PfSense VPN mit L2TP (IPsec) Protokoll für mobile Nutzer

Inhaltsverzeichnis
Das folgende VPN Tutorial ist eine Ergänzung zum bestehenden IKEv2 VPN Tutorial. Es beschreibt die VPN Anbindung von mobilen Benutzern oder Homeoffice Nutzern mit Windows, Mac OS, Linux sowie Smartphones und Pads unter Apple iOS und Android an die Firewall pfSense (Netgate).
Mikrotik Nutzer finden ein identisches Setup in einem separaten VPN Tutorial.
Mit dem hier eingesetzten L2TP VPN Protokoll werden immer die bordeigenen VPN Clients verwendet die alle Betriebssysteme, Smartphones usw. von sich aus schon mitbringen und die damit optimal ins Betriebssystem integriert sind.
Die Installation einer extra VPN Client Software ist in dieser L2TP VPN Variante wie auch bei der o.g. reinen IPsec IKE2 VPN Variante mit Server Zertifikat NICHT erforderlich!
Entgegen der zertifikatsbasierten IPsec IKEv2 Lösung, verzichtet das L2TP VPN Protokoll auf ein Server Zertifikat. Die VPN Einrichtung gerät damit insgesamt leichter und unkomplizierter.
Nachteil ist das die eindeutige VPN Server Identifizierung durch den Client mit einem Zertifikat fehlt, was eine Einschränkung in der Sicherheit bedeutet für Heim- und KMU Netze aber tolerabel ist.
Admins müssen hier entscheiden ob das eine oder andere Verfahren für sie günstiger und gem. ihrer Policies sicherer ist. Beide bieten mit den bordeigenen VPN Clients eine problemlose und kryptografisch sichere Client Anbindung per VPN an die Firewall oder Router.
Nutzer die die pfSense Firewall in einem Kaskaden Setup betreiben sollten die entsprechenden Hinweise im genannten Tutorial beachten die auch für L2TP VPNs gelten. OPNsense supportet derzeit kein L2TP. Hier bleibt dann die o.g. IKEv2 Variante.
Los gehts....
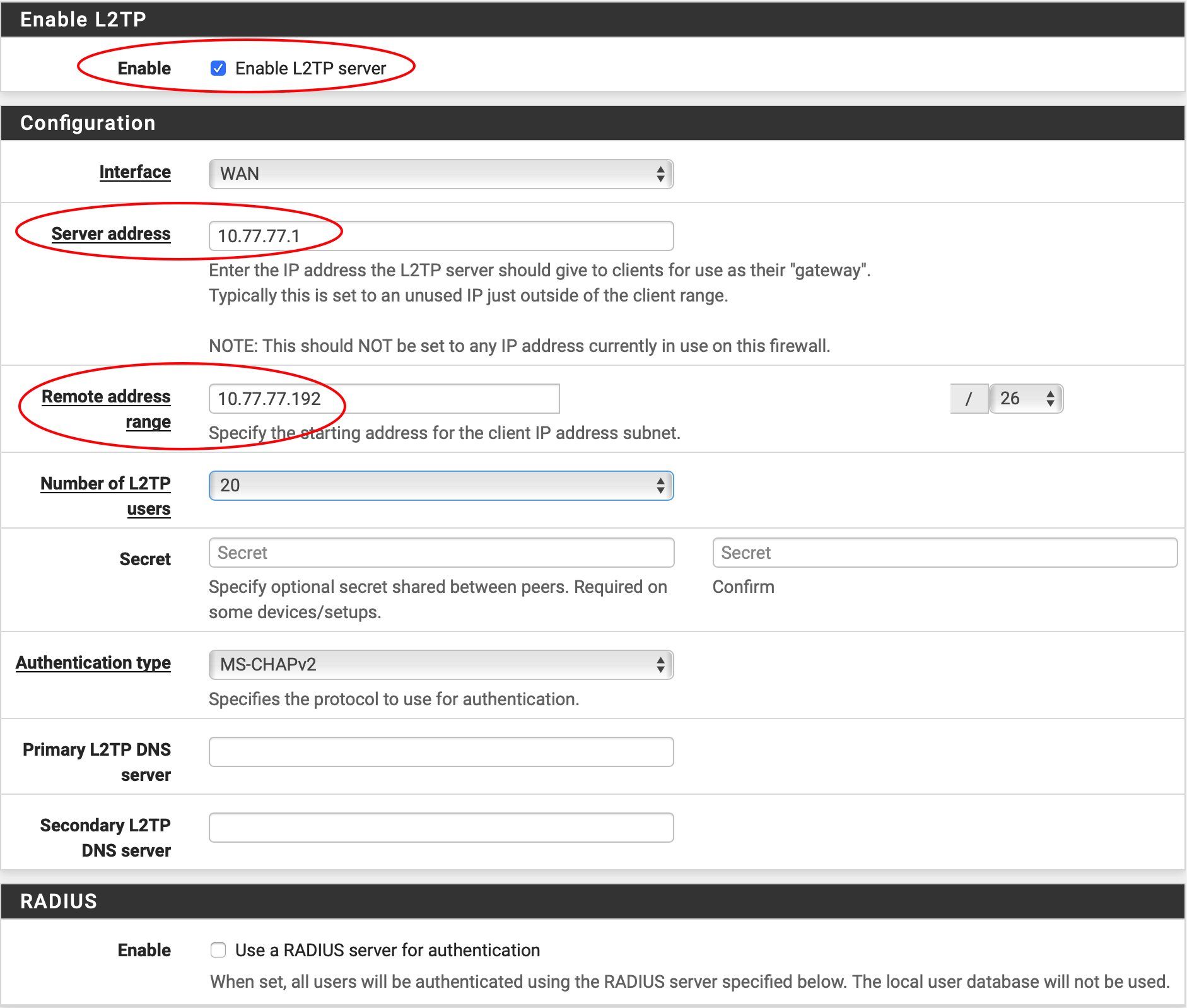
Zuerst aktiviert man im Menüpunkt VPN --> L2TP den L2TP Server mit folgenden Einstellungen:
- Haken aktiviert den L2TP Server
- "Interface" = WAN (WAN IP Adresse der Firewall)
- "Server Address" = Hier konfiguriert man eine VPN Server IP Adresse für das interne VPN Netzwerk. ACHTUNG: Dieses Netzwerk darf NICHT im Bereich der bestehenden Netzwerk IP Adressen der pfSense liegen ! Zudem sollte es niemals im Bereich vielfach verwendeter Standard IP Adressen, wie z.B. FritzBox (192.168.178.0), liegen da das zu einer Überschneidung und zur Fehlfunktion führt. Ideal sind hier etwas exotische IP Netze. Dieser Thread gibt Tips_zum_richtigen_VPN_Adressdesign ! Es ist sehr wichtig hier keine Banal 192.168er Allerweltsnetze zu definieren was oft zu Fehlfunktionen und Scheitern der VPNs durch Adressüberschneidungen führt !!
- "Secret" = leer lassen!
- "Remote Adress Range" = Adressbereich der VPN Clients. Dieses Netzwerk definiert den Client IP Bereich. Es darf sich NICHT mit der darüber liegenden Server IP überschneiden ! Das Beispiel hier nutzt das Subnetz 10.77.77.192 mit einer 26 Bit Maske (255.255.255.192) was damit insgesamt 62 VPN Clients erlaubt. (Server IP ist so im 10.77.77.0/26 Netz, Client Range im 10.77.77.192/26 Netz. Erlaubt wären bei /26 z.B. auch 10.77.77.64/26 oder 10.77.77.128/26). Eine größere Maske von z.B. /25 Bit (255.255.255.128, Netzwerk: 10.77.77.128) erlaubt insgesamt 126 VPN User usw.
- "Number of Users" = Hier gibt man die maximale Anzahl der zu erwartenden VPN User an. ⚠️ Die Anzahl muss natürlich zum obigen IP Bereich (Netzmaske) der VPN Adressen passen und immer kleiner sein als die maximale, durch die Netzmaske technisch mögliche Anzahl !
- "Authentication Type" = MS CHAPv2
- "L2TP DNS Server" = (Optional) Hier definiert man z.B. interne DNS Server (Windows) die man dem Client bei VPN Einwahl automatisch übergeben will. Lässt man es weg wird normal wie auch im LAN die pfSense als DNS IP vergeben.
- "Radius" = (Optional) Wer einen Radius Server zur externen User Authentisierung verwendet aktiviert ihn hier. In dem Fall entfällt der Eintrag der lokalen Userdaten. Ohne Radius leer lassen.
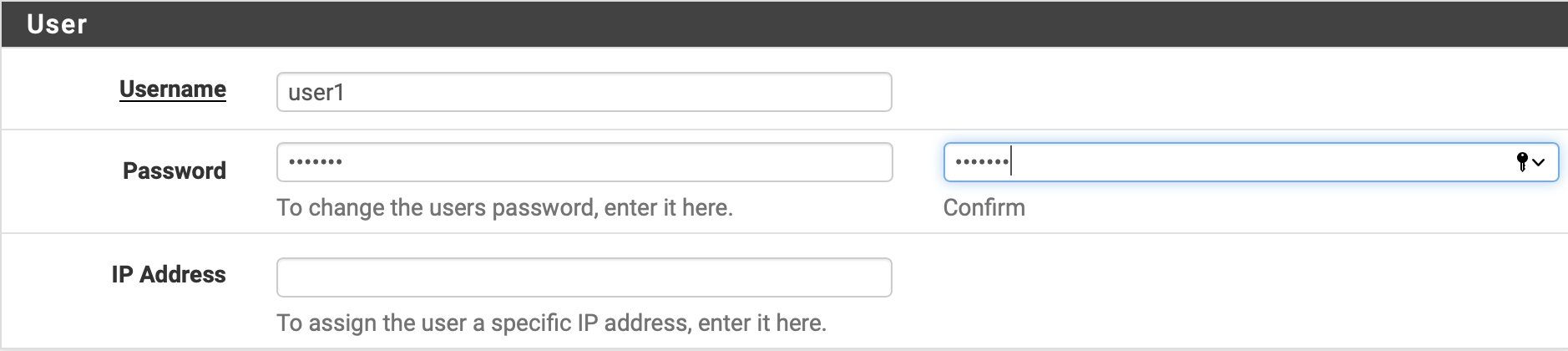
Im VPN -> L2TP User Menü konfiguriert man nun die Benutzernamen und Passwort zur VPN Einwahl.
WICHTIG: Unter IP Address kann man optional jedem Benutzer eine spezifische IP zuweisen lassen. Das ist wichtig wenn man später bestimmte Benutzer mit Firewall Regeln den Zugriff auf einzelne Netze oder Rechner oder auch Anwendungsdienste steuern will !
