard, statefull Zone Based Firewall or ZFW.
The Cisco router additionally provides an L2TP client VPN dialin access, which makes it possible to access the network with all standard, onboard L2TP VPN clients embedded in mobile devices with Windows, Apple MacOS, Apple iOS and Android as well as Linux.
The basic layer 3 overview of the example setup is shown in the following picture.
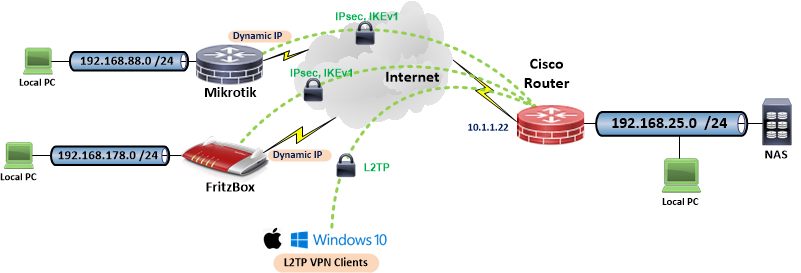
In this design the Cisco router acts as an IPsec responder (server) so that VPN site-to-site client routers (initiators) and mobile L2TP VPN clients can either connect with dynamic IP addresses, ds-lite addresses or with a static IP address. The Cisco configuration in the next chapter also shows an additional IPsec connection with static peer IP adresses. (Config example, not shown in the above picture!).
Due to the fact that Cisco‘s IOS configuration syntax is universal over all platforms, this configuration can be used for other router and switch models as well.
Enhanced ACL protection for CLI access and authorization secures login access on virtual interfaces as well as the serial console.
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug datetime localtime
service timestamps log datetime localtime show-timezone year
!
hostname cisco
!
security authentication failure rate 3 log
enable algorithm-type scrypt secret <password>
!
aaa new-model
aaa authentication login default local
aaa authentication ppp L2TP_AUTH local
aaa authorization console
aaa authorization exec default local
!
clock timezone CET 1 0
clock summer-time CEST recurring last Sun Mar 2:00 last Sun Oct 3:00
!
no ip source-route
no ip gratuitous-arps
!
ip dhcp binding cleanup interval 180
ip dhcp excluded-address 192.168.25.1 192.168.25.29
ip dhcp excluded-address 192.168.25.200 192.168.25.254
!
ip dhcp pool Local_LAN
network 192.168.25.0 255.255.255.0
default-router 192.168.25.1
domain-name mydomain.internal
dns-server 192.168.25.1
!
!
ip domain lookup source-interface GigabitEthernet 4
ip domain name mydomain.internal
ip name-server 9.9.9.9
login block-for 120 attempts 3 within 15
login quiet-mode access-class 23
login on-failure log
login on-success log
!
vpdn enable
!
vpdn-group L2TP
accept-dialin
protocol l2tp
virtual-template 1
no l2tp tunnel authentication
!
!
username <admin> privilege 15 algorithm-type scrypt secret <password>
!
username <l2tp_username> privilege 0 password <password>
!
lldp run
no cdp run
!
ip tcp path-mtu-discovery
!
class-map type inspect match-all ALLOW_IN
match access-group name ALLOWv4
!
class-map type inspect match-any ROUTER
match protocol tcp
match protocol udp
match protocol icmp
!
class-map type inspect match-all VPN
match access-group name VPN_NET
!
class-map type inspect match-any LOCAL
match protocol dns
match protocol http
match protocol https
match protocol pop3s
match protocol pop3
match protocol imaps
match protocol imap3
match protocol imap
match protocol smtp
match protocol sip
match protocol sip-tls
match protocol rtsp
match protocol ftp
match protocol ftps
match protocol ssh
match protocol ntp
match protocol tcp
match protocol udp
match protocol icmp
!
policy-map type inspect InternetToLocal
description Pass VPN traffic to LAN
class type inspect VPN
inspect
class class-default
drop
!