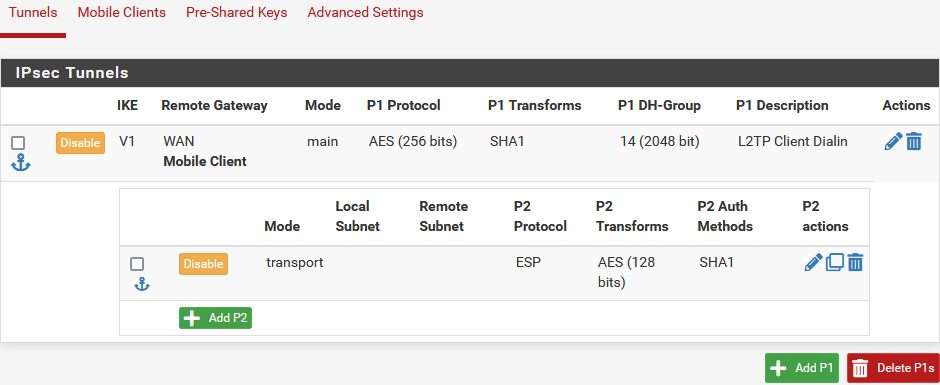
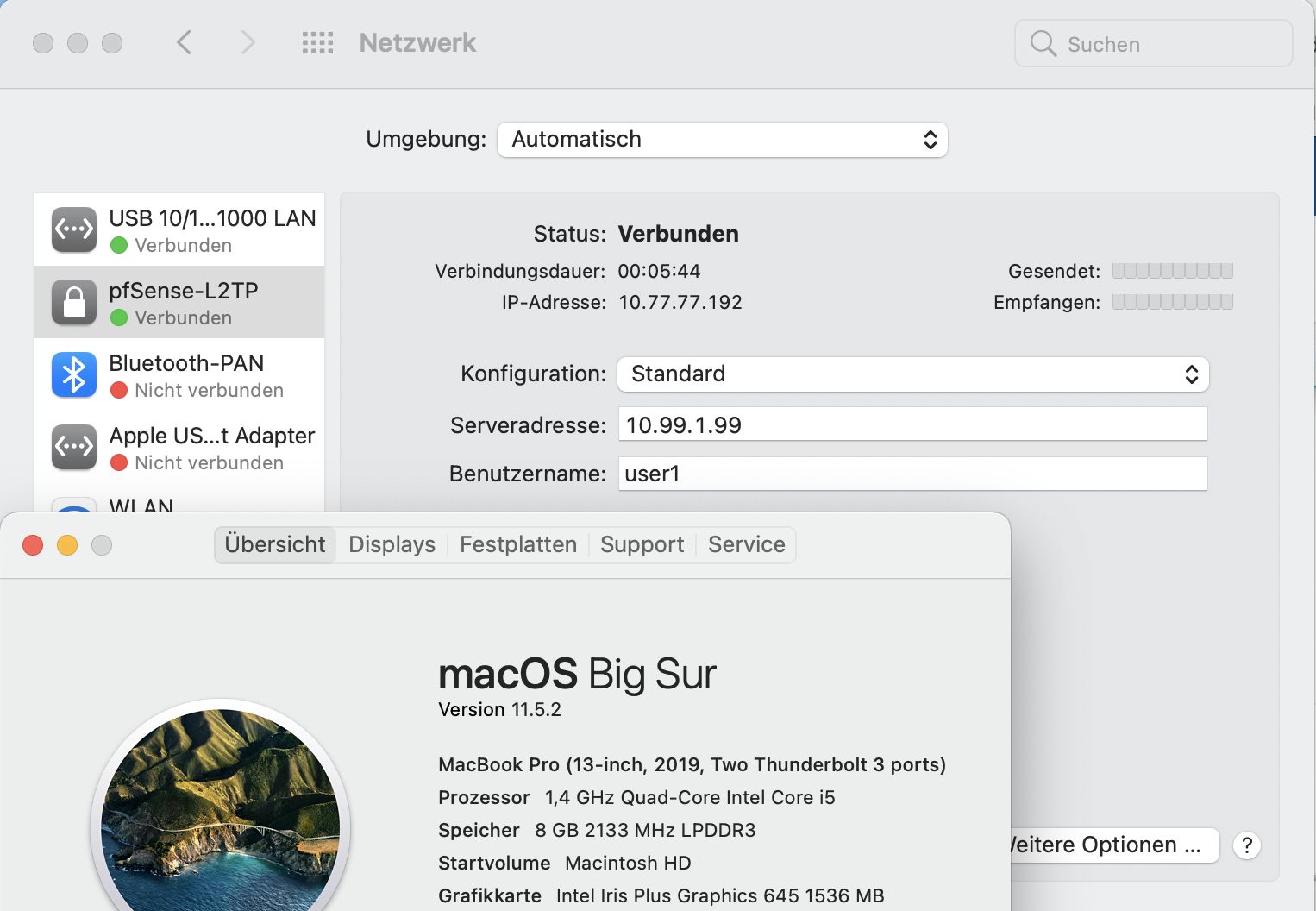
Der L2TP Tunnel nutzt IPsec ESP mit IKEv1 als Verschlüsselung was entsprechend im Menüpunkt VPN -> IPsec, Mobile Clients eingerichtet werden muss.
- "User Authentication" = Local Database
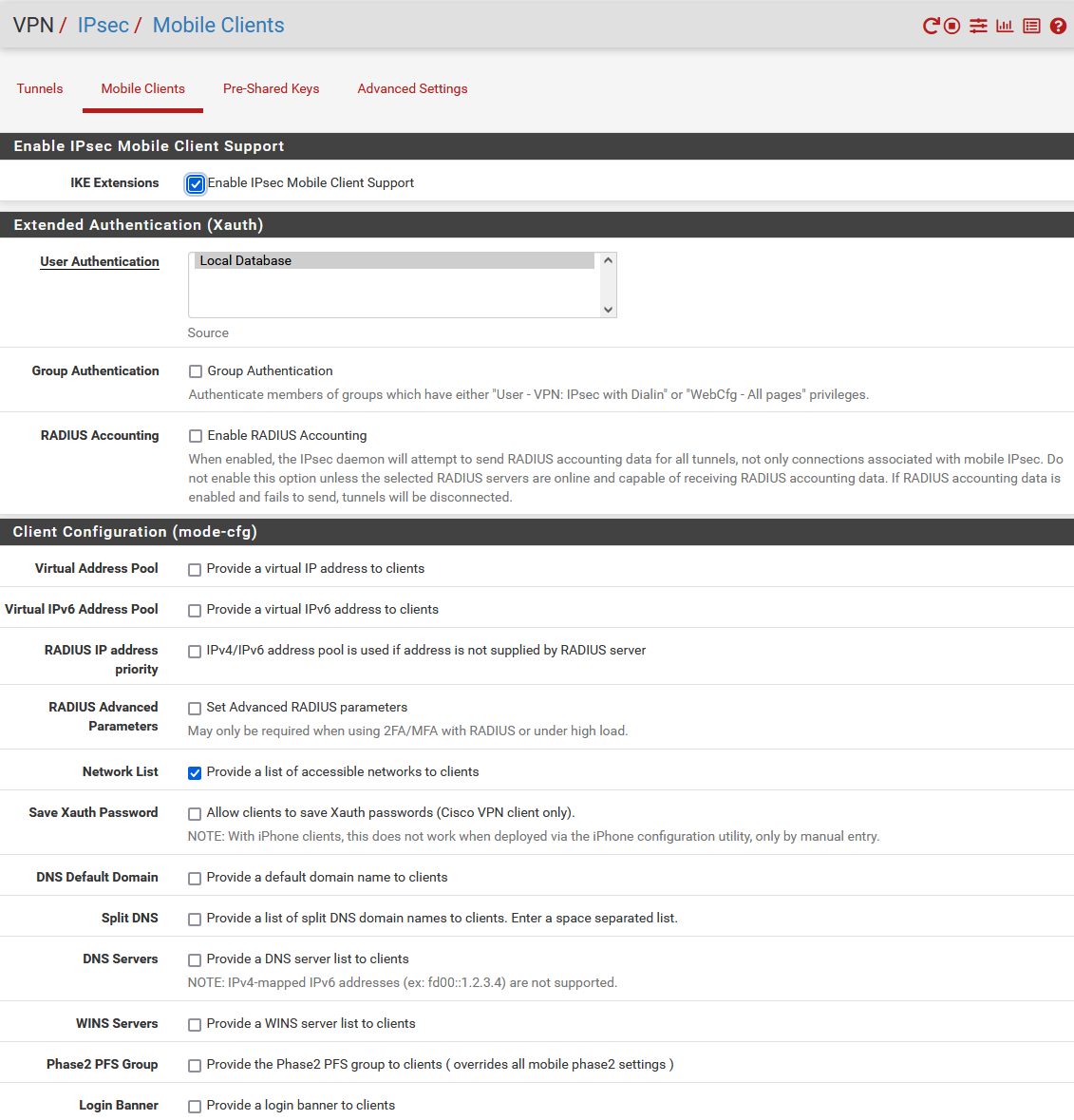
⚠️ Die folgende IPsec Phase 1 muss aus diesem Mobile Client Menü heraus eingerichtet werden !! Von dort also unbedingt rechts auf "Create Phase 1" klicken !

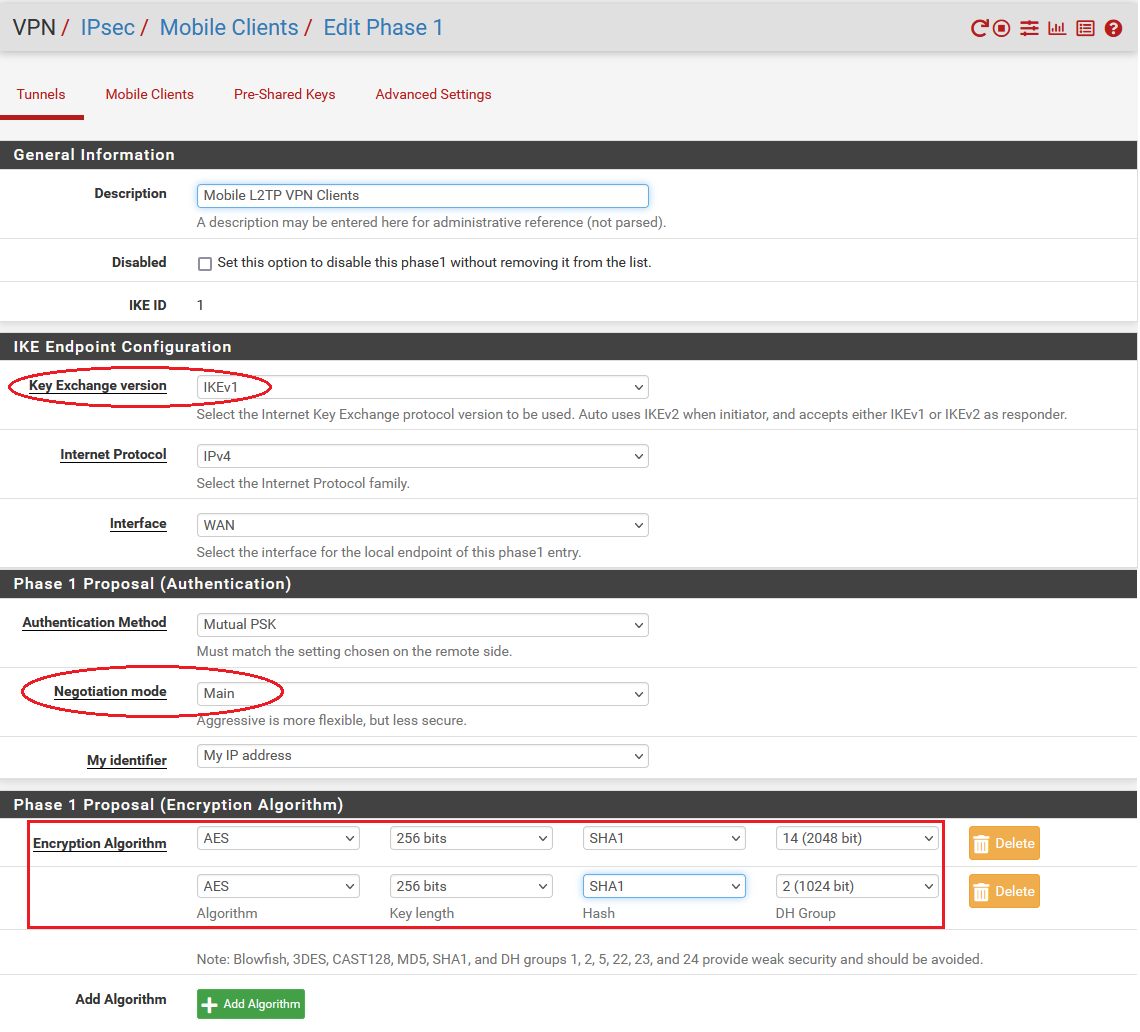
- "Key Exchange Version" = IKEv1
- "Authentication method" = Mutual PSK
- "Negotiation Mode" = Main
- "My Identifier" = My IP address
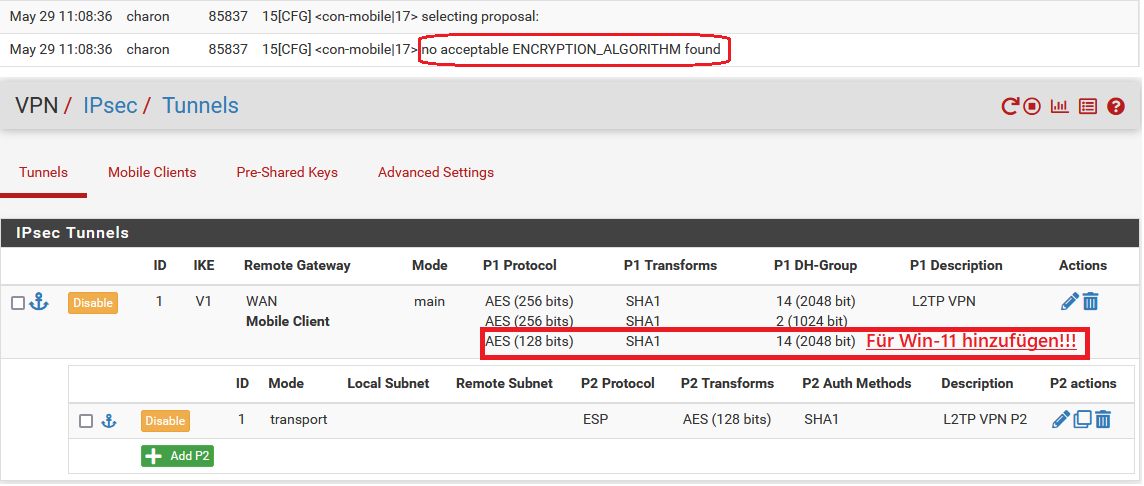
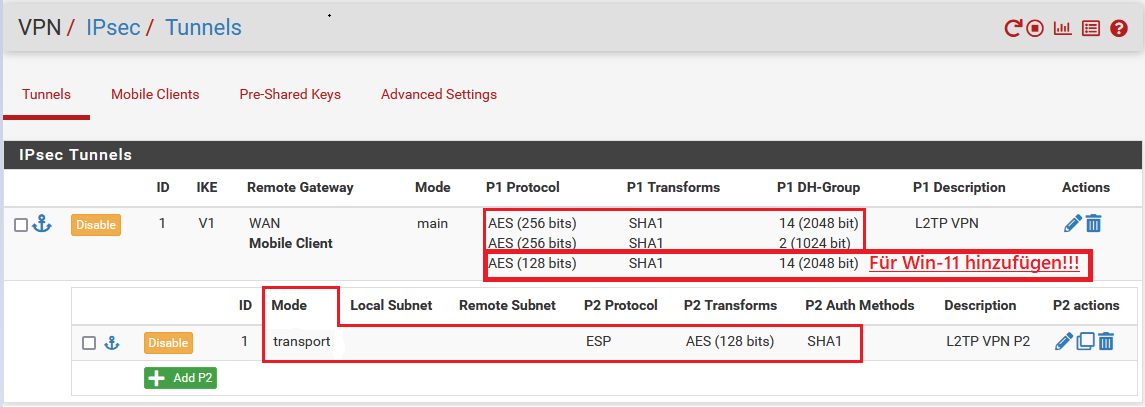
- "Encryption algorithm" = AES 256, ⚠️ Bei Windows 11 L2TP Clients! Diese erfordern aktuell (21H2) zusätzlich AES 128! Siehe HIER! Zu den 2 unten im Beispiel kommt eine Dritte mit AES128, SHA1, DH2 (o. DH14) hinzu. (Siehe Screenshot "P1/P2 Konfigübersicht" unten!)
- "Hash algorithm" = SHA1
- "DH key group" = 14 (2048 bit) (Achtung: Bei Fehlfunktion im VPN Aufbau mit älteren Smartphones, Chromebooks und einigen Android Modellen hier statt 14 dann DH key group = 2 (1024 bit) verwenden! Sinnvoll ist immer einen 2ten bzw. 3ten (Win11) P1 Eintrag mit DH2 zusätzlich hinzuzufügen um alle Optionen abzudecken !)
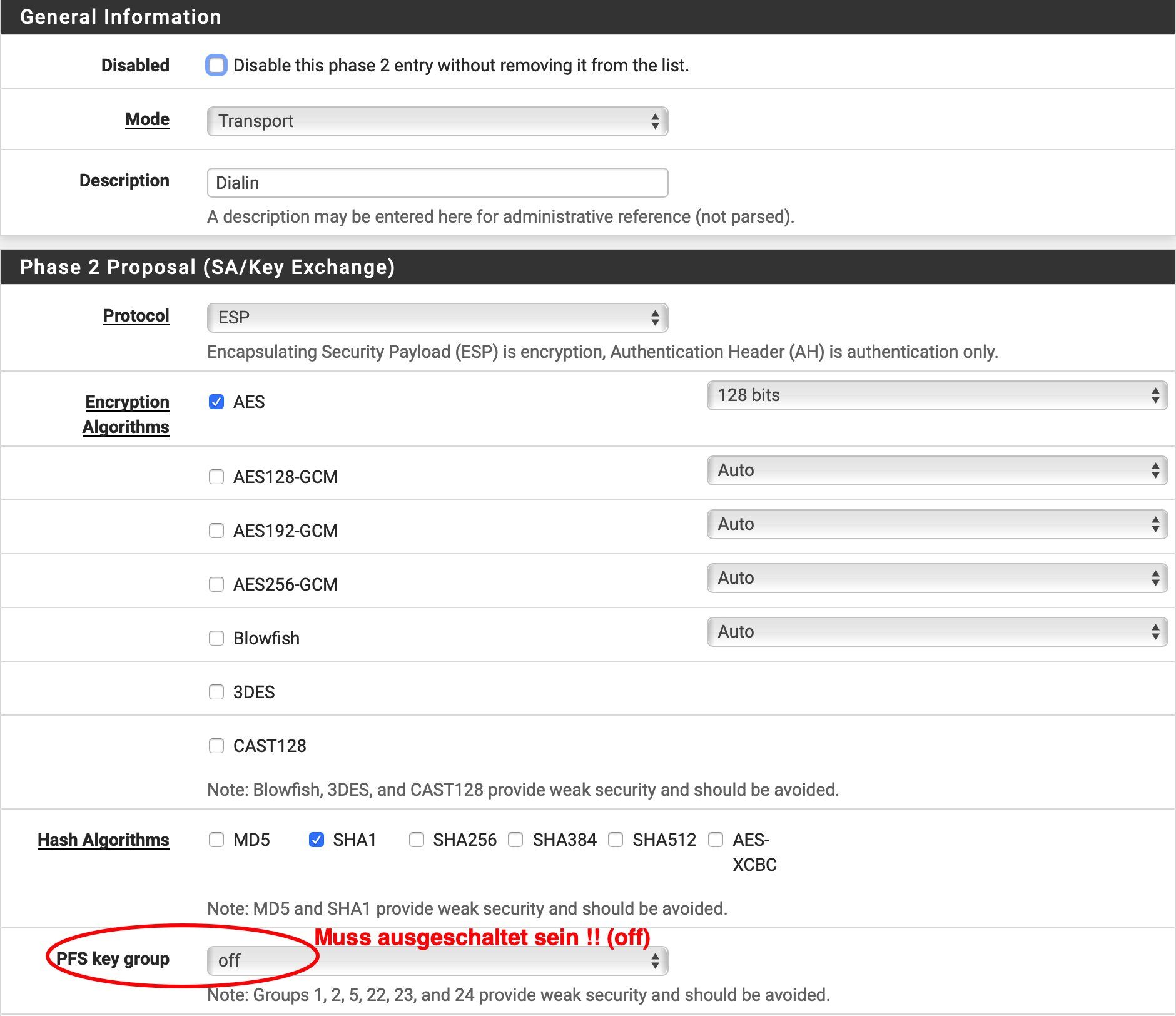
- "Mode" = Transport
- "Protocol" = ESP
- "Encryption algorithms" = nur AES 128
- "Hash algorithms" = nur SHA1
- "PFS Key Group" = off (muss auf AUS sein !)
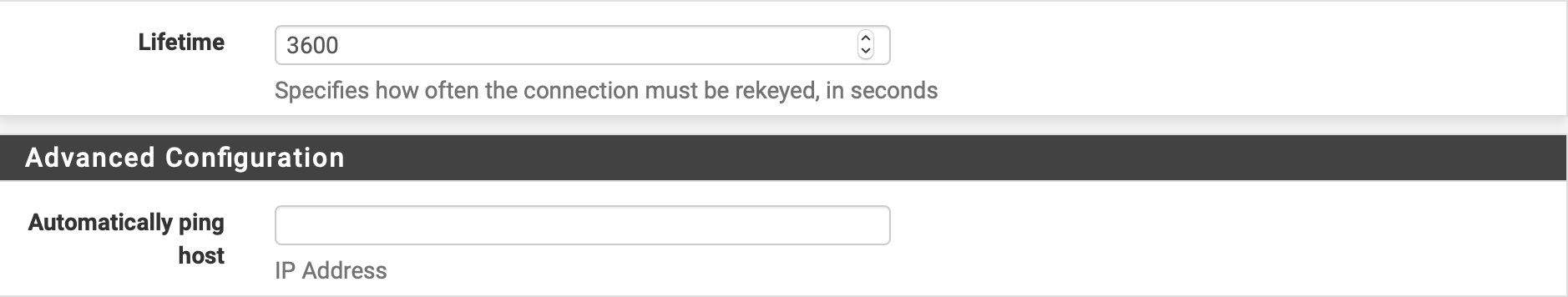
Hat man alles richtig konfiguriert sieht die Übersicht der P1 und P2 für die mobilen VPN Clients so aus:
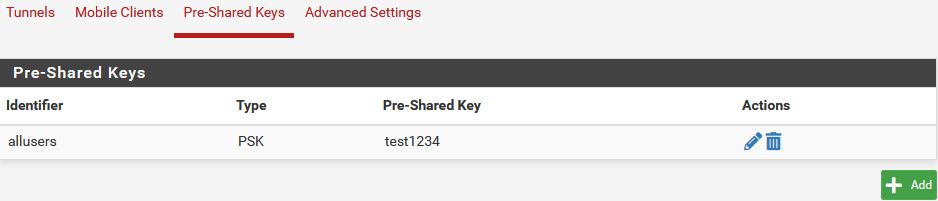
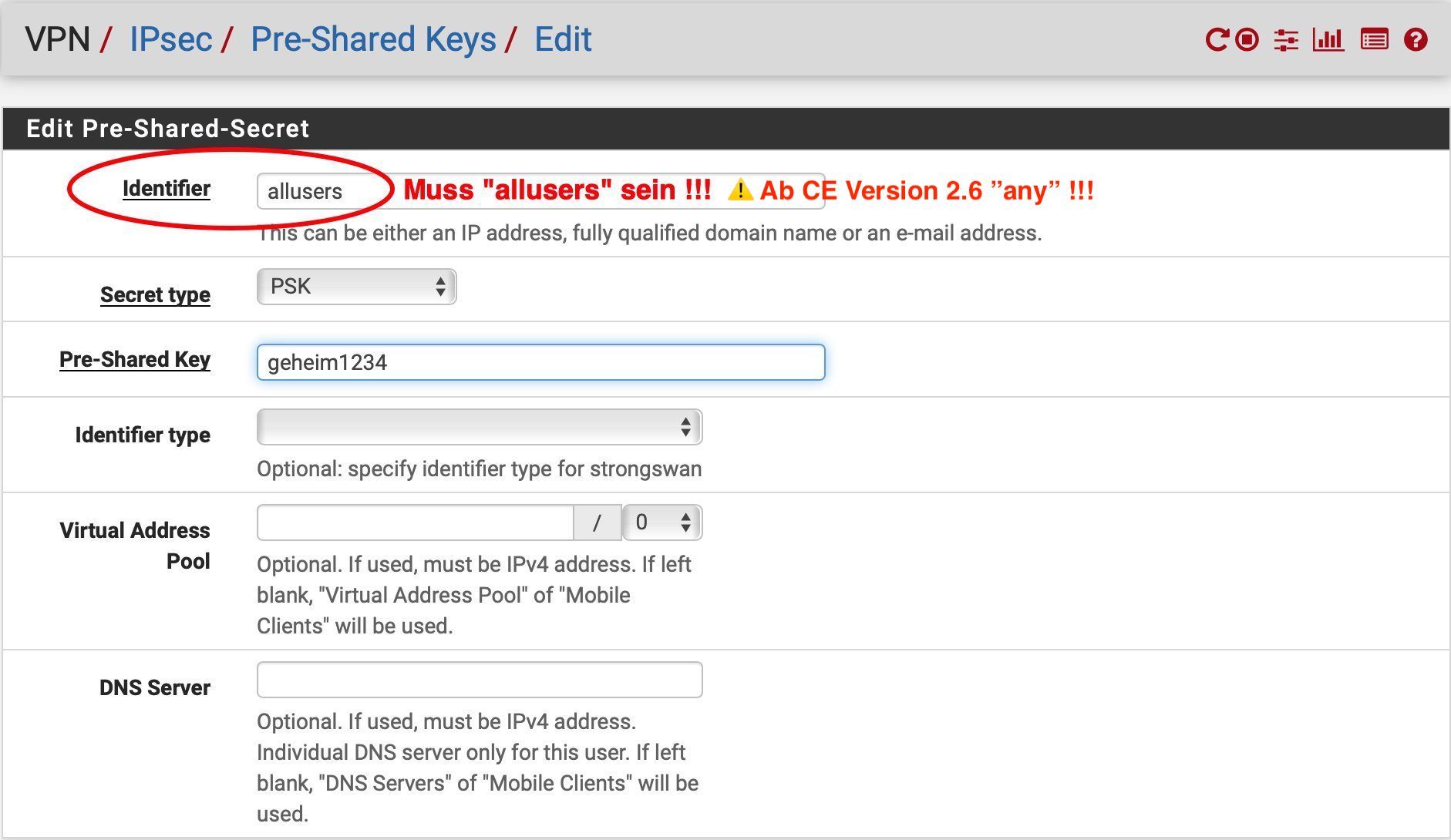
Im Menü VPN -> IPsec, Pre-Shared Keys
- "Identifier" = MUSS hier immer allusers sein ! Der String allusers ist eine Wildcard für den vorinstallierten L2TP Schlüssel. Er darf nicht verändert werden !