policy-map type inspect RouterToInternet
description Traffic Router to Internet
class type inspect ROUTER
inspect
class class-default
drop
!
policy-map type inspect LocalToInternet
description Traffic LAN to Internet
class type inspect LOCAL
inspect
class class-default
drop
!
policy-map type inspect InternetToRouter
description Permitted traffic Internet to router
class type inspect ALLOW_IN
pass
class type inspect VPN
inspect
class class-default
drop
!
zone security Internet
zone security Local
!
zone-pair security HomeToInternet source Local destination Internet
service-policy type inspect LocalToInternet
zone-pair security InternetToRouter source Internet destination self
service-policy type inspect InternetToRouter
zone-pair security InternetToLocal source Internet destination Local
service-policy type inspect InternetToLocal
zone-pair security RouterToInternet source self destination Internet
service-policy type inspect RouterToInternet
!
crypto keyring vpntest
pre-shared-key address <site_to_site_peer_ip> key <vpn_password>
pre-shared-key address 0.0.0.0 0.0.0.0 key <vpn_password>
!
crypto isakmp policy 10
encr aes 256
hash sha256
authentication pre-share
group 14
!
crypto isakmp policy 11
encr aes 256
authentication pre-share
group 14
!
crypto isakmp policy 12
encr aes 256
authentication pre-share
group 2
!
crypto isakmp policy 14
encr aes
authentication pre-share
group 2
!
crypto isakmp keepalive 10
crypto isakmp profile S-2-S
description IPsec VPN example static IP
keyring vpntest
match identity address <site_to_site_peer_ip> 255.255.255.255
crypto isakmp profile DYNIP
description VPNs mit dyn. IP
keyring vpntest
match identity address 0.0.0.0
!
crypto ipsec transform-set testset256 esp-aes 256 esp-sha256-hmac
mode tunnel
crypto ipsec transform-set testset256-fritzbox esp-aes 256 esp-sha-hmac
mode tunnel
crypto ipsec transform-set testset128 esp-aes esp-sha-hmac
mode tunnel
!
crypto ipsec transform-set L2TP-1 esp-aes 256 esp-sha-hmac
mode transport
crypto ipsec transform-set L2TP-2 esp-aes esp-sha-hmac
mode transport
!
crypto dynamic-map dynmap 10
description VPN Tunnel, dyn.IP FritzBox
set transform-set testset256-fritzbox
set pfs group2
set isakmp-profile DYNIP
match address FRITZ
!
crypto dynamic-map dynmap 12
description VPN Tunnel, dyn.IP Mikrotik
set transform-set testset256
set pfs group14
set isakmp-profile DYNIP
match address MIKROTIK
!
crypto dynamic-map dynmap 20
set nat demux
set transform-set L2TP-1 L2TP-2
set isakmp-profile DYNIP
!
crypto map vpntest 10 ipsec-isakmp
description VPN Tunnel, example static IP
set peer <site_to_site_peer_ip>
set transform-set testset256
set pfs group14
set isakmp-profile S-2-S
match address SITEtoSITE
!
crypto map vpntest 20 ipsec-isakmp dynamic dynmap
!
!
interface Loopback1
description Looback for L2TP client VPN pool
ip address 192.168.26.1 255.255.255.0
!
interface GigabitEthernet0
description Local LAN
switchport mode access
switchport nonegotiate
no ip address
!
interface GigabitEthernet4
description Internet WAN Port
ip address 10.1.1.22 255.255.255.0
ip nat outside
ip virtual-reassembly in
zone-member security Internet
crypto map vpntest
no lldp transmit
!
interface Virtual-Template1
description L2TP Client VPN Dialin
ip unnumbered Loopback1
zone-member security Local
peer default ip address pool L2TP_POOL
ppp authentication ms-chap-v2 L2TP_AUTH
!
interface Vlan1
description Local LAN IP
ip address 192.168.25.1 255.255.255.0
ip nat inside
zone-member security Local
!