- ⚠️ Ab pfSense Community Edition Ver. 2.6 ist dies geändert und lautet dann any ! (Dank an @TobiasNYC für diesen Hinweis)! (Anmerkung: Ein aktueller Test zeigt aber bei Ver. 2.6 das es völlig egal ist ob "any" oder "allusers" eingetragen ist!))
⚠️ Es sind 3 Firewall Regeln zu konfigurieren damit der L2TP VPN Zugriff klappt ! L2TP erstellt keine automatischen WAN Regeln!
- 1. Inbound Regel am WAN Port die L2TP VPN Traffic auf die Firewall WAN IP Adresse erlaubt
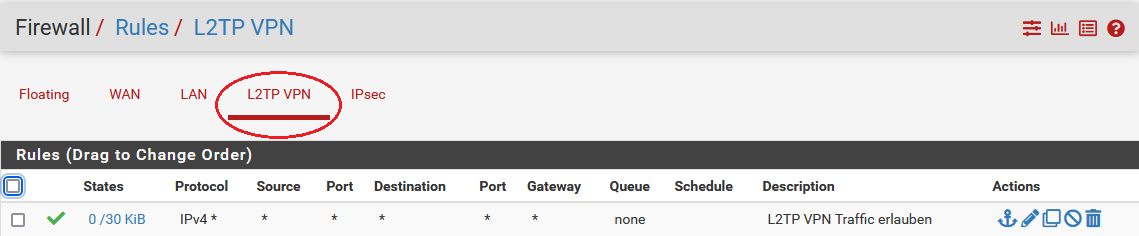
- 2. L2TP Tunnel Regel
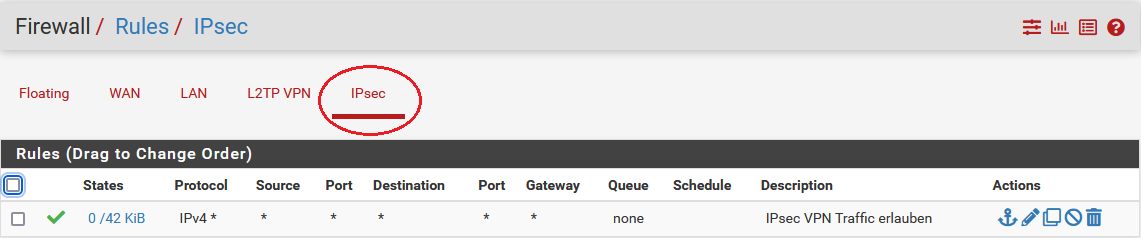
- 3. IPsec Tunnel Regel
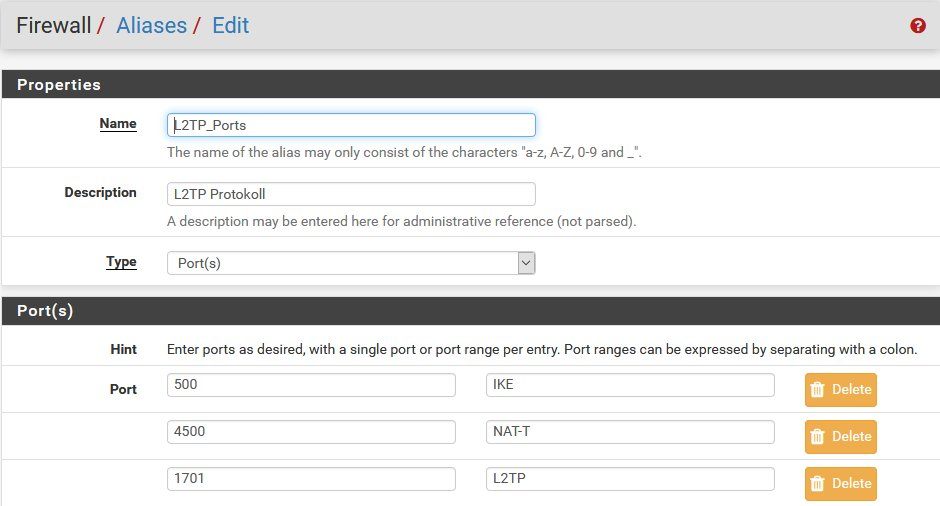
Hier definiert man die L2TP Ports idealerweise, der Einfachheit halber, vorab in einem Firewall Port Alias Eintrag mit UDP 500, 4500 und 1701. Zusätzlich dazu ist das ESP Protokoll freizugeben.
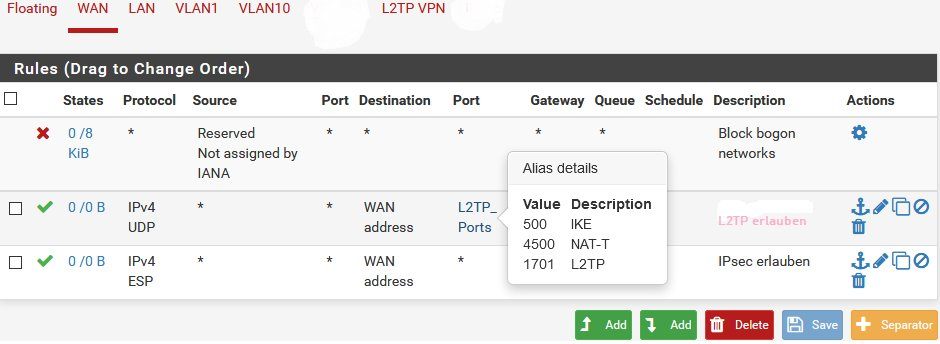
Hier nutzt man meist die bekannte "Scheunentor" Regel. Bei Bedarf kann (und sollte) sie später aber strikter eingestellt werden.
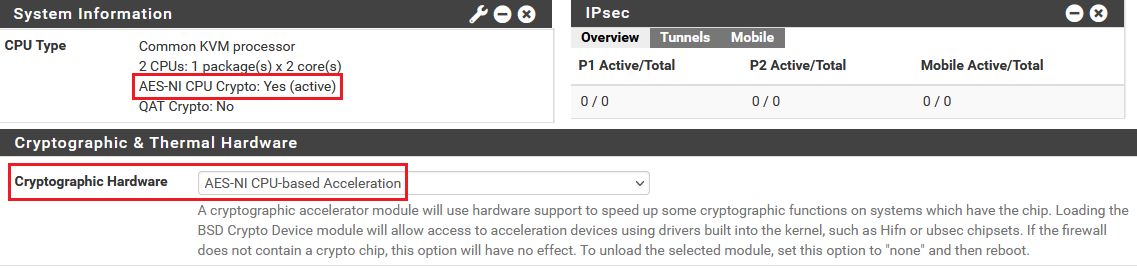
Für die VPN Skalierbarkeit (Performance) ist zu beachten immer den AES NI Support der Firewall CPU zu aktivieren und dies auch auf ggf. virtualisierte Firewalls an die VM durchzureichen! So wird der Grossteil der Verschlüsselung in Hardware gemacht.
Eingestellt wird dies im Menü Advanced -> Miscellaneous.
Empfehlenswert ist auch die Installation des IPsec Widgets im Dashboard. Das Widget ermöglicht den schnellen Überblick über aktive VPN User.
⚠️Versionen älter als 21H2 benötigen einen Patch ! 22H2 oder neuer erfordert keinen Patch!
Den Windows Client legt man mit dem bordeigenen Windows VPN Setup an:
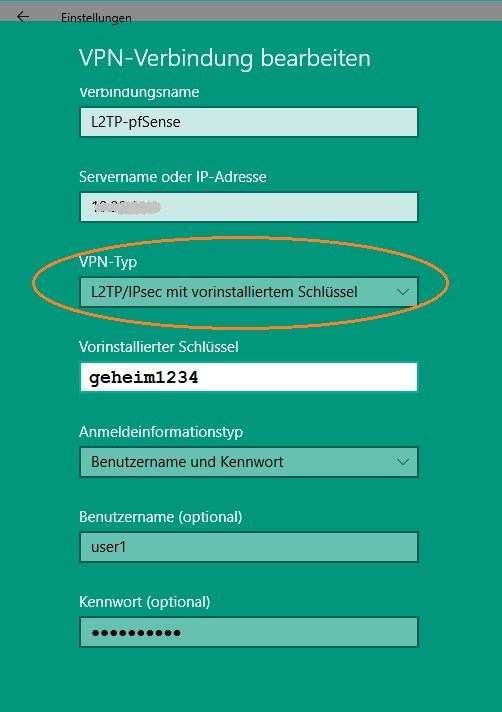
⚠️ Im Windows L2TP Client müssen zusätzlich noch ein paar spezifische Einstellungen vorgenommen werden!:
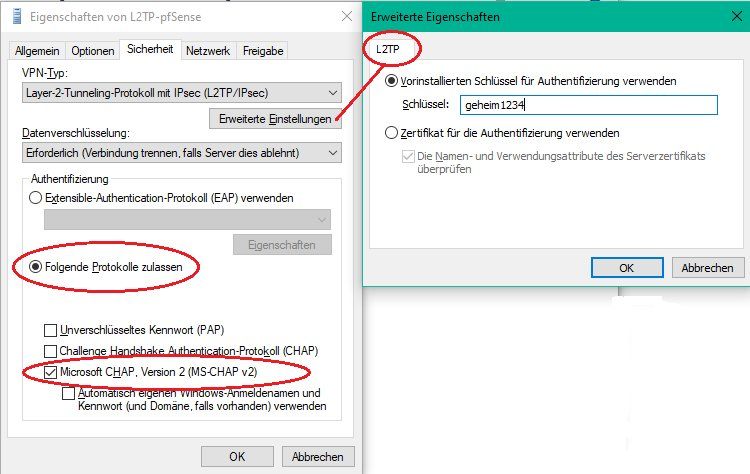
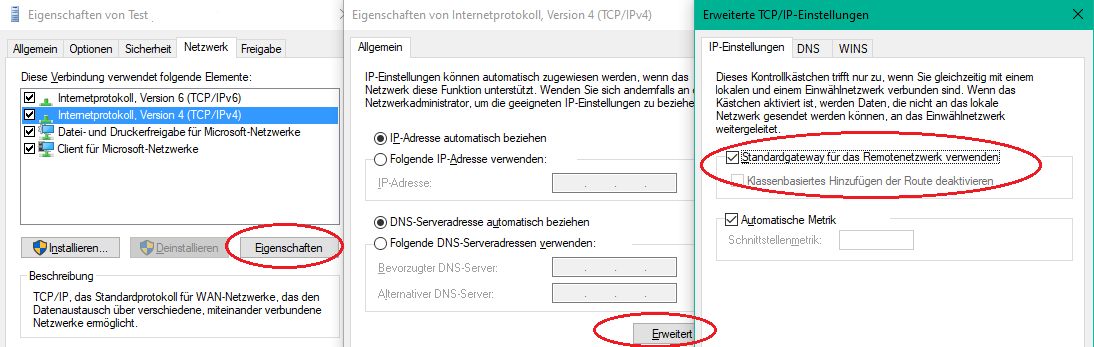
⚠️ Dieser Hinweis gilt für den Betrieb des L2TP VPN Servers hinter einem NAT Router in einer Router Kaskade!
Der Windows L2TP Client (und nur der!) supportet im Default kein NAT-Traversal und muss dazu erst mit einem Eintrag in der Windows Registry angepasst werden. (Siehe dazu auch HIER) Microsoft weist in ihrer Knowledgebase ebenfalls darauf hin!
Im Falle eines NAT Kaskaden Designs scheitert dann der Tunnelaufbau bei Windows. (Dank an Forenuser @FlorianHe für diesen Hinweis)
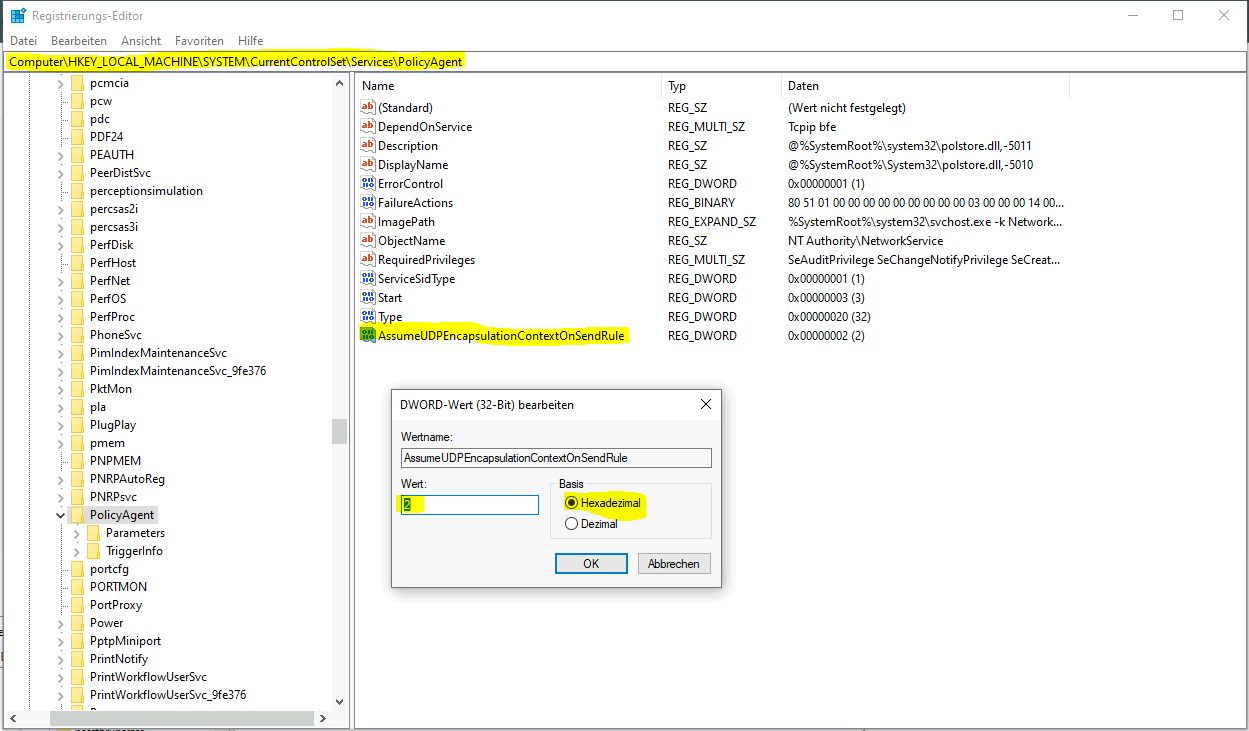
Das Kommando
reg add HKLM\SYSTEM\CurrentControlSet\Services\PolicyAgent /v AssumeUDPEncapsulationContextOnSendRule /t REG_DWORD /d 0x2 /f Er kann auch manuell über den Registry Editor regedit eingegeben werden:
Analog funktioniert die Einrichtung des Apple MacOS L2TP Clients:
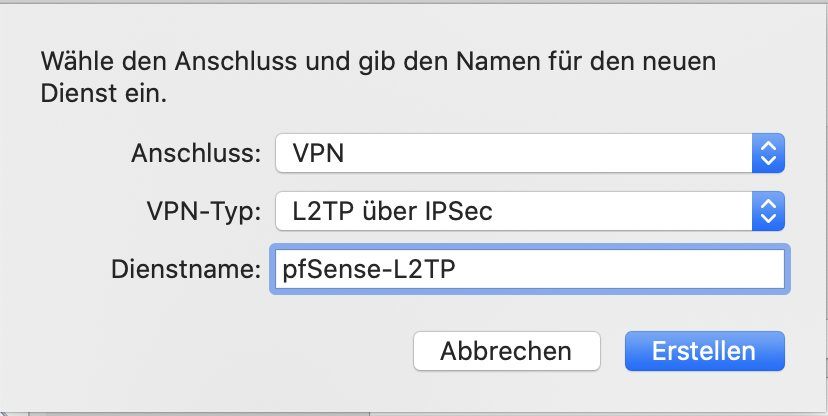
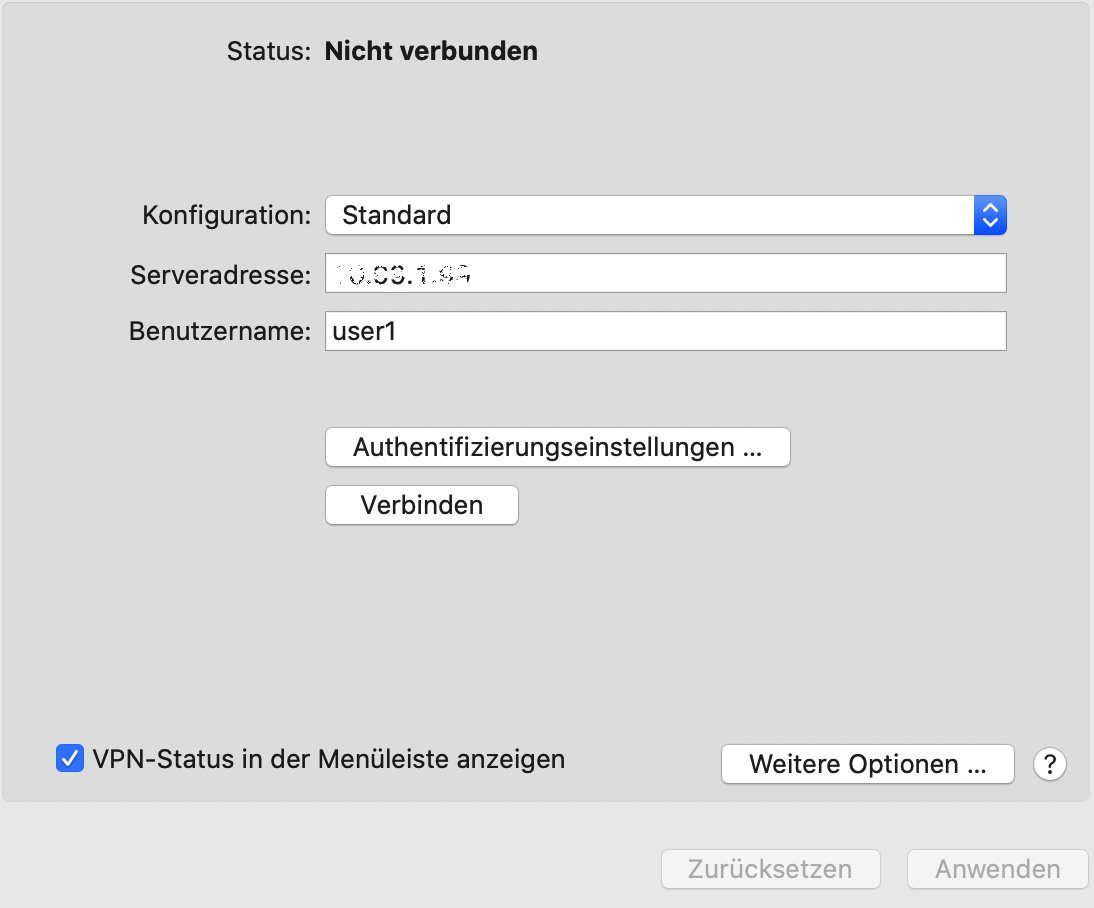
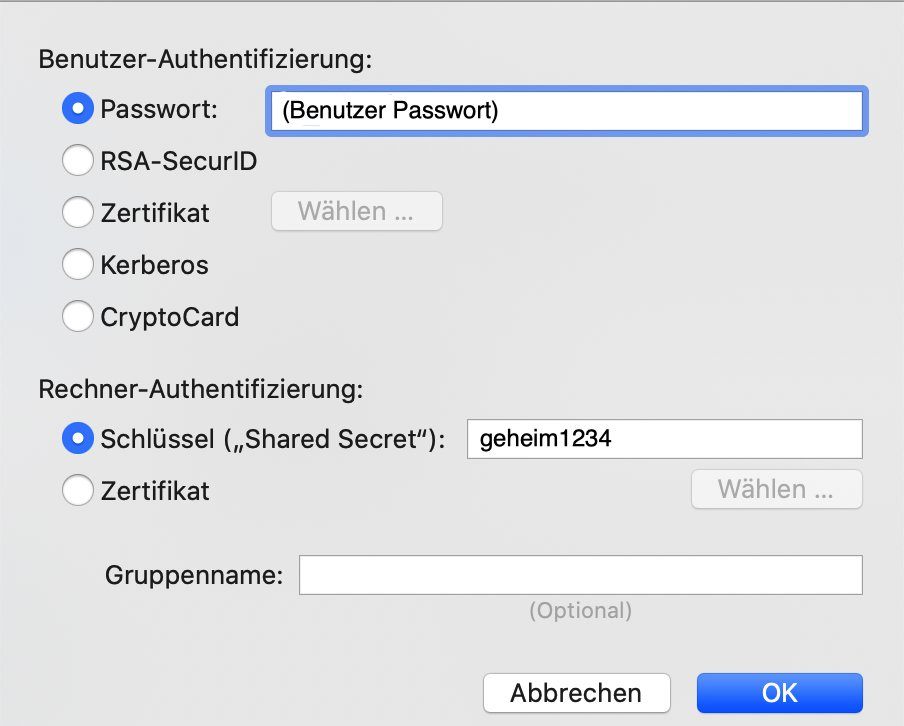
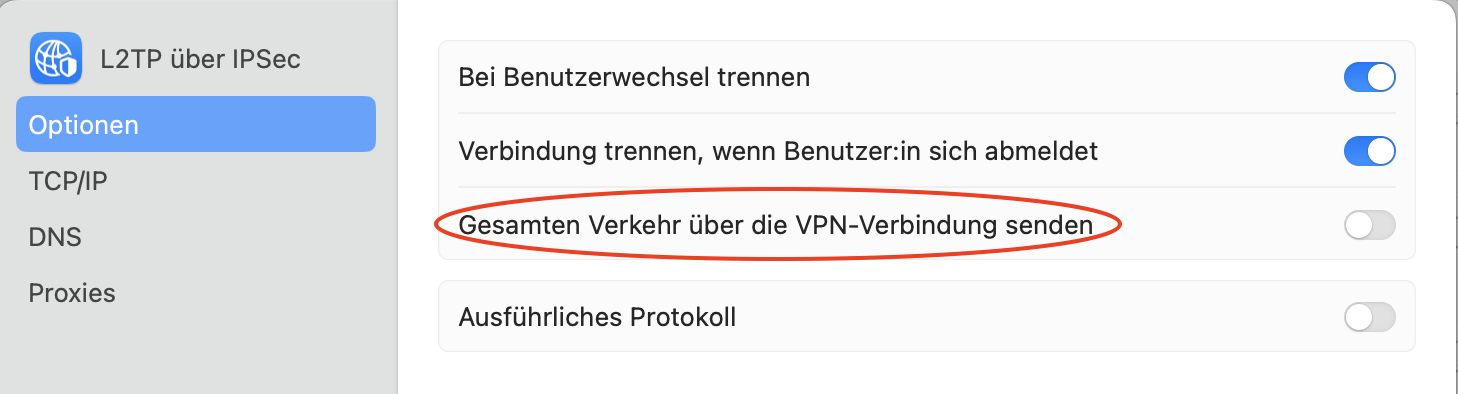
Der Apple iOS Client hat als einziger L2TP Client die Option "Split Tunneling" zu machen oder alles in den Tunnel zu senden:

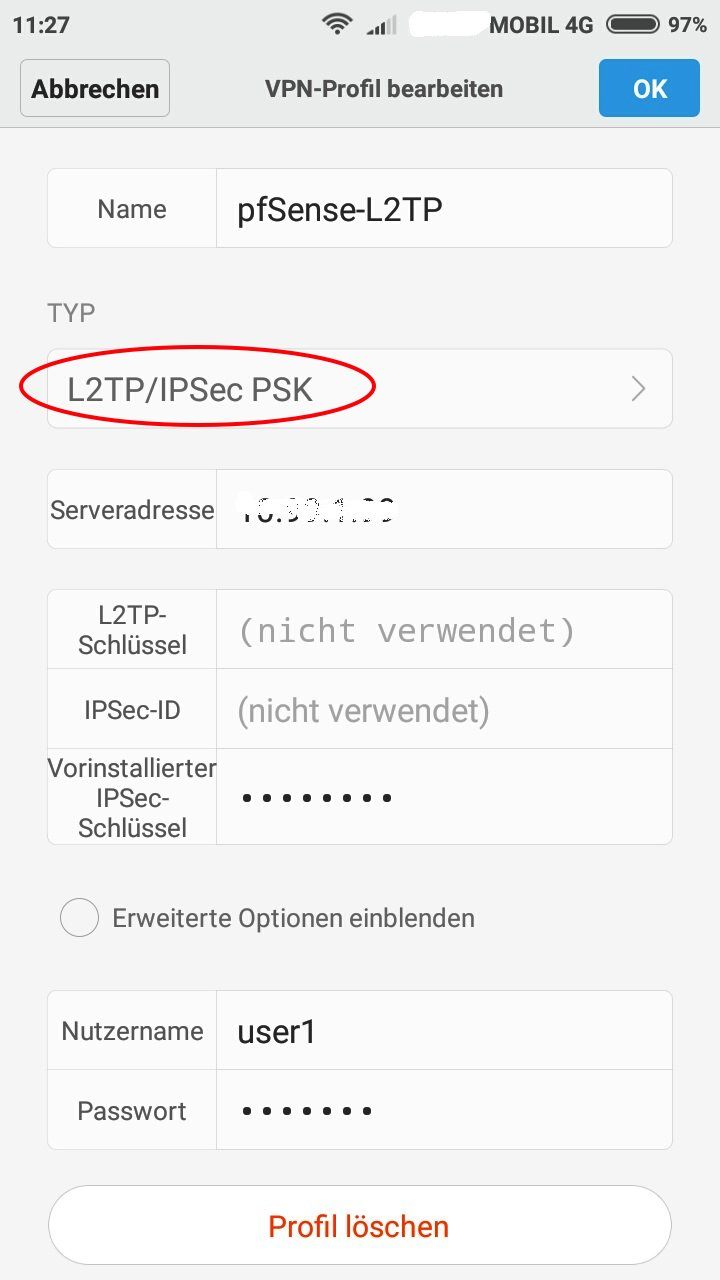
Achtung:
Einige ältere und einfache Android Smartphones (und vereinzelt alte Apple iPhones) supporten keine DH Key Gruppe 14 (2048 Bit) und dann scheitert der L2TP Verbindungsversuch.