ip local pool L2TP_POOL 192.168.26.200 192.168.26.210
!
no ip http server
no ip http secure-server
ip http authentication local
!
ip dns server
ip nat inside source route-map NONAT interface GigabitEthernet4 overload
ip route 0.0.0.0 0.0.0.0 <gateway_ip>
ip ssh time-out 60
ip ssh authentication-retries 2
ip ssh source-interface Vlan1
ip ssh version 2
!
ip access-list extended ALLOWv4
remark ZFW protocols allowed
permit udp any any eq 1701
permit udp any any eq isakmp
permit udp any any eq non500-isakmp
permit esp any any
!
ip access-list extended FRITZ
remark IPsec FritzBox
permit ip 192.168.25.0 0.0.0.255 192.168.178.0 0.0.0.255
permit ip 192.168.26.0 0.0.0.255 192.168.178.0 0.0.0.255
!
ip access-list extended MIKROTIK
remark IPsec Mikrotik
permit ip 192.168.25.0 0.0.0.255 192.168.88.0 0.0.0.255
permit ip 192.168.26.0 0.0.0.255 192.168.88.0 0.0.0.255
!
ip access-list extended SITEtoSITE
remark Static IP site-2-site VPN
permit ip 192.168.25.0 0.0.0.255 192.168.1.0 0.0.0.255
permit ip 192.168.26.0 0.0.0.255 192.168.1.0 0.0.0.255
!
ip access-list extended NATPOLICY
remark No NAT in VPN tunnel
deny ip 192.168.25.0 0.0.0.255 192.168.0.0 0.0.255.255
deny ip 192.168.26.0 0.0.0.255 192.168.0.0 0.0.255.255
permit ip 192.168.25.0 0.0.0.255 any
permit ip 192.168.26.0 0.0.0.255 any
!
ip access-list extended VPN_NET
remark ZFW pass VPN traffic
permit ip 192.168.88.0 0.0.0.255 192.168.25.0 0.0.0.255
permit ip 192.168.88.0 0.0.0.255 192.168.26.0 0.0.0.255
permit ip 192.168.1.0 0.0.0.255 192.168.25.0 0.0.0.255
permit ip 192.168.1.0 0.0.0.255 192.168.26.0 0.0.0.255
permit ip 192.168.178.0 0.0.0.255 192.168.25.0 0.0.0.255
permit ip 192.168.178.0 0.0.0.255 192.168.26.0 0.0.0.255
!
route-map NONAT permit 10
match ip address NATPOLICY
!
access-list 23 remark CLI Access ACL
access-list 23 permit 192.168.25.0 0.0.0.255
access-list 23 permit 192.168.26.0 0.0.0.255
!
banner exec #
You are connected to line $(line) at router $(hostname)
#
banner motd #
____ __ ___ ____
/\ _`\ __ /'_ `\ /'___`\ /'___\
\ \ \/\_\ /\_\ ____ ___ ___ /\ \L\ \ /\_\ /\ \ /\ \__/
\ \ \/_/_\/\ \ /',__\ /'___\ / __`\ \ \___, \\/_/// /__\ \ _``\
\ \ \L\ \\ \ \/\__, `\/\ \__//\ \L\ \ \/__,/\ \ // /_\ \\ \ \L\ \
\ \____/ \ \_\/\____/\ \____\ \____/ \ \_\/\______/ \ \____/
\/___/ \/_/\/___/ \/____/\/___/ \/_/\/_____/ \/___/
(WAN IP Address (Gigabit 4): 10.1.1.22 /24)
#
!
line vty 0 4
access-class 23 in
transport input telnet ssh
!
ntp source GigabitEthernet4
ntp server de.pool.ntp.org
ntp update-calendar
!
end The corresponding Mikrotik VPN configuration shown here is the customized, out-of-the-box default configuration where eth1 is the firewall protected WAN Port and ports 2 to x are the local LAN, bundled in a bridge to keep the setup as simple as possible. This has to be finetuned if VLANs etc. are used.
Configuration is shown in WinBox screenshots and the classic configuration via export.
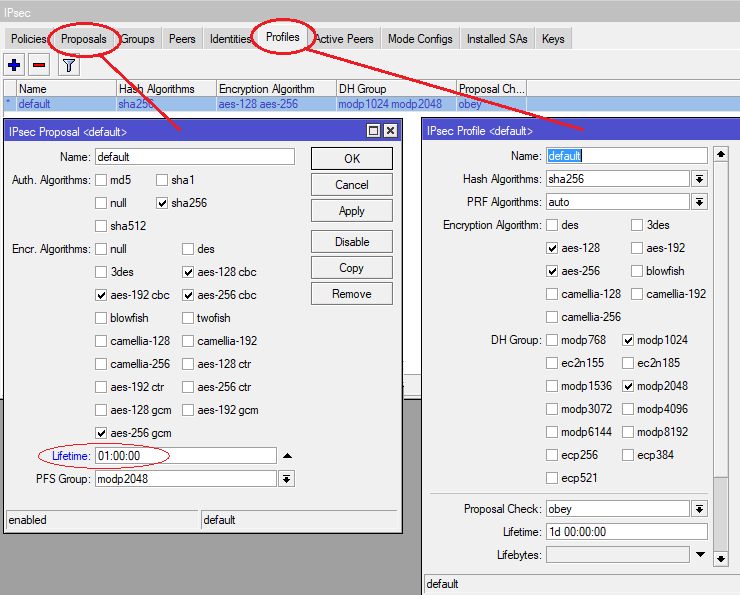
- Old and non secure cipher suites like 3DES etc. should be removed here. In case a stricter negotiation policy is required remove the 128bit and 192bit checkboxes as well as DH 1024. Recommendation is AES256 with SHA256 and DH Group 14 or stronger.
- Cisco is using a P2 lifetime of 1 hour by default which should be set in the Mikrotik settings as well. Allways use consistent lifetimes.
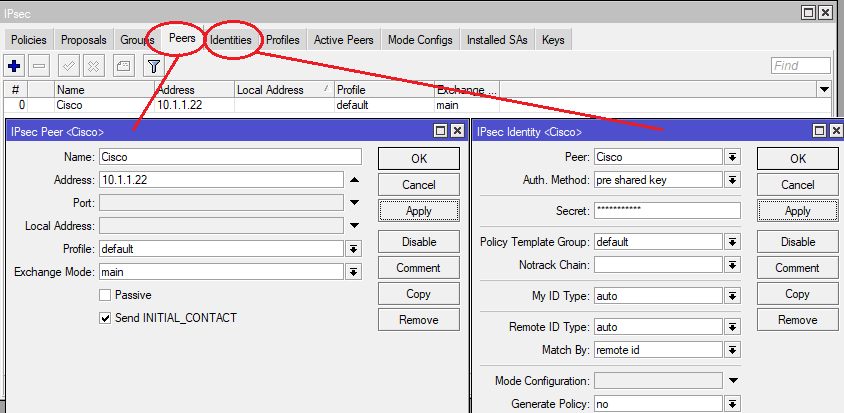
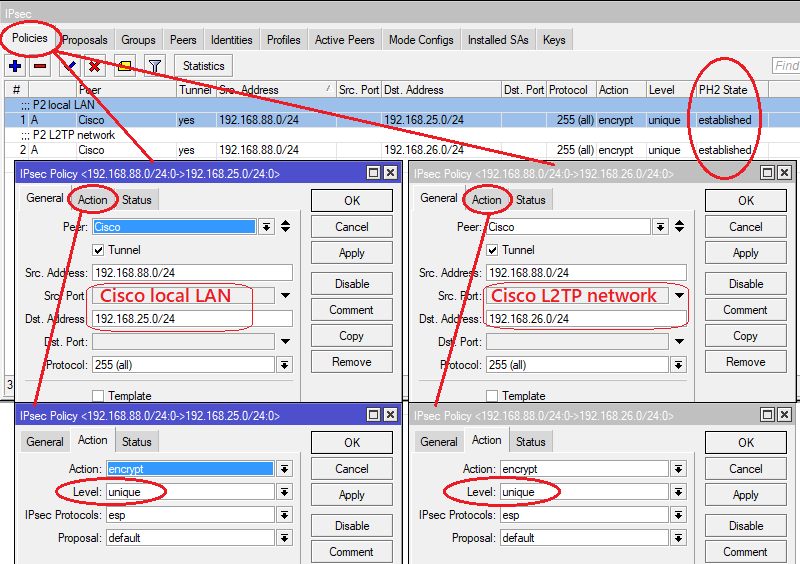
Two SA policies need to be configured here. One for the local LAN (.25.0/24) and one for the separate L2TP client IP (.26.0/24) network on the Cisco site.