In diesem Falle muss man für den Support älterer Geräte oben in den IPsec Settings auf DH key group = 2 (1024 bit) umstellen !
Unter Linux muss ggf. mit
sudo apt install network-manager-l2tp
sudo apt install network-manager-l2tp-gnome
die GUI Komponenten nachinstalliert werden. Das Strongswan Package muss auch installiert sein (xl2tpd, strongswan).
In aktuellen Ubuntu Versionen muss ein entsprechendes PPA eingebunden werden damit es mit dem neuen netplan läuft. (Siehe HIER und gilt nur für Ubuntu).
Bei Raspberry Pis mit Debian Bullseye muss in der raspi-config das Netzwerk Management auf den NetworkManager umgestellt werden. Ab aktuellem Bookworm ist der NetworkManager im Default aktiv!
Das Setup für das klassische L2TP Network-Manager GUI sieht so aus:
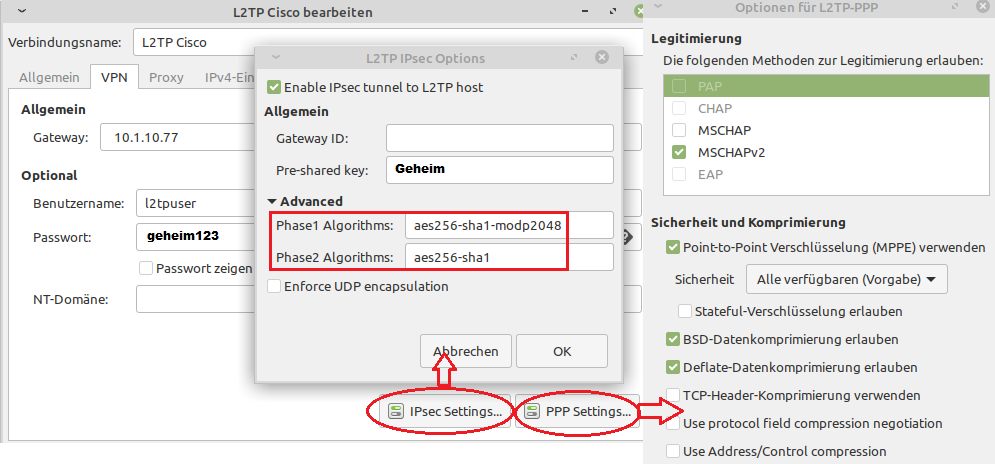
Eine weitere GUI Variante über die grafische Oberfläche hier.
NetGate L2TP/IPsec Handbuch:
docs.netgate.com/pfsense/en/latest/vpn/ipsec/l2tp-ipsec.html
Mikrotik L2TP VPN Server für alle onboard VPN Clients und Smartphones:
Mikrotik L2TP VPN Server Setup
VPN Verbindung Windows 10 zu MikroTik L2TP
L2TP Site to Site (Standort) Anbindung mit Mikrotik:
Mikrotik Site-2-Site mit L2TP
Cisco Router als L2TP VPN Server:
Cisco 800, 900, ISR1100 Router Konfiguration mit xDSL, Kabel, FTTH Anschluss und VPN
Windows und iPhone L2TP Client Routing und DNS Verhalten:
L2TP Client Routing u. DNS Windows und Apple iOS
pfSense / OPNsense IKEv2 VPN für mobile Benutzer mit bordeigener VPN Software:
IPsec IKEv2 VPN für mobile Benutzer auf der pfSense oder OPNsense Firewall einrichten
Benutzer Authentisierung mit Client Zertifikaten statt PSK:
Mobile Clients mit Client Certificate authentifizieren
Benutzer Authentisierung mit Radius Server:
Freeradius Management mit WebGUI
Mikrotik als SSTP VPN Server für Windows Clients:
justit.eu/mikrotik-sstp-vpn-fuer-windows-clients/
Windows 10: Schneller VPN Aufbau per einfachem Mausklick:
heise.de/ct/ausgabe/2017-19-VPN-und-Remote-Desktop-Verbindungen- ...
Windows User Credentials beachten:
Windows VPN L2TP , falsche Anmeldedaten
Automatisiertes VPN "on Demand" für iOS Apple Endgeräte über XML Templates:
VPN - Fritzbox vs. MikroTik
Windows 10 VPN IKE Verhalten:
docs.microsoft.com/en-us/openspecs/windows_protocols/ms-ikee/74d ...
FritzBox 7412 als preiswertes VDSL "nur" Modem für pfSense/OPNsense:
spiegel.de/netzwelt/gadgets/fritzbox-7412-als-dsl-modem-dect-bas ...
heise.de/select/ct/2020/2/1578238295698254
pfSense auf VmWare ESXi:
VLAN mit Cisco SG220, ESXIund Pfsense
Sophos Software Appliance UTM - VLAN - CISCO SG Series Switches
Fehler bei IPv6 vermeiden:
PFsense IPv6 - Was mache ich falsch ?
Seriellen Terminal Anschluss richtig handhaben:
Alschluss eines USB Seriel Adapter am APU2E4 Board
Email Benachrichtigungen richtig einrichten:
OPNSense - EMAIL Alerts - failed login
Link Aggregation (LAG) mit pfSense und OPNsense:
Link Aggregation (LAG) im Netzwerk
AirPrint Drucker und andere Bonjour/mDNS Dienste erreichbar machen:
Apple AirPrint über VLANs
OT: AdGuard DNS Filter auf pfSense/OPNsense installieren:
broadbandforum.co/t/205884/
OpenVPN auf der pfSense einrichten:
OpenVPN Server installieren auf pfSense Firewall, Mikrotik. DD-WRT oder GL.inet Router
Bitte markiere auch die Kommentare, die zur Lösung des Beitrags beigetragen haben
Content-ID: 585307
Url: https://administrator.de/tutorial/pfsense-vpn-mit-l2tp-ipsec-protokoll-fuer-mobile-nutzer-585307.html
Ausgedruckt am: 23.07.2025 um 11:07 Uhr
24 Kommentare
Neuester Kommentar
Ich bekomme das hier nicht zum laufen.
Weiss jemand, was da falsch läuft?
An support.apple.com/de-at/HT211840 liegt es nicht?
Mac:
Thu Sep 9 11:52:22 2021 : publish_entry SCDSet() failed: Success!
Thu Sep 9 11:52:22 2021 : publish_entry SCDSet() failed: Success!
Thu Sep 9 11:52:22 2021 : l2tp_get_router_address
Thu Sep 9 11:52:22 2021 : l2tp_get_router_address 172.20.10.1 from dict 1
Thu Sep 9 11:52:22 2021 : L2TP connecting to server 'vpn.xxxx.de' (xxx.yz.148.51)...
Thu Sep 9 11:52:22 2021 : IPSec connection started
Thu Sep 9 11:52:22 2021 : IPSec phase 1 client started
Thu Sep 9 11:52:22 2021 : IPSec phase 1 server replied
Thu Sep 9 11:52:23 2021 : IPSec phase 2 started
Thu Sep 9 11:52:24 2021 : IPSec phase 2 established
Thu Sep 9 11:52:24 2021 : IPSec connection established
Thu Sep 9 11:52:24 2021 : L2TP sent SCCRQ
Thu Sep 9 11:52:44 2021 : L2TP cannot connect to the server
PFsense:
Sep 9 11:52:22 charon 13353 06[NET] <6> received packet: from xyz.abc.116.238[500] to def.ijk.148.51[500] (788 bytes)
Sep 9 11:52:22 charon 13353 06[ENC] <6> parsed ID_PROT request 0 [ SA V V V V V V V V V V V V ]
Sep 9 11:52:22 charon 13353 06[CFG] <6> looking for an IKEv1 config for def.ijk.148.51...xyz.abc.116.238
Sep 9 11:52:22 charon 13353 06[CFG] <6> candidate: 0.0.0.0/0, ::/0...0.0.0.0/0, ::/0, prio 28
Sep 9 11:52:22 charon 13353 06[CFG] <6> found matching ike config: 0.0.0.0/0, ::/0...0.0.0.0/0, ::/0 with prio 28
Sep 9 11:52:22 charon 13353 06[IKE] <6> received NAT-T (RFC 3947) vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received draft-ietf-ipsec-nat-t-ike vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received draft-ietf-ipsec-nat-t-ike-08 vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received draft-ietf-ipsec-nat-t-ike-07 vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received draft-ietf-ipsec-nat-t-ike-06 vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received draft-ietf-ipsec-nat-t-ike-05 vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received draft-ietf-ipsec-nat-t-ike-04 vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received draft-ietf-ipsec-nat-t-ike-03 vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received draft-ietf-ipsec-nat-t-ike-02 vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received FRAGMENTATION vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> received DPD vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> xyz.abc.116.238 is initiating a Main Mode IKE_SA
Sep 9 11:52:22 charon 13353 06[IKE] <6> IKE_SA (unnamed)[6] state change: CREATED => CONNECTING
Sep 9 11:52:22 charon 13353 06[CFG] <6> selecting proposal:
Sep 9 11:52:22 charon 13353 06[CFG] <6> no acceptable INTEGRITY_ALGORITHM found
Sep 9 11:52:22 charon 13353 06[CFG] <6> selecting proposal:
Sep 9 11:52:22 charon 13353 06[CFG] <6> no acceptable DIFFIE_HELLMAN_GROUP found
Sep 9 11:52:22 charon 13353 06[CFG] <6> selecting proposal:
Sep 9 11:52:22 charon 13353 06[CFG] <6> no acceptable INTEGRITY_ALGORITHM found
Sep 9 11:52:22 charon 13353 06[CFG] <6> selecting proposal:
Sep 9 11:52:22 charon 13353 06[CFG] <6> no acceptable INTEGRITY_ALGORITHM found
Sep 9 11:52:22 charon 13353 06[CFG] <6> selecting proposal:
Sep 9 11:52:22 charon 13353 06[CFG] <6> no acceptable INTEGRITY_ALGORITHM found
Sep 9 11:52:22 charon 13353 06[CFG] <6> selecting proposal:
Sep 9 11:52:22 charon 13353 06[CFG] <6> no acceptable DIFFIE_HELLMAN_GROUP found
Sep 9 11:52:22 charon 13353 06[CFG] <6> selecting proposal:
Sep 9 11:52:22 charon 13353 06[CFG] <6> no acceptable INTEGRITY_ALGORITHM found
Sep 9 11:52:22 charon 13353 06[CFG] <6> selecting proposal:
Sep 9 11:52:22 charon 13353 06[CFG] <6> no acceptable INTEGRITY_ALGORITHM found
Sep 9 11:52:22 charon 13353 06[CFG] <6> selecting proposal:
Sep 9 11:52:22 charon 13353 06[CFG] <6> proposal matches
Sep 9 11:52:22 charon 13353 06[CFG] <6> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048, IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_512_256/PRF_HMAC_SHA2_512/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1536, IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1536, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024, IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_128/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024
Sep 9 11:52:22 charon 13353 06[CFG] <6> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Sep 9 11:52:22 charon 13353 06[CFG] <6> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Sep 9 11:52:22 charon 13353 06[IKE] <6> sending XAuth vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> sending DPD vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> sending FRAGMENTATION vendor ID
Sep 9 11:52:22 charon 13353 06[IKE] <6> sending NAT-T (RFC 3947) vendor ID
Sep 9 11:52:22 charon 13353 06[ENC] <6> generating ID_PROT response 0 [ SA V V V V ]
Sep 9 11:52:22 charon 13353 06[NET] <6> sending packet: from def.ijk.148.51[500] to xyz.abc.116.238[500] (160 bytes)
Sep 9 11:52:23 charon 13353 06[NET] <6> received packet: from xyz.abc.116.238[500] to def.ijk.148.51[500] (228 bytes)
Sep 9 11:52:23 charon 13353 06[ENC] <6> parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
Sep 9 11:52:23 charon 13353 06[IKE] <6> remote host is behind NAT
Sep 9 11:52:23 charon 13353 06[CFG] <6> candidate "con-mobile", match: 1/1/28 (me/other/ike)
Sep 9 11:52:23 charon 13353 06[ENC] <6> generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
Sep 9 11:52:23 charon 13353 06[NET] <6> sending packet: from def.ijk.148.51[500] to xyz.abc.116.238[500] (244 bytes)
Sep 9 11:52:23 charon 13353 06[NET] <6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (108 bytes)
Sep 9 11:52:23 charon 13353 06[ENC] <6> parsed ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
Sep 9 11:52:23 charon 13353 06[CFG] <6> looking for pre-shared key peer configs matching def.ijk.148.51...xyz.abc.116.238[172.20.10.2]
Sep 9 11:52:23 charon 13353 06[CFG] <6> candidate "con-mobile", match: 1/1/28 (me/other/ike)
Sep 9 11:52:23 charon 13353 06[CFG] <6> selected peer config "con-mobile"
Sep 9 11:52:23 charon 13353 06[IKE] <con-mobile|6> IKE_SA con-mobile[6] established between def.ijk.148.51[def.ijk.148.51]...xyz.abc.116.238[172.20.10.2]
Sep 9 11:52:23 charon 13353 06[IKE] <con-mobile|6> IKE_SA con-mobile[6] state change: CONNECTING => ESTABLISHED
Sep 9 11:52:23 charon 13353 06[IKE] <con-mobile|6> scheduling reauthentication in 23393s
Sep 9 11:52:23 charon 13353 06[IKE] <con-mobile|6> maximum IKE_SA lifetime 26273s
Sep 9 11:52:23 charon 13353 06[ENC] <con-mobile|6> generating ID_PROT response 0 [ ID HASH ]
Sep 9 11:52:23 charon 13353 06[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (76 bytes)
Sep 9 11:52:24 charon 13353 10[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (396 bytes)
Sep 9 11:52:24 charon 13353 10[ENC] <con-mobile|6> parsed QUICK_MODE request 1176519332 [ HASH SA No ID ID NAT-OA NAT-OA ]
Sep 9 11:52:24 charon 13353 10[IKE] <con-mobile|6> changing received traffic selectors 172.20.10.2/32|/0[udp/61568]=== def.ijk.148.51/32|/0[udp/l2f] due to NAT
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> looking for a child config for def.ijk.148.51/32|/0[udp/l2f] === xyz.abc.116.238/32|/0[udp/61568]
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> proposing traffic selectors for us:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> def.ijk.148.51/32|/0
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> proposing traffic selectors for other:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> xyz.abc.116.238/32|/0
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> candidate "con-mobile" with prio 1+1
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> found matching child config "con-mobile" with prio 2
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> selecting traffic selectors for other:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> config: xyz.abc.116.238/32|/0, received: xyz.abc.116.238/32|/0[udp/61568] => match: xyz.abc.116.238/32|/0[udp/61568]
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> selecting traffic selectors for us:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> config: def.ijk.148.51/32|/0, received: def.ijk.148.51/32|/0[udp/l2f] => match: def.ijk.148.51/32|/0[udp/l2f]
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> selecting proposal:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> no acceptable ENCRYPTION_ALGORITHM found
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> selecting proposal:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> no acceptable ENCRYPTION_ALGORITHM found
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> selecting proposal:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> no acceptable ENCRYPTION_ALGORITHM found
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> selecting proposal:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> no acceptable INTEGRITY_ALGORITHM found
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> selecting proposal:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> no acceptable INTEGRITY_ALGORITHM found
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> selecting proposal:
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> proposal matches
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_MD5_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_MD5_96/NO_EXT_SEQ, ESP:3DES_CBC/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:3DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ, ESP:3DES_CBC/HMAC_MD5_96/NO_EXT_SEQ
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> configured proposals: ESP:AES_CBC_128/HMAC_MD5_96/NO_EXT_SEQ
Sep 9 11:52:24 charon 13353 10[CFG] <con-mobile|6> selected proposal: ESP:AES_CBC_128/HMAC_MD5_96/NO_EXT_SEQ
Sep 9 11:52:24 charon 13353 10[ENC] <con-mobile|6> generating QUICK_MODE response 1176519332 [ HASH SA No ID ID NAT-OA NAT-OA ]
Sep 9 11:52:24 charon 13353 10[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (204 bytes)
Sep 9 11:52:24 charon 13353 10[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (60 bytes)
Sep 9 11:52:24 charon 13353 10[ENC] <con-mobile|6> parsed QUICK_MODE request 1176519332 [ HASH ]
Sep 9 11:52:24 charon 13353 10[CHD] <con-mobile|6> CHILD_SA con-mobile{5} state change: CREATED => INSTALLING
Sep 9 11:52:24 charon 13353 10[CHD] <con-mobile|6> using AES_CBC for encryption
Sep 9 11:52:24 charon 13353 10[CHD] <con-mobile|6> using HMAC_MD5_96 for integrity
Sep 9 11:52:24 charon 13353 10[CHD] <con-mobile|6> adding inbound ESP SA
Sep 9 11:52:24 charon 13353 10[CHD] <con-mobile|6> SPI 0xced0dc9e, src xyz.abc.116.238 dst def.ijk.148.51
Sep 9 11:52:24 charon 13353 10[CHD] <con-mobile|6> adding outbound ESP SA
Sep 9 11:52:24 charon 13353 10[CHD] <con-mobile|6> SPI 0x03595e06, src def.ijk.148.51 dst xyz.abc.116.238
Sep 9 11:52:24 charon 13353 10[IKE] <con-mobile|6> CHILD_SA con-mobile{5} established with SPIs ced0dc9e_i 03595e06_o and TS def.ijk.148.51/32|/0[udp/l2f] === xyz.abc.116.238/32|/0[udp/61568]
Sep 9 11:52:24 charon 13353 10[CHD] <con-mobile|6> CHILD_SA con-mobile{5} state change: INSTALLING => INSTALLED
Sep 9 11:52:25 charon 13353 06[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:25 charon 13353 06[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:25 charon 13353 06[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:25 charon 13353 06[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:25 charon 13353 06[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 3401304144 [ HASH N(DPD) ]
Sep 9 11:52:25 charon 13353 06[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:25 charon 13353 06[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:25 charon 13353 06[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:25 charon 13353 06[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:25 charon 13353 06[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 2200524928 [ HASH N(DPD_ACK) ]
Sep 9 11:52:25 charon 13353 06[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:25 charon 13353 06[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:26 charon 13353 10[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:26 charon 13353 10[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:26 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:26 charon 13353 10[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:26 charon 13353 10[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 3125698663 [ HASH N(DPD) ]