That way both LAN and VPN clients on the Cisco site are able to reach the local Mikrotik LAN via VPN.
⚠️ Make sure to set the Level setting in the Action menu to unique !
# dec/14/2022 16:01:23 by RouterOS 7.1.3
#
/interface ethernet
set [ find default-name=ether1 ] comment="WAN Port"
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip ipsec peer
add address=10.1.1.22/32 name=Cisco
/ip ipsec profile
set [ find default=yes ] enc-algorithm=aes-256,aes-128 hash-algorithm=sha256
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=sha256 enc-algorithms=\
aes-256-cbc,aes-256-gcm,aes-192-cbc,aes-128-cbc lifetime=1h pfs-group=modp2048
/ip pool
add name=default-dhcp ranges=192.168.88.100-192.168.88.200
/ip dhcp-server
add address-pool=default-dhcp interface=bridge name=defconf
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
/ip address
add address=192.168.88.1/24 comment="Local LAN" interface=bridge network=192.168.88.0
/ip dhcp-client
add comment=defconf interface=ether1
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf dns-server=192.168.88.1 gateway=192.168.88.1
/ip dns
set allow-remote-requests=yes
/ip dns static
add address=192.168.88.1 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" \
connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment="defconf: accept to local loopback (for CAPsMAN)" \
dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" ipsec-policy=\
in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" ipsec-policy=\
out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment="defconf: accept established,related, untracked" \
connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop all from WAN not DSTNATed" \
connection-nat-state=!dstnat connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" ipsec-policy=out,none \
out-interface-list=WAN
/ip ipsec identity
add peer=Cisco
/ip ipsec policy
add comment="P2 local LAN" dst-address=192.168.25.0/24 level=unique peer=Cisco src-address=\
192.168.88.0/24 tunnel=yes
add comment="P2 L2TP network" dst-address=192.168.26.0/24 level=unique peer=Cisco \
src-address=192.168.88.0/24 tunnel=yes
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" \
connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 \
protocol=udp
add action=accept chain=input comment="defconf: accept DHCPv6-Client prefix delegation." \
dst-port=546 protocol=udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=ipsec-esp
add action=accept chain=input comment="defconf: accept all that matches ipsec policy" \
ipsec-policy=in,ipsec
add action=drop chain=input comment="defconf: drop everything else not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept established,related,untracked" \
connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop packets with bad src ipv6" \
src-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: drop packets with bad dst ipv6" \
dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" hop-limit=equal:1 \
protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=500,4500 protocol=\
udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=ipsec-esp
add action=accept chain=forward comment="defconf: accept all that matches ipsec policy" \
ipsec-policy=in,ipsec
add action=drop chain=forward comment="defconf: drop everything else not coming from LAN" \
in-interface-list=!LAN
/system clock
set time-zone-name=Europe/Berlin
/system ntp client
set enabled=yes
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN The FritzBox VPN setup can be done either by the onboard webGUI or a customized VPN configuration file.
The setup GUI is pretty easy and done with a few mouseclicks.
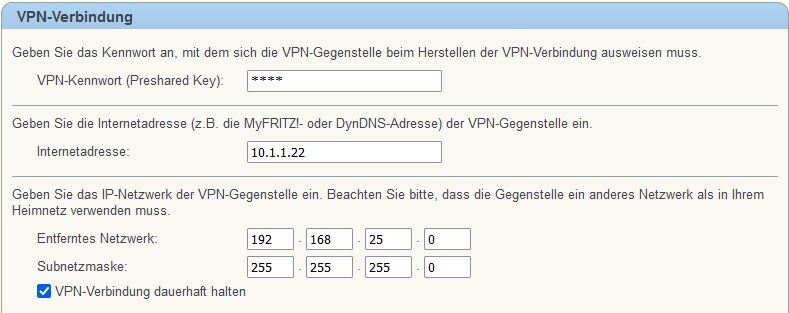
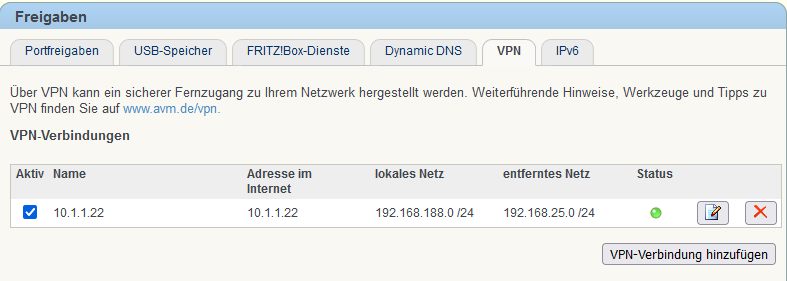
Further VPN settings for the FritzBox can also be done by a customized VPN configuration file.
Examples for FritzBox VPN files and more sophisticated informations regarding Fritzbox crypto algorithms can be found HERE.
General Cisco router setup:
Cisco 800, 900, ISR1100 Router Konfiguration mit xDSL, Kabel, FTTH Anschluss und VPN
Cisco, Mikrotik and pfSense with dynamic routing over VPN:
Cisco, Mikrotik, pfSense site-to-site VPN with dynamic routing
Detailed notes to FritzBox crypto credentials:
Fritzbox vpn crypto notes, part 1
Fritzbox vpn crypto notes, part 2
Secure port forwarding with Cisco ZFW firewall:
Cisco router with zone based firewall and port forwarding
Cisco Site-2-Site VPNs with IKEv2:
IPsec IKEv2 Standort VPN Vernetzung mit Cisco, pfSense OPNsense und Mikrotik
VPN Home Office Setup for Mikrotik and Fritzbox:
VPN zu FritzBox über Hardware?
Off topic:
Mikrotik VLAN tutorial:
Mikrotik VLAN Konfiguration ab RouterOS Version 6.41
Mikrotik PPPoE setup:
IPv6 mittels Prefix Delegation bei PPPoE (Mikrotik)
Fritzbox Wireguard configuration notes:
Fritzbox Wireguard notes
Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 2145635754
Url: https://administrator.de/tutorial/cisco-ipsec-vpn-with-mikrotik-or-fritzbox-2145635754.html
Ausgedruckt am: 13.07.2025 um 23:07 Uhr
Serie: Cisco-Tutorials
Cisco router with zone based firewall and port forwarding (englisch)Cisco IPsec VPN with Mikrotik or FritzBox (englisch)Cisco WLAN Access Points for Home Use: 1142N, 2702, 3702 and 3800 Comparison (englisch)Cisco, Mikrotik, pfSense site-to-site VPN with dynamic routing (englisch)1Cisco WLAN Access Points 3800, 3702, 2702 für den Heimgebrauch umrüsten124Cisco Telefon für All IP Anschluss, FritzBox und andere VoIP Anlagen fit machen183Cisco 800, 900, ISR1100 Router Konfiguration mit xDSL, Kabel, FTTH Anschluss und VPN285