Sep 9 11:52:26 charon 13353 10[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:26 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:26 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:26 charon 13353 10[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:26 charon 13353 10[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 1412957240 [ HASH N(DPD_ACK) ]
Sep 9 11:52:26 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:26 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:27 charon 13353 10[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:27 charon 13353 10[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:27 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:27 charon 13353 10[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:27 charon 13353 10[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 3169018633 [ HASH N(DPD) ]
Sep 9 11:52:27 charon 13353 10[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:27 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:27 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:27 charon 13353 10[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:27 charon 13353 10[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 161370408 [ HASH N(DPD_ACK) ]
Sep 9 11:52:27 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:27 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:28 charon 13353 10[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:28 charon 13353 10[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:28 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:28 charon 13353 10[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:28 charon 13353 10[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 2846347057 [ HASH N(DPD) ]
Sep 9 11:52:28 charon 13353 10[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:28 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:28 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:28 charon 13353 10[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:28 charon 13353 10[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 3166884827 [ HASH N(DPD_ACK) ]
Sep 9 11:52:28 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:28 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:29 charon 13353 10[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:29 charon 13353 10[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:29 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:29 charon 13353 10[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:29 charon 13353 10[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 1399713983 [ HASH N(DPD) ]
Sep 9 11:52:29 charon 13353 10[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:29 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:29 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:29 charon 13353 10[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:29 charon 13353 10[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 1972336736 [ HASH N(DPD_ACK) ]
Sep 9 11:52:29 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:29 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:30 charon 13353 10[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:30 charon 13353 10[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:30 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:30 charon 13353 10[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:30 charon 13353 10[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 652951414 [ HASH N(DPD) ]
Sep 9 11:52:30 charon 13353 10[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:30 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:30 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:30 charon 13353 10[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:30 charon 13353 10[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 404915874 [ HASH N(DPD_ACK) ]
Sep 9 11:52:30 charon 13353 10[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:30 charon 13353 10[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:31 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:31 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:31 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:31 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:31 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 920528892 [ HASH N(DPD) ]
Sep 9 11:52:31 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:31 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:31 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:31 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:31 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 3285350641 [ HASH N(DPD_ACK) ]
Sep 9 11:52:31 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:31 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:32 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:32 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:32 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:32 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:32 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 2256793496 [ HASH N(DPD) ]
Sep 9 11:52:32 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:32 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:32 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:32 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:32 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 1455714175 [ HASH N(DPD_ACK) ]
Sep 9 11:52:32 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:32 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:33 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:33 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:33 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:33 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:33 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 331134726 [ HASH N(DPD) ]
Sep 9 11:52:33 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:33 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:33 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:33 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:33 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 2640606474 [ HASH N(DPD_ACK) ]
Sep 9 11:52:33 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:33 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:34 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:34 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:34 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:34 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:34 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 1247638940 [ HASH N(DPD) ]
Sep 9 11:52:34 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:34 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:34 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:34 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:34 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 2530195038 [ HASH N(DPD_ACK) ]
Sep 9 11:52:34 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:34 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:35 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:35 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:35 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:35 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:35 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 2079041617 [ HASH N(DPD) ]
Sep 9 11:52:35 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:35 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:35 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:35 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:35 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 2914855772 [ HASH N(DPD_ACK) ]
Sep 9 11:52:35 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:35 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:36 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:36 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:36 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:36 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:36 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 860455598 [ HASH N(DPD) ]
Sep 9 11:52:36 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:36 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:36 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:36 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:36 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 841506726 [ HASH N(DPD_ACK) ]
Sep 9 11:52:36 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:36 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:37 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:37 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:37 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:37 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:37 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 2252303055 [ HASH N(DPD) ]
Sep 9 11:52:37 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:37 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:37 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:37 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:37 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 2173860112 [ HASH N(DPD_ACK) ]
Sep 9 11:52:37 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:37 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:38 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:38 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:38 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:38 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:38 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 2162668809 [ HASH N(DPD) ]
Sep 9 11:52:38 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:38 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:38 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:38 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:38 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 2263478134 [ HASH N(DPD_ACK) ]
Sep 9 11:52:38 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:38 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:39 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:39 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:39 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:39 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:39 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 2611093714 [ HASH N(DPD) ]
Sep 9 11:52:39 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:39 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:39 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:39 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:39 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 2556323718 [ HASH N(DPD_ACK) ]
Sep 9 11:52:39 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:39 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:40 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:40 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:40 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:40 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:40 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 4040646048 [ HASH N(DPD) ]
Sep 9 11:52:40 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:40 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:40 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:40 charon 13353 09[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:40 charon 13353 09[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 1484630634 [ HASH N(DPD_ACK) ]
Sep 9 11:52:40 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:40 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:41 charon 13353 09[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:41 charon 13353 09[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:41 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:41 charon 13353 09[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:41 charon 13353 09[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 830103228 [ HASH N(DPD) ]
Sep 9 11:52:41 charon 13353 09[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:41 charon 13353 09[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:41 charon 13353 09[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:41 charon 13353 12[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:41 charon 13353 12[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 3661340784 [ HASH N(DPD_ACK) ]
Sep 9 11:52:41 charon 13353 12[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:41 charon 13353 12[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:42 charon 13353 12[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:42 charon 13353 12[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:42 charon 13353 12[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:42 charon 13353 12[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:42 charon 13353 12[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 2881913898 [ HASH N(DPD) ]
Sep 9 11:52:42 charon 13353 12[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:42 charon 13353 12[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:42 charon 13353 12[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:42 charon 13353 12[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:42 charon 13353 12[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 1867954662 [ HASH N(DPD_ACK) ]
Sep 9 11:52:42 charon 13353 12[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:42 charon 13353 12[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:43 charon 13353 12[IKE] <con-mobile|6> sending DPD request
Sep 9 11:52:43 charon 13353 12[IKE] <con-mobile|6> queueing ISAKMP_DPD task
Sep 9 11:52:43 charon 13353 12[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:43 charon 13353 12[IKE] <con-mobile|6> activating ISAKMP_DPD task
Sep 9 11:52:43 charon 13353 12[ENC] <con-mobile|6> generating INFORMATIONAL_V1 request 1763851670 [ HASH N(DPD) ]
Sep 9 11:52:43 charon 13353 12[NET] <con-mobile|6> sending packet: from def.ijk.148.51[4500] to xyz.abc.116.238[15557] (92 bytes)
Sep 9 11:52:43 charon 13353 12[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:43 charon 13353 12[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:43 charon 13353 12[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:43 charon 13353 12[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 291869909 [ HASH N(DPD_ACK) ]
Sep 9 11:52:43 charon 13353 12[IKE] <con-mobile|6> activating new tasks
Sep 9 11:52:43 charon 13353 12[IKE] <con-mobile|6> nothing to initiate
Sep 9 11:52:44 charon 13353 12[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (76 bytes)
Sep 9 11:52:44 charon 13353 12[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 742545670 [ HASH D ]
Sep 9 11:52:44 charon 13353 12[IKE] <con-mobile|6> received DELETE for ESP CHILD_SA with SPI 03595e06
Sep 9 11:52:44 charon 13353 12[CHD] <con-mobile|6> CHILD_SA con-mobile{5} state change: INSTALLED => DELETING
Sep 9 11:52:44 charon 13353 12[IKE] <con-mobile|6> closing CHILD_SA con-mobile{5} with SPIs ced0dc9e_i (660 bytes) 03595e06_o (0 bytes) and TS def.ijk.148.51/32|/0[udp/l2f] === xyz.abc.116.238/32|/0[udp/61568]
Sep 9 11:52:44 charon 13353 12[CHD] <con-mobile|6> CHILD_SA con-mobile{5} state change: DELETING => DELETED
Sep 9 11:52:44 charon 13353 12[CHD] <con-mobile|6> CHILD_SA con-mobile{5} state change: DELETED => DESTROYING
Sep 9 11:52:44 charon 13353 11[NET] <con-mobile|6> received packet: from xyz.abc.116.238[15557] to def.ijk.148.51[4500] (92 bytes)
Sep 9 11:52:44 charon 13353 11[ENC] <con-mobile|6> parsed INFORMATIONAL_V1 request 2500915748 [ HASH D ]
Sep 9 11:52:44 charon 13353 11[IKE] <con-mobile|6> received DELETE for IKE_SA con-mobile[6]
Sep 9 11:52:44 charon 13353 11[IKE] <con-mobile|6> deleting IKE_SA con-mobile[6] between def.ijk.148.51[def.ijk.148.51]...xyz.abc.116.238[172.20.10.2]
Sep 9 11:52:44 charon 13353 11[IKE] <con-mobile|6> IKE_SA con-mobile[6] state change: ESTABLISHED => DELETING
Sep 9 11:52:44 charon 13353 11[IKE] <con-mobile|6> IKE_SA con-mobile[6] state change: DELETING => DELETING
Sep 9 11:52:44 charon 13353 11[IKE] <con-mobile|6> IKE_SA con-mobile[6] state change: DELETING => DESTROYING Weiss jemand, was da falsch läuft?
An support.apple.com/de-at/HT211840 liegt es nicht?
Bei VPN/IPsec/Pre-Shared-Keys zeigst du im Screenshot die Parameter für EAP an. Bei PSK (so wie in deinem Screenshot dargestellt) zeigt er bei mir nur Identier, Secret Type und Pre-Shared-Key an.
Wenn die den Secret-Type auf EAP umstelle, dann wird in der 2.5, so wie in deinem Screenshot zusätzlich die Parameter Identifier type, Virtual Address Pool und DNS Server angezeigt.
Wenn die den Secret-Type auf EAP umstelle, dann wird in der 2.5, so wie in deinem Screenshot zusätzlich die Parameter Identifier type, Virtual Address Pool und DNS Server angezeigt.
Der identifier "alluser" hat sich geändert in "any" (PFS Community Edition 2.6)
Hat mich jetzt fast einen ganzen Tag Lebenszeit gekostet, um den Fehler rauszufinden.
Wer den Fehler "no shared key found" im System Logs IPsec findet sollte dies unbedingt prüfen!
PS: der Autor dieses Tutorials sollte erwägen, diese Info an die entsprechende Stelle preiszugeben!!!
Hat mich jetzt fast einen ganzen Tag Lebenszeit gekostet, um den Fehler rauszufinden.
Wer den Fehler "no shared key found" im System Logs IPsec findet sollte dies unbedingt prüfen!
PS: der Autor dieses Tutorials sollte erwägen, diese Info an die entsprechende Stelle preiszugeben!!!
@aqui
Vielen Dank für das tolle Tutorial.
Ich habe hier noch einen kleinen Hinweis für Windows als Client.
Bei mir Windows 11 Pro 22H2 tauchte "Fehler 789" im Ereignislog auf.
Nach kurzer Google-Suche bin ich hier gelandet
Ich musste auch die beiden Keys in der Registrty setzen wie hier beschrieben: Fehler 789 beim Versuch einer VPN L2TP IPSEC Verbindung unter Windows 7 Enterprise herzustellen
Und für alle die sich wundern, dass sie nicht auf Ihre Rechner / Server zugreifen können ein Tipp: Wenn die pfsense als Standardgateway eingetragen ist, hilft das ungemein
Vielen Dank für das tolle Tutorial.
Ich habe hier noch einen kleinen Hinweis für Windows als Client.
Bei mir Windows 11 Pro 22H2 tauchte "Fehler 789" im Ereignislog auf.
Nach kurzer Google-Suche bin ich hier gelandet
Ich musste auch die beiden Keys in der Registrty setzen wie hier beschrieben: Fehler 789 beim Versuch einer VPN L2TP IPSEC Verbindung unter Windows 7 Enterprise herzustellen
Und für alle die sich wundern, dass sie nicht auf Ihre Rechner / Server zugreifen können ein Tipp: Wenn die pfsense als Standardgateway eingetragen ist, hilft das ungemein
Es macht also immer Sinn beide DH Groups in der P1 zu setzen. Ggf. war das der Fehler?!
nein, definitiv nicht.Ich habe deine Anleitung 1:1 abgearbeitet und bin dann bei Problemen davon ausgegangen, das deine Anleitung korrekt ist und habe sie entsprechend nicht mehr angefasst.
2 Probleme gabs:
1. ich habe die Registryeinträge gesetzt - keine Ahnung ob nur einer oder beide notwendig sind. Ohne gab es immer den o.g. Fehler.
2. Ich hatte das Standardgateway auf dem Server hinter der pfsense vergessen zu ändern.
Mit den beiden Änderungen lief in meinem Fall alles. Deine Anleitung ist also bulletproof!
Möchte erstmal (wie früher so oft) ein großes DANKE sagen. Hatte das komplett übersehen, dass die Sense nun auch L2TP/IPSec supported. So konnte ich mein geliebtes olles XDA-Orbit mit Bordmitteln zum synchronisieren verbinden und das nervige OpenVPN loswerden.  Dafür reicht auch EDGE mit 256 kbit/s...
Dafür reicht auch EDGE mit 256 kbit/s...
ABER: Wie kriege ich die PfSense (2.6) dazu, zusätzlich auch das "klassische" mobile IPSec mit PSK / XAUTH zu supporten? Wird schon in der Phase 1 schwierig... Entweder - oder... Sie supported ja nachwievor nur eine Phase 1 für die mobile Einwahl. Hast Du ne Idee für nen Workaround? Irgendwie von hinten mit der Faust... Also einfach eine "normale" Phase 1 kreieren und dieser dann die mobile Einwahl unterschieben? Bin da bisher nicht weiter gekommen...
LG
El Buckonehro
Edit zu Win 11: Es sollte ohne Weiteres möglich sein, in Win 11 SHA-256 unter den supported Ciphers freizuschalten. Ist immer irgendwo in der Registry, googelt man leicht. Hat wohl ein Entwickler da gepennt...
ABER: Wie kriege ich die PfSense (2.6) dazu, zusätzlich auch das "klassische" mobile IPSec mit PSK / XAUTH zu supporten? Wird schon in der Phase 1 schwierig... Entweder - oder... Sie supported ja nachwievor nur eine Phase 1 für die mobile Einwahl. Hast Du ne Idee für nen Workaround? Irgendwie von hinten mit der Faust... Also einfach eine "normale" Phase 1 kreieren und dieser dann die mobile Einwahl unterschieben? Bin da bisher nicht weiter gekommen...
LG
El Buckonehro
Edit zu Win 11: Es sollte ohne Weiteres möglich sein, in Win 11 SHA-256 unter den supported Ciphers freizuschalten. Ist immer irgendwo in der Registry, googelt man leicht. Hat wohl ein Entwickler da gepennt...
Wie meinst du das genau??
Na ja, ich nutze "eigentlich" ne IKEv1 Einwahl und den Shrew-Client mit XAuth Identifizierung für die User. Der läuft auch auf Win10 stabil.
Wenn ich nun auf der PfSense die Phase1 für L2TP/Ipsec konfiguriere kann ich ja nur "Mutual PSK" definieren damit es klappt. Sobald ich da "Mutual PSK and XAuth" setze funktioniert die L2TP/IPsec Einwahl nicht mehr, auch wenn ich den Peer Identifier auf "any" setze.
Wie kann ich User identifizieren und die Berechtigungen für die VPN-Einwahl der User auf der PfSense für IPSec mobile Clients ohne L2TP nutzen UND eine L2TP/Ipsec einwahl ermöglichen? Ich kann dem L2TP Client die User ja nicht zusätzlich schon für die IPSec-Einwahl mitgeben. Und die Pfsense erwartet offenbar "irgendwas" wenn ein Peer Identifier in der Phase 1 gesetzt ist. "Nix" ist hier offenbar keine untergruppe von "any".
Will sagen: Die ganze tolle Nutzerverwaltung der PfSense für die VPN-Einwahl ist obsolet, wenn man L2TP nutzt. Schade...
Zitat von @aqui:
Der läuft auch auf Win10 stabil.
Na ja, das ist ein bisschen (mit Verlaub) "krank" wenn du problemlos mit IKEv2 die Win10 onboard Clients nutzen kannst. Ist schon recht sinnfrei da dann noch einen ollen IKEv1 Client extra zu installieren...aber nundenn. Warum einfach machen wenn es antik und umständlich auch geht?! 🤣Ganz einfach: Gewohnheit. "Never change a running system." Oder: "Never disturb a working customer."
Lange Zeit musste man sich bei der PfSense entscheiden, ob IKEv1 ODER IKEv2 für die mobile Einwahl verwendet werden soll. Kein Parallelbetrieb. Habe gerade nochmal gecheckt: Nun kann sie beides je nach Anfrage. (Seit 2.5 oder 2.6?) Ist einfach ein Überbleibsel aus der Zeit des Parallelbetriebs Win7 / Win 10...
Sobald ich da "Mutual PSK and XAuth" setze funktioniert die L2TP/IPsec Einwahl nicht mehr,
Erwartbar...⚠️ Du hast beachtet das bei L2TP die Tunnel Connection immer im Transport Mode arbeitet und NICHT im Tunnel Mode wie vermutlich bei deinem Shrew Client?!
Beide Modi sind NICHT kompatibel!
Das doof ist.
Die ganze tolle Nutzerverwaltung der PfSense für die VPN-Einwahl ist obsolet, wenn man L2TP nutzt.
Nein, wie kommst du auf solchen Unsinn?? Sorry...Du musst auch die einzelnen L2TP User mit Usernamen und Password auf der Firewall definieren.
Da hast du dann leider das Tutorial nicht richtig gelesen (was ja mal passieren kann als einäugiger Buccaneer 😉) oder missverstanden?! 🤔
Genau, dochdoch. Doppelmoppel. In den User-Settings ist halt nur die VPN-XAuth Einwahl vorgesehen, nicht die L2TP. Die definiere ich getrennt. Ist ja auch alles kein Weltuntergang, ich muss hier nun nen olles Windows Mobile 6 mit L2TP/IPSec ab und an ins Netz bringen. Absolutes Nischenthema. Ist mir schon klar, mein Bester.
e mare sanitas
Buc nicht Kanzler
Serie: VPN-Praxistutorials
IKEv2 VPN server for Windows and Apple clients on Raspberry Pi (englisch)1IKEv2 VPN Server für Windows und Apple Clients mit Raspberry Pi11Merkzettel: VPN Installation mit Wireguard29PfSense VPN mit L2TP (IPsec) Protokoll für mobile Nutzer24Merkzettel: VPN Installation mit OpenVPN39IPsec IKEv2 Standort VPN Vernetzung mit Cisco, pfSense OPNsense und Mikrotik1Cisco, Mikrotik, pfSense VPN Standort Vernetzung mit dynamischem Routing13IPsec IKEv2 VPN für mobile Benutzer auf der pfSense oder OPNsense Firewall einrichten212IPsec VPN Praxis mit Standort Vernetzung Cisco, Mikrotik, pfSense, FritzBox u.a20